It is not new for malware authors to abuse redirection/shortening services to trick victims into clicking links to malicious URLs. This blog explains how users are tricked into clicking what looks like an YouTube link but are in reality redirected to malicious websites and thereby becoming a threat for them.
This post about “Casino hack” is one such example. The very word will definitely lure users into clicking the link to find out more. Little do they know that this is a trap laid out by the threat actors to download malware onto their devices.
Attackers use keywords in URLs like Casino hack, Telegram crack, Hack tools, game names to lure the victims into clicking those URLs which in turn will lead them to sites compromised by attackers to download malicious files. One such site used is Upload.ee.
Upload.ee is a genuine site and is used to upload and download files with best quality and speed, this has been used by the attacker to host malware.
The URL redirection link from YouTube is hxxps[:]//www.youtube.com/redirect?v=sqxO40hXxq0&event=video_description&q=https%3A%2F%2Fwww.upload.ee%2Ffiles%2F12574316%2FCasino_Hack_by_YAZD_v3.49.rar.html&redir_token=QUFFLUhqbWxNY05PdGpOdTJfRG9qUHFTamU5Nlh0cnYzQXxBQ3Jtc0ttMFNLS3otU3dVZ1pfNDhRYWhiZE1KeUdLdDY5c3hrN0xpX3k2S3B4ZHl3cW41WktNdnR3Q1RERktoWWNoS3VHeVdWdm13dmhYSzdKVXVGeG1qYzlub0k5Vnp4dWxFbnBVVXpaUXNTMkFqM05ycS16QQ%3D%3D.
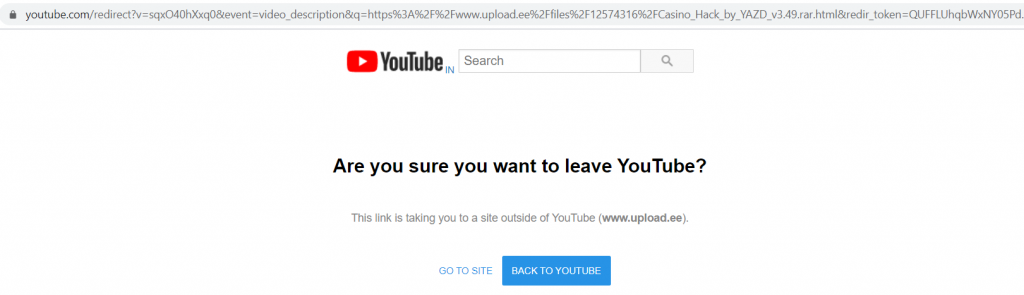
This link leads to the Upload.ee site, from where the Casino_Hack_by_YAZD_v3.49.rar is downloaded.
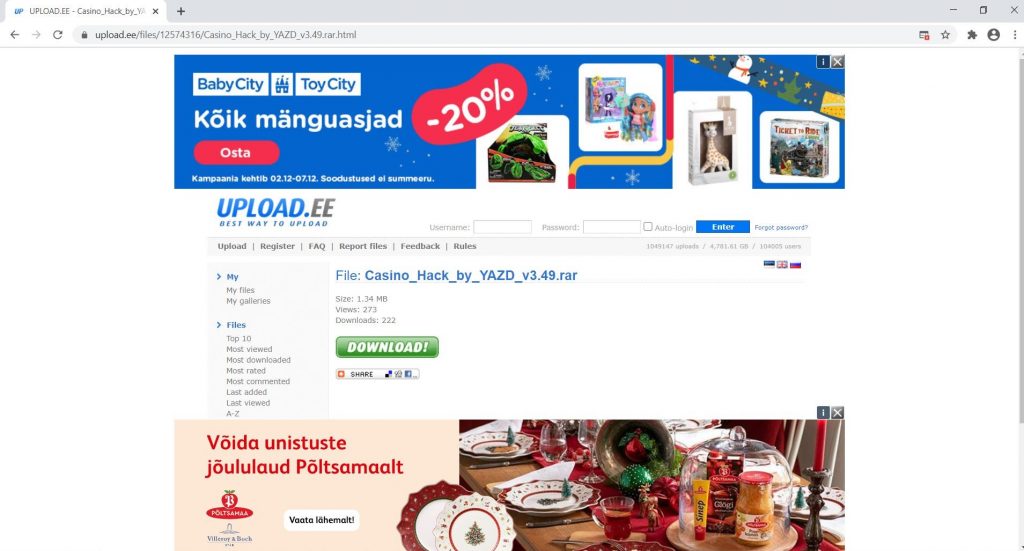
On extracting Casino_Hack_by_YAZD_v3.49.rar, it contains Casino Hack by YAZD v3.49.exe, Casino Updater.exe and a Read Me.txt as shown in Figure 3 and Figure 4.
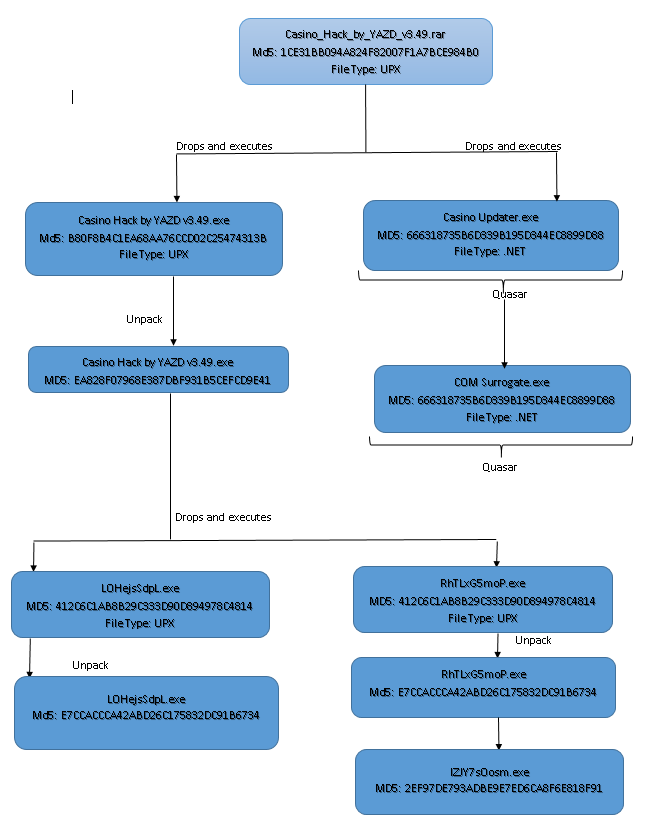
The working flow of Casino_Hack_by_YAZD_v3.49.rar has been depicted below.
Casino Hack by YAZD v3.49.exe
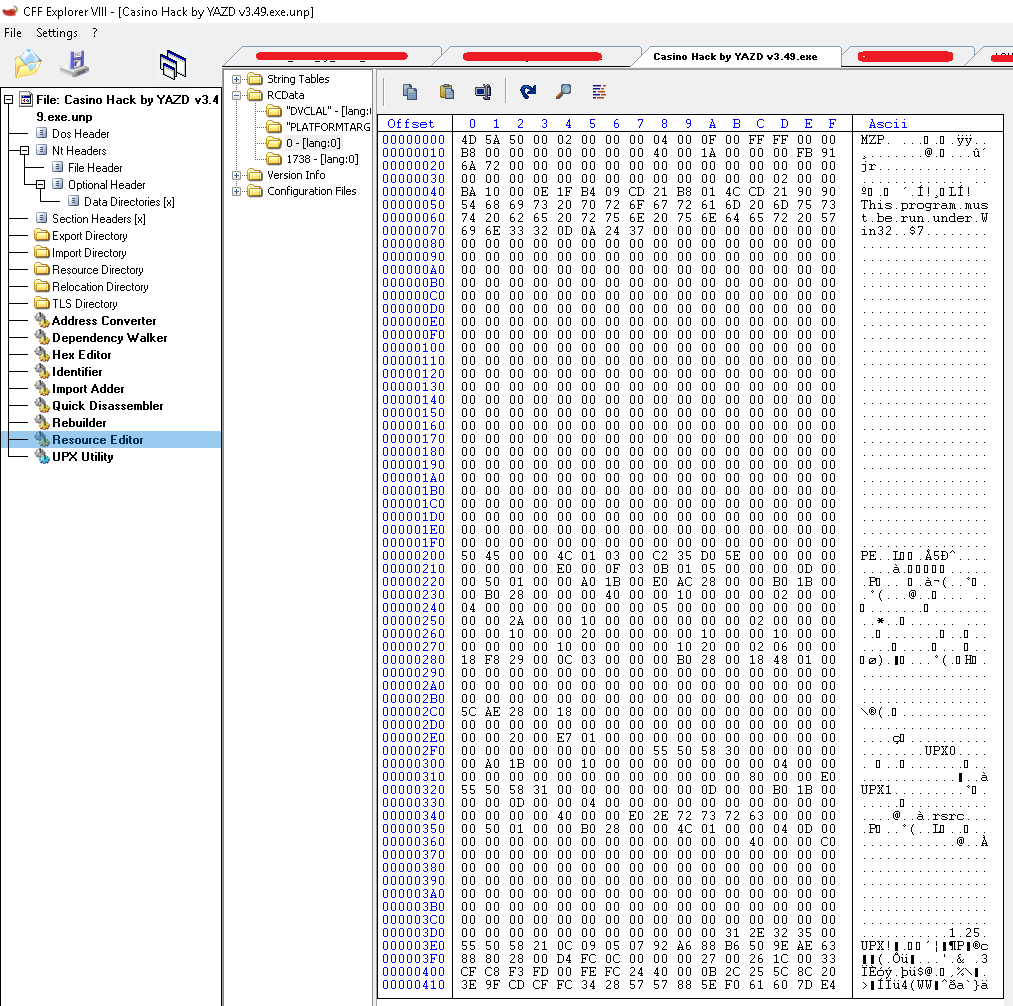
The extracted file Casino Hack by YAZD v3.49.exe is found to be UPX packed and on unpacking the file, it has a PE file in its resource section.
This Casino Hack by YAZD v3.49.exe drops C:\Users\_\AppData\Local\Pic1fPBkmq\LOHejsSdpL.exe and C:\Users\_\AppData\Local\Temp\RhTLxG5moP.exe which is again a UPX packed file and the unpacked files contains PE file at its resource section. RhTLxG5moP.exe inturn drops C:\Users\_\AppData\Local\Temp\lZJY7sOosm.exe.

Casino Updater.exe
The other extracted file Casino Updater.exe is found to be a malicious Quasar RAT executable. Quasar RATs are open-source Remote Administration Tools for Windows written in C# and available publicly in the GitHub repository. Figure 8 lists the features of Quasar RAT which are pretty self explanatory.
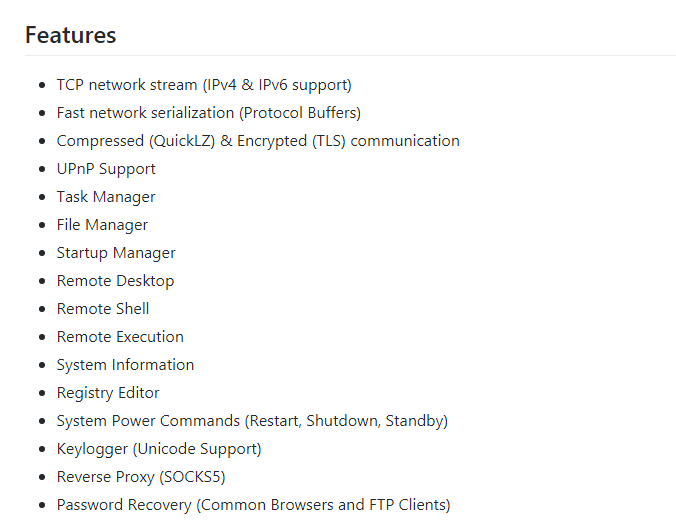
These are .NET files and most of the time these are found to be used by many APT actors and in most instances these are packed to make the analysis difficult.
The Quasar malware Casino Updater.exe starts itself from another location C:\Users\_\AppData\Roaming\COM Surrogate and creates persistence by making changes in the Autorun registry HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run\COM Surrogate.
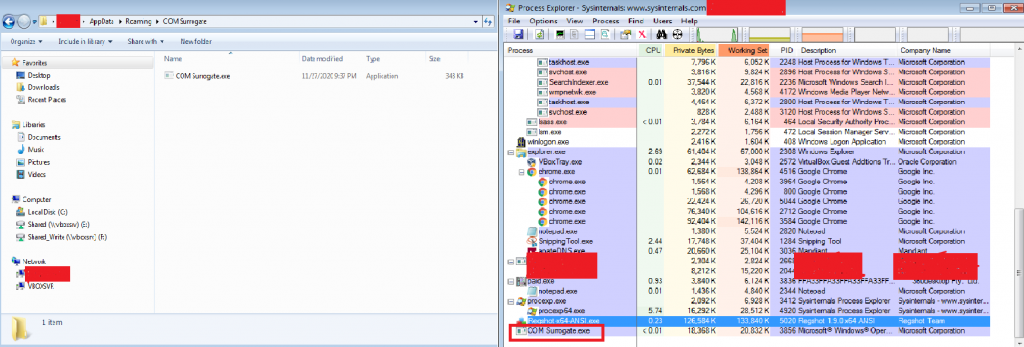
The IP contacted by Casino Updater.exe is 208.95.112.1 and this IP has been observed to be carrying out SSH brute force attacks in the past. The domains contacted are ip-api.com and hasamu.duckdns.org where ip-api.com is usually used by RATs and spyware as reconnaissance on systems that are infected.
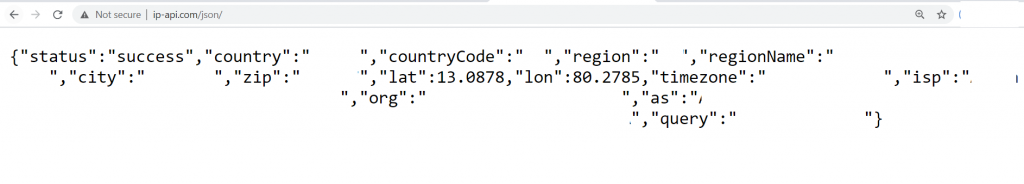
The attacker sends a http GET request to hxxp[:]//ip-api.com/json/ where the geolocation of the malware being downloaded is received by the attacker.
Some of the APT groups that have used Quasar RAT in the past are Iran based APT 33, Pakistan based Gorgon group, Gaza cybergang, India based Dropping Elephant and China based APT 10. The main intention of all these groups has been information theft and espionage activities.
Remote Access Trojans can cause heavy damages. The target could be all kinds of sectors because this tool is open-source and could be used by any threat actor. Since Quasar RAT have many features and capabilities, it is better to always be precautious while clicking any link.
Here at K7 Labs we keep actively monitoring such malware and have proactive detection for all the variants that are downloaded by clicking the malicious redirect YouTube (or any other legitimate service) URLs.
Indicators of Compromise (IOCs)
| MD5 | File Name | K7 Detection Name |
| 1CE31BB094A824F82007F1A7BCE984B0 | Casino_Hack_by_YAZD_v3.49.rar | Trojan ( 0001140e1 ) |
| B80F8B4C1EA68AA76CCD02C25474313B | Casino Hack by YAZD v3.49.exe | Password-Stealer ( 00567ea11 ) |
| 666318735B6D339B195D344EC8899D88 | Casino Updater.exe | Trojan ( 00521dab1 ) |
| 666318735B6D339B195D344EC8899D88 | COM Surrogate.exe | Trojan ( 00521dab1 ) |
| 412C6C1AB8B29C333D90D894978C4814 | LOHejsSdpL.exe | Password-Stealer ( 00567ea11 ) |
| 412C6C1AB8B29C333D90D894978C4814 | RhTLxG5moP.exe | Password-Stealer ( 00567ea11 ) |
| 2EF97DE793ADBE9E7ED6CA8F6E818F91 | lZJY7sOosm.exe | Trojan ( 0001140e1 ) |
MITRE ATT&CK
| Tactics | Techniques |
| Execution | Execution through API |
| Persistence | Registry Run Keys/Startup Folder |
| Winlogon Helper DLL | |
| Defense Evasion | Install Root Certificate |
| Discovery | Query Registry |