DLL Side-Loading has always been a thorn for AV products from the time it came to existence. It is so reliable that it quickly gained popularity among threat actors thereby increasing the number of attacks using the same. In recent times, Chinese APT groups have been leveraging DLL side-loading techniques to orchestrate ransomware attacks. In short, DLL side-loading is a technique that uses malicious DLLs which look legitimate and relies on legitimate executables to load these DLLs without proper checks and execute them.
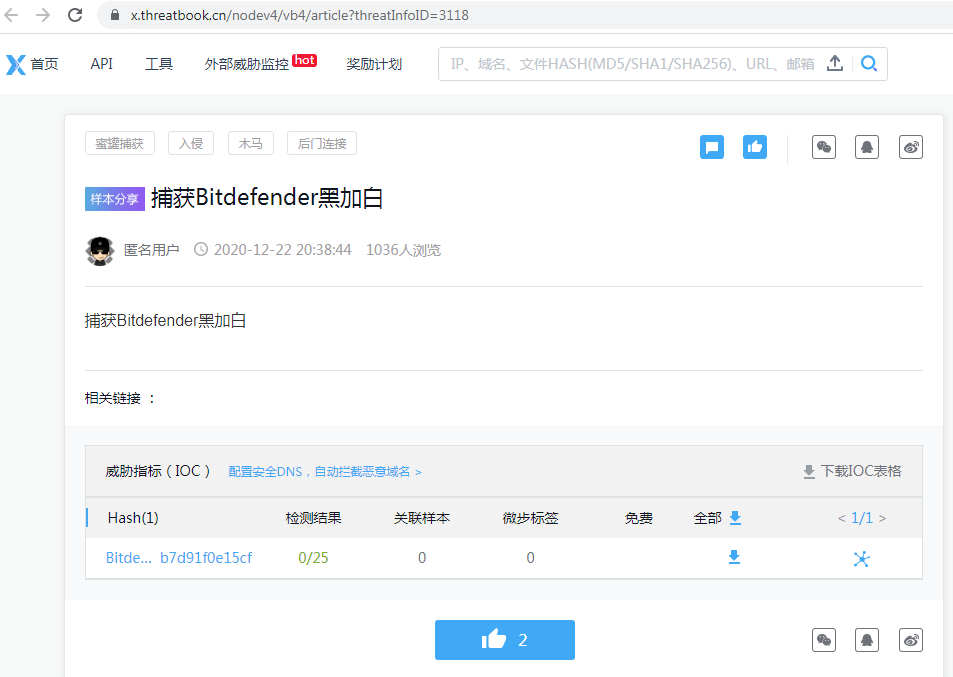
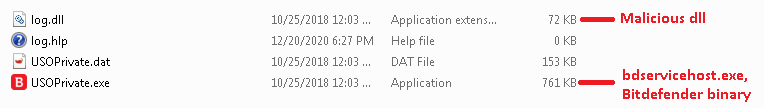
Following this trend, we recently came across a zip file submission in threatbook.cn with the title “Bitdefender” as depicted in Figure 1. When unzipped, the folder has four files among which is a legitimate Bitdefender 2019 binary, vulnerable to DLL side-loading and a log.dll which is a malicious DLL loaded along with the Bitdefender binary when executed as depicted in Figure 2.
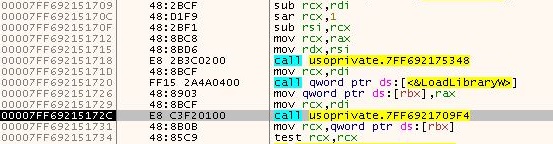
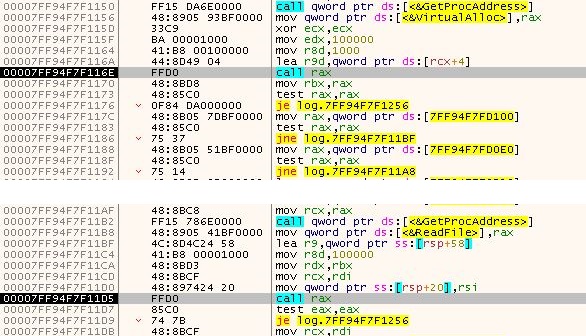
The binaries found in the zip archive are 64-bit files and when executed, the bdservicehost.exe named as USOPrivate.exe loads the log.dll using LoadLibraryW API as depicted in Figure 3.
First of all, the log.dll retrieves the function like VirtualAlloc, ReadFile, VirtualProtect using the LoadLibrary and GetProcAddress routine. Then it allocates space using VirtualAlloc API as shown in Figure 4. Using ReadFile API it reads the encrypted content from file USOPrivate.dat and moves it to the allocated space and changes its characteristic to executable using VirtualProtect API.
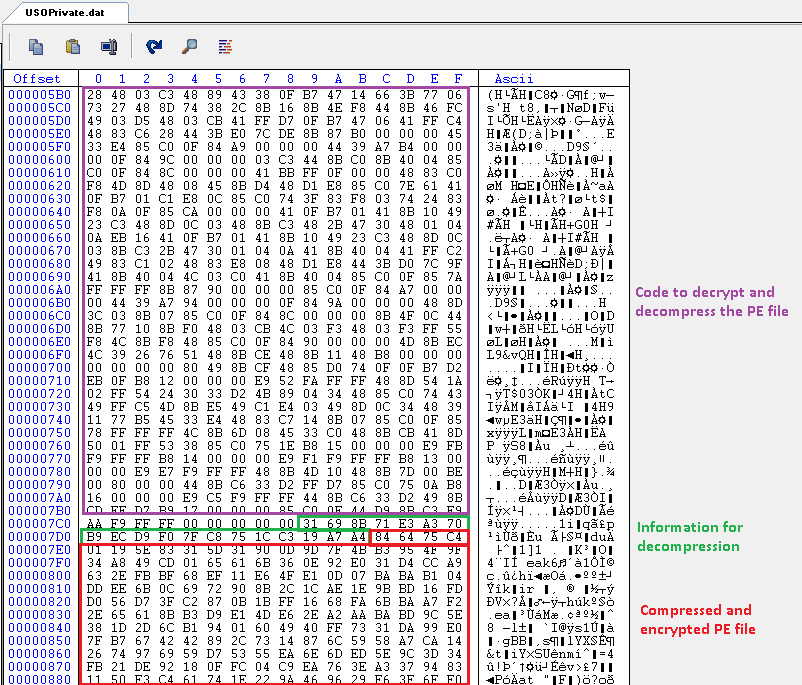
The content of USOPrivate.dat has two parts as described in Figure 5. Byte 0x0 to 0x7c8 has the code which is responsible for decrypting and decompressing the fully functional PlugX RAT PE file which is present in the second part of the file, that is bytes after 0x7c8.
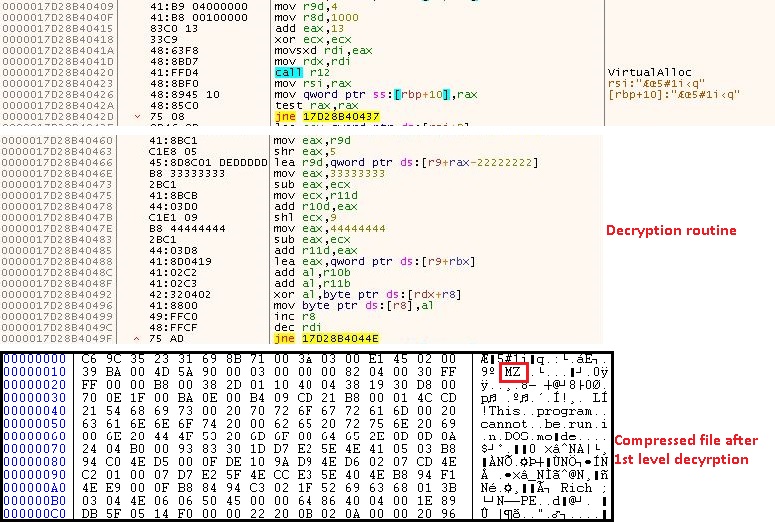
The flow is transferred to the first part of the code by log.dll. The first step is to retrieve the API function used in the code by using GetProcAddress routine. Then it allocates the memory using VirtualAlloc API and decrypts all the bytes after offset 0x7c8 as depicted in Figure 6.
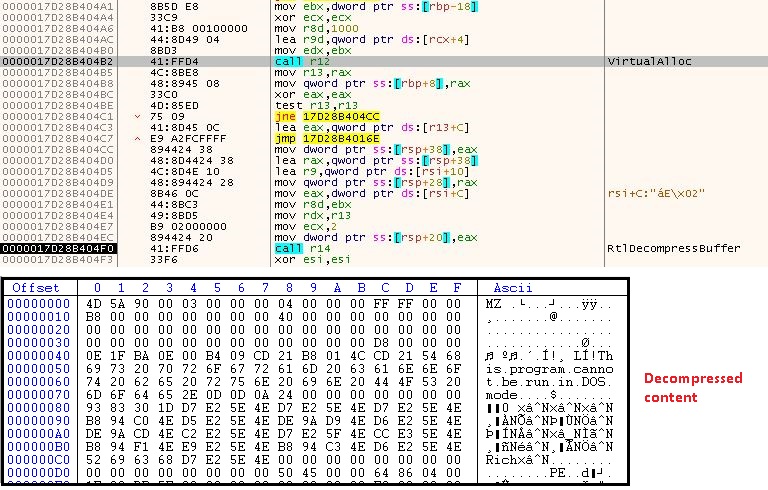
Then it again allocates a virtual space to decompress the content received after first level decryption by using RtlDecompressBuffer API as depicted in Figure 7.
The PE file received after decompression is a fully functional PlugX RAT and the C2 contacted by the PlugX payload is caonimade[.]11i[.]me as depicted in Figure 8.
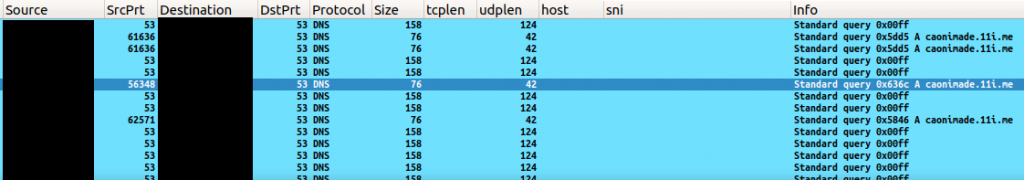
PlugX RAT
PlugX is a fully loaded RAT with functionalities such as upload, download, keystroke logging, collecting webcam information and remote cmd.exe shell which made its debut in 2014 and became famous since then. It is still being used by Chinese APT groups in multitude of attacks where the recent one being the ransomware attack.
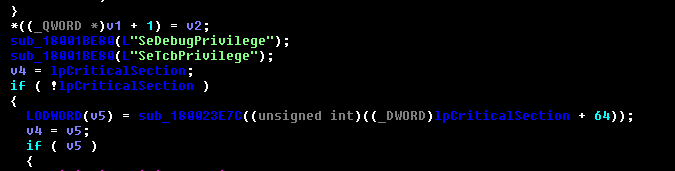
The PlugX checks if it has SeDebugPrivilege and SeTcbPrivilege and if not modifies it accordingly. SeDebugPrivilege is required to debug and adjust the memory of a process owned by another account irrespective of the security descriptor (that is it grants access to a process to inspect and change another process). Process with SeTcbPrivilege is considered as part of the trusted computer base.
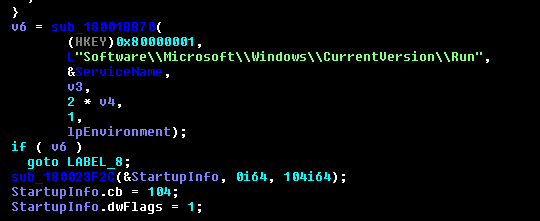
For persistence, it adds Run entry and vbs file in the Startup location.
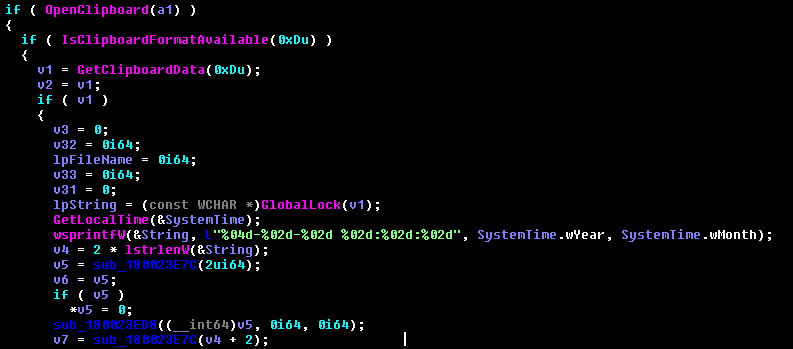
It also checks for clipboard data as depicted in Figure 11 along with the date.
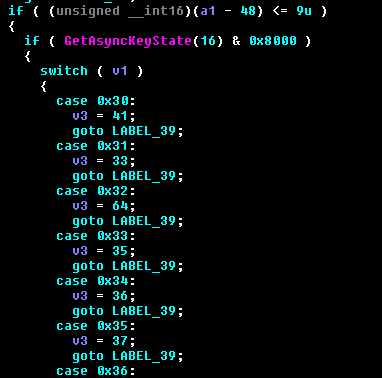
Then it logs the keystrokes. First, it checks the key state using GetAsyncKeyState API and masks it with 0x8000 to see if it is high or low, which is key pressed or released respectively. Here, hex equivalent of 16 is 0x10 which is the SHIFT key as depicted in Figure 12. Then it uses switch case statements to get the state of other appropriate keys.
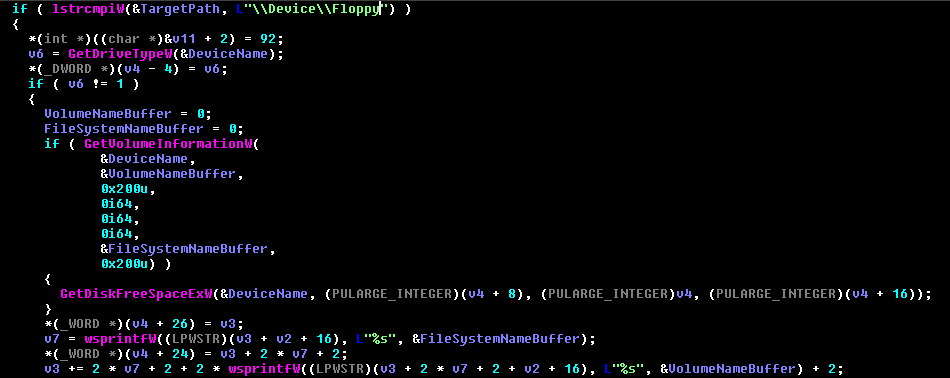
It then gathers information of all the disk space available and also the information of some removable drives attached or plugged in as depicted in Figure 13.
Some of the other functions it can do which is already mentioned in several blogs are process injection to svchost.exe, upload and download files using InternetReadFile, InternetWriteFile, URLDownloadFile API etc., execute remote shellcodes retrieved from C2, gather information about all the running processes in the system etc. On the whole, it has all the functions to take over your system completely.
These kinds of RATs can do heavy damage by themselves and you can imagine how it would be if it downloads additional payload like ransomware, coin miners onto the system. This DLL side-loading technique along with the PlugX RAT are heavily used by Chinese APT groups like Mustang Panda, APT27 and Winnti.
Here at K7Labs we actively monitor such malware and have proactive detection for all these files. So stay safe from these kinds of attacks in this pandemic situation by using a reputed AV product such as “K7 Total Security”.
Indicators Of Compromise (IOCs)
| MD5 | File Name | K7 Detection Name |
| 03797703F999E8E5029EDBEE30446ED2 | log.dll | Riskware ( 0040eff71 ) |
| DDC3BBA6EB84E83822958D0273945C60 | decompressed PlugX binary | Riskware ( 0040eff71 ) |
C2
caonimade[.]11i[.]me