Torrenting is a popular form of peer-to-peer (P2P) file sharing. While torrenting is not illegal by itself, it is often associated with sharing copyrighted material like movies, games and software which amounts to piracy and hence illegal. The websites that host such torrents not only drop malware on to a victim’s system but also earn money via advertisements through distribution of adware. Threat actors do their fair share of abusing such services, They run malware campaigns by bundling malware with “Cracked Software” whose torrents are uploaded to such sites. This goes to show that users are eventually compromising their devices. Pirated software means a user may not get proper updates (feature and security) to that software and eventually contract malware either at the time of installation or via security flaws in an outdated software.
It is normal for people to incline towards stuffs that are “free”. Piracy tempts this bunch, and makes them a victim of malicious attacks. Torrenting can be legal, illegal or a bit of both based on the demography. There are no specific rules in our country to regulate the download and usage of copyrighted content and hence this piracy business thrives here.
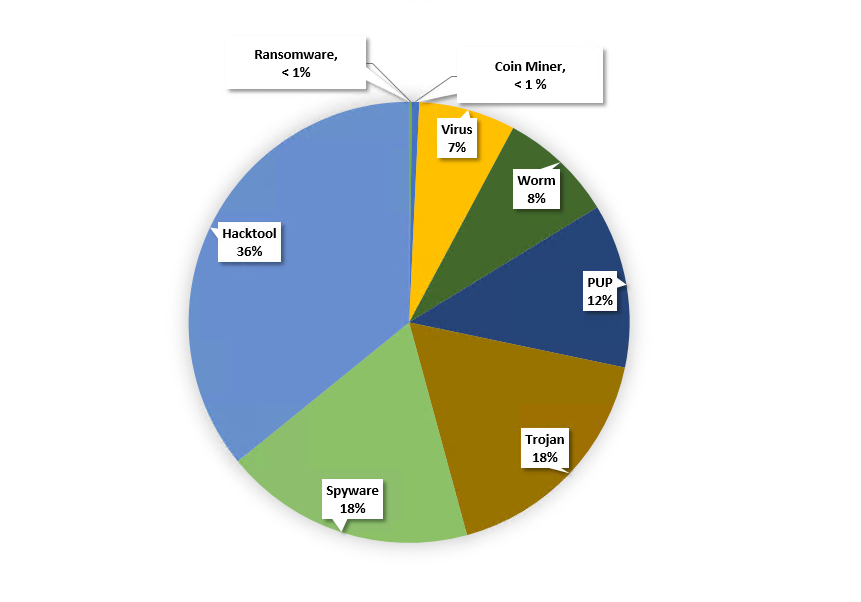
Our telemetry data for the last three months were filtered to extract filenames that contain keywords like “Crack”, “Activator”, “Keygen”, “Serial key”, “Loader” and “Patch”. These were downloaded from various sites among which Torrents were the predominant source. These files are categorized according to their actual behaviour as shown in Figure 1.
Mostly a software and its activator are shared in these sites for the user to download as a bundle. In this, the software which the user intends to install in their system is usually a trial version which is legitimate. But the activators/patchers/keygens that accompany these software in several cases can contain malware. An activator is a piece of software that can illegally bypass trial mode forever by patching the code in the software that actually checks for trial expiry. AV companies mark these activators as PUP (Potentially Unwanted Programs or Keygens). These activators may come bundled with malware that infect the victim’s machine with RATs, Trojans and in some cases even ransomware.
Installation Checks
These activators are either encrypted or password protected, thus making it more challenging for the AV vendors to detect them. Usually the password to these files are placed in the “Readme.txt” file that is accompanied with this software or shown in the webpage from where it is downloaded. For installation of these activators, the users are instructed to disable Anti-Virus softwares, thereby making it far too simple for the user’s machine to be compromised.
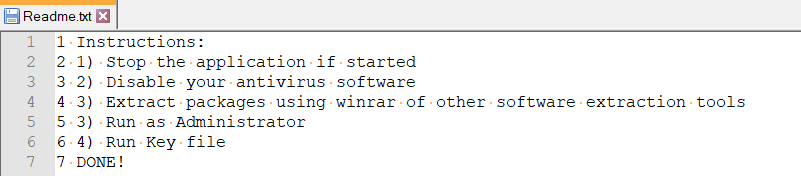
The strategy used by the threat actors for the malware campaigns is to create multiple versions of the same file by renaming them to the latest or popular software so as to reach a lot of targets. Comments in the Torrent download page are also disabled so that victims don’t alert other potential victims of the malicious nature of the file to be downloaded.
Let us now look at a few of the malware campaigns.
Glupteba Campaign
We recently came across a Torrent site sharing cracked software, activators while delivering Glupteba malware. This malware family was first spotted in 2014.
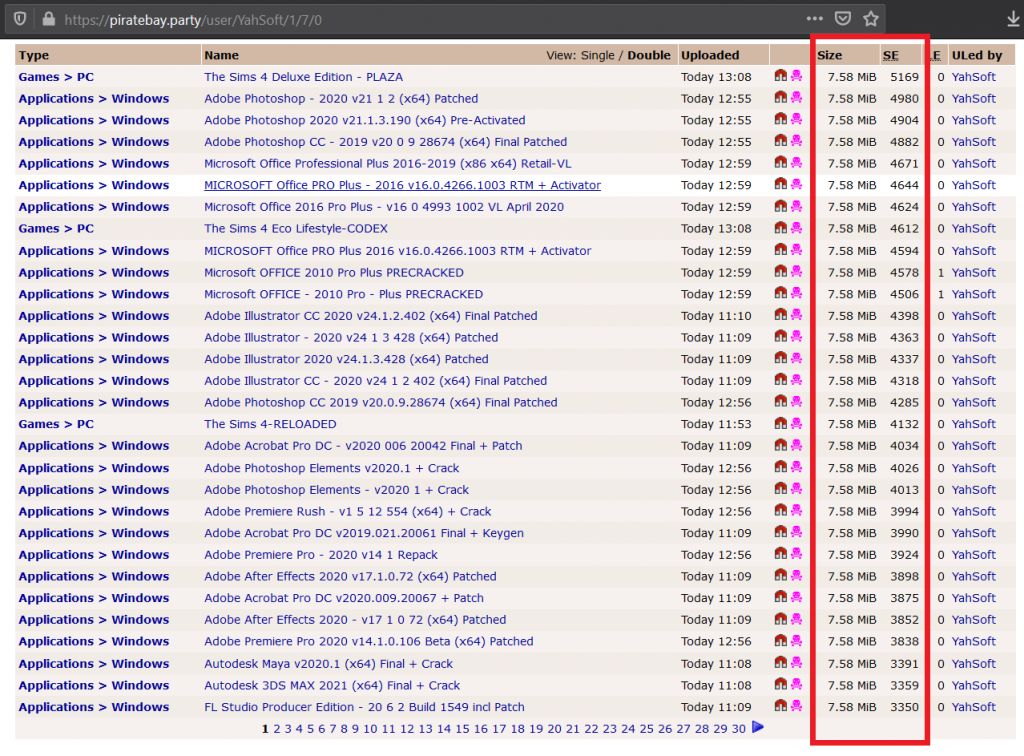
The “Seeding” indicates that a lot of users have already downloaded and were thereby infected, that too in a short span of time as shown in Figure 3.
Glupteba represents both a malware family, and its distribution framework. It has multiple capabilities which includes
- Data exfiltration and Browser Password Stealer
- Command line – CNC communications
- Living off the land techniques
- Anti-VM and detection techniques.
- Backdoor activities
- Cryptojacking with regular updates
- Remote Code Execution
- Lateral movement via EternalBlue exploit
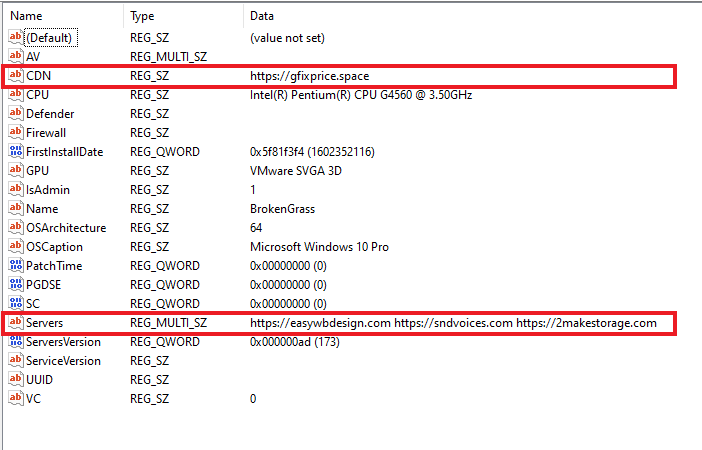
The activity starts with collecting the system information using WMI commands and storing it in a registry with its CNC server address.
It achieves persistence by copying itself to the folders such as “\AppData\Local\Temp\”, “\Windows\rss\” or “\Windows\temp\” with a filename that mimics system processes such as “csrss.exe”, “scheduled.exe” or “app.exe”.
It then adds itself to the “Task Scheduler” to run every 10 minutes, using the Windows binary “certutil.exe”. This malware also can manipulate “fodhelper.exe” and runs the file with elevated privileges by bypassing UAC.

It also adds Windows Defender and firewall rules to allow communication without any interruption.

If there are errors at any phase, the failure messages are reported to the server using HTTP requests along with details of the failure.
Altogether the malware can update, download, execute commands, notify, verify-version, take screenshots, steal browser passwords, cookies and histories, upload all collected information to CNC servers.
Glupteba uses one CDN server for content delivery and several other C2 servers for various other purposes. It uses Bitcoin Blockchain as a communication channel for receiving updated configuration information once successfully installed. All the other components are installed on an as-needed basis.
UnDetected Campaign
In another similar malware campaign that we came across, the payload was a password stealer.
It starts by retrieving the public IP of the victim’s machine from “api.ipify.org” and stores it in the system as a “.png” file. It then retrieves passwords from browser cookies, encrypts everything as a bundle and sends them to the CNC servers.
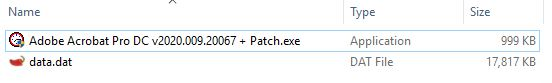
The downloaded file contains the malware and some junk data. The junk data has been added to increase the overall file size and to avoid suspicion as shown in Figure 8.
The malware resembles the Cobalt Strike’s Beacon payload.
Other OS Malware Campaigns
Apart from Windows OS, other platforms like macOS and Android are also being targeted. Pirated software is enticing for a user regardless of the platform thus creating more victims.
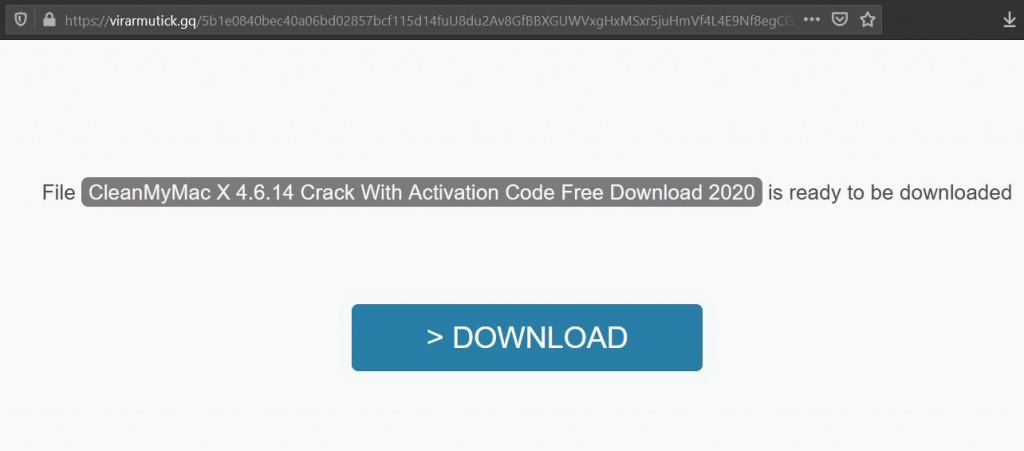
This site shown in Figure 9 downloads Mac adware.
Similar to the above attacks we have also come across gaming software which have been embedded with coin miners as gaming PCs are usually built with high performance GPUs which makes them a lucrative target.
Conclusion
Piracy is really a concern for the developers as they are not making a profit when their content is being distributed for free on Torrent sites. Due to the large volume of data being exchanged and the P2P’s decentralised model, it is almost impossible to verify all the data. And with added lack of, or not so strict moderator rules/guidelines, Torrent websites end up containing a lot of malicious content. Moreover, there aren’t any proper content regulation policies in place that can govern such sites. Users are thereby advised to maintain caution when downloading software from these sites. Also use a reputable security product such as “K7 Total Security”, “K7 Mobile Security” and “K7 Antivirus for Mac” to scan any software that you download and keep it updated. The popular adage “There ain’t no such thing as a free lunch” is very apt here.
Indicators Of Compromise (IOCs)
| Hash | File Name | K7 Detection Name |
| 460A3F2D678508BB124F40856D8BD166 | Windows – Adobe Photoshop CC – 2019 v20 0 9 28674 (x64) Patch | Trojan ( 0056a3b51 ) |
| A81A70B79945ABCA5EEE1293E140B36A | Windows – Adobe Photoshop CC – 2019 v20 0 9 28674 (x64) Patch | Trojan ( 0056a3b51 ) |
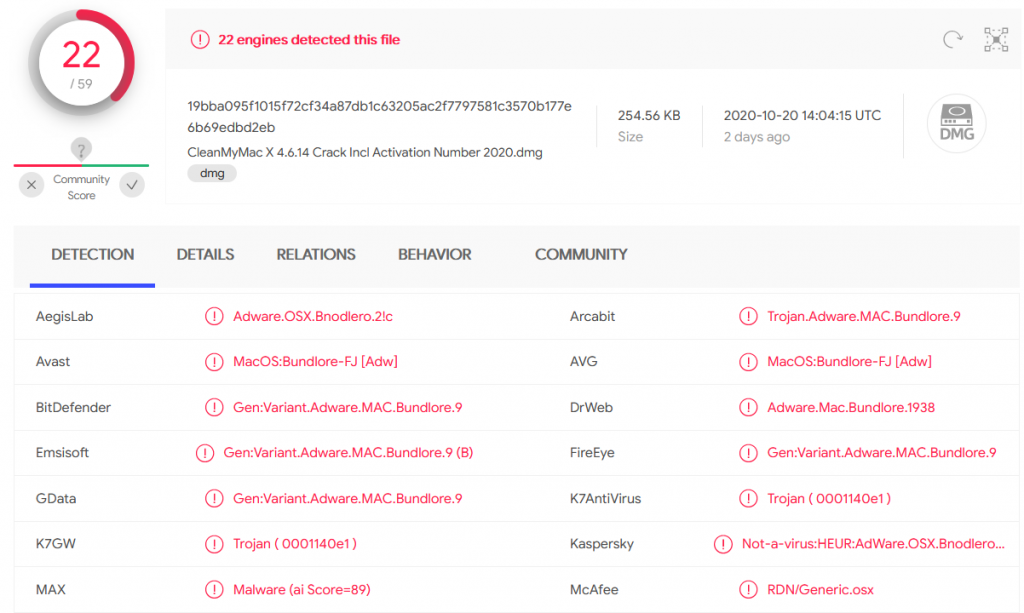
| fd2efb9b94091767726b4a0ca407c5a9 | Mac -CleanMyMac X 4.6.14 Crack Incl Activation Number 2020.dmg | Trojan ( 0001140e1 ) |
Links
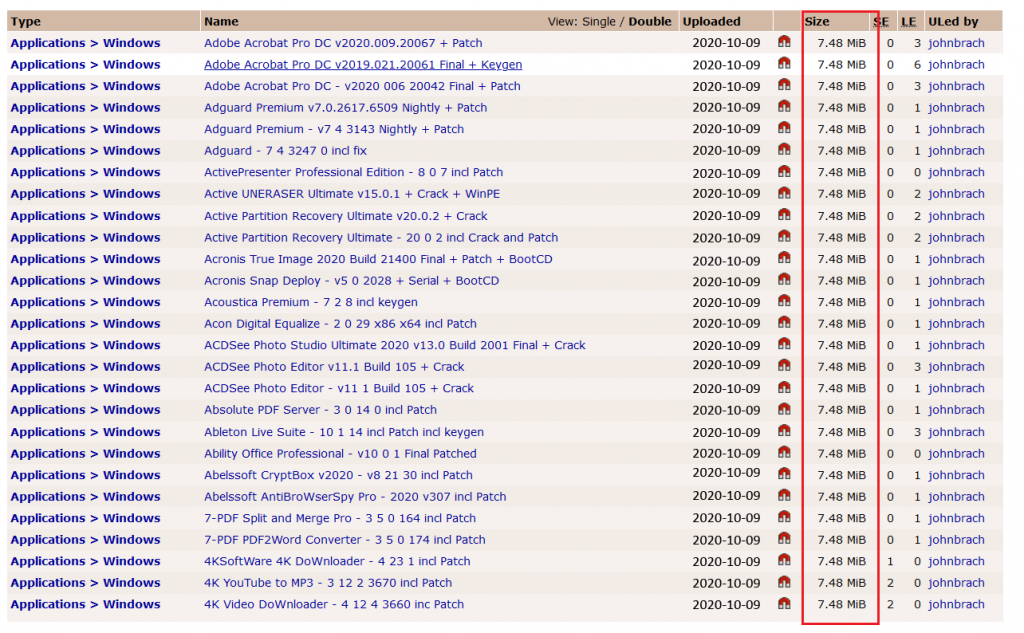
https[:]//piratebay[.]party/user/YahSoft/1/7/0
https[:]//thepirate-bayproxy.com/search.php?q=user:johnbrach
http[:]//letcracks[.]com/search/search[.]php?&q=CleanMyMac%20X%204.6.14%20Crack%20With%20Activation%20Code%20Free%20Download%202020










