Remote Access Trojan (RAT) is a type of malware that, as the name suggests, can remotely access a victims’ system after successful infection. This blog is about one such RAT, RomCom RAT which can take complete control of a compromised system by spoofing and deploying fake versions of legitimate applications on the victims’ system to gain initial trust.
Let us get into the details of one of the samples which drops a malicious RomCom RAT binary. This sample was digitally signed by Noray Consulting Ltd. On further analysis, we observed that Noray Consulting Ltd had a dummy LinkedIn page and a dubious website to deceive the victims.
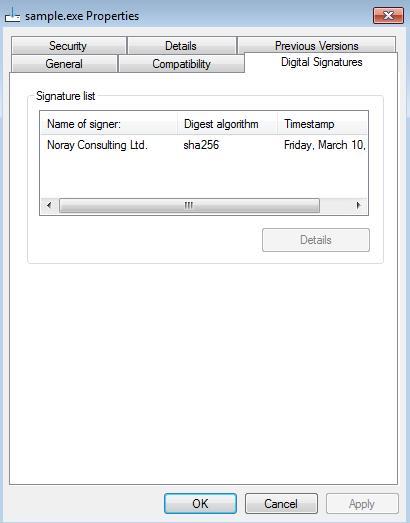
Figure 1 shows the digital sign and the name of the signer.
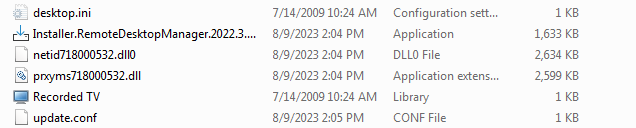
It was observed that the setup file drops RomCom files in C:\Users\Public\Libraries. We observed that all DLLs dropped were VMProtect’ed files.
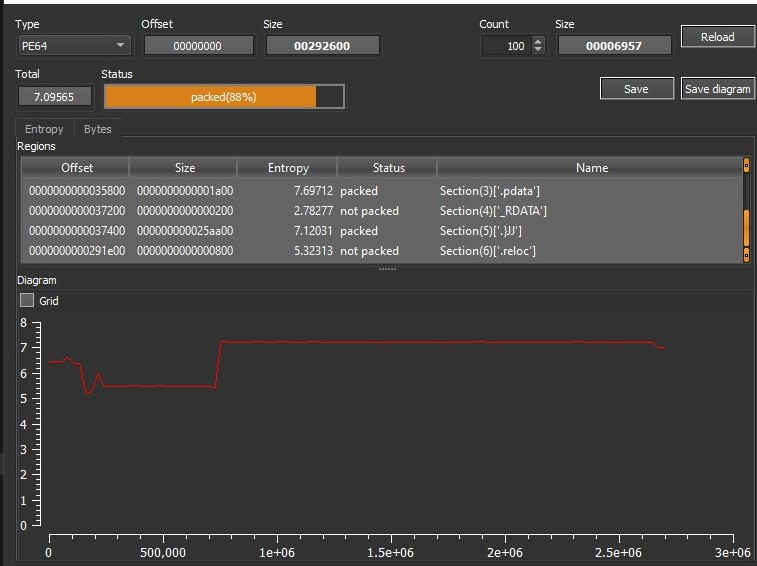
From Figure 3, we can see that the dropped file netid7*.dll0 has high entropy and is a VMProtect’ed file.
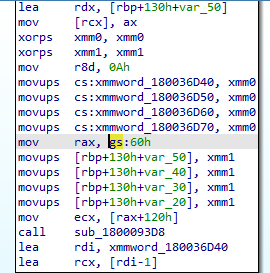
Here we can observe that the malware accesses the Process Environment Block (PEB) using gs:60h, after getting access to which, it checks for the OS Build number using rax+120h
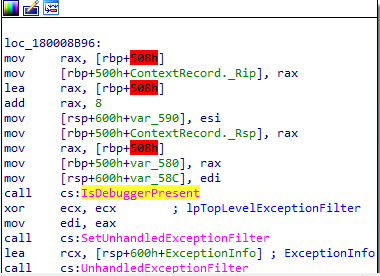
Then the current process is checked if it is being run under a debugger.
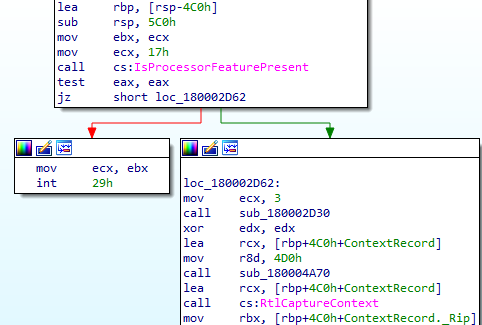
It then uses IsProcessorFeaturePresent, the argument 0x17 is passed to check if the __fastfail option is available or not.
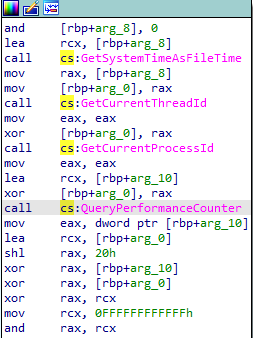
Here, QueryPerformanceCounter is being used for anti-debug techniques. When a process is being debugged there is a delay between instruction and execution. By using QueryPerformanceCounter we can measure the delay taken to run each instruction.
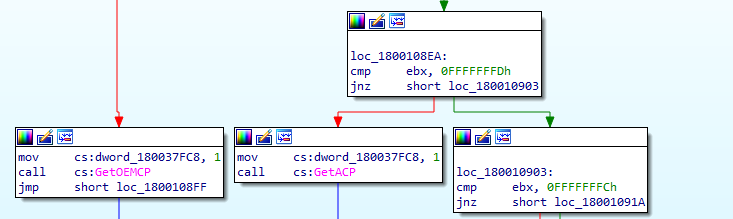
In the above figure, we can see that GetOEMCP is used, which returns the OEM code page identifier of the Operating System.
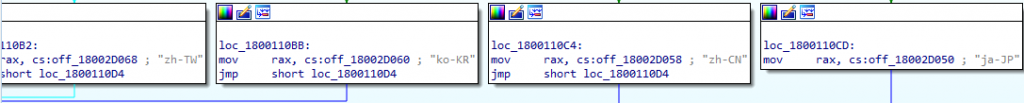
The malware then checks if the code page identifier is one of zh-CN, zh-TW, ko-KR, ja-JP. This is done to check if there is any clipboard data related to Chinese, Japanese or Korean language. If it is in one of these locales, the malware process throws an exception and terminates.
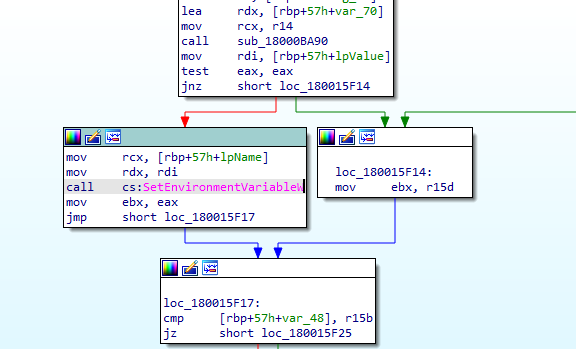
The sample under consideration has the ability to set an Environment Variable, it has been observed that malware tends to bypass the normal order of loading a DLL and loading it from another location.
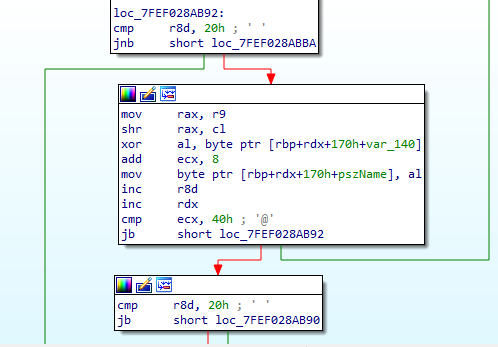
The malware keeps all the static data like url, client header, registry value, filename encrypted, which is decrypted as shown in Figure 11.
For example
Encrypted filename –
3B 20 54 18 7E 4F 8C 7F 70 20 5D 18 22 4F 86 7F 70 20 41 18 0C 4F
Decryption key –
08 20 24 18 0C 4F E3 7F
The decrypted filename –
3proxy.exe
Encrypted Rundll32 path –
1B 5A 05 49 6F 95 80 90 2F 13 05 4D 7F 88 90 9A 35 53 6B 42 74 8E 8A 9B 34 0C 6A 2C 28 9E 9C 9A 78
Decryption key –
58 60 59 1E 06 FB E4 FF
Decrypted Rundll32 path –
C:\Windows\System32\rundll32.exe
Encrypted string –
7B 20 2C 16 67 FF 92 7F 7C 20 34 16 63 FF 81 7F 6F 20 2D 16 63 FF CE 7F 66 20 3D 16 72 FF E0 7F
Decryption key-
08 20 58 16 06 FF E0 7F
Decrypted string – s.t.a.r.t.l.e.a.g.u.e…n.e.t
Basic XOR encryption/decryption is at play here.
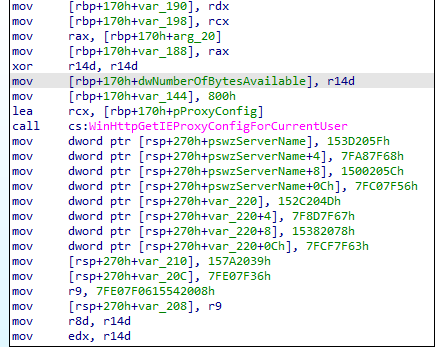
WinHttpGetIEProxyConfigForCurrentUser API is used to get the Internet Explorer proxy configuration for the current user. Then using this the malware can exfiltrate data gathered from the victim.
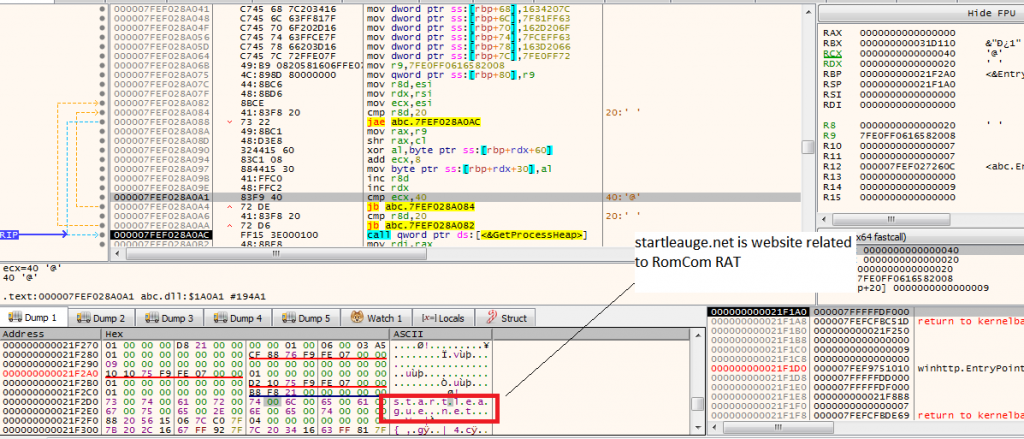
Here, we can observe that it’s decrypting “startleauge.net” using the decryption function mentioned in Figure 11.
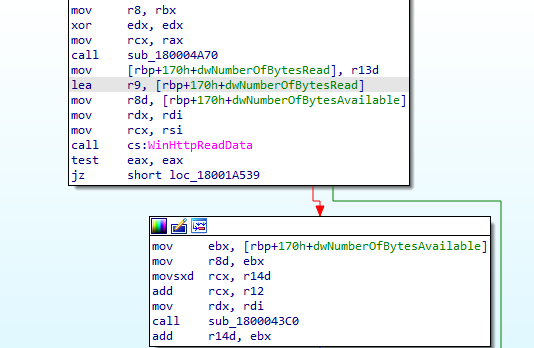
RomCom RAT uses WinHttpReadData API to download any file which is pushed by the C2.
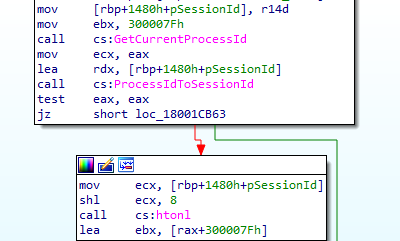
The malware tries to check if any active RDP session is live using the API ProcessIdToSessionId then proceeds to use the retrieved session ID to establish connection.
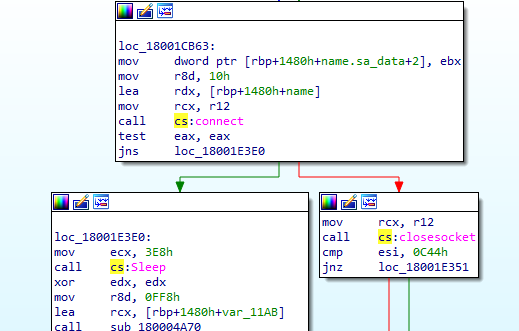
In Figure 16 we can observe that this RomCom RAT is trying to connect to C2. However, if the connection is not established then there is a sleep time before checking again.
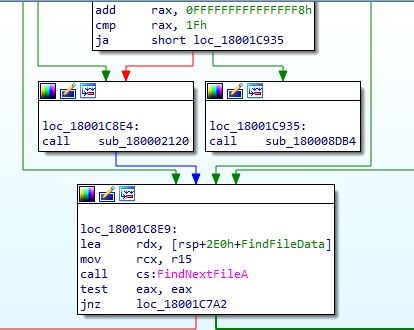
It traverses the file system using FindFirstFileA, FindNextFileA and collects a list of filenames and sends it to C2.
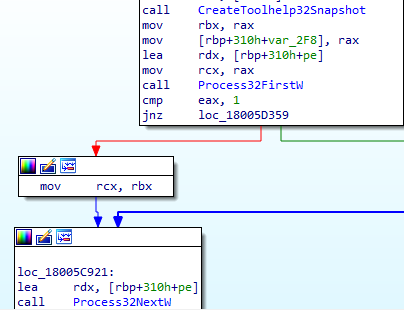
It uses CreateToolHelp32Snapshot and then iterates through the process using Process32FirstW and Process32NextW which is used to list all the running processes.
It has been observed that in a number of instances RomCom threat actors have used fake websites and applications to do its malicious activity.
We at K7 Labs provide detection for RomCom RAT and all the latest threats. Users are advised to use a reliable security product such as “K7 Total Security” and keep it up-to-date to safeguard their devices.
Indicators of Compromise (IOCs)
| Hash | Detection Name |
| 007A67BFA732084B3F8278B302BEF49E | Trojan ( 005a54be1 ) |
| 6F47723E5FC6E96AB5E9F96F6BC585FA | Trojan ( 00566ad51 ) |
| 46AC4B26D35F619D8A1415B5E4365A52 | Trojan ( 005a3e761 ) |
C2
startleauge.net
References
https://blogs.blackberry.com/en/2023/07/romcom-targets-ukraine-nato-membership-talks-at-nato-summit







