Unity is strength – this age old adage is true for just about everyone, even the bad guys.
It has become a common practice for threat actors to work in tandem for various reasons, viz. better chances of evading detection, increased magnitude or sophistication of the attack, etc., all of which are means to higher ill-gotten gains. And the availability of (malicious) source code on popular platforms like GitHub, Pastebin, etc. only makes life easier for these cyber criminals.
With this blog post we are going to explain one such recent “collaboration” which we would like to dub “The Scumbag Combo”, a true story of two malware families coming together to victimize the innocent and vulnerable.
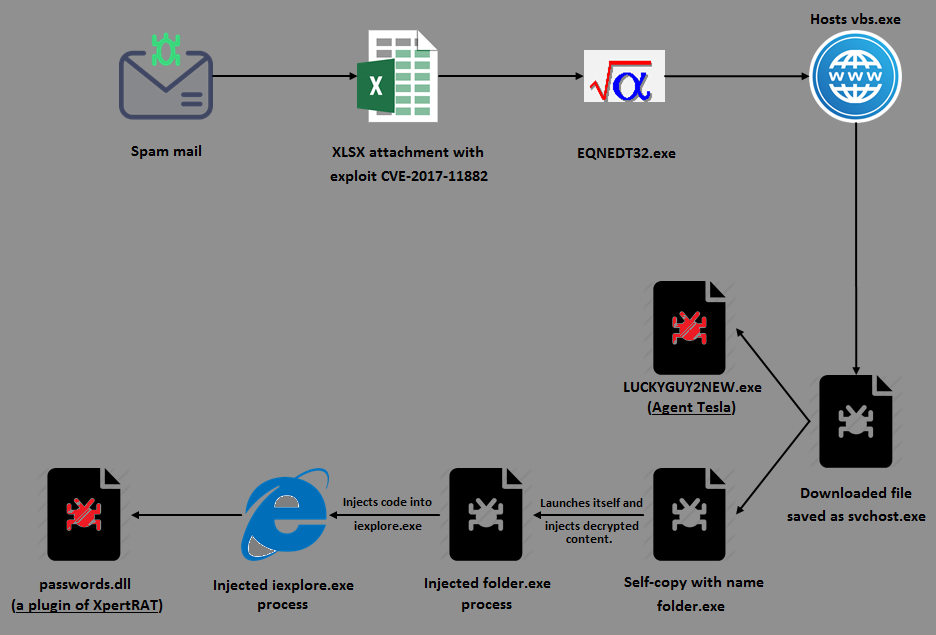
First, an introductory pictorial representation of the infection flow (Figure 1) before going into the morbid details.
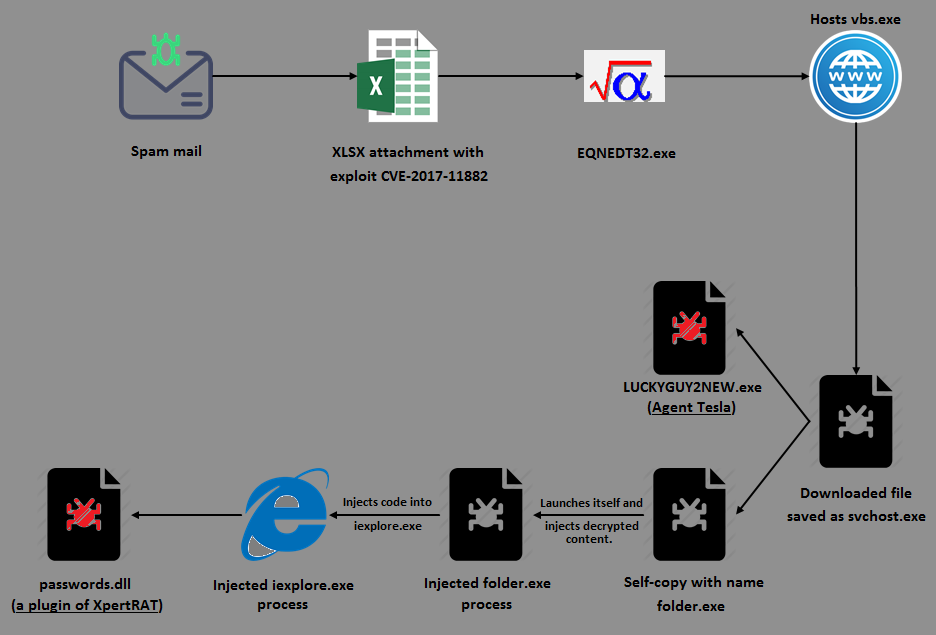
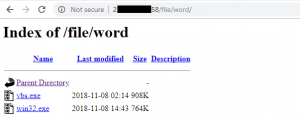
It all starts with a spam email containing an XLSX attachment that exploits the Microsoft Equation Editor’s remote code execution vulnerability (CVE-2017-11882) to download the file vbs.exe hosted on an open directory (Figure 2), save it as svchost.exe under %AppData% directory and automatically execute it. That covers half the picture and is fairly standard stuff, but then the rest gets pretty interesting.
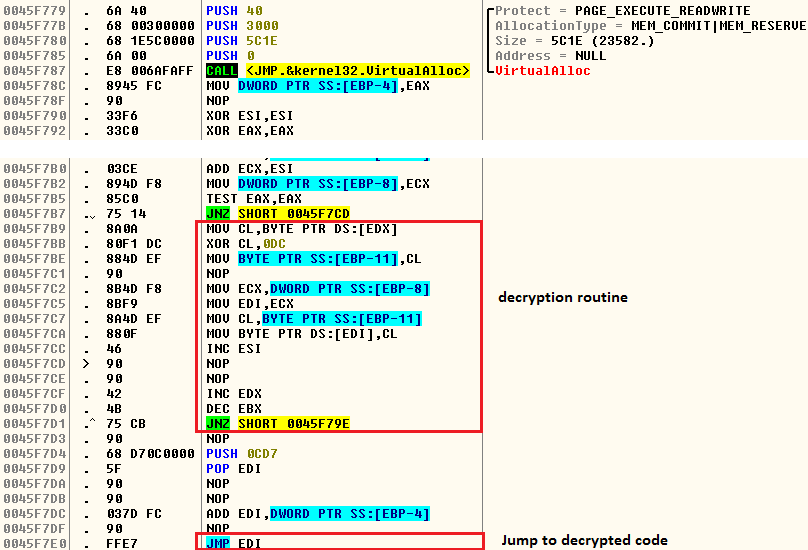
On execution, this fake svchost.exe decrypts the code responsible for the delivery of the aforementioned scumbags into allocated heap memory, and transfers the control to it (Figure 3).
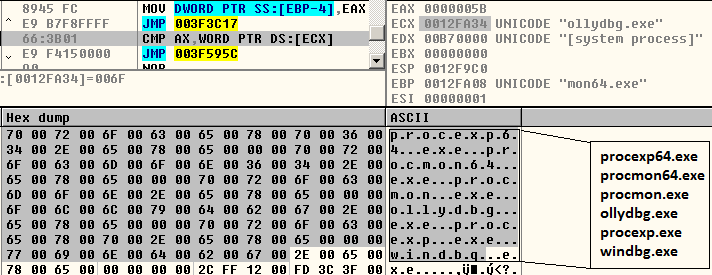
This decrypted code then continues to construct an import table for APIs to be used later. Additionally, it also checks for the presence of malware analysis and debugging tools (Figure 4), as well as anti-malware processes (Figure 5).
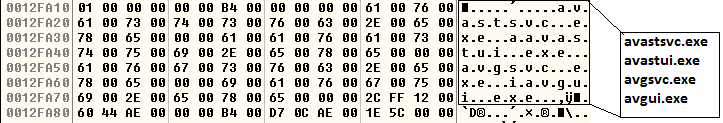
It further looks for the following anti-malware processes:
- avp.exe
- bdwtxag.exe
- bdagent.exe
- dwengine.exe
- avastui.exe
If any of the aforementioned processes are found it terminates itself.
If suitably assuaged, it continues to create a folder called “folder” under %AppData% and copies itself to this location as folder.exe (Figure 6).
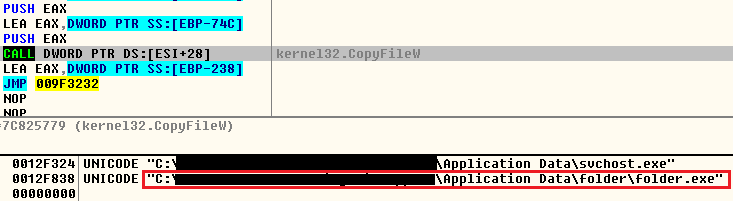
As the next step it decrypts a PE file LUCKYGUY2NEW.exe (Figure 7) into allocated heap memory, drops it under the %temp% folder, and executes it using the API ShellExecuteW.
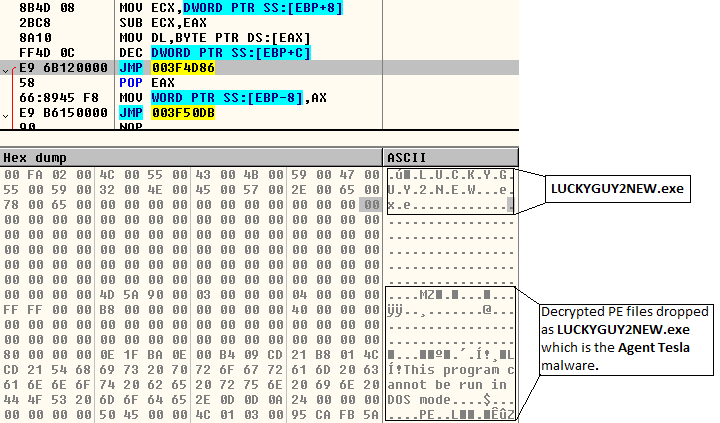
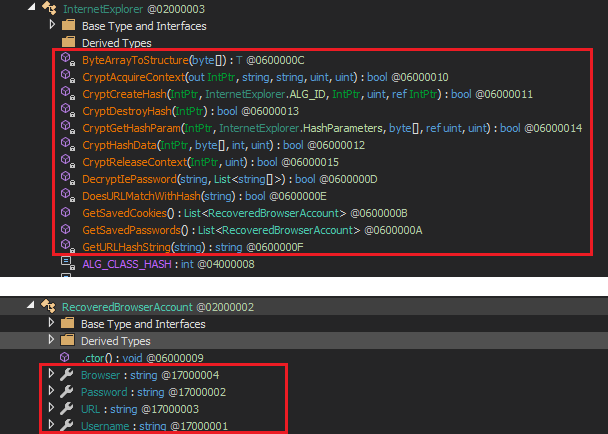
This binary, LUCKYGUY2NEW.exe, which is found to be an MSIL file, is the first of the scumbag duo to get onto the compromised system: Agent Tesla. It has keylogging, screen and video capturing, and password stealing capabilities. The password stealing module can extract saved passwords (Instagram, Twitter, Gmail, Facebook, etc.) from various browsers (Figure 8), mails and FTP clients.
Having delivered the Agent Tesla component, svchost.exe goes on to execute its copy folder.exe from within %AppData%\folder, which orchestrates the dramatic entry of the second protagonist of the scumbag show: XpertRAT. After executing folder.exe, the svchost.exe process gets terminated.
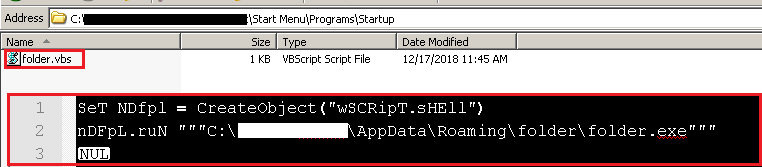
Note, persistence of folder.exe is handled by a VB script folder.vbs dropped in the Startup directory (Figure 9).
folder.exe does a redundant check for traces of the same set of malware analysis/debugging tools and anti-malware processes as depicted in Figures 4 and 5 above.
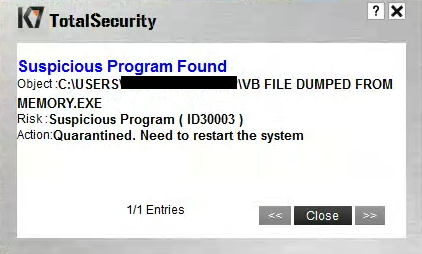
Next it decrypts yet another PE file in yet another blob of heap memory. And if you think that this is the XpertRAT component, well, you are plain wrong. Dumping the file from memory revealed it to be a Visual Basic compiled binary which injects into a legitimate Microsoft Internet Explorer (iexplore.exe) process.
folder.exe then creates another folder.exe process in a suspended state, injects the decrypted Visual Basic binary into it and resumes the thread (Figure 10). By the way, what’s with these guys and the word “folder”?! No imagination. Sheesh!
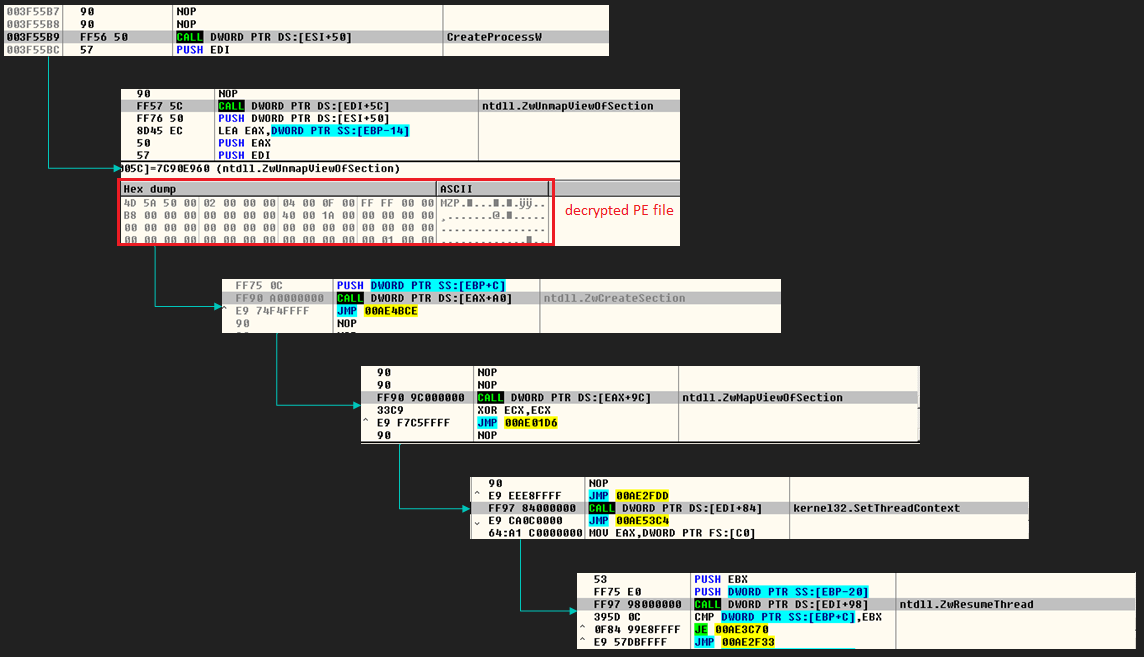
Once the injected process begins executing, it spawns the legitimate iexplore.exe process in a suspended state, injects its own code into it and resumes the thread. This then connects to a Command and Control server (C&C or C2) to which it sends the compromised system information (Figure 11), and requests for the Remote Access Trojan (RAT) component – XpertRAT.
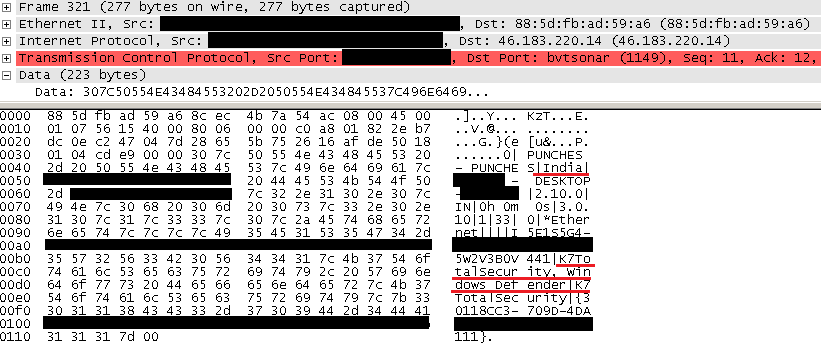
The C&C server, after validating the information from the compromised system, will respond with the RAT component – passwords.dll, an XpertRAT plugin as depicted in Figure 12.
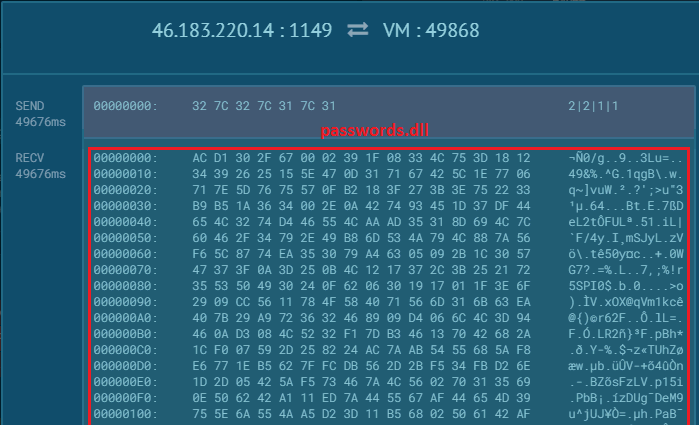
This plugin is used to retrieve all the usernames and passwords (Instagram, Twitter, Gmail, Facebook, etc.) stored in various browser caches and emails on the compromised system, which may then be stored in a text file to be either dispatched to the C&C or accessed remotely.
Lo and behold, all the actors are now on stage.
But worry not K7 users, for as always, we have you covered at every single layer of this attack! 🙂
Security Guidelines
- Install the latest service packs & hotfixes from Microsoft and enable automatic update/notification for patches on Windows.
- Cultivate the usage of spam filters.
- Do not open any email attachment that looks suspicious or that you weren’t expecting.
- Check the email and make sure it is not spoofed before downloading and opening any attachments.
- Upgrade all applications to the latest • stable versions.
- Install, enable and regularly update reliable security software such as K7 Total Security.
Indicators of Compromise (IoCs)
Files:
| Hash | Component | K7 Detection |
|---|---|---|
| 528D53B945516C8F18C63C5B8DF4695E | XLSX attachment | Trojan ( 0001140e1 ) |
| E0374BCC3615F00CDD9C9E3845A1EB74 | svchost.exe / vbs.exe | Riskware ( 0040eff71 ) |
| 88A93172E9BB75CE8638C36FF744BE55 | LUCKYGUY2NEW.exe | Trojan ( 0052d5341 ) |
| 9F9C272BF3372F6EE920DEAA00926689 | folder.vbs | Trojan ( 0001140e1 ) |
| 5C3E2E94AF5622A06D06EAC83CFA4C2B | VB file dumped from memory | Trojan ( 004be7cd1 ) |
| 2EEC4FEAAD2D41A806A8D3197A4F538B | passwords.dll | Trojan ( 0001140e1 ) |
URLs:
Dynamic detection:
Behaviour based detection of folder.exe process injection into iexplore.exe