There are thousands of applications and software products on the internet. Many of them are potentially unwanted, ranging from browser plugins, price aggregators, driver installers, to apps that claim to make your computer a zillion times faster. App developers, promoters and distributors will have some monetization strategy on these products, mostly through advertisement or by demanding payment for premium features.
Over the years, there came a new monetization strategy which employs what appears to be a barter system. For allowing the customer to use their app for free, the developers get to use the customer’s system resources for their own purposes. Coin mining was a prominent operation on such idle system resources. Now they have gone a step further and are bartering for the customer’s IP address / network resource. We have seen multiple such apps over a couple of years.
In this blog, we will analyze a few of these apps and enumerate the pitfalls that any user will experience through the various stages during and after the installation process.
Application’s Behaviour
The ip/resource-usage-module is generally integrated into the PUAs. The PUA trades the free usage of the app to users, in exchange for the user’s IP or their device’s free/idle resource. Many times we found that the PUA does not provide the user with proper options to control the behaviour of the third party monetization module.
We have categorised the suspicious behaviour of the monetization module (and also the app’s) into the following stages :
- On executing the installer
- During the installation
- Prior to the installation completion
- After launching the application
On executing the installer
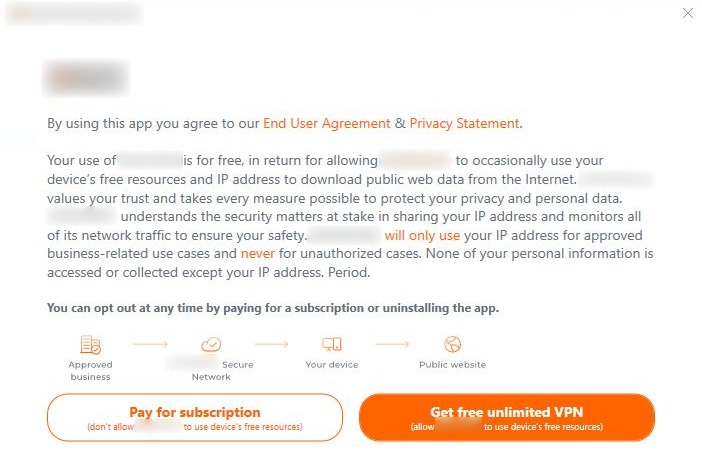
In one of the applications, when the user double clicks the installer/setup file, in an attempt to install it, the app displays a prompt in which the user is provided with options regarding the third party application.
- Accept – It allows the user to to get free unlimited VPN in exchange for free device’s resources or IP of the user’s system
- Decline – It redirects the user to a cart page where they need to buy this product in order to use it
The installation can only proceed when the user selects the “Accept” option (Get free unlimited VPN). It can be inferred that the application coerces the user to share their ip and resources in order to use this app for free.
During the Installation
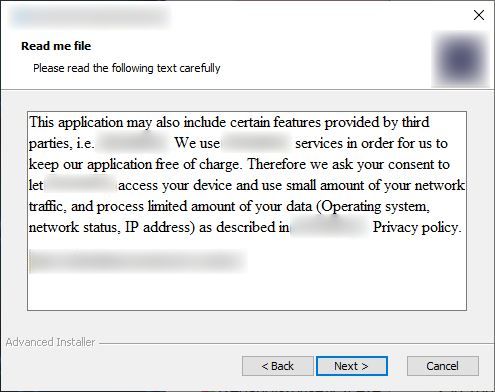
- In this stage, when the user attempts to install the app, it displays a prompt related to the third party module in-between, thereby masquerading as a part of the normal installation flow. In that prompt, it asks to provide permission to access the device and IP of the users’ system
- In this third party prompt, the user can proceed with the installation process only when the user selects the “Next” option, and on the other hand the installation is cancelled or interrupted when the “Cancel” option is selected
- This behaviour of the app can be inferred as follows: the app forces the user to provide access to the device and network traffic if they want to use this app. Also, a third party module masqueraded in the installation flow is suspicious and misleading
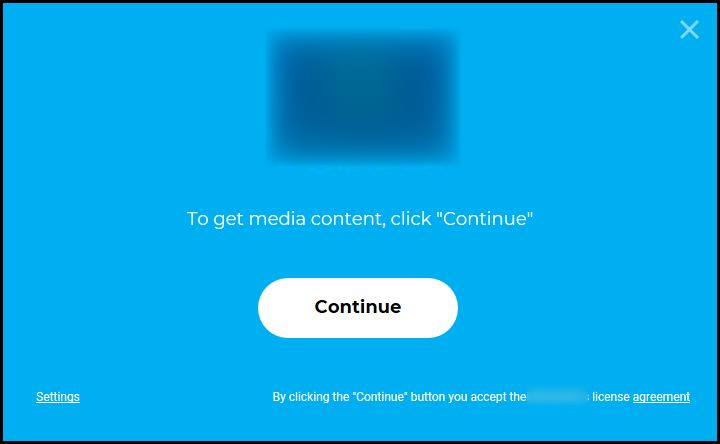
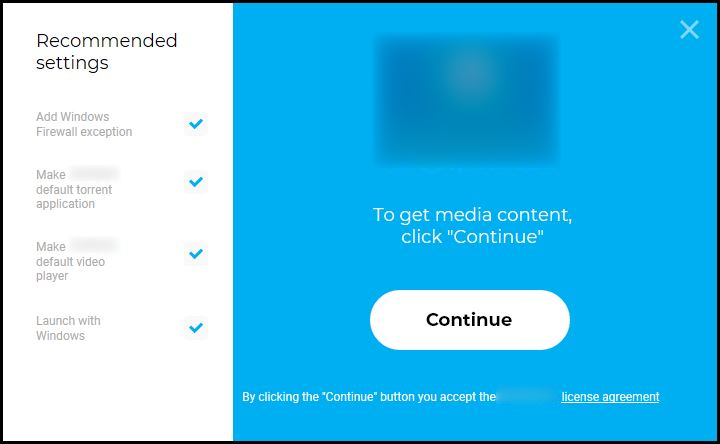
- This is another kind of scenario observed during the installation process of an application. When we try to install an app, in the installation prompt it has a “Settings” option which is not clearly visible but, when the settings option is clicked we can see that the option ”Add windows firewall exception” is enabled by default
- The ”Add windows firewall exception” option seems to be normal wording rather than an option in the settings. If the user doesn’t notice the “Settings” option or rush the installation process they would miss the chance to disable ”Add windows firewall exception” option, so it can be seen as a kind of behaviour that tricks the user into avoiding the option related to windows firewall
- This could lead to system vulnerabilities such as security breach like hacking or malware attack and damage/loss of data etc.
Prior to installation completion
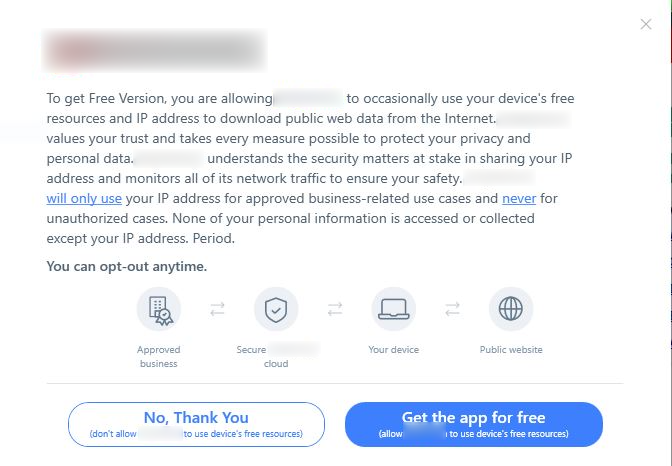
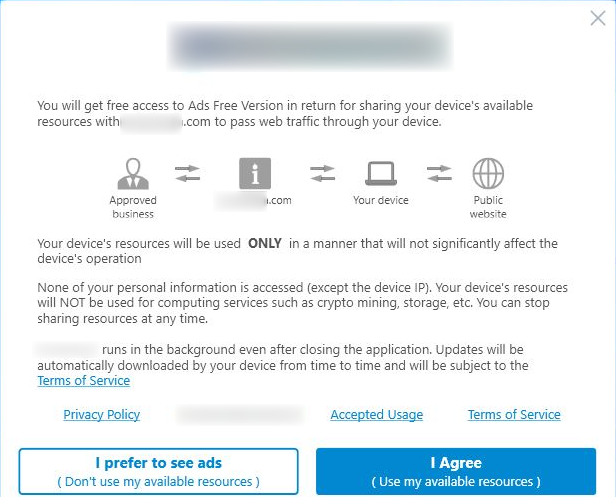
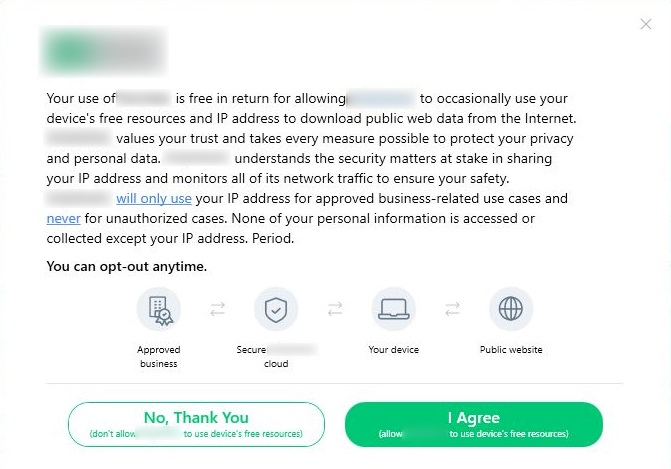
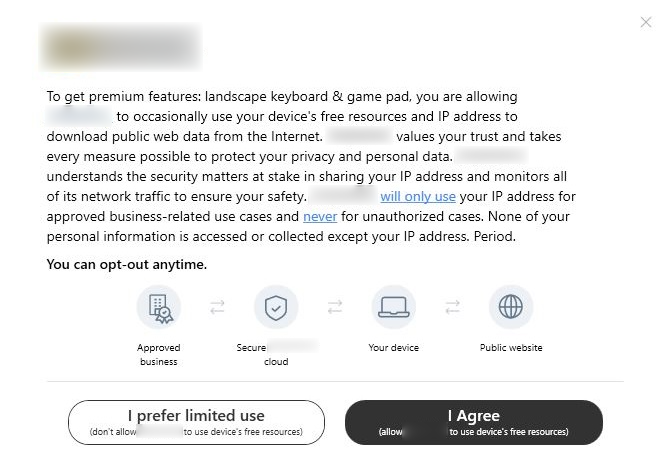
In this type, a prompt related to the third party app is displayed when the installation is about to complete. This prompt shows two options, they are:
- Accept – “Get the app for free”/ “I agree” option that allows the user to use the app for free, in exchange to the user’s ip and resource sharing
- Decline – “No, thank you”/ “I prefer to see ads”/ “I prefer limited use” option
Despite selecting the “Decline” option, the app proceeds with the installation, thus forcing the user to select the “Accept” option.
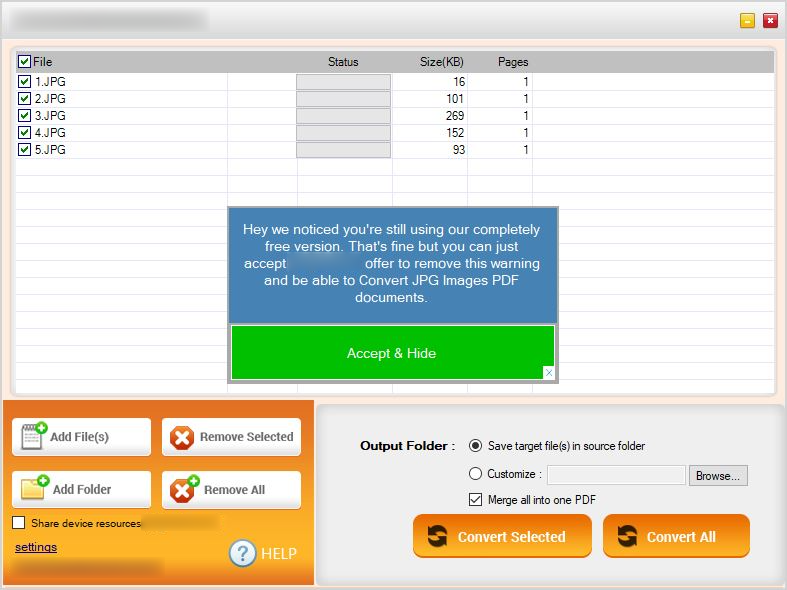
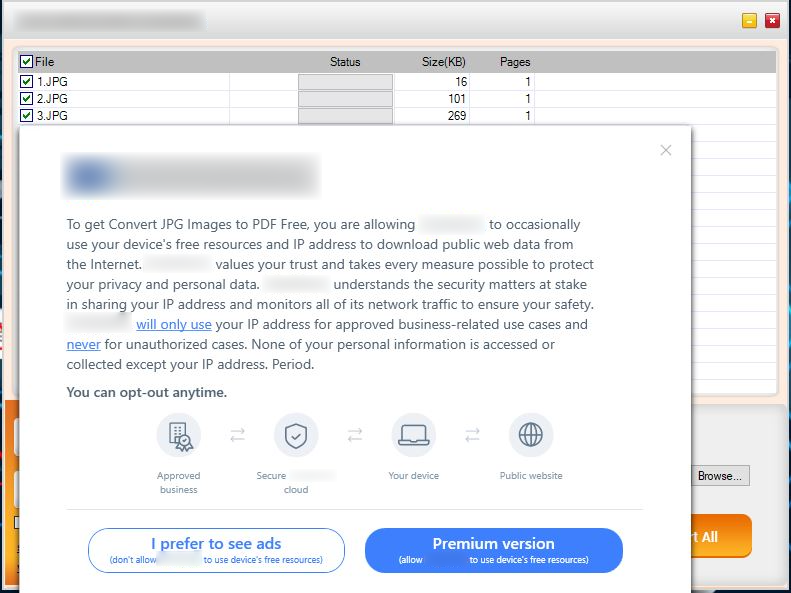
After launching the application
In this type, the prompt related to a third party module is shown only when the app is launched after the installation. The users can use the features for “Free” only when they “Agree/Accept” to share their devices resources and ip or else the user cannot use the features in the app and even more they need to buy the product if they want to use it. This is also considered as suspicious behavior where it coerces the user to accept ip and device resource sharing in order to use the features of the app. Also the prompt (displayed below) appears whenever the app is launched
Why should we steer clear of these apps
As discussed earlier, the apps that we encountered had a common behaviour even though they vary from one another. They ask the user to provide permission to access the user’s device resource or ip address in exchange for the free usage of the app or get full functionality. We would usually assume that the developers and whoever gets hold of our data would only use it for improving their services. Even though they have provided information regarding how the collected system data would be used, as a matter of fact, we can’t say that nothing would happen to our data or our system after we share them with a third party. Your ip address or system resource can be compromised at any given time and could be used for unethical purposes that could jeopardize the user.
Pros of IP sharing
- It can be used for monetization purposes so that user’s can utilize the app for free
Cons of IP sharing
- It can be used to spy on other users
- It can be used to launch cyber attacks such as dropping malware, DDOS, cryptojacking among others
- It can be used to access illegal sites
- It can be used to steal data and other sensitive information







