Earlier this year Google removed Stalkerware (Spy Tracker) apps from Google Play Store after Avast Threat Labs reported on it.
These apps are promoted to be used for genuine purposes such as keeping a tab on loved ones, especially to monitor kids’ activities, or for finding one’s phone. However, most of the time they are used for what the name implies – Stalk/Spy.
Some of the things that Stalkerware can do without being noticed in a victim’s device are given below:
- Track SMS, email, location and third-party messaging apps (WhatsApp, Snapchat, Facebook Messenger, WeChat, Telegram, Hangouts, etc.,)
- Secretly track a person’s activity
- Access camera and microphone for recording incoming calls, viewing live feeds, etc.,
- Access contact list, call log history, photos and videos, web browsing history, etc.,
Infection Vector
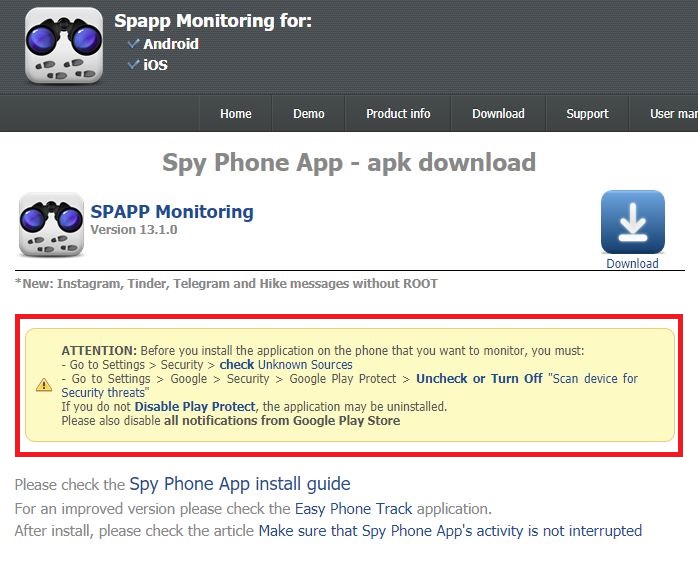
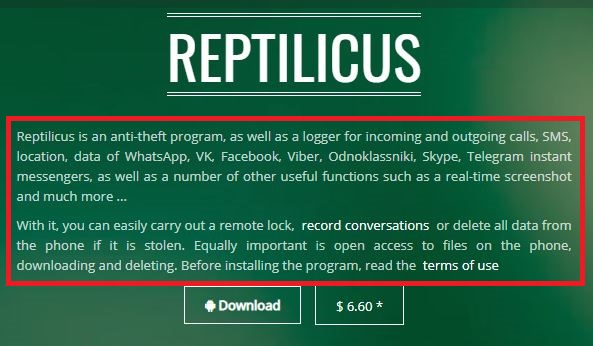
Stalkerware need not necessarily be found only on the Google Play Store; they are mostly found in third-party markets or as a direct download from the vendor website, as shown in Figure 2.
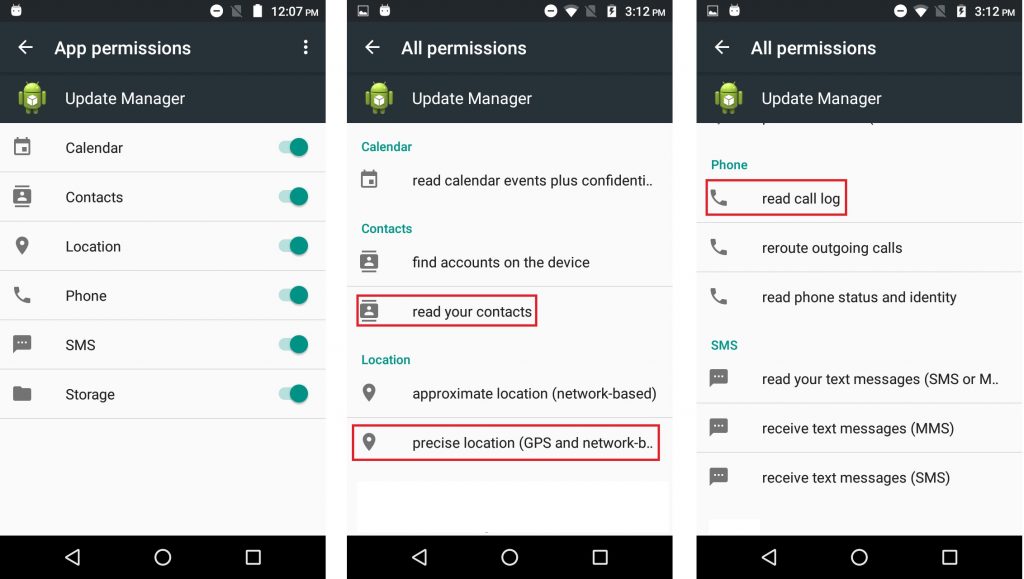
The stalker needs to have at least temporary physical access to the victim’s device to install the app. This app also requests permission to take complete control of the victim’s device. For instance, from the Figure 1 we can see that the stalker can read your contact list, know your location, know who you have spoken to etc.,
Once installed, these apps try to hide themselves from the user; for obvious reasons, the app does not appear in the App Drawer list. This is possible due to the fact that these apps typically have no icons and leave no obvious traces of their presence.
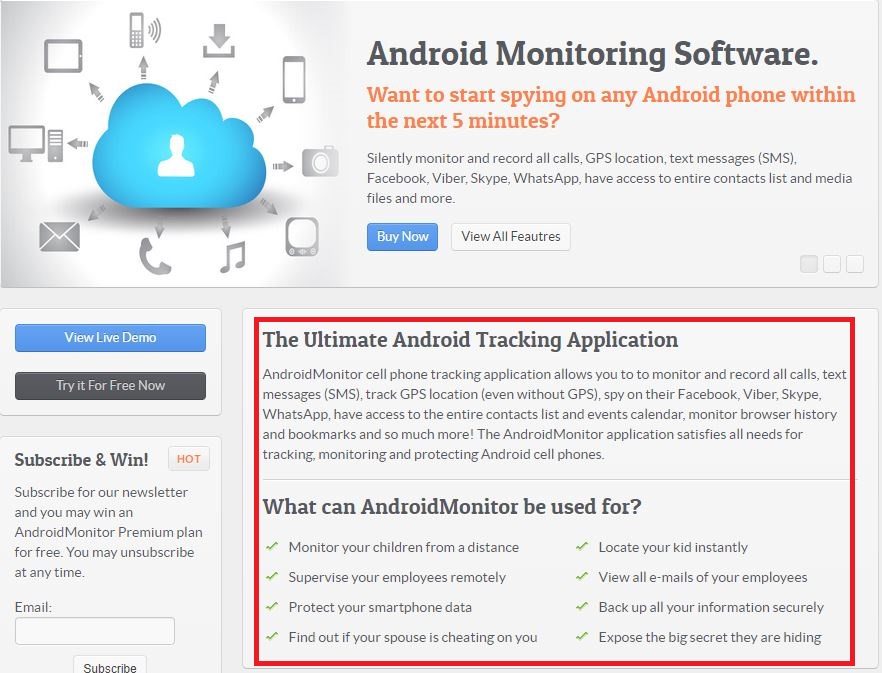
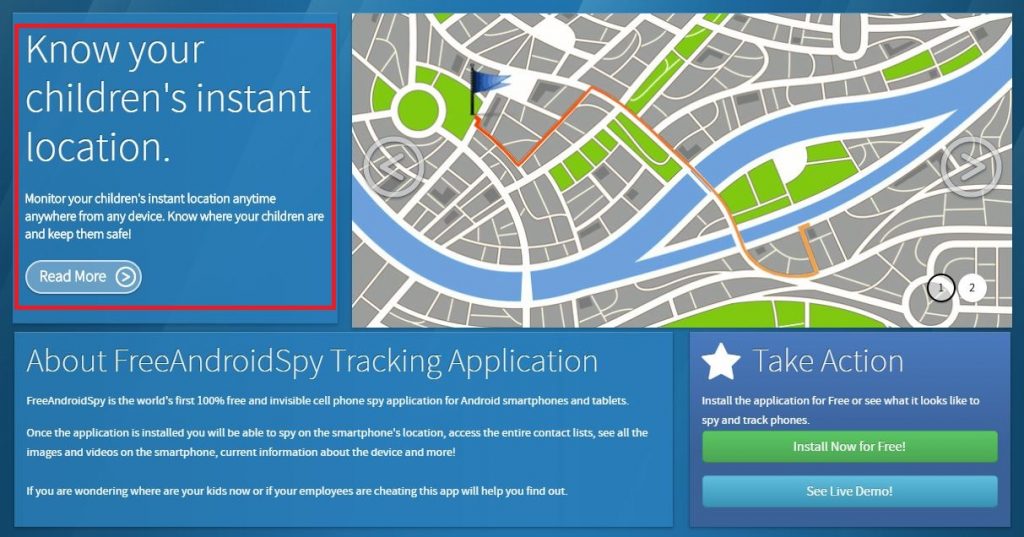
A few deceptive apps are given in Figure 2,3,4 and 5.
Some apps instruct the user to enable “Unknown Sources” on the device and to disable “Google Play Protect”, so as to be able to install and avoid being flagged by a security product.
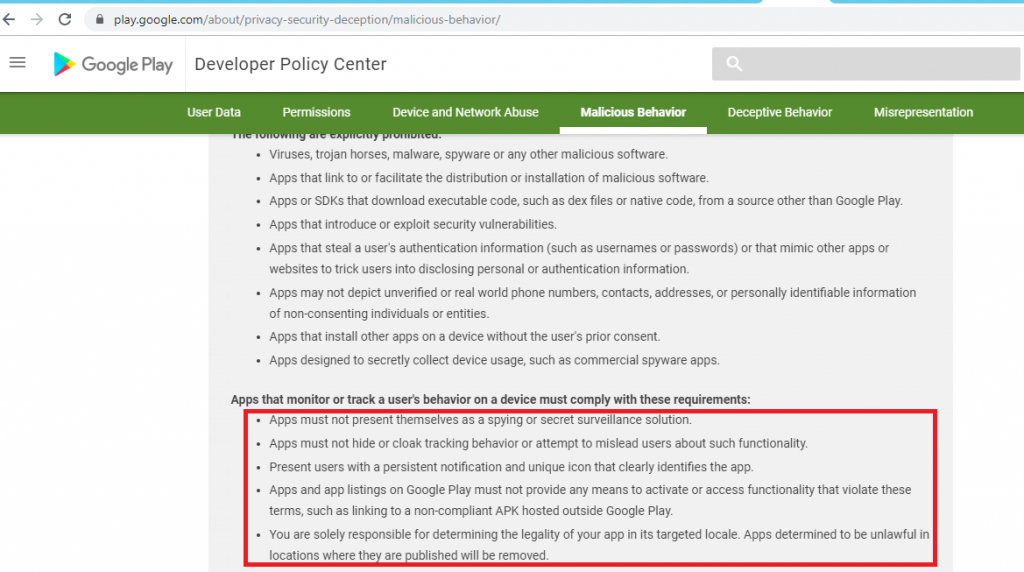
These apps are also seen to violate Google’s Security Policy as shown in the Figure below.
We also noticed that even though many stalkerware apps were removed from the Google Play Store, as mentioned earlier, there were still a few stalkerware apps remaining on the store. For example, EaseMon iSpy Tracker, a parental monitoring app was still available on the Google Play Store as shown in Figure 7. However, at the time of publishing this blog, we noticed that the app has subsequently been ejected from the Google Play Store.
The detection details are as below:
File name: iSpyTracker (com.aws.ispytracker.apk)
Md5: 6FD9B156316F6AF6C134A0763F731278
Detection name: Spyware ( 00557f6c1 )
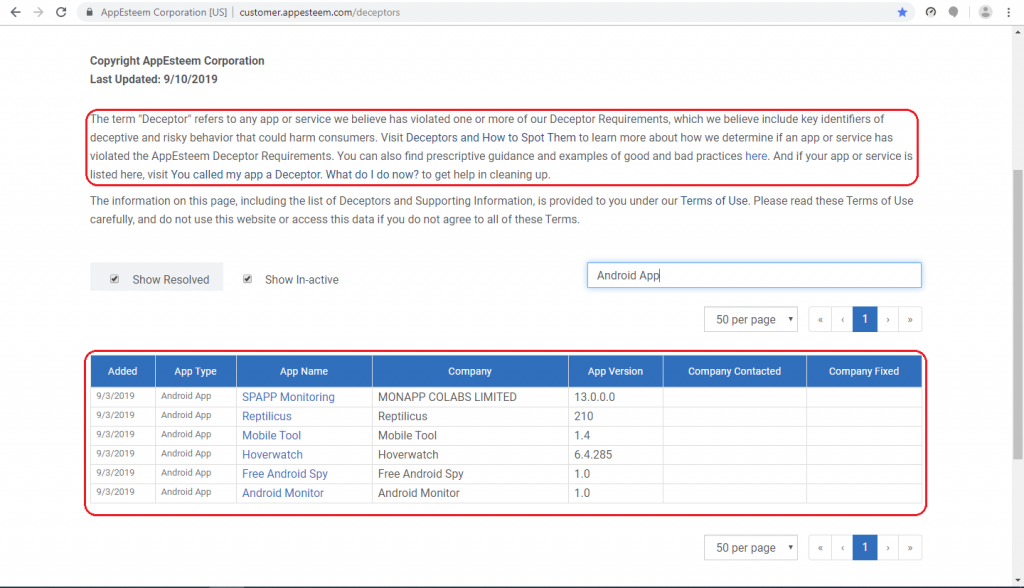
AppEsteem, a US-based certifier of apps across platforms, publicly classifies these apps as deceptive, if they violate any of AppEsteem’s deceptor requirements. The app type could be Windows, macOS, Chrome extensions, Affiliates, Download Sites, call centers and, most recently, Android apps. These deceptive apps and deceptor violations are shared with cybersecurity vendors and the world at large.
Tips to stay safe
- Lock your device by ensuring you set a PIN, pattern or by using biometrics.
- Never leave your device unattended.
- Ensure your OS is up-to-date with the latest security patches.
- Install a reputable mobile security product such as K7 Mobile Security and ensure that it is kept up-to-date.
Indicators of Compromise (IoCs)
| App Name | Hash | Detection Name |
| SPAPP Monitoring | 3745E46C14664AEBC8D3D28271F74D91 | Trojan ( 0054fddb1 ) |
| Reptilicus | 8B58CFA79D7A6BA7D95CC0CA7FBB6C06 | Trojan ( 00557ad51 ) |
| Mobile Tool | CFFE2E8644383FA355B8BAC993590B54 | Trojan ( 0054e9761 ) |
| Hoverwatch | 0213169357EFFA5C8BAEC66806318D4A | Trojan ( 00557ad61 ) |
| Free Android Spy | 803EC87ED407BDD67EBE7B0671FFCC15 | Trojan ( 0054e9761 ) |
| Android Monitor | AB80B7240696CCB7DC676CD141C81752 | Trojan ( 0054e9761 ) |