HTTP vs HTTPS
Both are protocols using which information is exchanged between a web server (where the website you visit is hosted) and a web browser (on your device). HTTP (Hypertext Transfer Protocol) is a widely used protocol for data transfer over the web, but the data exchanged using HTTP is sent as plain data (WYSIWYG), whereas with HTTPS (Hypertext Transfer Protocol Secure) the data gets encrypted using cryptographic methods such as SSL or TLS.
Is HTTPS 100% safe?
The right answer is not all the time!!
Our research shows that cyberattacks employing websites using the HTTPS protocol for communication is increasing day by day.
Why isn’t HTTPS always secure?
Though the website uses HTTPS as a protocol, it secures the information during transport only, not in the server. Even though the mechanism to transfer the information is secure, there is no guarantee about the security of the information being sent once it reaches the server. After receiving the information from the client side, it’s the responsibility of the server to keep the information safe and secure, as there may be cases where the server is vulnerable to other attacks such as SQL injection, XSS (Cross-Site Scripting), CSRF (Cross Site Request Forgery) etc., and your information may not be safe.
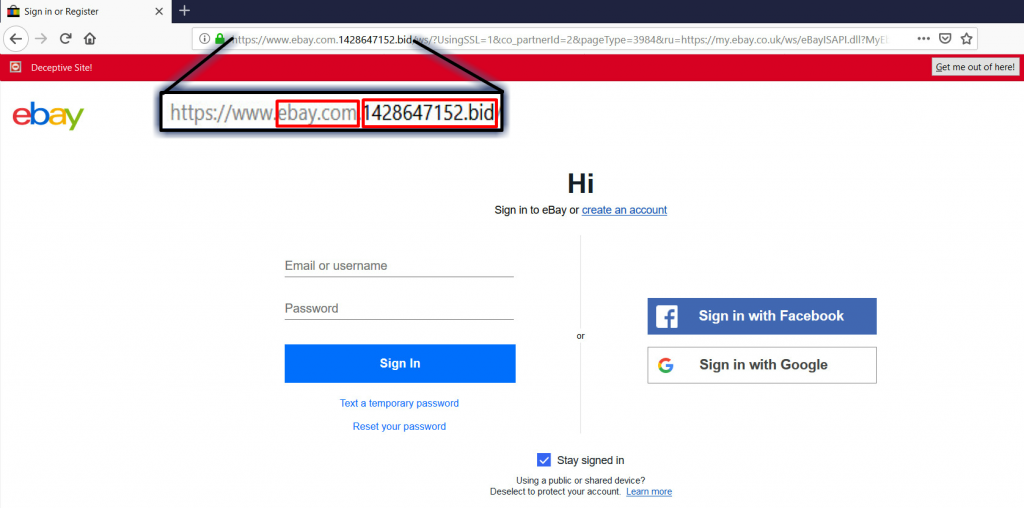
Phishing is still possible with the HTTPS protocol. Let’s take a careful look at an example phishing link for ebay below (legitimate link: https://www.ebay.com/).
Though the address bar for the above URL has a green padlock, meaning that communication with the website is encrypted, and the URL contains ‘ebay.com’, the actual hosting domain name (1428647152.bid) is clearly not ebay.com. As it is owned by the attacker, the confidential information like user credentials in this case, will be received by the attacker. This is just one example to show that HTTPS would not always prevent the stealing of credentials entered by an unsuspecting victim.
Reasons for the rise in the number of malicious HTTPS URLs
- Hosting and SSL certificate charges have become cheap because of which the threat actors easily host malicious stuff on a secure server. Some file hosting services which use HTTPS are free and have been known to host malware.
- The secured website itself has been infected with malware. This is due to the fact that though the communication is secure, the web server may be prone to well-known vulnerabilities like SQL injection, cross-site scripting etc., as merely encrypting network traffic doesn’t prevent a website which is vulnerable to attack from being exploited and compromised to host malware.
- Browsers warn the user whenever they hit a non-secure (HTTP) site. This might induce a level of caution in the user who would then be more vigilant and less prone to social engineering attacks. Hence, malware authors have resorted to hosting their ‘content’ on secure websites (HTTPS), thereby circumventing browser alarms and infecting the unsuspecting user.
Malicious HTTPS trends
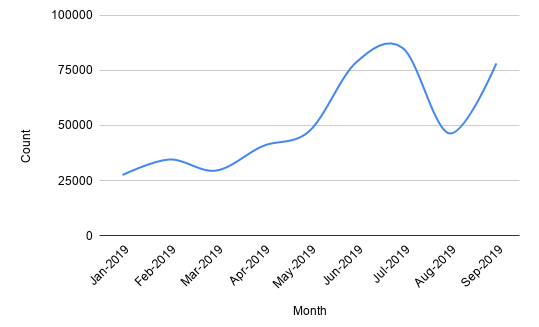
As a cybersecurity company, we handle thousands of malicious URLs on a daily basis. Nowadays, we are seeing a consistent increase in the number of malicious URLs hosted on HTTPS. The graph below shows the number of malicious HTTPS URLs collected over 2019.
There is also an upward trend in the number of malicious HTTPS URLs that are being used by various third-party AV testers to evaluate the web blocking features of all security vendor participants’ products.
Web-based infections are not limited to PCs (Windows OS) alone; Mac, and mobile OS platforms like iOS and Android are also at risk.
Precautions
- Sometimes users throw caution to the wind and go ahead with browsing, even if an HTTPS site has an invalid/expired certificate. This should be avoided especially when confidential data, such as user credentials, have to be transmitted
- When your browser throws a warning of “Connection is Not Secure”, it doesn’t necessarily mean that the site you visited is infected. It’s just a warning that your communication with the site is not through a secure, encrypted channel and is, therefore, vulnerable to eavesdropping.
- Check the domain name before the Top-level domain (TLD) whenever you browse any website. For e.g. in the web address “www.ebay.com”, com is the TLD and the domain name is “ebay” indicating that the website belongs to “ebay”.
- Use a trusted security software protection like K7 Security products and keep it updated.
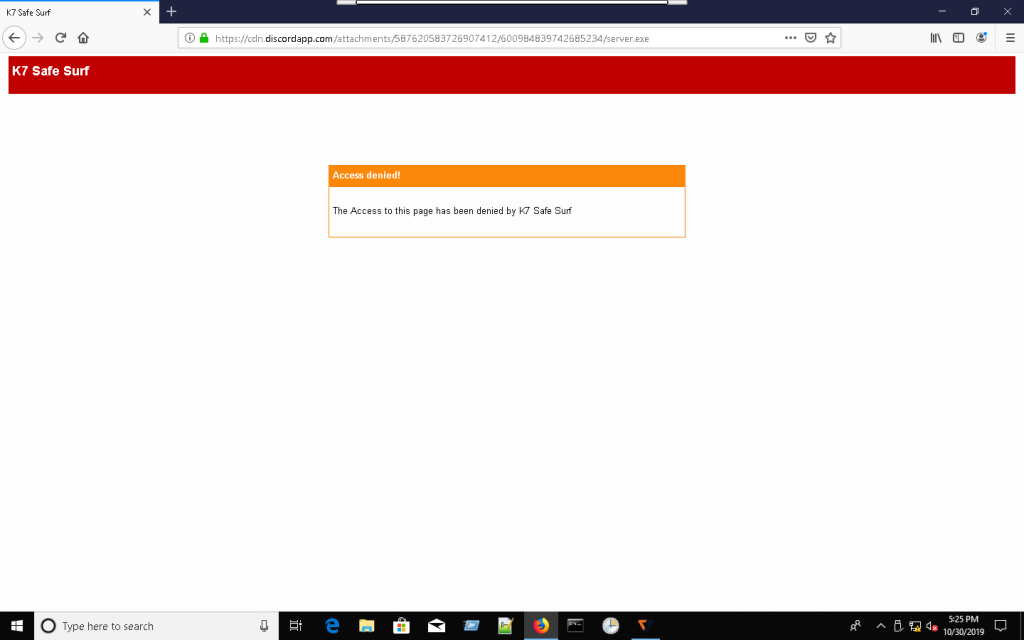
Find an example of how a malicious URL is blocked by K7 Safe Surf below.
Checking the SSL certificate of a URL
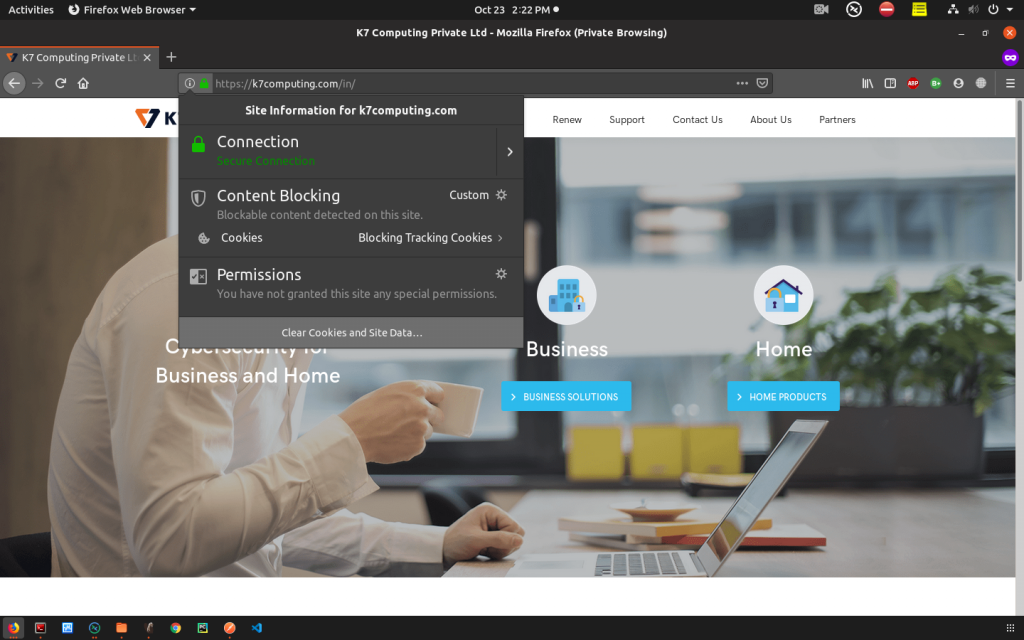
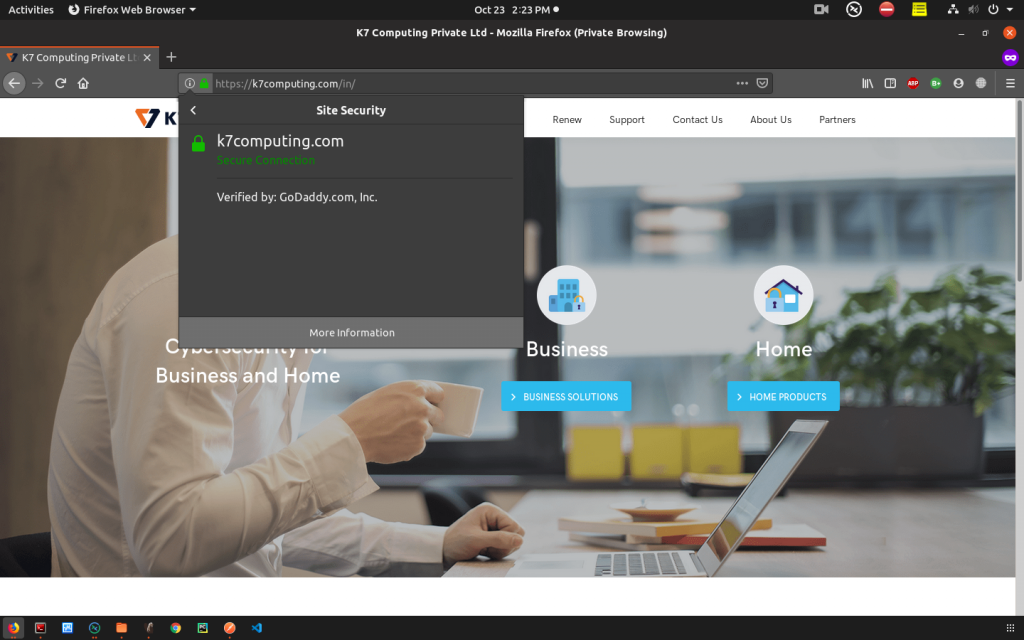
Click on the padlock icon which pops up with “Secure Connection” message as below.
Click on the arrow next to that message to view the detailed information about that SSL certificate.
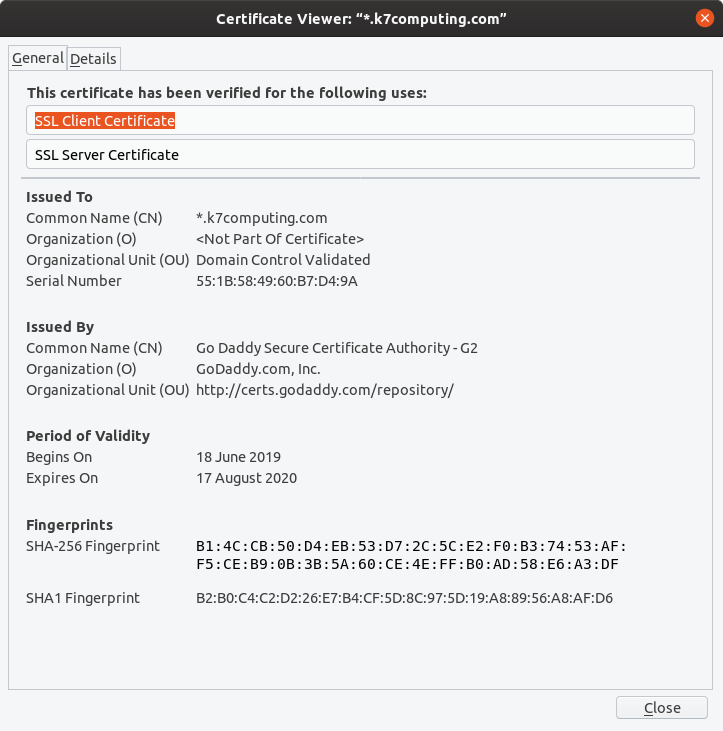
Click on “More Information” which points to the “Security” tab and click on “View Certificate” to view the complete information of the certificate. This window will provide the information of the certificate like Issued By, Period of Validity etc.
Above discussed points should be kept in mind before opening the URLs and providing your Personally identifiable information (PII) online. In this digital era, one needs to keep themselves safe from prying eyes. We also need to understand that a green padlock does not guarantee that your information is safe.