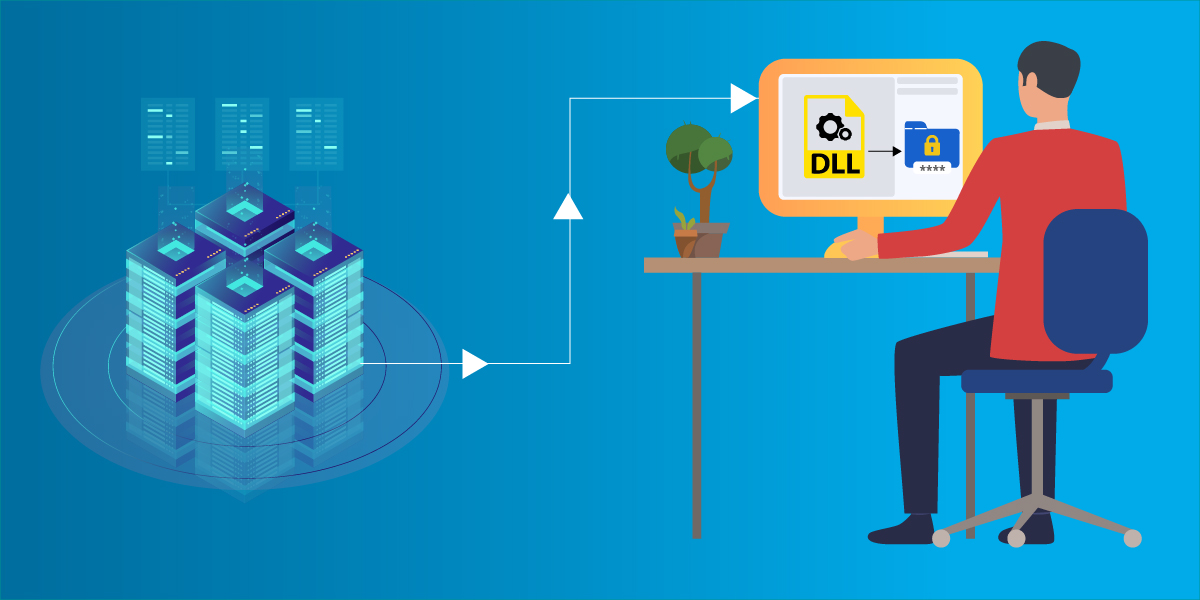
In one of our recent IR case, we found Phobos ransomware being executed using DLL sideloading technique. The threat actors (TA) used a legitimate signed binary WiseTurbo.exe from Lespeed Technology Co., Ltd to perform sideloading of NlogExt.dll. WiseTurbo.exe imports sqlite3.dll, the TA modified the sqlite3.dll’s import table to include an entry for NlogExt.dll with single export function NlogGetInterface.
Thus the initial installer when executed, unpacks all the files onto %TEMP%\Tech tool store\, and executes WiseTurbo.exe, thus loading sqlite3.dll which in turn loads NlogExt.dll in memory and executes the DLLMain. NlogExt.dll on loading, reads the file “CM” which is present in the same directory and contains a shellcode, onto memory. The shellcode eventually leads to the decoding of a PE file in memory and transfers the execution to its Entry point. The PE file allocates a new heap area and unpacks the final Phobos ransomware in memory and executes it. Detailed analysis is given below.
Analysis
MD5: AAA058858261D7C0E73FA1B8264A9A3D (setup.exe)
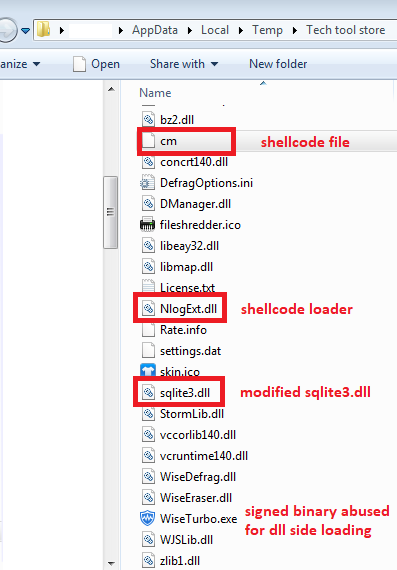
Setup.exe (file recovered from the victim machine) is an installer file, which on execution, unpacks all the files into %TEMP%\Tech tool store\ along with shellcode file “CM”, modified sqlite3.dll, NlogExt.dll and Wiseturbo.exe which is the signed binary from Lespeed Technology Co., Ltd., along with other files which are clean.
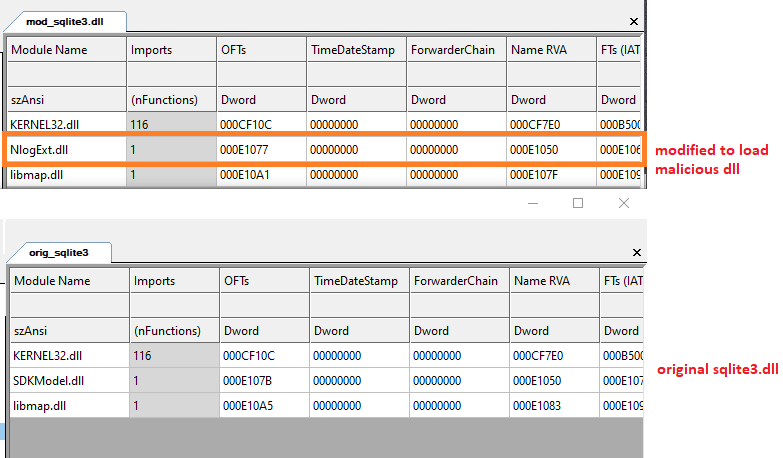
The image below shows the difference between modified and original sqlite3.dll. The TA have modified the import section to load NlogExt.dll.
Once all the files have been unpacked, wiseturbo.exe is executed. Since wiseturbo.exe imports from sqlite3.dll it loads it from the unpacked directory, further now that modified sqlite3.dll is loaded, it loads the DLL NlogExt.dll in memory, thus executing the DLLMain of NlogExt.dll.
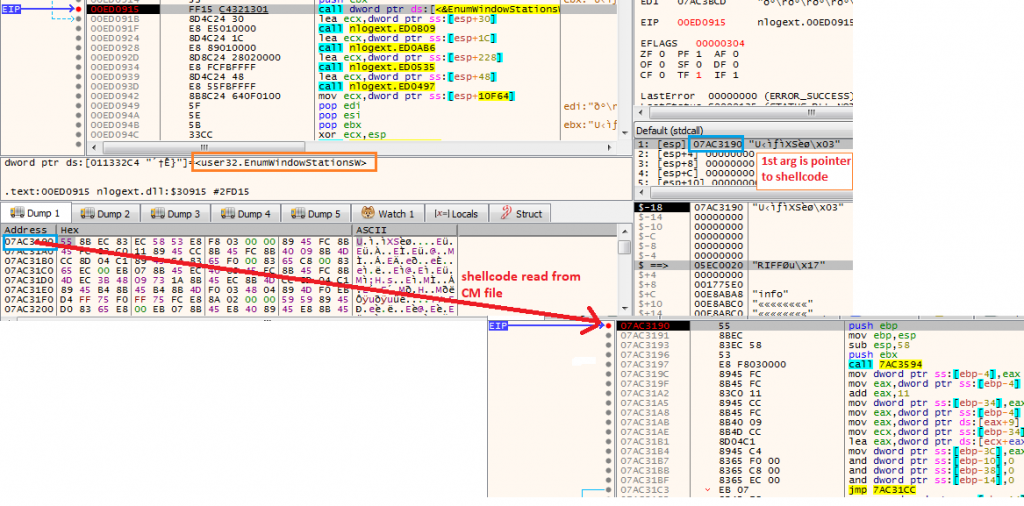
In the DLLMain, a new thread is created to execute the export function NlogGetInterface, it reads the file “CM” from the current directory and maps it into memory. The ‘CM’ file contains a shellcode and an encrypted PE file. The base at which the dll is mapped is saved at offset 0x4b08b from the start of mapped memory. Next it creates a new heap memory to copy just the shellcode which is present at offset 0x4a697 of size 0xA3C bytes. The execution is transferred to shellcode by abusing the windows callback feature, the malware calls EnumWindowsStationsW with a pointer to shellcode as first argument.
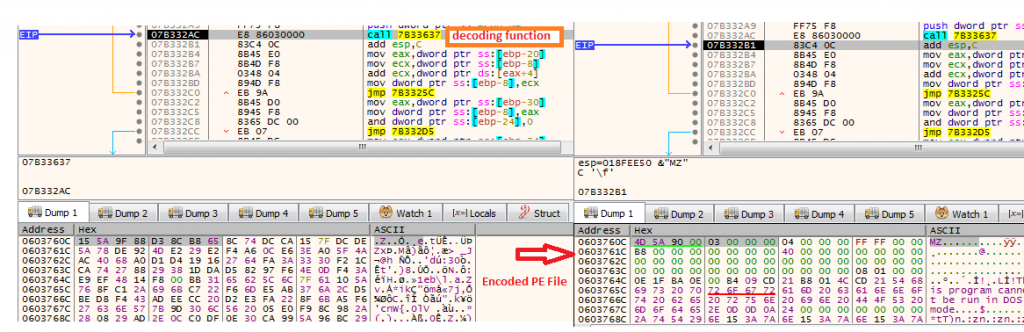
The shellcode copies an encoded PE from the CM File from offset 0x4be9c and decodes it in memory, which is the Phobos crypter.
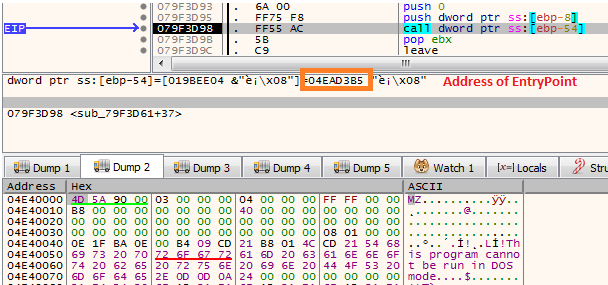
Once the PE file is decoded, the shellcode maps it section by section into the memory and transfers the execution to its Entrypoint.
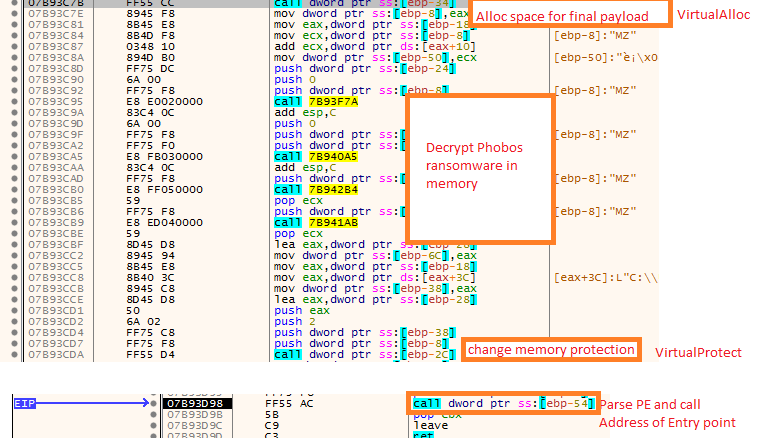
Once the execution is transferred to the Phobos crypter, we can dump the final payload by setting a breakpoint on VirtualAlloc and VirtualProtect. As shown in Figure 7, there are 3 calls made to decrypt the final PE file completely into our memory, Memory protection constants are modified accordingly and execution is transferred to the final Phobos Ransomware. The encrypted files were tagged with the extension ‘.devos’.
We at K7 Labs provide detection against latest threats and also for this Phobos Ransomware. Users are advised to use a reliable security product such as “K7 Total Security” and keep it up-to-date so as to safeguard their devices.
IoCs
File Name | Hash | Detection Name |
Installer (setup.exe) | AAA058858261D7C0E73FA1B8264A9A3D | Riskware ( 00584baa1 ) |
Shellcode Loader (NlogExt.dll) | 1A75878DEA8F5580C25E0B9F1C734949 | Trojan ( 0059e68e1 ) |
Phobos Crypter | 25674F5426C59051960F0D00F06F0B77 | Riskware ( 0040eff71 ) |
Phobos Ransomware | 9DE437C0A1F9E633186F5F631D32AF8A | Trojan ( 0001140e1 ) |