Recently we received an email from the RBI (Reserve Bank of India), or so it claims to be, regarding a ‘One Time Password’ registration. This ended up in the spam folder. Let us see why.
Here is the email in question:
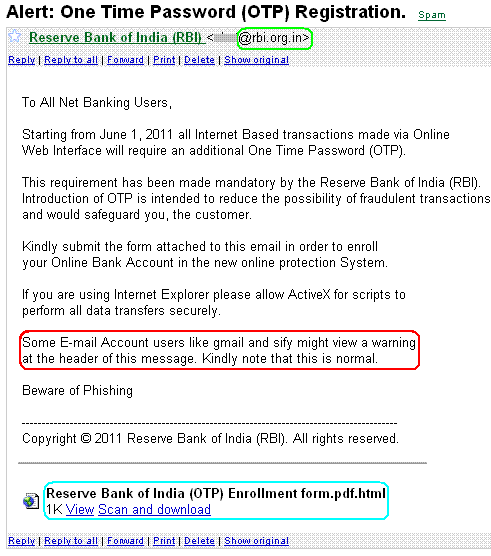
- The source of this email (highlighted green) is ‘rbi.org.in’ which is not suspicious but is probably spoofed.
- It informs us to ignore any warning (highlighted red) that the email client might give us. This is suspicious.
- The attachment (highlighted cyan) has a double extension. This is clearly suspicious.
There is even a tail-piece of advice to ‘Beware of Phishing’ to make the user feel good about the message. After all, no thief warns you about impending thievery, right? Wrong!
Once you download and open the attachment you are directed to the following page:
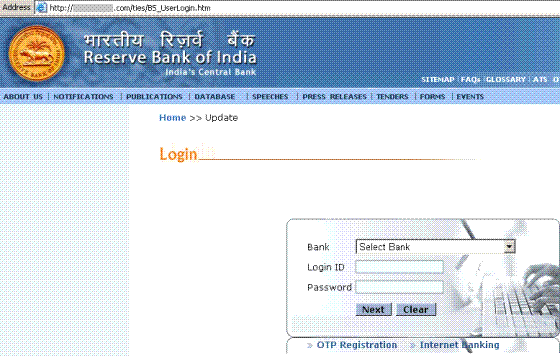
This looks like a normal RBI page. But a closer look at the address reveals for a fact that this not an RBI page. It is a login page but it is not secure, and there is no ‘https’ authentication. This is a cleverly constructed page. Only the ‘Login ID’ and the ‘Password’ fields are custom made. The rest is ‘borrowed’ from the actual RBI site, therefore clicking on any of the menu items would still take you to the valid RBI page.
Let us check what is inside the attachment:
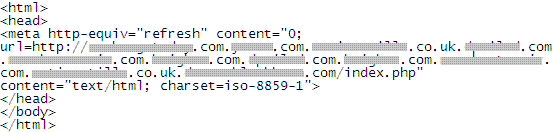
This URL has quite a number of sub-domains (grayed out for security reasons), none of which is even remotely related to the RBI. This is highly suspicious. Double-clicking on the attachment would take you to the page shown above which masquerades as a bona fide RBI site.
Let us start filling in the form with some fake details:
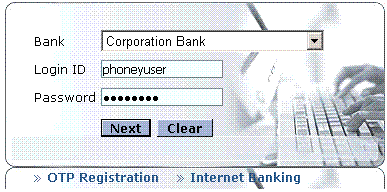
Once you fill in the details and click next you will be taken to the following page wherein you’ll be asked to fill in your transaction password and mobile number:
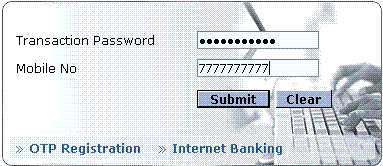
Once you click submit it throws a message that the registration is successful. But there was no actual password registration done during the entire exercise. The mail states an additional password is to be created, which was never done here. Whenever a new password is created any valid system would ask you to confirm your password, which was not the case here. Hence this is a clear attempt to phish out confidential details.
The network captures of the above exercises show the password and user names being sent over the Internet as plain text messages:
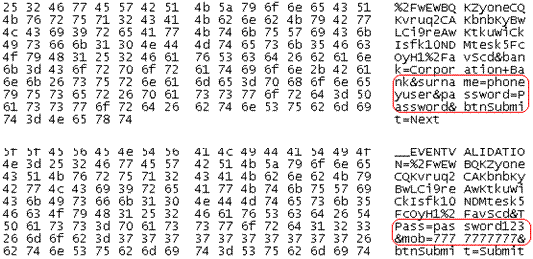
Never would your bank send your banking credentials as plain text. They are always sent over a secure connection in an encrypted format.
At the time of writing the attack domain was still live. To avoid being a victim of such social engineering attacks, the solution to a large extent still rests with the user, even though URL filtering and phishing heuristics do thwart many of these attempts at phishing. Please read through one of the earlier entries to find out how to recognize and stay away from phishing scams – ‘Teach a Man to Anti-Phish’
Kaarthik R.M
K7 TCL








