STOP/DJVU ransomware was first seen in the last quarter of 2018. Since then we have seen various forms of this malware, active till date. In this blog we will present a technical analysis of one such sample.
MD5: ad2836ab1793d67eae124e749b371a6d
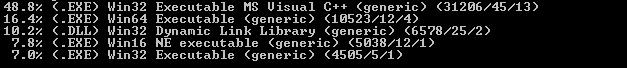
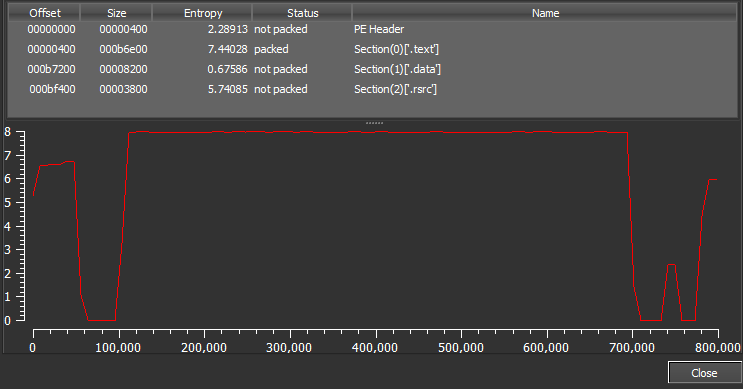
As you can see from Figure1 it is a C++ binary. Further static analysis revealed the .TEXT section to be packed as you can see in Figure2.
When we run the sample the process tree would look as shown in the picture below
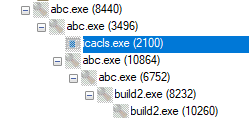
Looking carefully at the child processes, we can see icacls.exe being used. icacls.exe is a command line utility which is used to modify NTFS file system permission and the command line arguments “/deny *S-1-1-0:(OI)(CI)(DE,DC)” after which the user will not be able to delete the folder containing a copy of the initial malicious executable (abc.exe).

Malware then launches itself with the parameters as shown below

Another Persistence technique used by malware is creating a Run entry “SysHelper”.
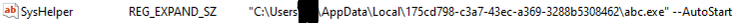
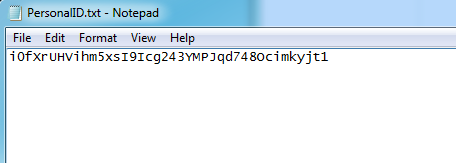
It also assigns some unique PersonalID and drops it as PersonalID.txt in C:\ SystemID folder
So let’s open the sample in x32dbg to unpack it. We’ll not go deep into unpacking as there are various blog posts regarding that and not many changes have been done to STOP/DJVU from previous years samples.
GetProcAddress API is used to retrieve the address of the VirtualProtect function, memory area is allocated and VirtualProtect is used to change its protection to 0x40 which Enables execute, read-only, or read/write access to the committed region of pages.
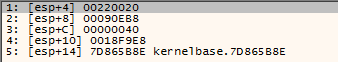
When the allocated bytes are written in memory it reveals to be a Shellcode as you can see in Figure9. After the shellcode is written in memory then an unconditional jump “JMP EAX” transfers the control to the shellcode.
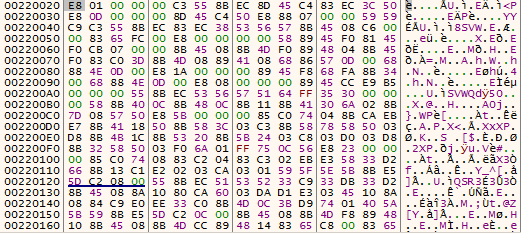
Analysing the shellcode reveals that it again allocates some memory. EAX register shows the return address/address of the allocated memory as shown in Figure10. After the memory is populated it drops another shellcode as shown in Figure11

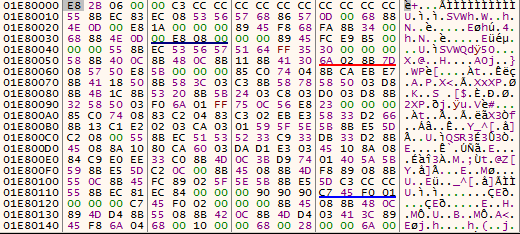
Looking at the strings from the dumped shellcode reveals various interesting APIs but the most interesting API was ResumeThread which is usually used in a Process Injection technique called Process Hollowing. After dumping the Process which was Injected we received a new Binary.
Analysing it statically we got to see some interesting strings from the unpacked payload like
PDB Path – E:\Doc\My work (C++)\_Git\Encryption\Release\encrypt_win_api.pdb
URL String – hxxps://api[.]2ip[.]ua/geo[.]json
Further analysing it we came to know initially that it connects to the url string mentioned above, the url gives information about the IP address, location etc as shown below
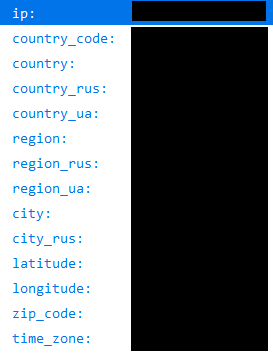
After that “country_code” values are compared with the following and it will only proceed further if not one of them.
- “RU” (Russia)
- “BY” (Belarus)
- “UA” (Ukraine)
- “AZ” (Azerbaijan),
- “AM” (Armenia),
- “TJ” (Tajikistan)
- “KZ” (Kazakhstan)
- “KG” (Kyrgyzstan)
- “UZ” (uzbekistan)
- “SY” (Syria)
And then it tried to connect to a URL and download a separate binary.
URL 1 – hxxp://zerit[.]top/dl/build2[.]exe
The URL is down now.
It will connect with URL 1 which later found to be downloading a Vidar stealer(build2.exe)
Vidar Stealer is a stealer which was observed in october 2018 and seen in numerous campaigns. Various Ransomware groups like GrandCrab used Vidar stealer in the process for distributing the ransomware as a 2nd stage payload. Interesting thing about this stealer is it fetches its configuration from the C2 server at runtime and it acts according to the commands received. Typically this stealer steals the user’s data and compresses everything to a ZIP archive and then exfiltrates it to the attacker.
Initially looking at it statically we’ll observe it to be packed and after unpacking it, the unpacked sample still contains Anti-Analysis-like Decrypted string, Decrypted APIs which it resolves in memory at runtime as shown below.
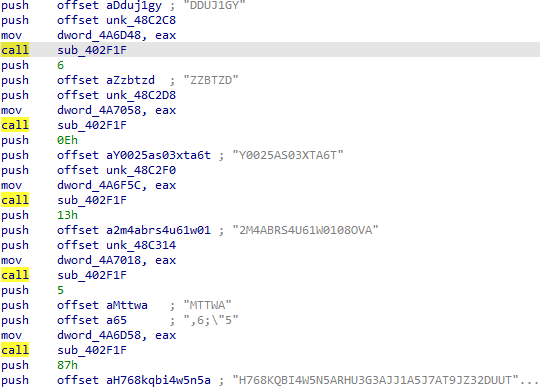
The decrypted data in memory as shown below
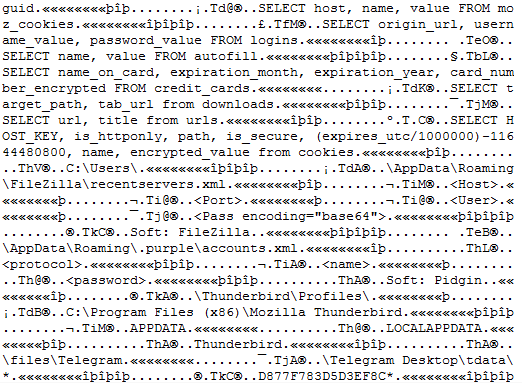
Decryption logic in assembly
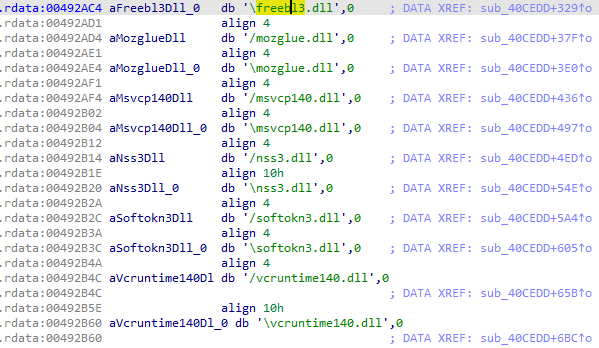
Download 5 extra legit dll’s to steal the sensitive data from IP 116[.]202[.]185[.]47
Vidar stelear connects with the C2 to get commands as to even what to collect and infiltrate. This is done by zipping all of the collected data and sending it to the C2 server.
It has the ability to steal data like browsing history, Cookies, login credentials of Various browsers like Firefox and Chrome etc. Even it tries to steal Cryptocurrency wallets of Ethereum, Electrum, MultiDoge etc. Initially it tries to collect basic information about the system and create a text file named “information.txt” as shown below and zip it all together and send it back to IP 116[.]202[.]185[.]47
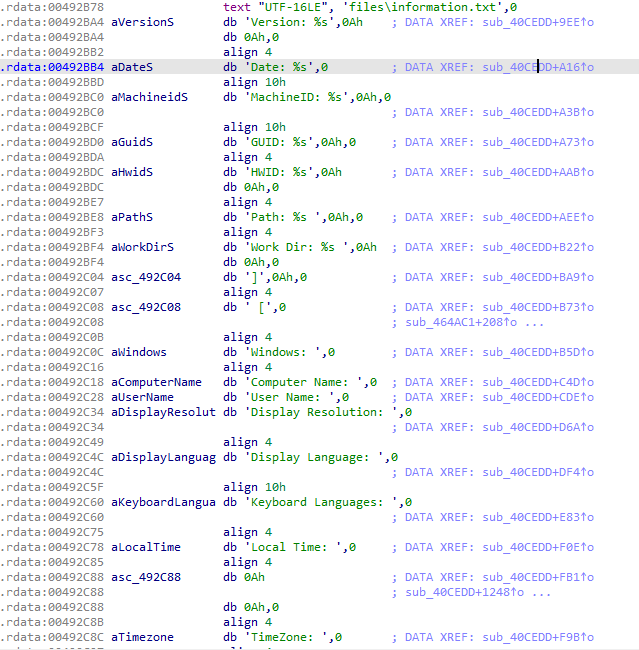
Figure17
Then after exfiltration it executes the second downloaded file from
URL 2 – http://fuyt[.]org/files/1/build3[.]exe which was accessed and downloaded along with URL1 but not executed at that time. Build3.exe is the Ransomware payload which encrypts the file with “.wdlo” extensions as shown below.

Indicators of Compromise(IOC)
| File Name | MD5 | K7 Detection Name |
| file.exe | ad2836ab1793d67eae124e749b371a6d | Trojan ( 005690671 ) |
| build2.exe | 8d86786e071aae59172dbdc0677abc3e | Trojan ( 005649fd1 ) |
| build3.exe | f5438e4937aa0e8e5da0b38e1fccd031 | Trojan ( 0058fe491 ) |
C2 :
hxxps://api[.]2ip[.]ua/geo[.]json
hxxp://zerit[.]top/dl/build2[.]exe
hxxp://fuyt[.]org/files/1/build3[.]exe
116[.]202[.]185[.]47