Recently we came across a tweet shared by petikvx. The tweet was on a ransomware family that had the group name similar to the WARLOCK DARK ARMY. The similarities with Chaos ransomware seem to end with the attacker group’s name. Upon analyzing the ransomware from the tweet we suspect both to be very different groups just based on their malware’s attributes.
The sample under consideration was compiled using C/C++, in case of Chaos ransomware it is usually .Net. Statically looking at the file we noticed a resource entry under Bitmap with an identifier “14”, while analyzing the file code we noticed that this resource was read and loaded on to the memory. Hence we decided to dump that resource entry.
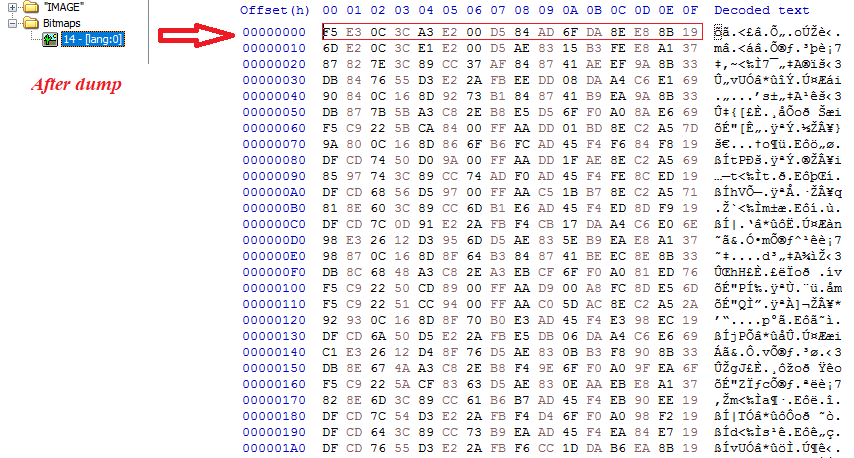
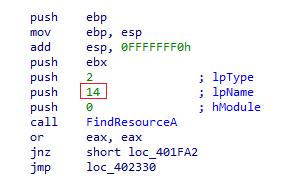
During our code analysis we found this blob was XOR encrypted. The first 16 bytes of this blob acts as the key for XOR decryption and the rest is the data which plays a key role in this ransomware’s infection/encryption mechanism. Shown below is the code that does the mentioned activity.
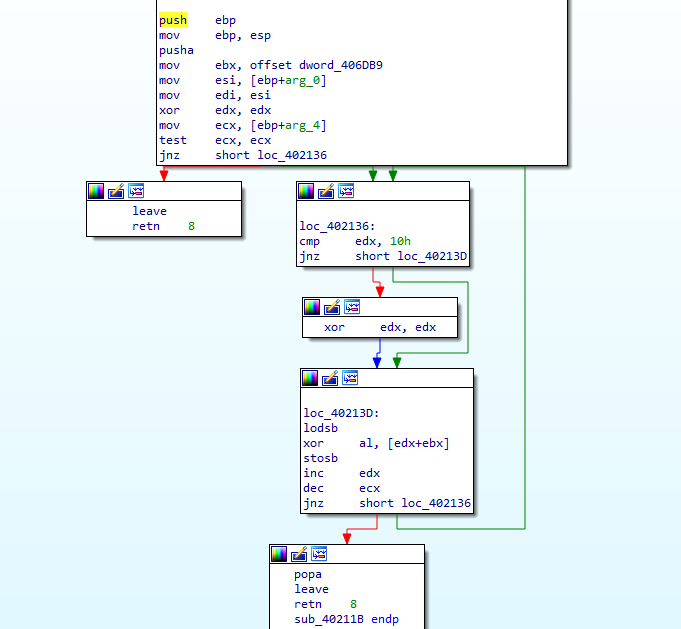
We used CyberChef to decrypt the data from the resource blob. Shown below is the decrypted content of the blob.
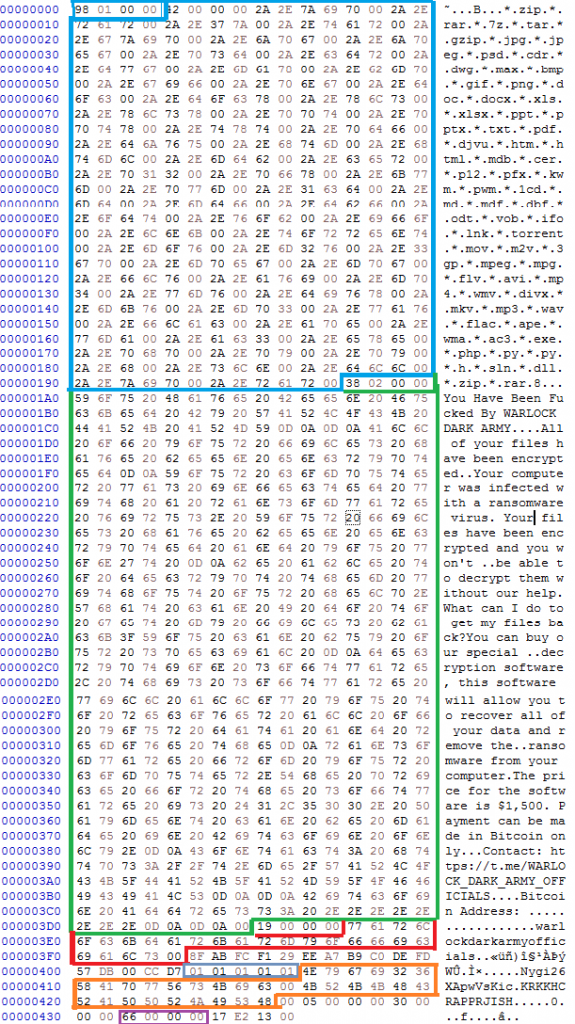
At first glance it is evident that this data blob contains information that is used during the ransomware encryption process, like list of extensions to look for and the ransom note etc. Here the first DWORD which is highlighted in BLUE denotes the size of the data block that follows, which are relevant extensions to look for encryption. The DWORD is little endian, denoting that this block is 0x198 bytes.
At the end of this block of data is another DWORD, highlighted green, which has the size of the next block of data holding the ransom note or the content of the readme text (0x238 is the number in little endian). The next DWORD highlighted red represents the extension of the files after encryption, which is “.warlockdarkarmyofficials”.
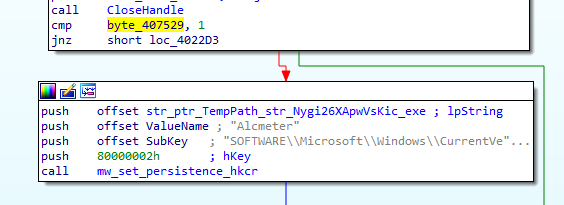
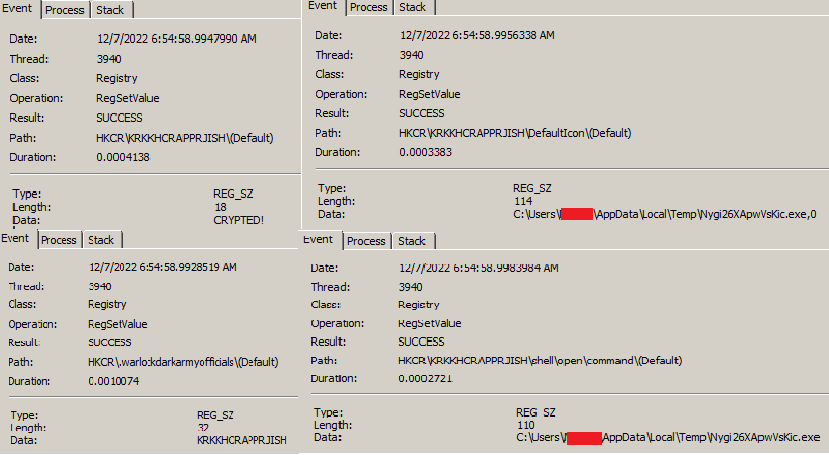
After 0x10 bytes there is a value 01. If 01 is present then the below HKCR entries are written to the Windows Registry. The ransomware sets an entry under HKCR with the key name “KRKKHCRAPPRJISH”, highlighted orange. There are Shell->open->command entries under this key which defaults to the malware’s self-copy location. Mostly done to set default icons for specific file types.
The DWORD highlighted in purple denotes the number of bytes to skip when the malware starts to encrypt a file, 0x66 bytes in this case.
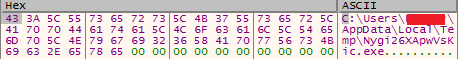
After execution it copies itself with the filename of “Nygi26XApwVsKic” to the temp folder.
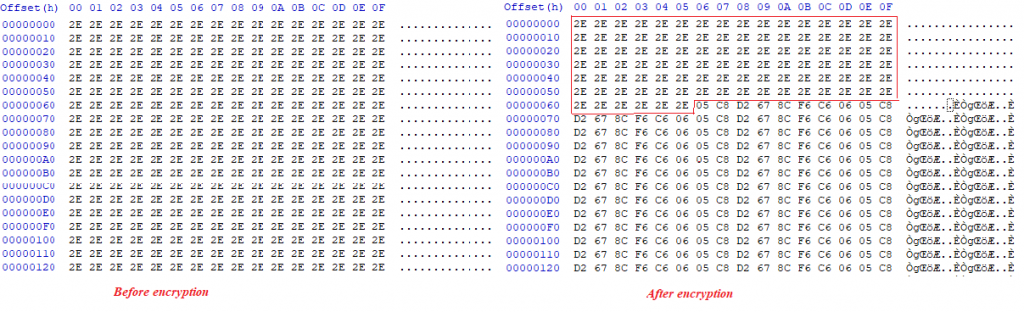
It then sets persistence via the run registry.
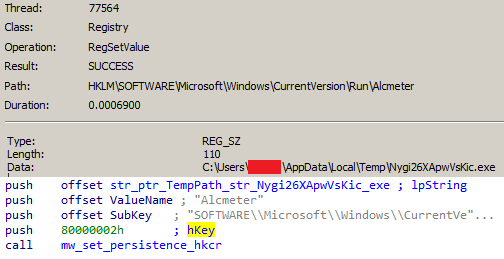
The algorithm used in this malware is “Tiny encryption algorithm”. This is one key difference between Chaos and this ransomware, Chaos uses AES.
After the encryption of all the files, it leaves a ransom message as shown below:
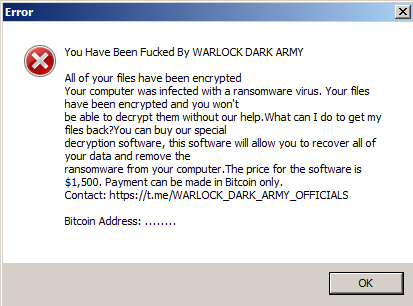
In the above message the actors have not mentioned any cryptocurrency wallet’s address for making the ransom payment, they have however mentioned a Telegram channel for the payment and decryption, it goes without saying that one should not attempt to pay up the ransom to get the files back.
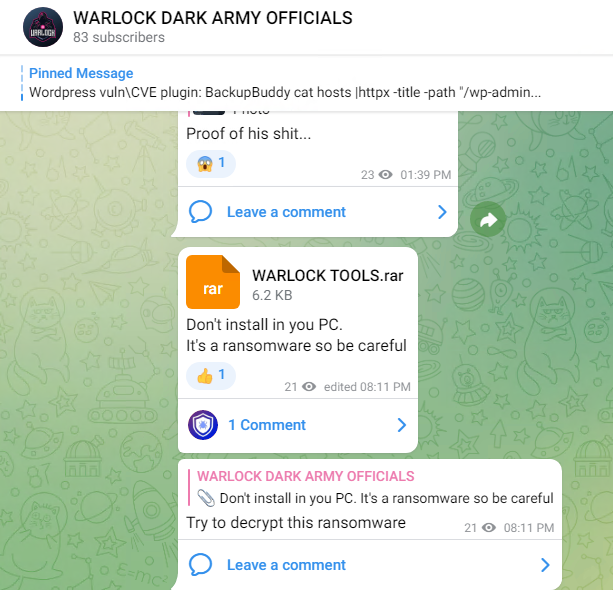
This Telegram channel also acts as a marketplace for malware distribution, apart from being used as the payment channel.
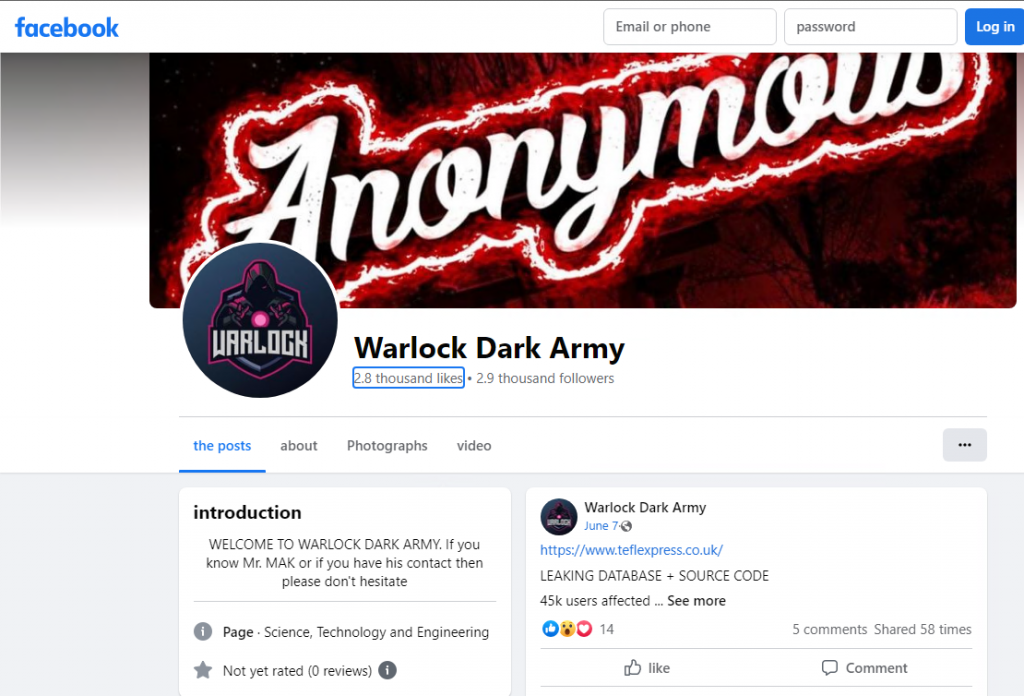
This group had their social media pages in Facebook and Instagram as well, but were taken down. Shown below is the Facebook page of Warlock Dark Army, one can note the identical profile pictures though (Ref. Telegram group profile pic and Facebook profile pic). The similarities are only in the naming and the images, but based on the TTPs we can say that both are unrelated.
We at K7 labs provide detection against such threats. Users are advised to use a reliable security product such as “K7 Total Security” and keep it up-to-date so as to safeguard their devices.
IOCs
Hash : f0979d897155f51fd96a63c61e05d85c
Detection name : Ransomware ( 005451b81 )








