In Feb-2023, Microsoft (MS) patched a vulnerability in Microsoft Word which, if successfully exploited, could allow an attacker to execute remote code without authentication on victims’ machines. This vulnerability has been assigned CVE-2023-21716 and has a CVSS score of 9.8, making it a critical issue. This vulnerability impacted MS word and the Outlook Preview Pane as well. Microsoft along with the patch released a work around for the vulnerability but did not release details about the vulnerability.
While we were analysing to identify what was patched, on 06-March, the researcher who reported the bug released a PoC on Twitter. In this blog, we will be taking a look at some internals of CVE-2023-21716. So far there is no evidence to suggest exploitation of this vulnerability in the wild.
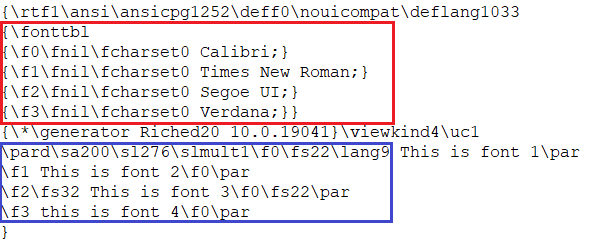
Rich Text Format (RTF) is a document file format published by Microsoft. It uses control words to define various sections and properties of the document. CVE-2023-21716 exists in the way MS Word parses the RTF files. The RTF file structure has \fonttbl control word, which defines a group of all the fonts that can be referred to in the document. These fonts are referred to using the assigned font number \f<num>.
In Figure 1, the part highlighted in red shows \fonttbl control word defined and the part highlighted in blue shows the fonts being referred to in the text, in a regular RTF file.
By providing a long list of fonts to this control word, it is possible to crash MS Word when this specially crafted document is open. We were able to generate a RTF document using the published PoC. As expected, as soon as it was open using MS Word, it crashed.
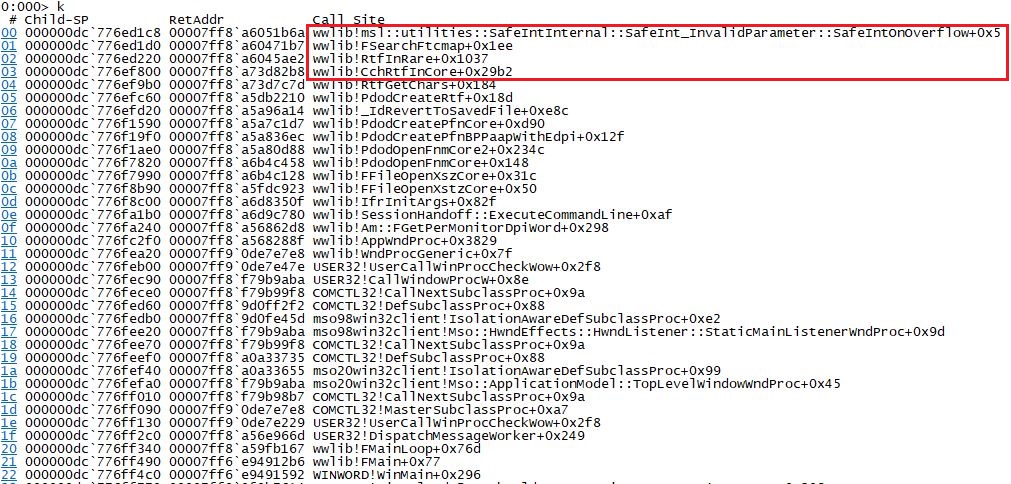
After configuring WinDbg to catch the crash, postmortem debugging, we were able to analyse the crash. Figure 2 shows the stack trace at the time of crash.
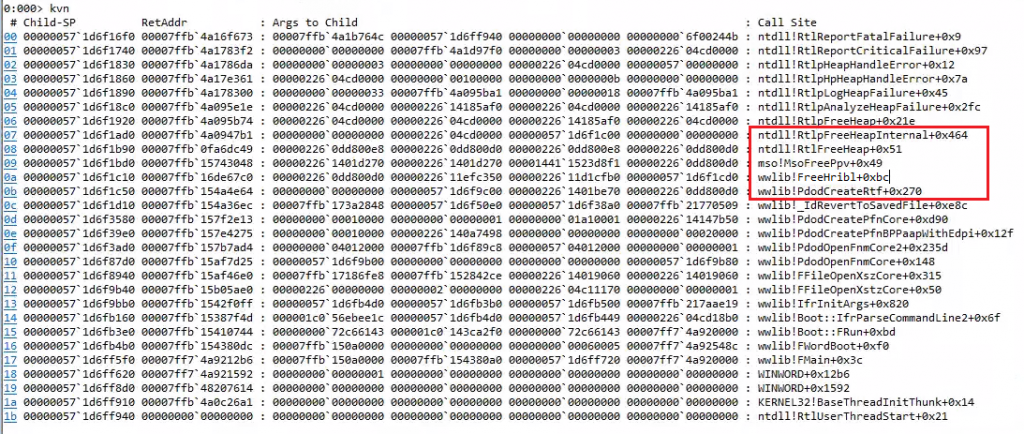
Using the WinDbg crash analysis extension, we observed that this crash is caused due to a heap overflow in the call made to MsoFreePpv() function in mso.dll by wwlib.dll. wwlib.dll is responsible for parsing RTF documents in MS Word.
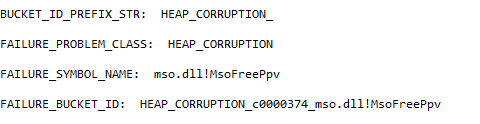
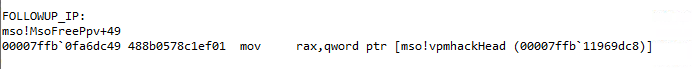
Figure 3 shows the Heap Corruption message displayed by the WinDbg. Figure 4 points towards the location of the crash.
The Patch
As per the details available online by the researcher who reported the issue to MS; the issue was reported in Nov-2022, however, was patched only in Feb-2023. To patch the reported issues, MS has added a function call to SafeIntOnOverflow() from SafeInt class, in wwlib!FSearchFtcmap() function. SafeInt is a class defined to gracefully handle overflows. Figure 5 shows the patch diff of FSearchFtcmap() function in the two versions of the wwlib.dll.
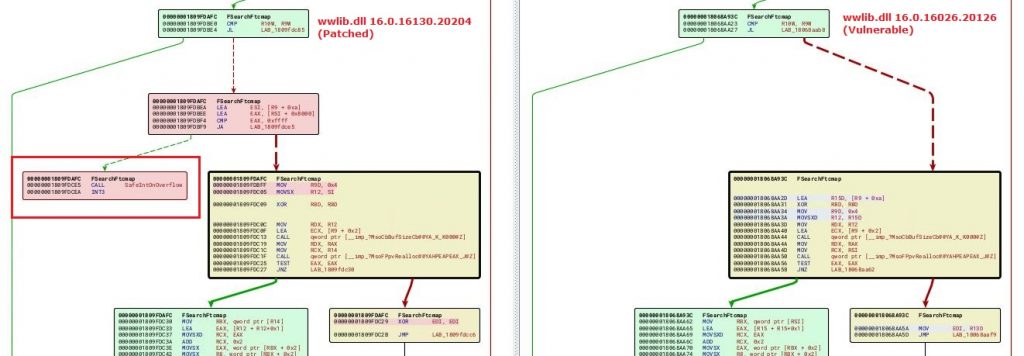
This new function prevents MS Word from crashing. When the postmortem debugger is enabled, it shows that the overflow is caught safely. There were reports that on some systems the patch was not working properly, but we could not verify those claims.
In the last couple of years, with Microsoft restricting document macros from executing to prevent cyber attacks, threat actors have resorted to exploiting vulnerabilities in MS Office – Word, Excel and RTF files. With the publicly available PoC, we believe threat actors might start exploiting this RTF vulnerability to gain a foothold in the target network.
We recommend –
- All users should keep their OS and applications such as MS Office up-to-date
- Use MS Office protected mode to access documents from untrusted sources
- MS File Block policy can be used to block RTF files from unknown and untrusted sources







