Over the past few months we at K7 Threat Control Lab have identified a plethora of security vulnerabilities in Indian Cyberspace.
Incidentally, most of these security breaches were the result of some common mistakes like using vulnerable software components, ignoring vendor security updates, maintaining a weak security policy or mis-configuring security products.
As discussed in a previous K7 blog, such oversights increase susceptibility to security incidents like data loss and malware/ransomware infections on systems/networks. Figuring out the root causes behind such perilous attacks revealed a few interesting statistics (many thanks to Open Source Intelligence aka OSINT).
Here go the key findings from our research.
Insecure Services and Ports
Figure 1 summarizes publicly exposed networking services (such as SSL, SMB, HTTP etc.) and ports throughout the country.
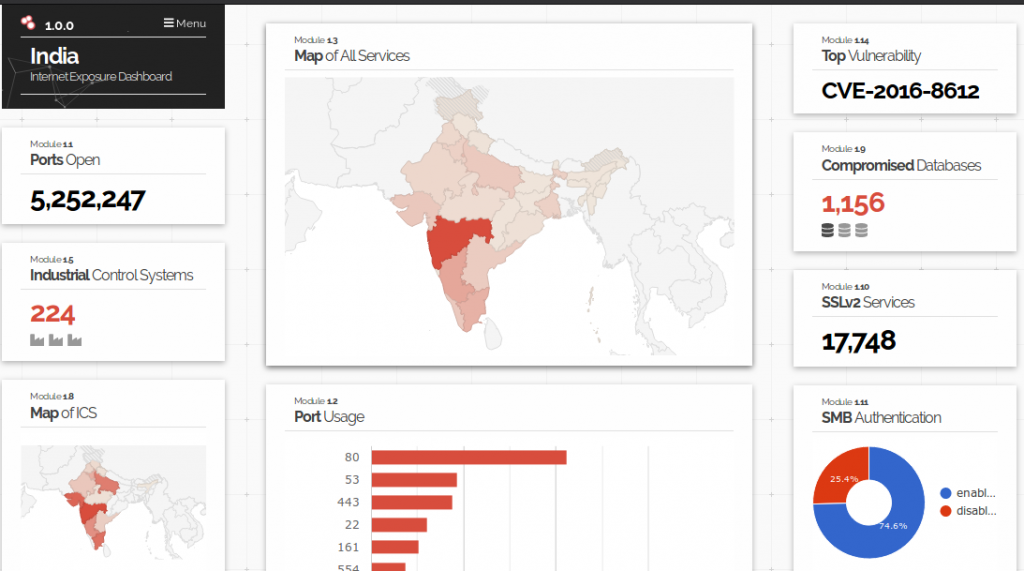
Taking a closer look at the scenario, we found around 1,156 compromised databases around the country putting user data in constant jeopardy. Astoundingly, this number has remained unchanged over the past few months. We couldn’t contact the resource owners as the contact details are not readily available.
HTTP Rather Than HTTPS
Despite HTTPS being available for almost two decades, many web servers still prefer HTTP, thus exposing users’ data to unauthorized access. For the unacquainted, HTTPS piggybacks upon HTTP entirely on top of TLS to encrypt the HTTP traffic.
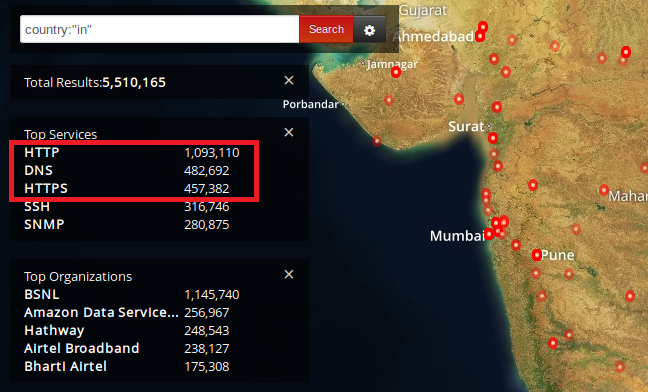
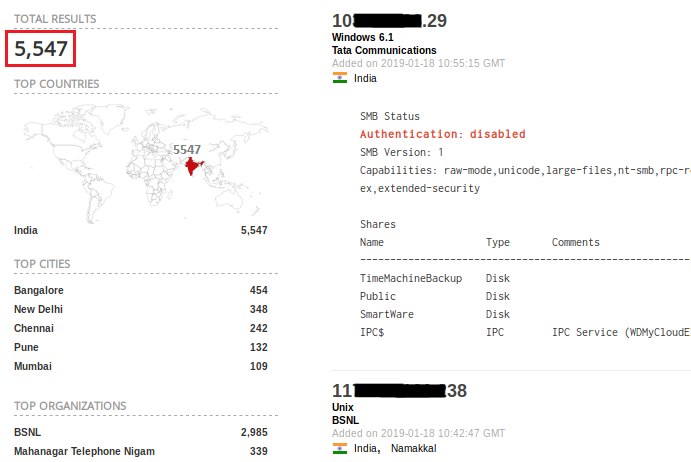
Moreover, domestic port usage statistics explain that port 80 (used by default by plain HTTP) is far more in use in comparison to port 443 (used by default by HTTPS), meaning clear text transmission of user data over the internet can be easily eavesdropped upon by hackers (yes, we acknowledge the fact that there will be some HTTP port redirection to HTTPS).
Figure 2 below displays the exact count of exposed HTTP and HTTPS ports in India. Ironically around 500,000 domestic servers still rely on HTTP rather than its advanced counterpart.
If you are on the list too, we recommend enabling SSL/TLS on your web server immediately. Remember, a web server without enabling SSL/TLS means sending a visitor’s sensitive data (like passwords) unencrypted over a public network. And that allows adversaries in the network or downstream to snoop on the unencrypted data stream between the client and the server.
Query: country:”in”
Remote Administration Services
Let’s move on to the next important security issue, remote administration.
Most corporate networks allow an administrator and a few privileged users to connect to internal servers and machines remotely for ease of troubleshooting and flexible work practices.
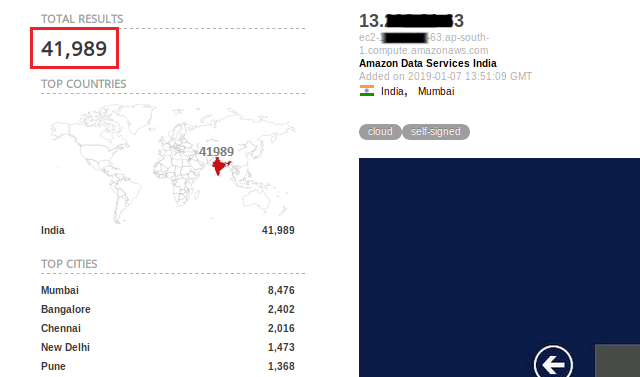
However, a mere fraction of these networks uses an extra layer of security like two-factor authentication or VPN while doing so. Through a query on Shodan, we found 41,989 systems in the country leave ports 3389 and 5800 (corresponds to RDP and VNC services respectively as shown in Figure 3) open without two-factor authentication or VPN, enough for an intruder to get into the network.
In recent months, variants of Dharma & SamSam ransomware have been spotted in the wild using RDP brute-force attacks on weak credentials to get an initial foothold into the system.
Query: country:”in” port:3389,5800
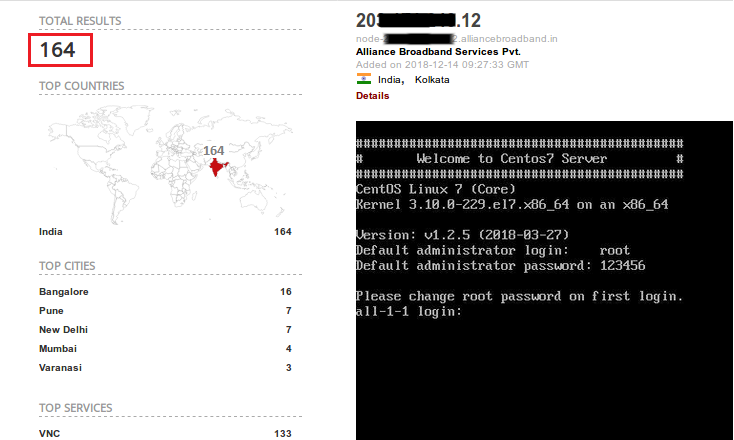
By using more detailed queries on Shodan, we were able to identify servers with authentication disabled for VNC (Figure 4), SMB (Figure 5) and Jetty services. Yes, ‘Authentication disabled’ means a remote user can directly connect to the service and enter the network without requiring any authentication. By reading this definition itself one can understand the gravity of the situation here.
Query: “Authentication disabled” country:”in” product:”VNC”
Samba is a software suite that gives Linux ability to interact using the SMB protocol.
Query: “Authentication disabled” country:”in” product:”Samba”
SMB v1 Ports
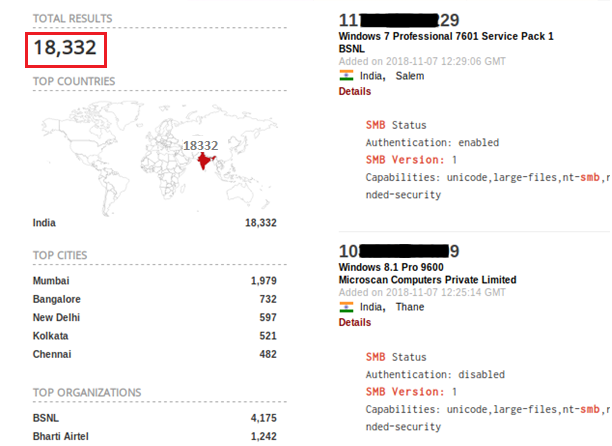
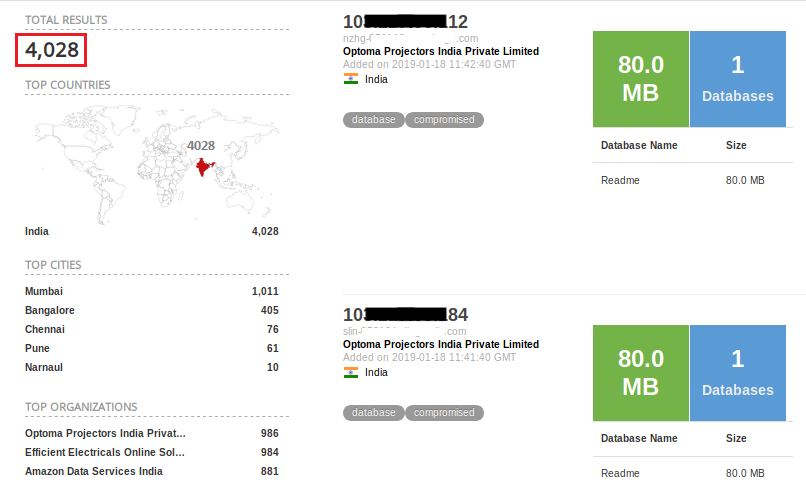
Remember Wannacry? The worst ransomware of 2017 which affected more than 200,000 systems around 150 countries. With the level of chaos it created all around, anyone would expect IT admins to disable SMB v1 ports exposed over the internet. But in reality, unfortunately, there are roughly 18,000 devices in India with SMB v1 ports still exposed online (Figure 6).
Query: port:445 “SMB Version:1” os:Windows !product:Samba country:”in”
Crypto miners like pyromine have also be identified using SMB vulnerabilities to spread.
Apache Server Manager
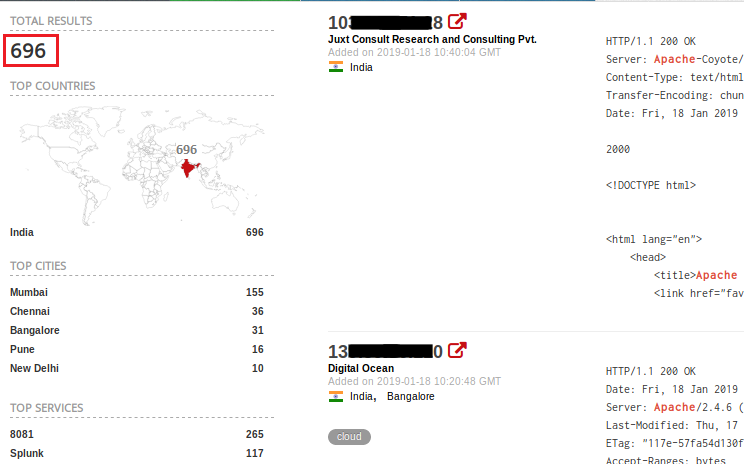
We have seen a few incidents where the attacker was able to get access to a publicly-exposed Apache server by brute-forcing a set of credentials. Searching for a similar pattern, we were able to get 696 default Apache server manager portals exposed to the internet (Figure 7). Having an effective IDS/IPS system in place can alert and prevent such credential brute-force attacks.
Query: country:in and “/manager/html/” and “apache”
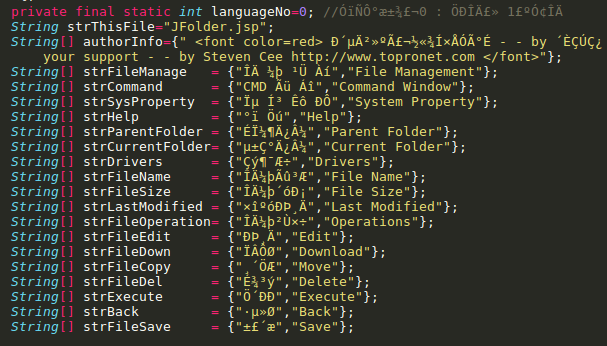
Adversaries brute-force credentials for Apache server manager logins and upload a web shell to gain and maintain access to server resources post a successful attack. Figure 8 shows a snippet of an open-source web shell found uploaded on a compromised server following such an attack.
Printers
Recently, an ardent fan of Pewdiepie defaced more than 50,000 internet connected printers worldwide to help the YouTube vlogger encroach upon the top spot. The incident was enough to alert various organizations to rethink their system security on the Internet.
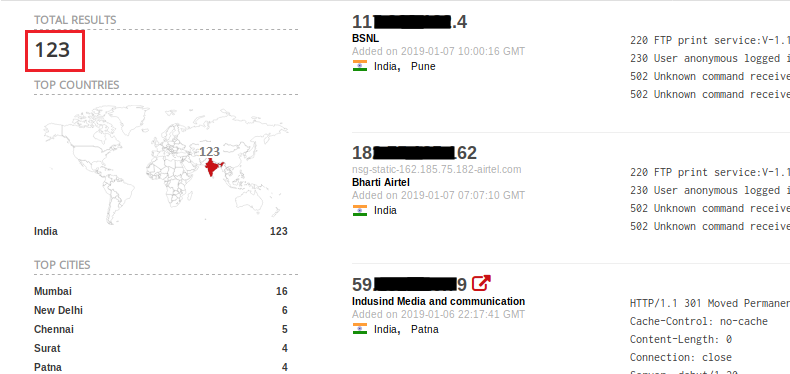
A little over a month after this, however, many users still seem unaware of the risks. Through a query we found 123 printers are still directly reachable over the internet (Figure 9).
Query: country:in device:printer
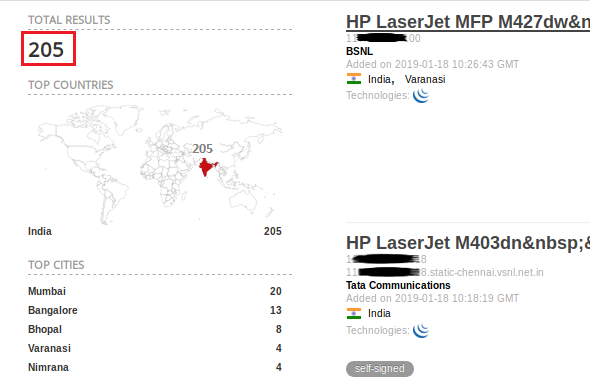
Using a more specific search query, we were able to gain access to the unauthenticated interfaces of 205 HP LaserJet printers exposed to the internet (Figure 10). Among others, HP printers count is at the top of the list. Such insecure interfaces may give information about printer status and internal network configuration to help understand an organization’s internal network.
Query: Server: Virata-EmWeb/R6_2_1 country:”in”
Many Internet of Things (IoT) devices, such as printers, lack essential security features to protect them against cyber threats which, at times, makes them the weakest link to be exploited in the attack chain.
Databases
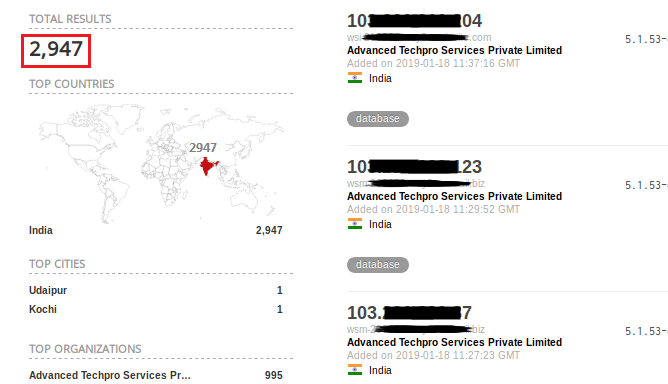
Moving to database technologies, MySQL is still one of the most popular open-source databases around the world. Even in India most of the organizations use MySQL since it is deemed cost-effective and efficient. We found 2,947 systems still hosting MySQL Community Edition 5.1.53 which is vulnerable to a number of remote code execution bugs (Figure 11).
Query: product:MySQL country:”in” version:”5.1.53-community-log”
MongoDB, known for its data storage flexibility, is now notorious for exposing almost 100 million user data records. Besides, in a data breach reported in Nov 2018, around 700,000 records of American Express India customers were leaked due to a compromised MongoDB server.
Query: product:MongoDB country:in
End-of-Support software
IIS
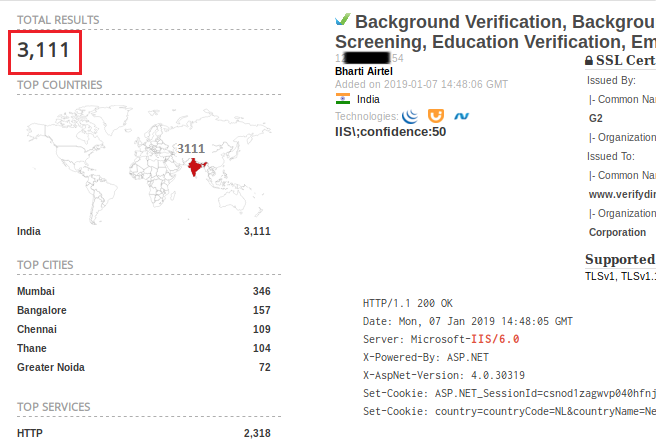
In Sept 2017, two years after Microsoft ditched support for Internet Information Services (IIS) 6.0 and Windows Server 2003, a crypto miner malware was reported in the wild utilizing CVE-2017-7269 to infect IIS 6.0 servers for mining Monero crypto currency. As it turns out, 3,111 web servers hosting applications over IIS 6.0 (Figure 13) are still at large. The scenario hasn’t changed much even after multiple remote code execution exploits reported on IIS 6.0 as recently as 2017.
Query: country:in “IIS/6.0”
Windows XP

Windows XP lost all support from Microsoft in April 2014. Without frequent security updates, Windows XP computers have become much more vulnerable to being hacked.
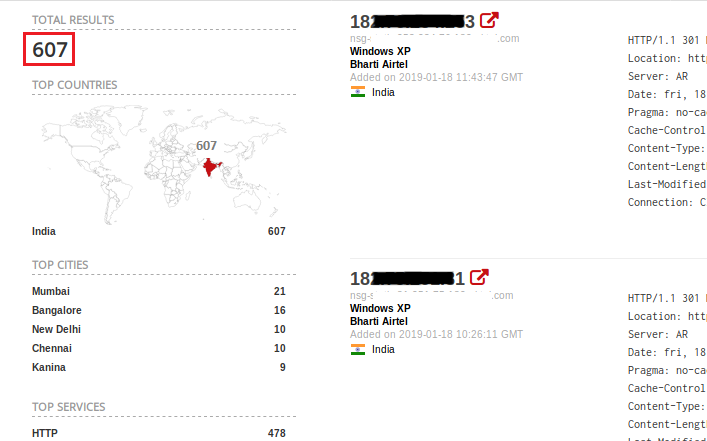
As might be expected, 607 Windows XP computers in India are accessible via public IP (Figure 14). Using Windows XP is a high risk even if the system is in the internal network as malware can pivot to internal networks from other connected infected computers.
Query: country:in os:”Windows XP”
Misconfigurations
Weak or Default Passwords

In August 2016 the world was introduced to the horrorsome botnet Mirai. Its concept was simple; probe device for default credentials; infect it; repeat. It resulted in some of the biggest Distributed Denial of Service (DDOS) attacks we have ever witnessed.
But people have remained the same, boring and predictable. Many users still hate to tax their brain and so continue to pick terribly weak passwords like 123456 or QWERTY, and so on.

Beware, many malware in the wild are more than capable of brute-forcing weak and default passwords existing in routers, RDP services and exposed web servers like Apache.
Cloud Technologies
Adopting cloud infrastructure like Azure and AWS is a super cool, cost-effective measure. But using these with default settings is not.
Around the world, more than a million users’ data has been leaked due to improperly-configured or exposed sensitive keys on these servers. Few notorious vulnerabilities in cloud services are subdomain takeover, bucket listing and improper permissions for the objects.
An OSINT website grayhatwarefare.com has listed the number of AWS buckets that it was able to crawl and the number of files available in each of them (Figure 15). However, this bucket list doesn’t specify the user’s origin, but might consist of Indian users as well.
ElasticSearch
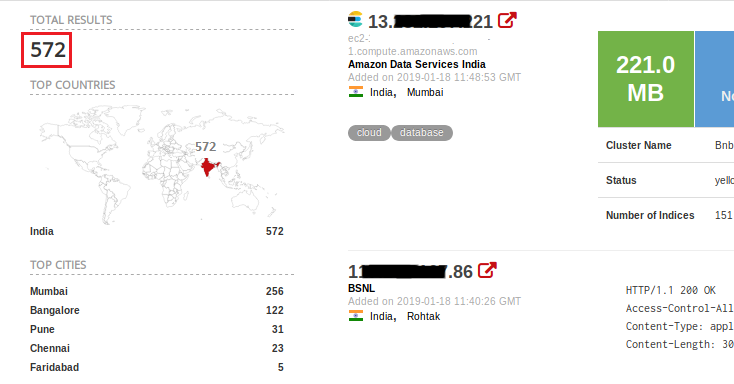
Advanced analytics technologies like ElasticSearch are also leaving an impact on the Indian IT scenario. Earlier this year ElasticSearch (ES) surfaced in the news when its servers were spotted hosting Point-of-Sale (POS) malware in the United States, mostly due to a server misconfiguration issue. We were able to find 572 ES databases exposed to the public in India (Figure 16).
Query: country:”in” port:9200 json
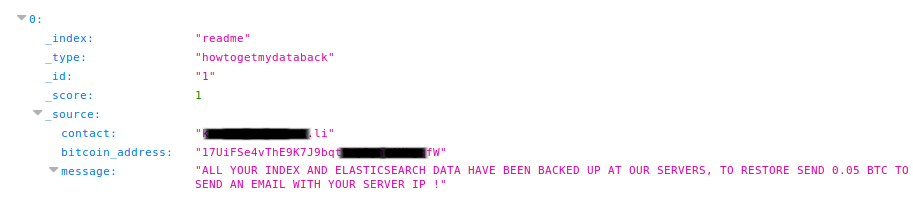
57 million US citizens’ data was leaked very recently through an exposed ES server as it was misconfigured for public access. Apart from the data leak, there have also been a few ransomware incidents. Figure 17 shows one such ransomware incidents we have observed through our intelligence feeds.
Pirated Software

Another major factor that still provides an easy target for malware infections in both consumer and business segments is the use of pirated or cracked OS and software, downloaded from 3rd party sites or torrents which are known to carry bundled malware with them. We strongly advise our customers against using 3rd party activators to activate Microsoft Windows and Office products. Always use genuine software as a part of security best practice.
Conclusion
The vulnerabilities discussed in this blog provide easy ways for an attacker to gain access to critical systems or user databases resulting in financial and other confidential data leakage and loss. Cyber criminals don’t need to search for any 0-days or complex exploits. Attackers are using such OSINT techniques to identify targets with known, common security loopholes, to infiltrate into the network and carry out malware infections. Some of these result in direct access to critical infrastructure as in the case of services with ‘authentication disabled’. For others, a credential brute-force attack or any simple exploit could result in successful unauthorized access to the system.
Indian organizations are quite competent in utilizing new technologies for scaling their business efficiently. But when it comes to security, many of them are still rather clueless, demonstrating weak security posture due to misconfiguration and unpatched hardware and software systems.
In many instances, numerous systems on the network exist without proper security software, making them the sweet spot to the slasher.
Organizations need to identify such weak or less-secured endpoints and ensure they have controls in place to mitigate any attack. Investing in various security products has proven helpful in defending against cyber threats over time but these efforts may be futile if organizations fail to follow security best practices designed to safeguard them.
Security Recommendations
- Establish and maintain a vulnerability management program
- RDP access must only be allowed using secure VPN or two-factor authentication
- Update software and apply security patches on time
- Migrate to the latest product version that is supported by the vendor. Avoid unsupported software versions for any reason
- Properly configure any server, cloud or other infrastructure (like printers or databases) with security and data as the primary goals
- Block unwanted ports
- Uninstall unused software
Image sources: Shodan & Grayhatwarfare.