Continuing our series on cyber security, following the fifth part on Social Networking, this blog post aims to initiate the readers on the what, where and how of Digital Signatures in information security.
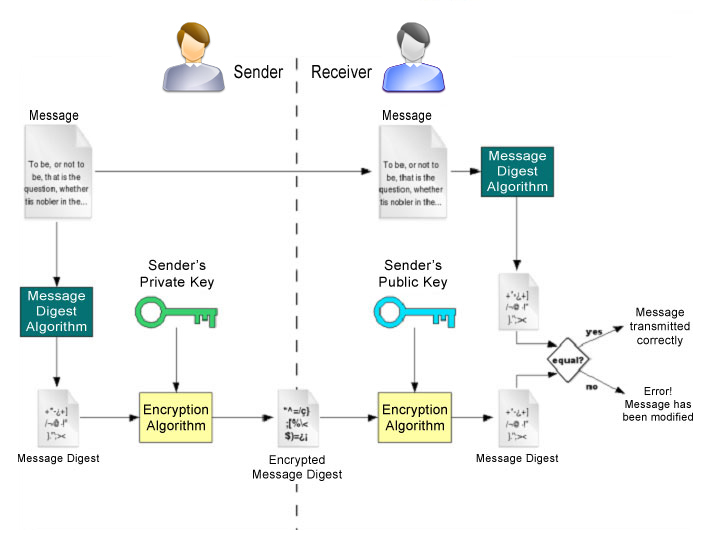
A digital signature is a method of authenticating both the source and the content of any form of electronic data/message. When validated the recipient of the signed electronic data/message can be confident of the integrity of the content, i.e. it hasn’t been altered in any form during transit, and that the sender is the person or entity that signed the content.
 Source: https://www.esignit.org/NewEsignit/images/Digital%20authentication%20process.jpg
Source: https://www.esignit.org/NewEsignit/images/Digital%20authentication%20process.jpg
Digital signatures are based on asymmetric cryptography; a complex mathematical scheme involving a set of public, i.e. freely distributable, and private (aka ‘secret’) encryption keys is employed to create a secure channel for transmission of data across any network. If deployed correctly the receiver can believe that the data/message is perfectly authentic, and the sender cannot claim that it was fraudulent/forged unless the sender admits that their private key has been stolen and misused.
A basic example of usage of a digital signature would be an e-receipt for an online transaction, such as for an online insurance premium payment for which the insurance company could issue a digitally signed receipt from a specific person in that organisation. This receipt would normally require a signature by hand if done as a physical paper transaction. This method of digital authentication will become more and more prevalent as organisations move away from paper documentation.
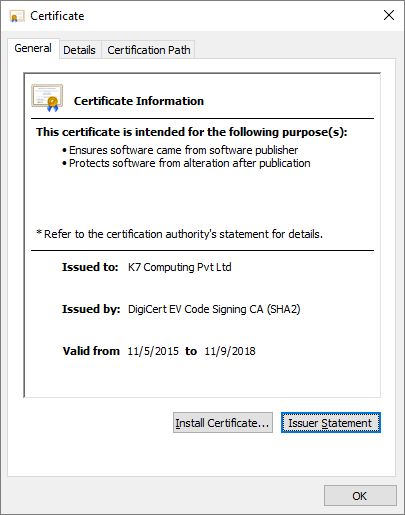
Digital signatures are also used in digital certificates that are issued to entities that seek them. A digital certificate is like an identity card issued to an entity by a “Certification Authority” (CA), e.g. VeriSign. The certificate contains information about the entity that has been vetted by the CA, the entity’s public key, the CA’s name and the CA’s digital signature.
Since CAs are meant to carefully vet entities before issuing them certificates for a price, typically from INR 50,000 (USD 800) to INR 100,000 (USD 1500) for a period ranging from 1 year to 3 years for an EV (Extended Validity) Cert, digitally signed files are accorded an enhanced trustworthiness. Windows identifies likely safe or harmless files based on the validity of digital signatures on files that are executed on the OS using pre-populated trusted certificates in its certificate repository. Windows employs UAC (User Access Control) mechanisms to prevent malicious files from executing automatically. Files that have digital signatures from Microsoft can suppress UAC while other signers need to be authorized for execution on ‘first run’.
Websites also use digital certificates for authentication, typically an SSL (Secure Socket Layer) certificate. There are various processes for certifying a website. It can be certified on the domain level based on the registration information or the respective organisation can be certified, which would follow a more manual process of scrutiny to check the authenticity of the organization, etc. An EV Cert however requires a higher level of scrutiny and background checks. If a website handles sensitive, personally identifiable information it should be a secure site with appropriately verified digital certificates.
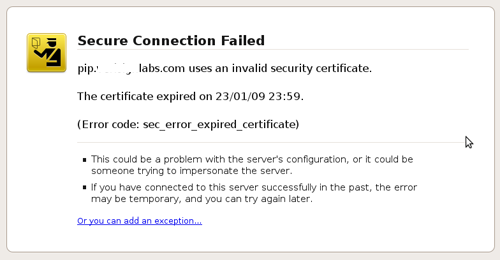
As seen in the image above a digital certificate is not issued for eternity but only for a stipulated period of time. This is done to ensure that an organisation once legitimate remains legitimate to retain certificate renew rights. A CA could either choose to not issue a certificate to the organisation after the stipulated period is complete or, if the organisation has gone rogue, the CA could revoke the certificate during the validity period. A time limit on the validity of a certificate also reduces the potential damage which could be done if a certificate has been silently leaked, i.e. stolen, and is being used to sign malware.
Microsoft now employs a strict policy on what is allowed to be loaded into Windows kernel memory. Windows 10 strictly loads driver files if and only if they are signed by an EV certificate. An EV cert requires legal and human validation of the purchaser, and is a cert which fulfills the EV vetting criteria of the CA. This move should hopefully disrupt the kernel rootkit infection vector on Windows 10 machines.
Though digital signatures play a big part in securing digital content they too have their fair share of cases of abuse and misuse. A follow up to this blog post that discusses more about how digital signatures are misused can be expected in the near future … stay tuned.
…to part 7: (Frau)Duly Digi-Signed
Images courtesy of:
sslshopper.com
esignit.org
K7 Threat Control Lab
If you wish to subscribe to our blog, please add the URL provided below to your blog reader: https://labs.k7computing.com/feed/