Ransomware attacks appear to be ubiquitous. Ransomware is a type of malware which denies access to your computer resources, say by encrypting your personal documents, until a hefty sum is paid to the criminal gang which caused the infection. We recently blogged about two examples of ransomware, namely CTB Locker and TeslaCrypt.
We constantly advise against paying anything to the malware syndicates for two primary reasons:
- Generating income for these cyber crooks would only serve to incentivise their criminal activities, and would fuel their future attacks.
- There is absolutely no guarantee that paying up the ransom of potentially hundreds of dollars would actually restore your files.
In this blog we will focus on the latter point, drawing on a real-life case study involving a friend of mine.
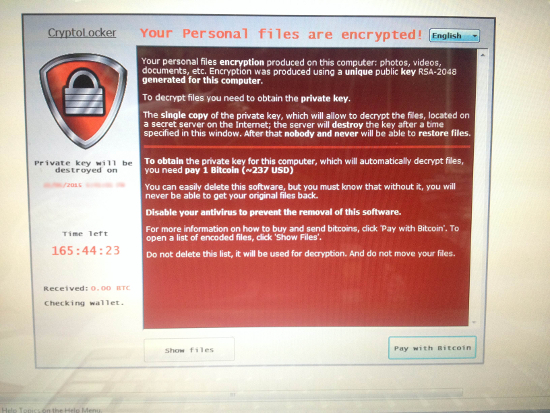
A few weeks ago my friend (not a K7 user at the time) was, unfortunately, struck hard by a ransomware pretending to be the mother of modern ransomware, the infamous CryptoLocker. The above image is a screenshot of the ransom demand which was splashed on his screen. The ransomware was not, of course, CryptoLocker, but yet it was lethal enough, encrypting my friend’s personal files with advanced algorithms. The sample was packed with a custom NSIS SFX wrapper which has been used by CTB Locker in the recent past, suggesting a potential link between the two strains of ransomware.
My friend did not care too much about his local files which were hit. However, as (mis)fortune would have it, his plugged-in external drive containing the early photos of his kids was ravaged. Ransomware tend to enumerate and modify as many target files on as many drives as possible. By targeting personal or confidential files such as images, Microsoft Office documents, etc., the criminal elements increase the pressure to pay up. Even police departments have occasionally felt compelled to part with funds.
Given the importance of the images on his external drive, my friend was prepared to satisfy the ransom demand to the tune of US$ 237; no piddling amount. I had urged him against paying up, arguing the case based on the points made above. However he felt that if there were any chance of getting his kids’ pictures back he would have to give it a try.
A couple of days later, after having secured the requisite bitcoin, the ransomware kicked into action displaying a status bar and claiming it was in the process of decrypting all the files it had encrypted earlier. Many hours later, having left the “decryption tool” to do its business overnight, my friend assumed his files had been restored. However he was unable to open most of the images and the documents he attempted to view. I offered to look at the files at the binary level to determine whether any data could be recovered.
He sent me several example files which were failing to open. My analysis showed that for many files absolutely no attempt had been made to decrypt them since they had no visible headers. In other cases some headers were visible but large chunks of the files remained garbled junk. Such was the extent of the damage to the image files that even clever image-fixing-software was not able to recover anything.
To cut a long story short, despite coughing up more than US$ 237, my friend was yet unable to recover his kids’ photos. The moral of the story is: refrain from paying these nasty criminals in any way, shape or form. They are hardened thieves without any sense of compunction or honour, so please do not be fooled by apparent largesse.
As always we highly recommend taking regular backups of your important files on media which are not constantly connected to your computer (external media and/or on online repositories), thus, in the event of a ransomware attack, you could still have your files without paying the bad guys a single paisa.
Samir Mody
Senior Manager, K7TCL
If you wish to subscribe to our blog, please add the URL provided below to your blog reader: https://labs.k7computing.com/feed







