Kazy Crypter has been sold in many underground forums and markets since 2014. The cost of this crypter averages between 13 USD to 30 USD depending on the number of days it will be used and it is advertised as fully compatible with most of the well-known RATs available in the market such as LuminosityLink, NanoCore, etc. Nowadays, though it’s not used very often, there was a submission of the Kazy Loader module to VT during the 1st week of March along with the source code of Kazy Crypter. This blog gives you the complete analysis of Kazy Crypter and its loader functionalities.
The Crypter was last seen on Hack Forums in 2018 with the price of 13 USD and by 2019 there was also a thread stating that the author doesn’t reply to his email and the crypter hosting site is down.
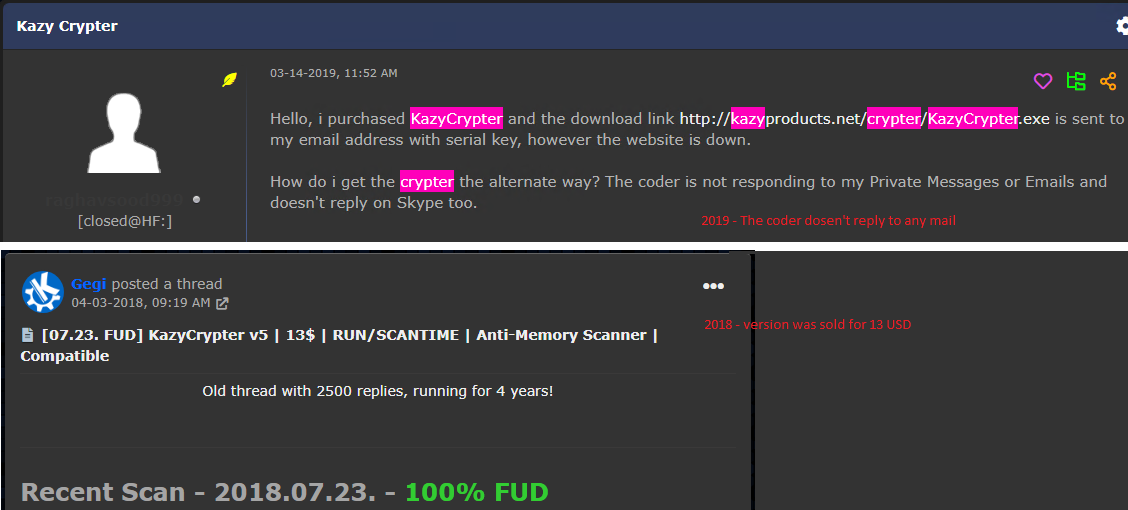
In 2021, the cracked version of the Crypter was seen being promoted in one of the underground forums as depicted in Figure 2.
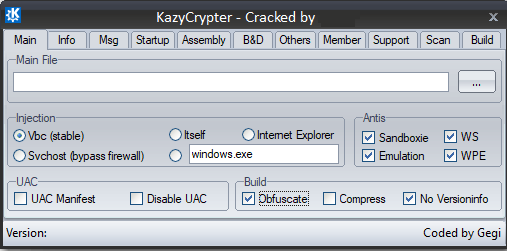
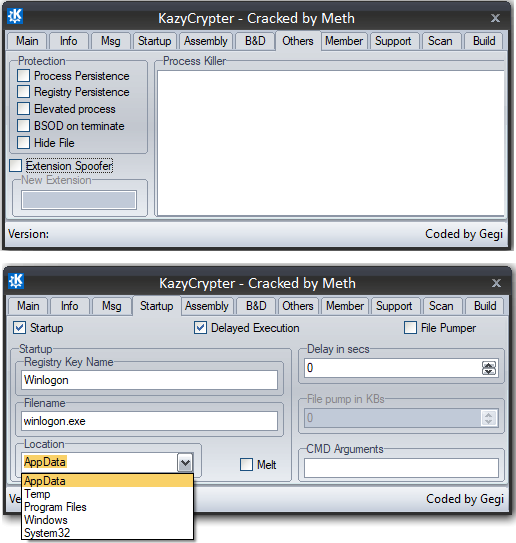
The GUI of the Crypter is quite straightforward and very simple to use. The 1st tab in the GUI has the option to input the file to be compiled with options such as whether to obfuscate, compress the file or use Anti-VM, Anti-Sandbox and Anti-Emulator functionalities as depicted in Figure 3.
Apart from this, it also has a host of other functionalities for process persistence, registry persistence, BSOD on process termination, hiding files, delayed execution, file size pumping with random junk data, start-up location and self-copy to location like %Appdata%, %temp%, Program files etc., as depicted in Figure 4.
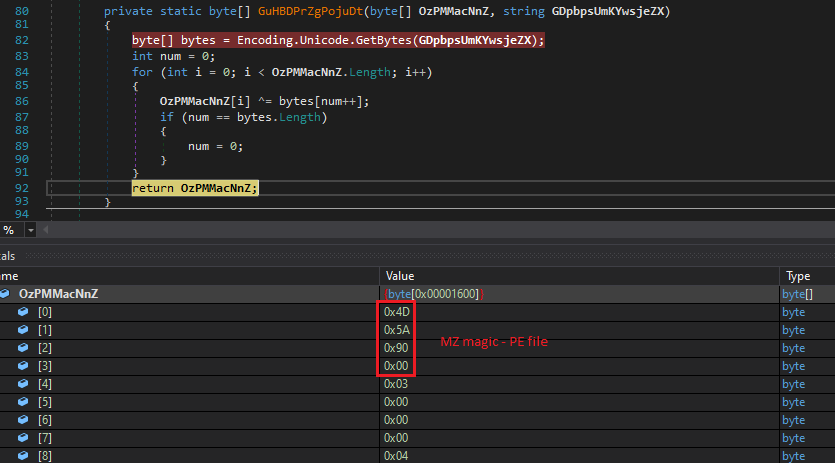
Once the file is built and compiled, we receive a file which is a minimum of 70KB size and varies depending on the functions you select. The 1st task of the binary upon execution is to decrypt the PE loader’s DLL file name Kazyloader.dll stored in an array as depicted in Figure 5.
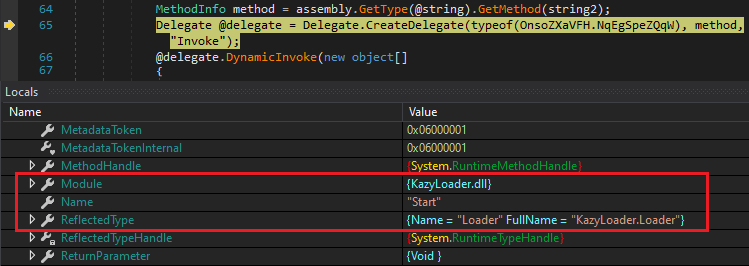
It then creates a Delegate for the function which dynamically invokes and calls the Start function of the decrypted file Kazyloader.dll as depicted in Figure 6. Delegates are similar to pointers in C and C++ functions. It is a reference type variable that holds reference to a method and that reference can be changed at runtime. Programmers often tend to use delegates when they need to pass a method as a parameter of another method.
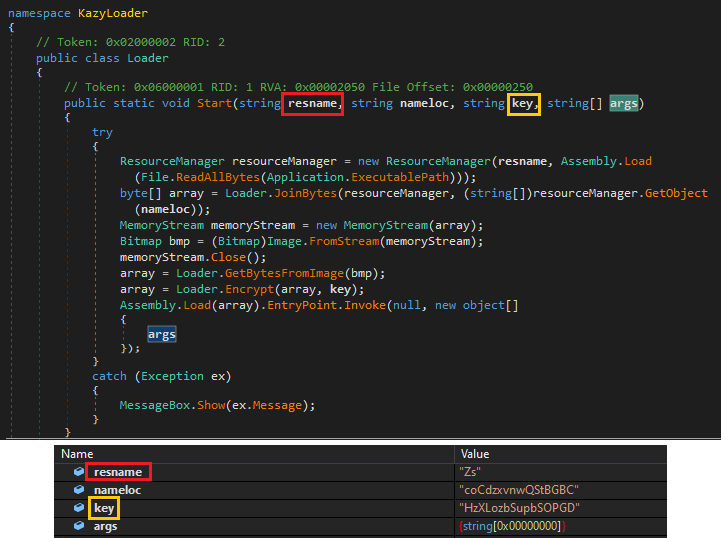
The argument passed to the Start function are
resname – resource name where encrypted content is present as a PNG file
key – decryption key
Args – string array to store the decrypted content
Then it loads the PNG data in the resource and retrieves the required byte from the image and stores it in an array as depicted in Figure 8.
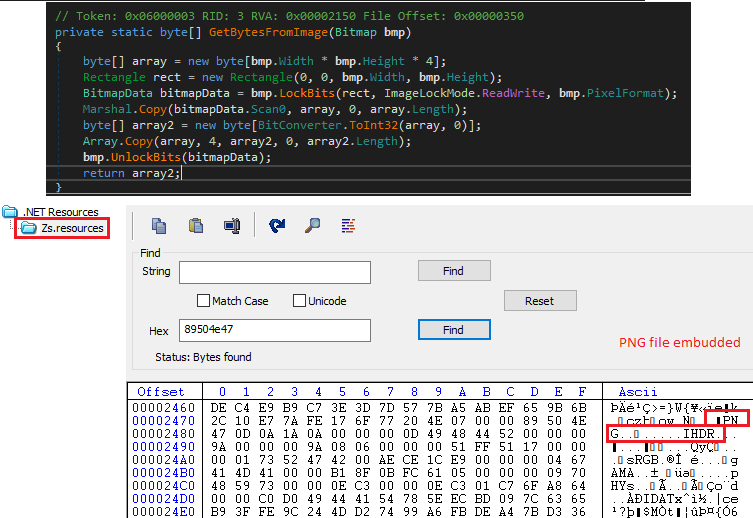
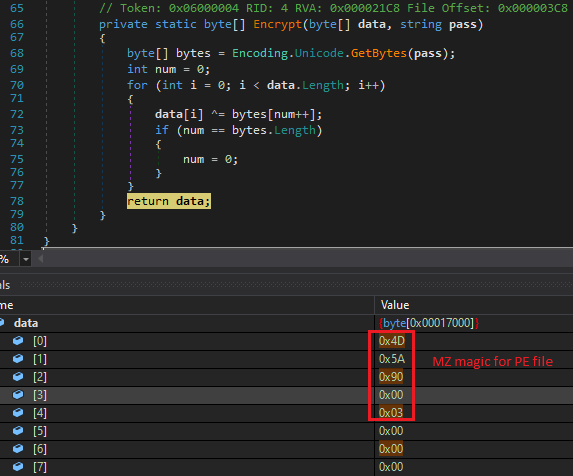
Then it proceeds to decrypt the payload that was compiled using the Kazy Crypter and stores it in an array as depicted in Figure 9. Once the decryption is complete, it then invokes and calls the entry point of the payload to execute the same.
Considering the time when the Kazy Crypter showed up, we can glean that it is pretty old and almost all the AV vendors have behaviour detections. But the fact that it was submitted to VT only recently with the latest compilation time means someone is again working on it or at least evaluating it. K7 Labs continuously monitors such kinds of malware, tools and campaigns to provide effective protection against all of them.
Indicators of Compromise (IOCs)
A1F567E926F1E7E86F1B5176B291368B – Trojan ( 0058f62d1 ) – Kazyloader.dll
C48772ABD1903CDC23258190E9F88730 – Trojan ( 0058f62d1 ) – Kazyloader.dll